In a first-of-its-kind joint action today, the United States and the United Kingdom sanctioned seven individuals associated with the Russia-based cybercrime gang Trickbot. The actors designated today include high-level managers within the group, as well as lower-level developers and a money launderer who – until now – have largely evaded scrutiny. With these designations, the U.S. and U.K. governments are sending the message that whether an actor is an administrator, an affiliate, a developer, a services provider, or a money launderer, no one involved in the ransomware supply chain is safe.
The key to disrupting ransomware is to disrupt this supply chain, and today’s action – a partnership between the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the U.K.’s Foreign, Commonwealth, and Development Office; National Crime Agency; and His Majesty’s Treasury – demonstrates global coordination in this effort to dismantle Russian cybercrime and ransomware.
What is Trickbot?
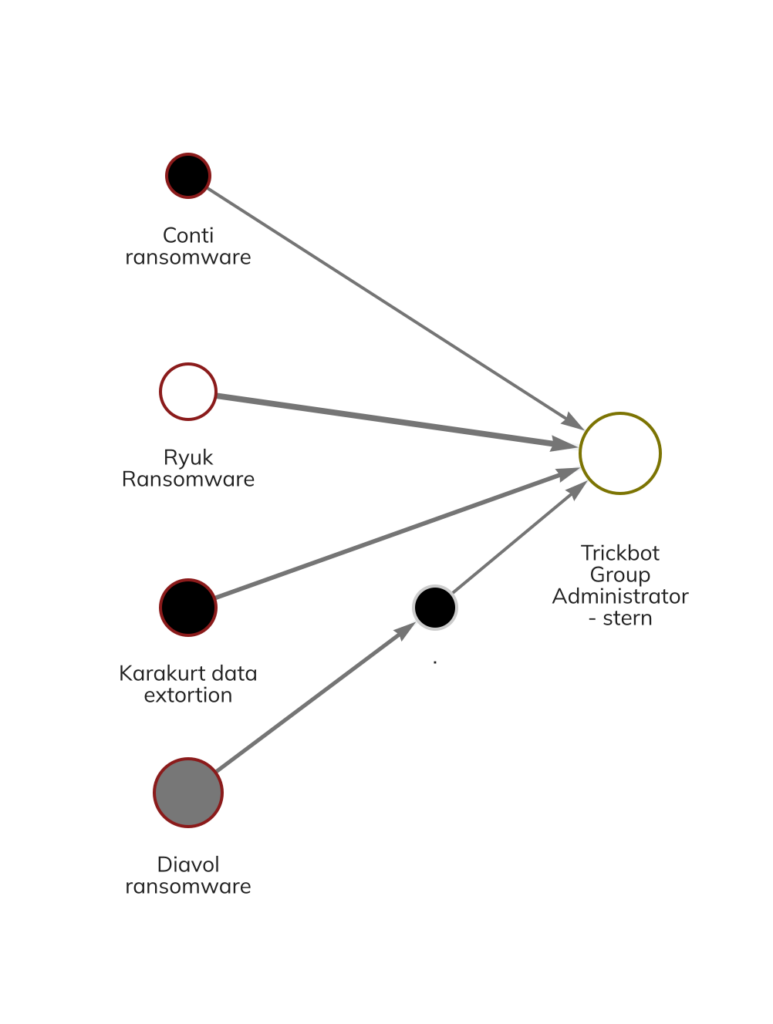
Trickbot is a type of malware that has been used in cyber attacks against businesses and individuals all over the world. Trickbot has dominated the malware threat landscape since 2016 and has partnered with ransomware groups to deploy several strains including Ryuk, Conti, Diavol, and Karakurt. The Chainalysis Reactor graph below shows wallets associated with these strains sending funds to Stern, the Trickbot administrator. According to Chainalysis data, strains related to Trickbot have extorted at least $724 million worth of cryptocurrency in their lifetimes. This makes Trickbot the second highest earning cybercrime group, following the North Korean-linked Lazarus group.
Ransomware and cryptocurrency
Because ransomware payments are demanded in cryptocurrency – usually Bitcoin – it may at first seem like cryptocurrency enables this extortion. But crypto is instrumental in fighting it. The blockchain allows us to link ransomware actors together, including developers like Trickbot, affiliates like those who work for Conti, and other enablers. Cryptocurrency blockchains are transparent, and with the right tools, law enforcement agencies can follow the money on the blockchain to better understand and disrupt an organization’s operations and supply chain.
As Chris Farrimond, Director Threat Leadership at the National Crime Agency, shared with Chainalysis in an email:
“The primary driver behind designating those responsible for damaging malware and ransomware attacks is to impose cost and risk on their operations. This is especially important on the blockchain, as we know Cyber Crime actors use cryptocurrencies to monetise the profits of their crimes.”
“We are fully committed to working with partners across the public and private sector to clamp down on the illegal use of cryptocurrencies and ensure sanctions are enforced on the blockchain, as they would in the traditional banking system.”
“Cryptocurrency analytical and compliance tools are critical to the NCA’s ability to investigate and disrupt these organised crime groups’ activities, and are capabilities we will continue to develop in pursuance of our mission.”
While OFAC and the U.K. HM Treasury Office of Financial Sanctions Implementation (OFSI) did not include specific cryptocurrency addresses as identifiers within their designations, Chainalysis has identified several of these actors’ cryptocurrency wallets.
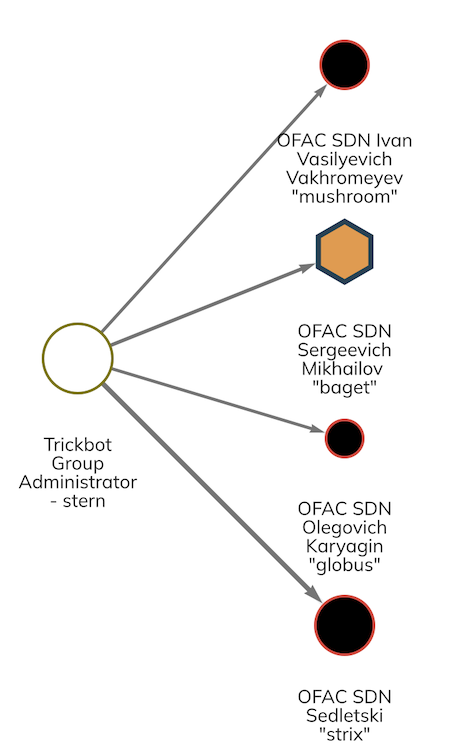
In the Reactor graph below, we can see that Trickbot administrator Stern sent funds to at least four of the seven actors designated today: Ivan Vakhromeyev (aka Mushroom), Maksim Mikhailov (aka Baget), Valentin Karyagin (aka Globus), and Valery Sedletski (aka Strix). These payments are likely in exchange for work these actors completed for Trickbot operations or for funding services and subscriptions needed for development.
Blockchain analysis like we see above allows investigators to map out all participants in ransomware operations, from the leaders and administrators all the way down to those in supporting roles.
The blockchain is forever
Today’s joint U.S.-U.K. action is a great example of how the inherent transparency of cryptocurrency enables deeper, more comprehensive investigations of organized crime groups than is possible when bad actors use fiat currency. Every transaction is visible on the blockchain for all time — there are no complex networks of banks and shell corporations holding the relevant data — so investigators can more easily map out the financials of the organization and see how all players fit together. In this case, investigators used that information to take action against Trickbot’s developers, and make it clear that no one who participates in ransomware at any level is safe from law enforcement scrutiny.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

