The intersection of cryptocurrency and geopolitical conflict has been a growing topic over the last year. From nation state ransomware attacks, to U.S. National Defense Fellow Jason Lowery’s Softwar thesis, many believe that cryptocurrency has a role to play in 21st century warfare. The ongoing Russia-Ukraine War has provided the best example of this to date, with both sides using crypto to solicit donations and finance the war effort. However, we recently discovered what appears to be an example of a more direct, aggressive usage of Bitcoin for counterintelligence, through the unprecedented weaponization of the OP_RETURN field. We’ll explain below.
Mystery Bitcoin user labels nearly 1,000 addresses as Russian government assets in OP_RETURN transactions
It’s no secret that Russian state actors have embraced cryptocurrency. Chainalysis has written in the past about geopolitically motivated ransomware attacks carried out by Russian groups against Ukrainian targets in the leadup to the war, and since the invasion, pro-Russia groups have solicited millions in crypto donations. Additionally, Russia-based cybercrime syndicates like those under the Evil Corp umbrella have suspected links to Russian intelligence.
Under ordinary circumstances, it would be difficult to detect cryptocurrency addresses used by hostile actors unless you were actively looking for them. But starting on February 12, 2022 — weeks before the Russian invasion of Ukraine — and ending on March 14, 2022, an anonymous Bitcoin user sounded the alarm and called out nearly 1,000 addresses they claim belong to Russian security agencies. How did they do it? OP_RETURNs. OP_RETURN is a field used to store data in transactions, effectively allowing users to attach messages to transactions and broadcast them to the entire blockchain, where they’ll be saved forever. OP_RETURNs also mark the transaction’s output as invalid, meaning that any Bitcoin attached to an OP_RETURN transaction is gone forever. In this case, an individual or group sent thousands of transactions to a total of 986 unique Bitcoin addresses, claiming that these addresses were linked to Russian intelligence agencies. Here’s what some of that transaction activity looks like in Chainalysis Reactor.
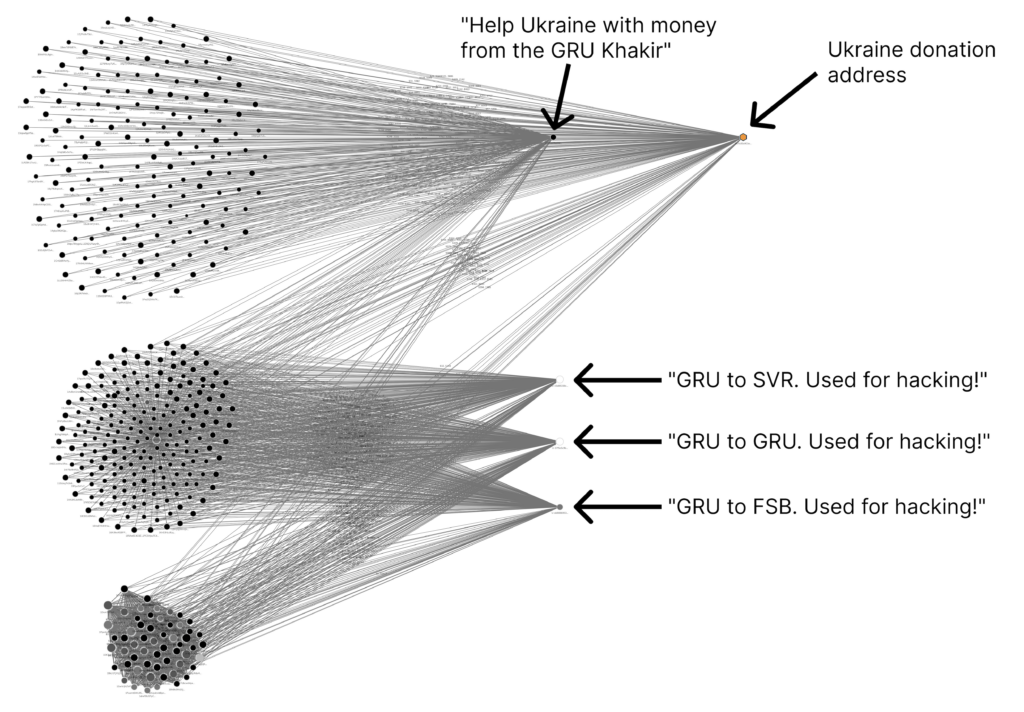
Each transaction contained one of the four following messages, originally written in Russian:
- “GRU to SVR. Used for hacking!”
- “GRU to GRU. Used for hacking!”
- “GRU to FSB. Used for hacking!”
- “Help Ukraine with money from the GRU Khakir”
Each message claims the address in question was used in hacking operations by one of three Russian agencies: the Foreign Military Intelligence Agency (GRU), Foreign Intelligence Service (SVR), and Federal Security Service (FSB). To make things even more interesting, most of the OP_RETURN messages originated from addresses that the OP_RETURN vigilante also said belong to the Russian government in other OP_RETURN messages. Assuming the vigilante’s accusations are true, that would mean this individual accessed the private keys of Russian-controlled addresses, either through hacking or collaboration with an insider. In a series of transactions taking place in April 2022 — a few months after the others, and over a month into the invasion — the OP_RETURN vigilante sent funds held by what they claim to be a Russian-controlled address to a Ukrainian aid donation address, as indicated by the last of the four OP_RETURN messages — we can see that donation address in the upper right-hand corner of the Reactor graph above.
The address 1CMugHhsSf8Bzrp142BpvUynWBR1RiqMCk provides a good example of a case where the OP_RETURN vigilante may have hacked the private keys of Russian-controlled addresses. 1CMug… initially sent OP_RETURN transactions accusing several other addresses of belonging to the Russian government, burning its 0.059 BTC balance in the process (1CMug… initially received those funds in 2020 from an unknown source). Later, 1CMug… received OP_RETURN transactions from other addresses claiming that it too was connected to Russian government operations. Many of the other addresses followed a similar pattern. Assuming the OP_RETURN messages are true, activity like this would indicate that the OP_RETURN sender gained access to the private keys of some GRU addresses, either through hacking or collaboration with an insider.
Do the accused addresses really belong to Russian intelligence and security services?
The value of the analysis above hinges on whether you believe the vigilante’s claims. Anyone can say whatever they want in an OP_RETURN message, but how can we know that the addresses our vigilante tagged really are connected to Russian hacking activity?
We have good evidence for at least three of the addresses. Two of them — 1DLA46sXYps3PdS3HpGfdt9MbQpo6FytPm and 1L5QKvh2Fc86j947rZt12rX1EFrCGb2uPf — are referenced in a now-archived blog post from cybersecurity firm HYAS, in which the firm indicates the Russian SVR utilized the addresses to purchase infrastructure used in the infamous Solarwinds hack.
The third address appears to have been used as part of a Russian disinformation campaign. In the leadup to the 2016 U.S. Presidential Election, Russia’s GRU covertly set up the website DCLeaks.com, and used it to publish hacked materials relating to U.S. political figures. The DOJ indictment against Russian intelligence officers involved in the disinformation campaign states that agents paid in Bitcoin to lease the DCLeaks.com server from a Malaysian web hosting provider. The address used to lease that server — 18N9jzCDsV9ekiLW8jJSA1rXDXw1Yx4hDh — was also tagged by our OP_RETURN vigilante as belonging to the GRU.
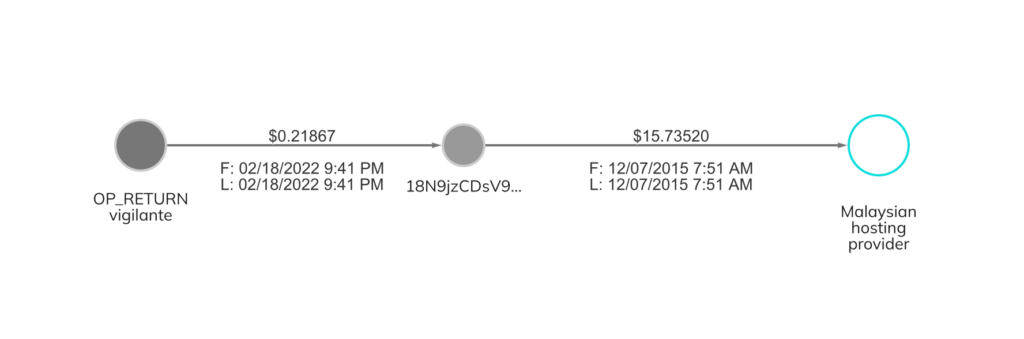
The fact that the OP_RETURN messages appear to have been accurate for three of the addresses lends credibility to the claims against the others as well.
We should also note how much money the OP_RETURN sender gave up to spread these messages. An OP_RETURN is in essence an invalid transaction output, and effectively burns any Bitcoin sent to that output. If one wanted to simply send a message to another person via OP_RETURN, it wouldn’t make sense to include anything more than a dust-sized amount of Bitcoin, since those funds will be rendered inaccessible. However, our OP_RETURN sender included substantial sums in most of these transactions, burning over $300,000 worth of Bitcoin in total. Our hypothesis is that the OP_RETURN sender did this to make the discovery of the transactions, and the accusations associated with them, more likely. The fact that the OP_RETURN sender was both willing and able to burn hundreds of thousands of dollars’ worth of Bitcoin in order to spread their message makes the information potentially more credible. Further, we should emphasize that the OP_RETURN sender stopped burning funds after the Russian invasion was underway. It was at this point that they instead began sending funds to Ukrainian aid addresses, suggesting relatively pure intentions and clarifying their support of the Ukrainian cause.
How does Bitcoin fit into the future of cyber warfare?
It turns out that a public, permanent, immutable ledger isn’t just a strong foundation for a new, transparent financial system. It may also have a role in the future of cyber warfare. Assuming their messages are true, the OP_RETURN sender did something very powerful when they encoded their accusations onto the blockchain. Besides the fact that the Russian government has lost access to those Bitcoin thanks to the OP_RETURN function, it will now be very difficult for Russian agencies to use those addresses for similar purposes in the future, or to fund new addresses with Bitcoin currently held by the accused addresses. The possibility that the OP_RETURN sender acquired private keys for Russian-controlled addresses also suggests that the Putin regime’s crypto operations aren’t secure.
Most importantly, those OP_RETURN messages will be there forever — no government or corporation can take them down. The unique case of the OP_RETURN vigilante underlines how important it is for 21st century militaries and intelligence agencies to understand and utilize blockchain technology, while also compromising their enemies’ ability to do so.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

