Nearly every important service we interact with — email addresses, social media platforms, bank accounts, cryptocurrency wallets — lives on our smartphones. That means that if a cybercriminal gets control of your phone, they can disrupt your entire life. Unfortunately, SIM swap attacks give them the means to do just that.
What is a SIM swap attack?
A SIM swap attack occurs when a cybercriminal tricks their victim’s mobile phone service provider into porting the victim’s phone number over to a new SIM card embedded in a device the hacker controls. Once this happens, the criminal can use the phone to access the victim’s email, reset all of their login information, and do whatever they want with it. In many cases, not even two-factor authentication can protect victims, since so many people rely on SMS to receive their login codes, which cybercriminals can of course access once they control a victim’s phone. SIM swap attacks are probably most damaging when hackers manage to access their victim’s bank accounts or cryptocurrency wallets, as they can then drain the victim’s money to accounts they control.
Perhaps most concerning is the low level of technical know-how required to successfully carry out a SIM swap attack. All the cybercriminal has to do is convince the victim’s mobile carrier to port their number to a new phone. They can do this by obtaining the victim’s personal details through social engineering, phishing, or even just by purchasing information on individuals who have been compromised in a data breach or other hack. In some cases, mobile carrier employees will port the victim’s number without the hacker providing the necessary personal details, either because they’re fooled or even because they’ve been paid off. Regardless of the specifics, none of these methods requires much skill with computers, meaning nearly any cybercriminal can pull it off with enough motivation.
How prevalent are SIM swap attacks?
It’s difficult to say exactly how many people fall victim to SIM swapping, as many cases go unreported and there’s no central authority tracking this activity. But the data we do have indicates they’re on the rise. The Action Fraud division of the City of London Police reported that known cases in the city rose from 144 in 2015 to 3,111 in 2018. Those 3,111 cases resulted in total victim losses of over £9 million. Things may be even bleaker in parts of the developing world. One bank in Mozambique for instance recently reported an average of more than 17 SIM swapping cases per month. And again, one has to assume that many cases go unreported as well.
While we can’t know the exact number of SIM swapping victims, a recent study from Princeton quantifies how easy they are to pull off. For the study, researchers made 50 total attempts to have employees at five different mobile carriers (ten attempts per carrier) complete SIM swaps that shouldn’t have been authorized, armed each time with varying degrees of authentication information on hand to test how low the carriers’ threshold to wrongly port a number truly is. The researchers were successful in pulling off the SIM swap 39 of those 50 times, and in many cases were only asked to provide the easiest authentication details. The study suggests that customers of major mobile carriers are much more vulnerable to these attacks than they realize.
It’s also worth noting how financially damaging SIM swap attacks can be. In one notable case, a 15-year-old New York high school student successfully SIM swapped a cryptocurrency entrepreneur and stole nearly $24 million worth of cryptocurrency from him, simply routing the funds from the victim’s wallet to those under the hacker’s own control. EuroPol recently brought down a cybercriminal ring that pulled off over 100 attacks to steal over €3 million, with some individual victims losing more than €100,000. Even Twitter founder Jack Dorsey wasn’t safe, as a squad of hackers in 2019 used SIM swapping to take over his Twitter account and send several offensive messages to his millions of followers (no word on any monetary losses). Cybersecurity researcher Brian Krebs has also pointed out that the culprits behind the infamous Twitter Hack in July had ties to the online SIM swapping community.
So, while we can’t say for sure how many people fall victim to SIM swaps in a given year, the data shows that most customers of major mobile carriers are at least vulnerable to these attacks, and that the consequences can be financially devastating.
Case study: Tracking cryptocurrency stolen in SIM swap attacks
As the leading providers of cryptocurrency investigations and compliance software, Chainalysis is often tasked with investigating SIM swap attacks that involve the theft of cryptocurrency specifically. Earlier this year, a victim reached out to us anonymously and asked us to help them recover over $25,000 USD worth of cryptocurrency stolen from them in this way, providing their address at the popular Poloniex Exchange from which their funds were taken, as well as two addresses to which the attacker transferred the victim’s funds. While the victim stopped communicating with us after this initial report, we were able to use the three addresses they provided to trace where criminals moved the victim’s funds using Chainalysis Reactor, our primary investigative tool. You can see those fund movements in the Reactor graph below.
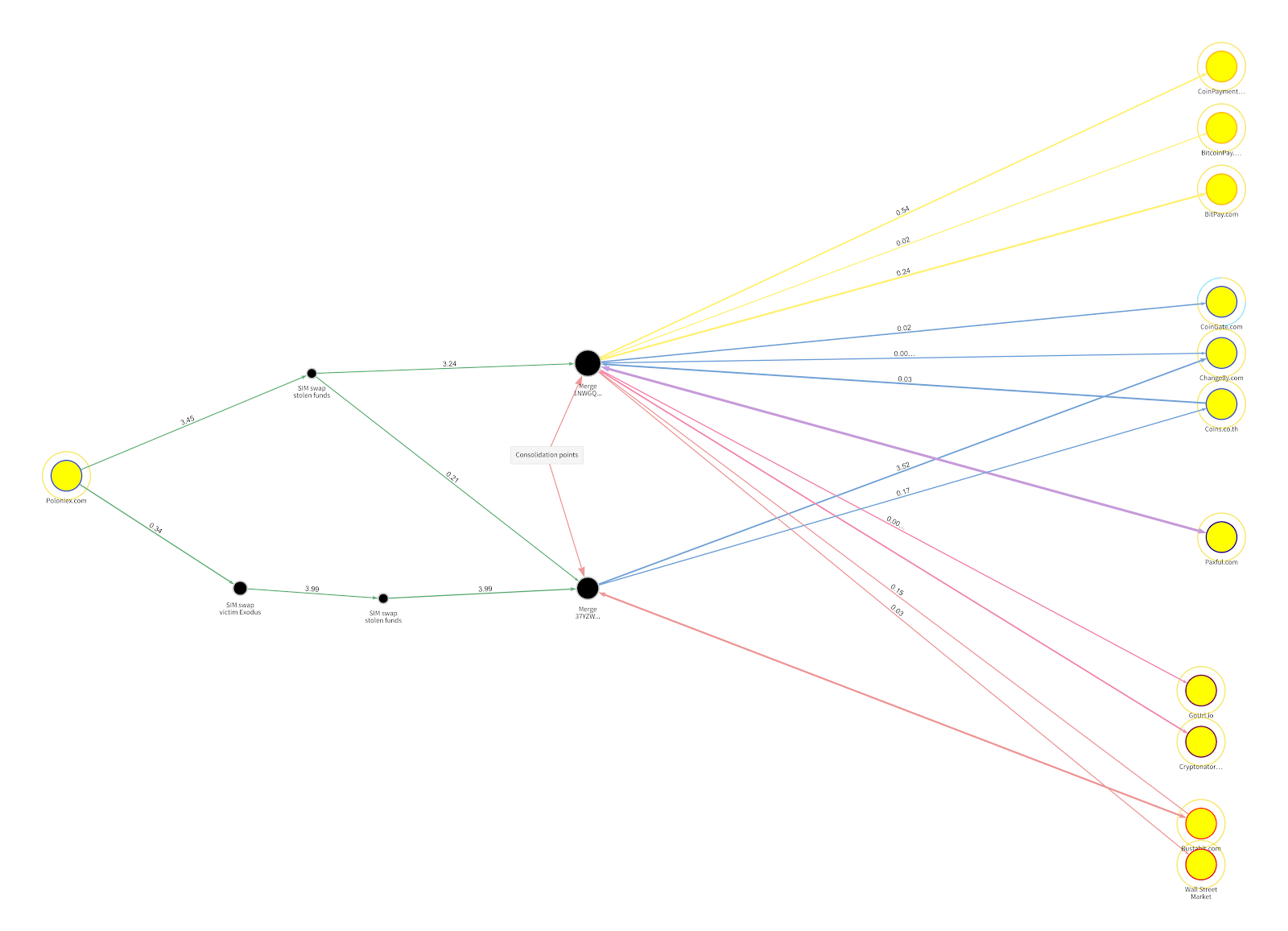
The funds begin in the victim’s wallet at Poloniex on the left-hand side of the screen. The attackers began by splitting the victim’s funds into two groups, which they moved through a series of private wallets before reaching the two that we’ve labeled “consolidation points.” From there, the funds were split further and spread across addresses at 11 different cryptocurrency services: three merchant services providers, three standard exchanges (meaning they generally comply with financial regulations and cooperate with law enforcement), two high-risk exchanges, two darknet markets, and one peer-to-peer exchange. If police were investigating this case, we would likely advise them to subpoena the three standard exchanges and ask them to provide any information they have on those addresses that could identify the attackers.
Compliance professionals and law enforcement must work together to stop SIM swappers
There are steps individuals can take to protect themselves against SIM swapping. Some mobile carriers, for instance, let users opt in to an enhanced security setup that requires them to provide a unique PIN any time they wish to port their number to a new device. We would recommend readers enable this feature if possible, and encourage more carriers to offer it or even consider making it the default setting. We would also recommend not using SMS verification in two-factor authentication. Users should instead use dedicated apps like Google Authenticator or other, more powerful alternatives.
However, as one threat researcher at Flashpoint explained to Wired in a recent article, the unfortunate truth is that in most cases, a determined SIM swapper can successfully attack their target of choice. Individuals following cybersecurity best practices probably isn’t enough to stop these attacks. Instead, compliance professionals in both traditional finance and cryptocurrency, as well as security leaders at mobile carriers, must work together with law enforcement to prevent SIM swapping wherever possible and track down cybercriminals who pull off successful attacks. Chainalysis is eager to help.
Want to learn more about how cybercriminals utilize cryptocurrency? Download our 2020 Crypto Crime Report for original data, research, and case studies on all forms of cryptocurrency-related crime, including scams, exchange hacks, darknet markets, and more.
