This blog is an excerpt of our upcoming mid-year update on ransomware. Sign up here to have the full report emailed to you when it comes out.
Ransomware exploded in 2020 and shows no signs of slowing down nearly five months into 2021.
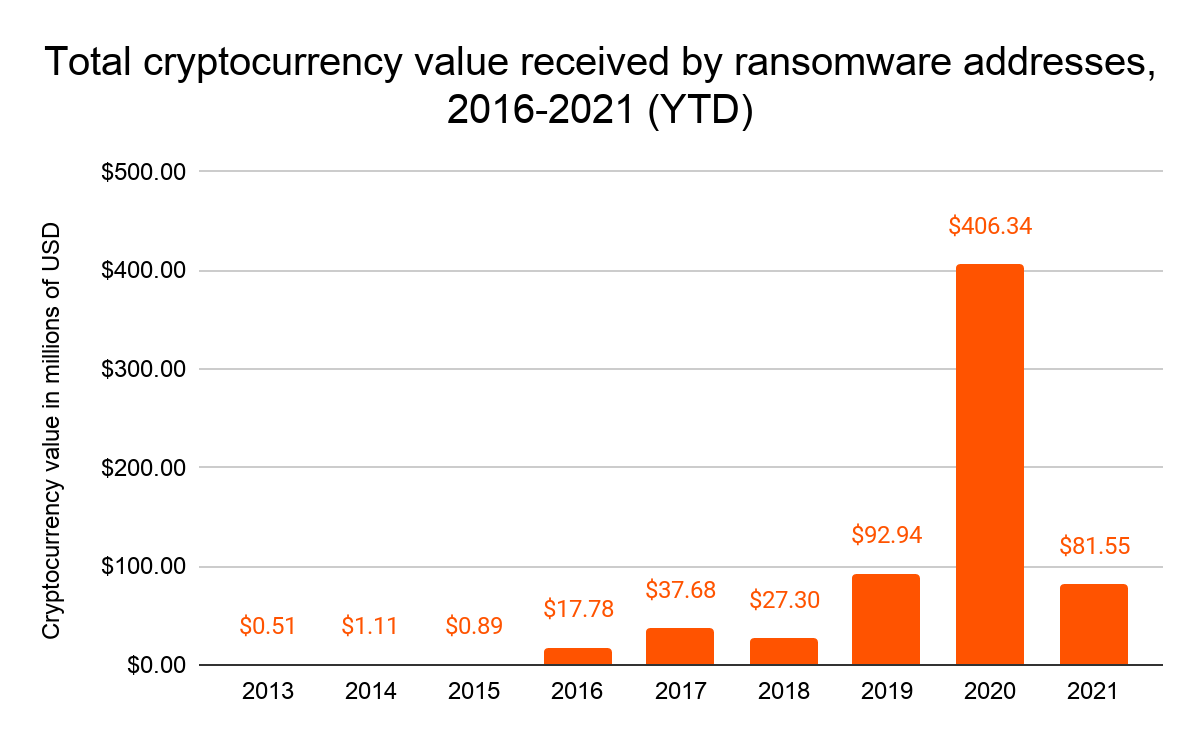
When we published the 2021 Crypto Crime Report in February, blockchain analysis showed that the total amount paid by ransomware victims increased by 311% in 2020 to reach nearly $350 million worth of cryptocurrency. No other category of cryptocurrency-based crime had a higher growth rate. However, we warned readers that that number was likely a lower bound of the true total. Sure enough, since publishing, we’ve identified new ransomware addresses with payments we’d yet to count, and now know that ransomware victims paid over $406 million worth of cryptocurrency to attackers in 2020. Again, that number will continue to grow as we discover more ransomware addresses.
As of May 10, 2021, we know that ransomware attackers have taken in at least $81 million worth of cryptocurrency from victims. Again though, $81 million must be considered a floor for the time being, as the figure will almost certainly grow as we identify more ransomware addresses.
The increase in ransomware starting in 2020 has been driven by a number of new strains taking in large sums from victims, as well as a few pre-existing strains increasing earnings.
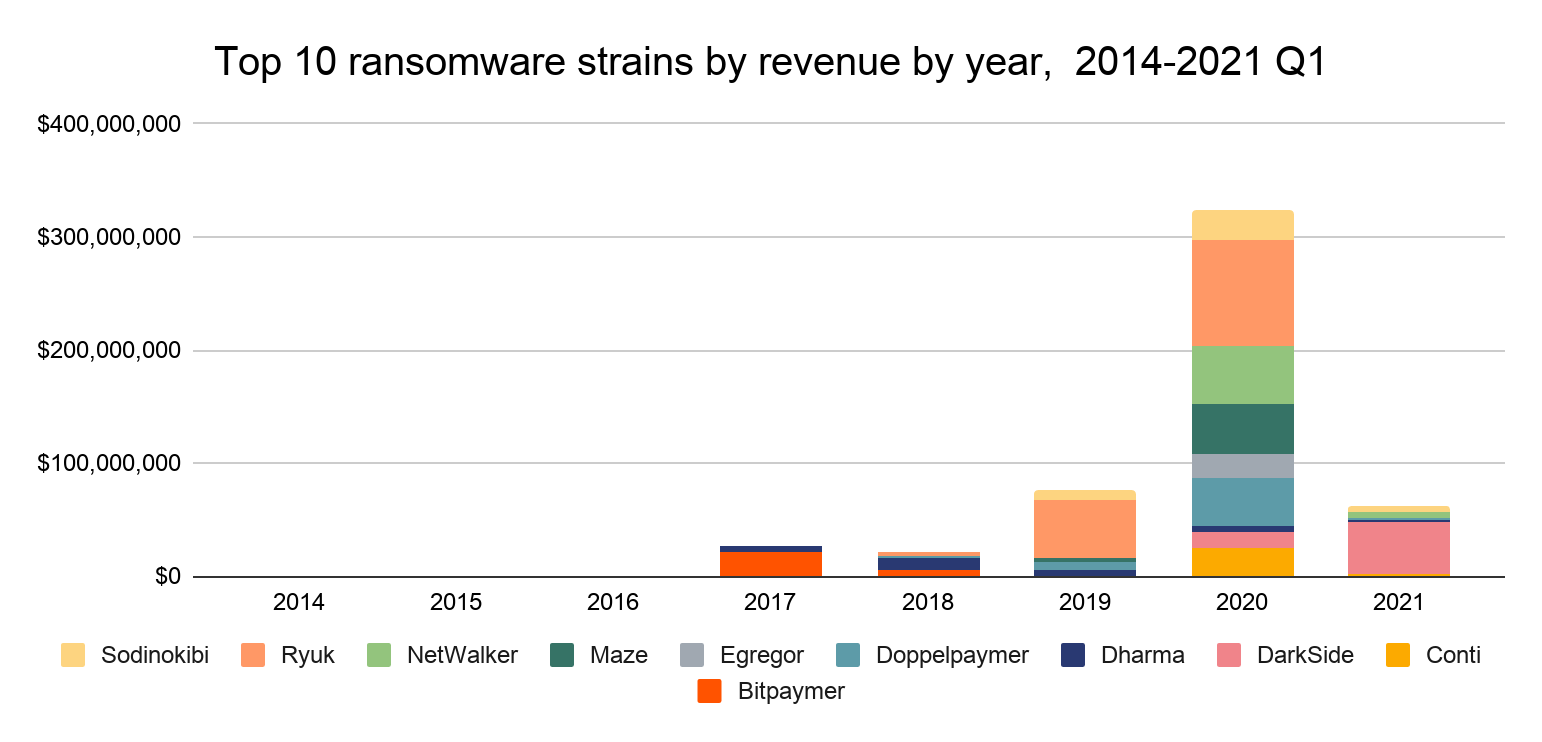
Ransomware strains don’t operate consistently, even month-to-month. Below, we see that the top-earning strains have ebbed and flowed from the beginning of 2020 to the present, based on our current data and address attributions.
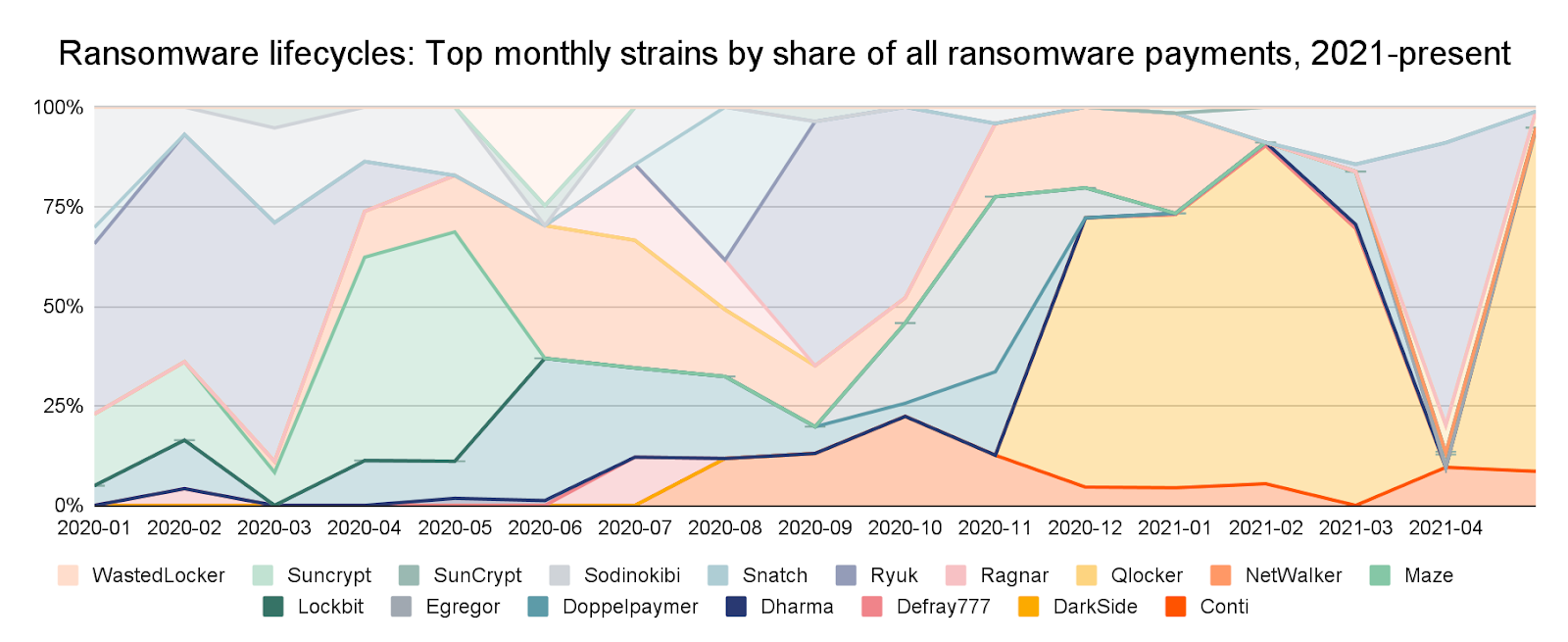
The number of strains active throughout the year may give the impression that there are several distinct groups carrying out ransomware attacks, but this may not be the case. As we explored in last year’s Crypto Crime Report, many strains function on the RaaS model (Ransomware as a Service model), in which attackers known as affiliates “rent” usage of a particular ransomware strain from its creators or administrators, who in exchange get a cut of the money from each successful attack affiliates carry out.
Many RaaS affiliates migrate between strains, suggesting that the ransomware ecosystem is smaller than one might think at first glance. In addition, many cybersecurity researchers believe that some of the biggest strains may even have the same creators and administrators, who publicly shutter operations of one strain before simply releasing a new, very similar strain under a new name. With blockchain analysis, we can shed light on some of these connections by analyzing how addresses associated with different ransomware strains transact with one another.
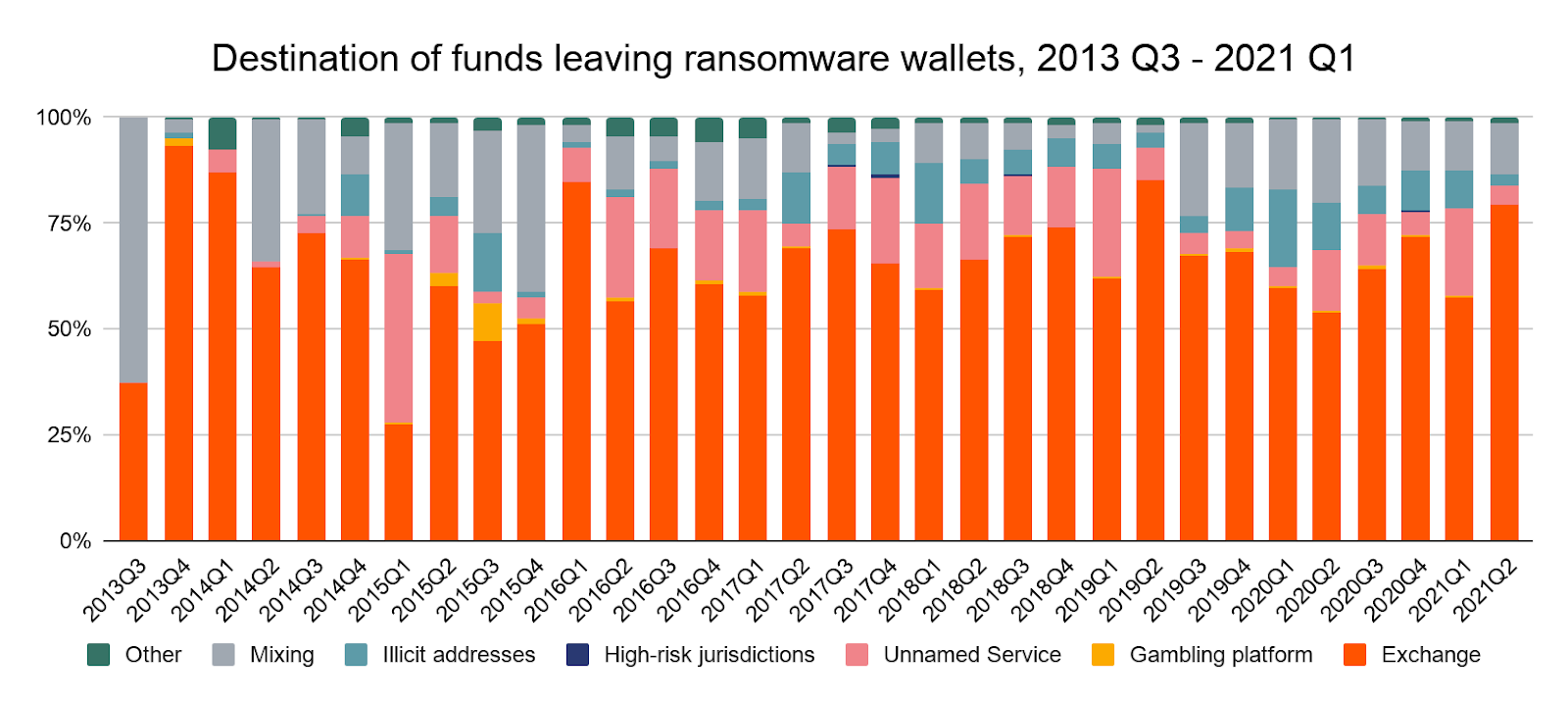
Ransomware attackers move most of the funds taken from their victims to mainstream exchanges, high-risk exchanges (meaning those with loose to non-existent compliance standards), and mixers.
Are illicit third-party data and infrastructure providers enabling bigger ransomware attacks?
One key trend we’ve observed starting in 2020 is the drastic growth in the size of the average known ransomware payment.
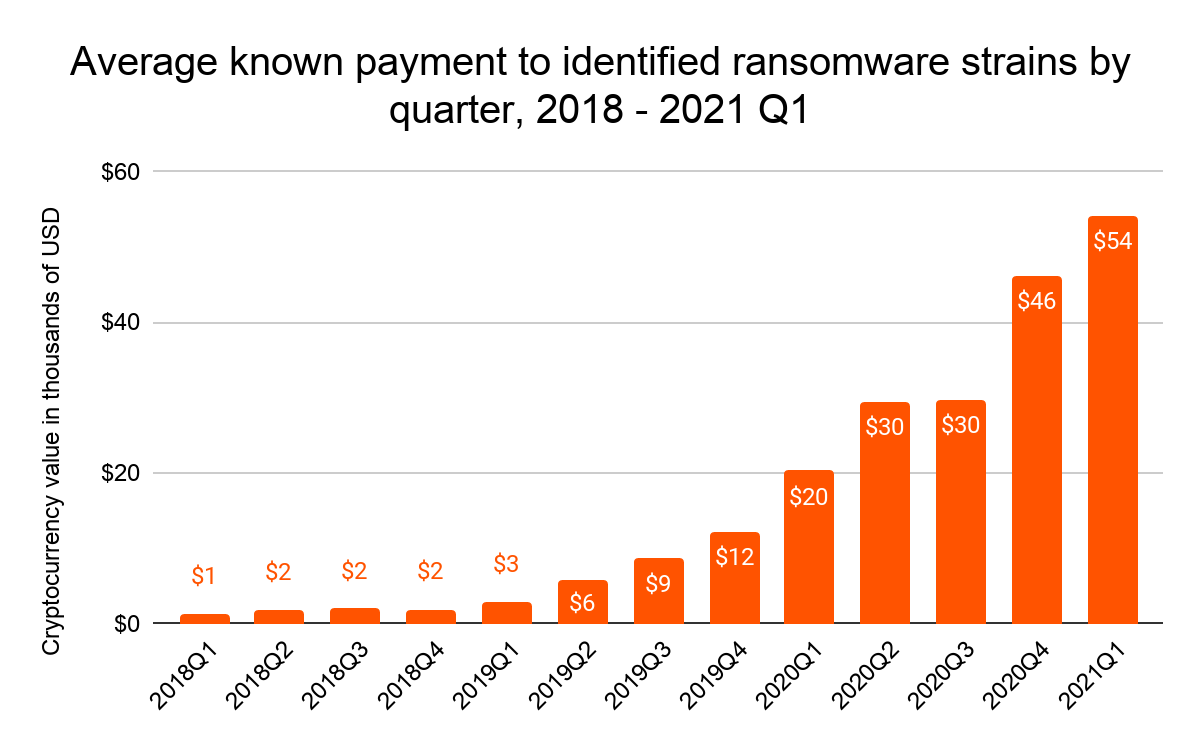
The average known ransomware payment has more than quadrupled from $12,000 in Q4 2019 to $54,000 in Q1 2021. News stories have highlighted much larger outlier ransoms, such as the $50 million ransom payment that REvil demanded from computer parts manufacturer Acer earlier this year, though it’s unclear if Acer paid. While we’ve yet to observe payments of that size, the largest observed ransom payment per quarter has grown substantially over the last two years.
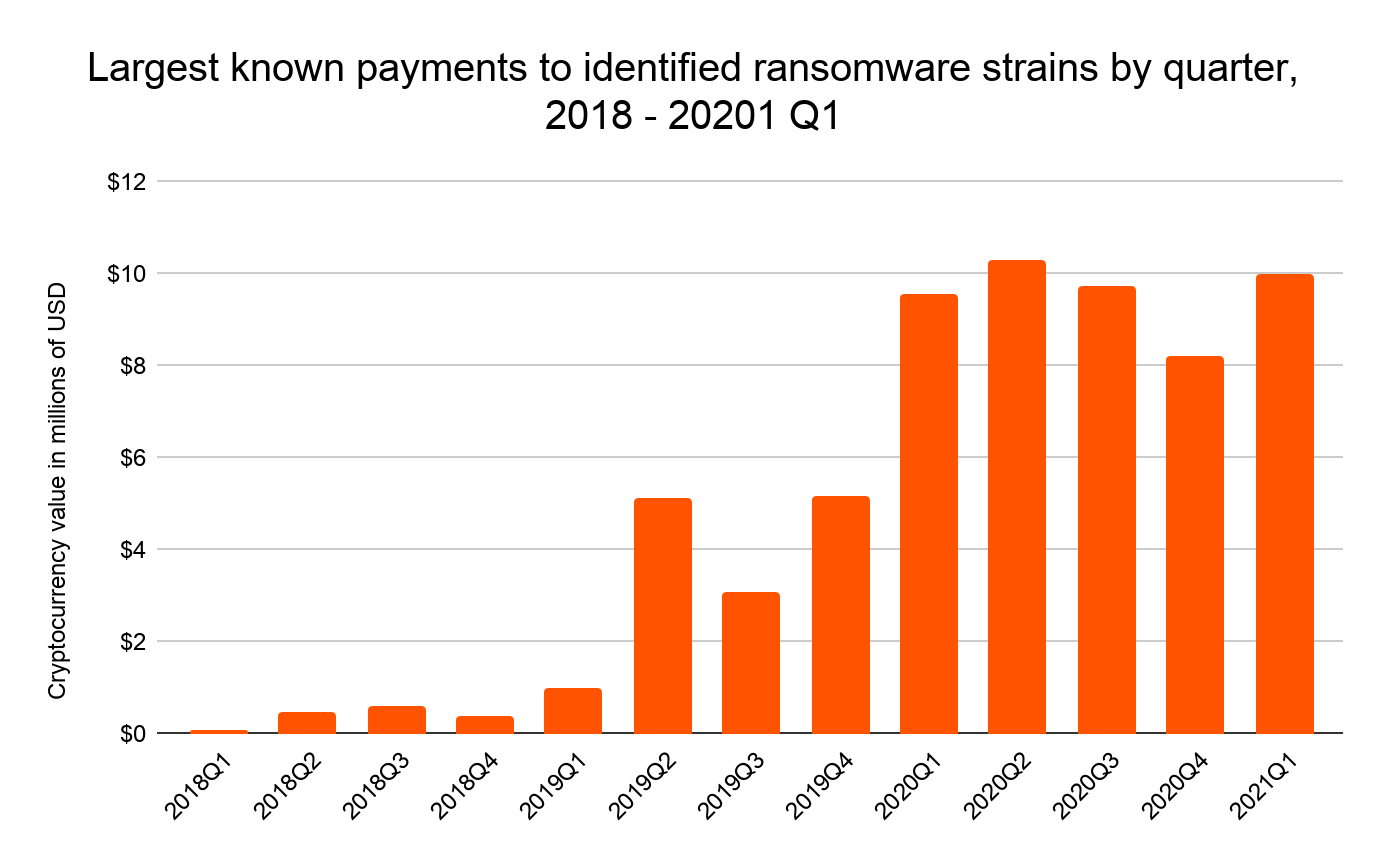
Prior to Q1 2020, we never saw a ransomware payment above $6 million, but since then have seen at least one per quarter.
These rises in ransom payment sizes coincide with an increase in payments from ransomware addresses to other illicit addresses associated with ancillary ransomware services.
Illicit third-party services refer to a number of providers, some of whom operate explicitly as criminals, who can help cybercriminals carry out larger, more effective attacks. These tools, many of which are available on darknet markets, include:
- Infrastructure as a Service providers. Ransomware attackers need cyber infrastructure such as bulletproof web hosting, domain registration services, botnets, proxy services, and email services to carry out attacks. Additionally, many rely on cloud hosting and other forms of infrastructure to carry out data exfiltration attacks, which refers to a new strategy in which ransomware attackers leak data stolen from victims in an effort to force faster and larger payments. We see an example of this in the ongoing attack on the Washington, D.C. police force, reportedly by the ransomware group Babuk. Babuk has released the personal information of several D.C. police officers since the attack began in order to put pressure on the department.
- Hacking tools and access providers. Ransomware attackers may purchase network access to victims who have already been compromised under a framework known as Access-as-a-Service. Others will buy tools to help them break into victims’ networks themselves. One example is exploit kits. Exploit kits scan for vulnerabilities to establish an initial foothold on the network or deploy a payload like ransomware. These exploits make it possible for ransomware attackers to go after larger organizations with more advanced cybersecurity, who can typically afford higher ransoms than less sophisticated organizations. Another example would be malware as a service, which allows cybercriminals to lease software to distribute ransomware more effectively.
- Fraud shops. Fraud shops also play an important role in ransomware operations. Fraud shops are a subset of darknet markets that sell stolen data, including passwords and personally identifying information (PII) for many individuals, and even compromised RDP credentials used to gain access to a victim’s network. Similar to the exploits and access described above, this information can help ransomware attackers break into victims’ computer networks.
- Post-attack services: Some Ransomware and RaaS have adopted enhanced methods of extortion, such as hiring underground call centers to call victims directly, and layering in DDoS attacks on victims refusing to pay, likely leased through DDoS-as-a-Service providers. Ransomware administrators are even paying for salaried employees to help victims through the ransom payment process, including professional negotiators.
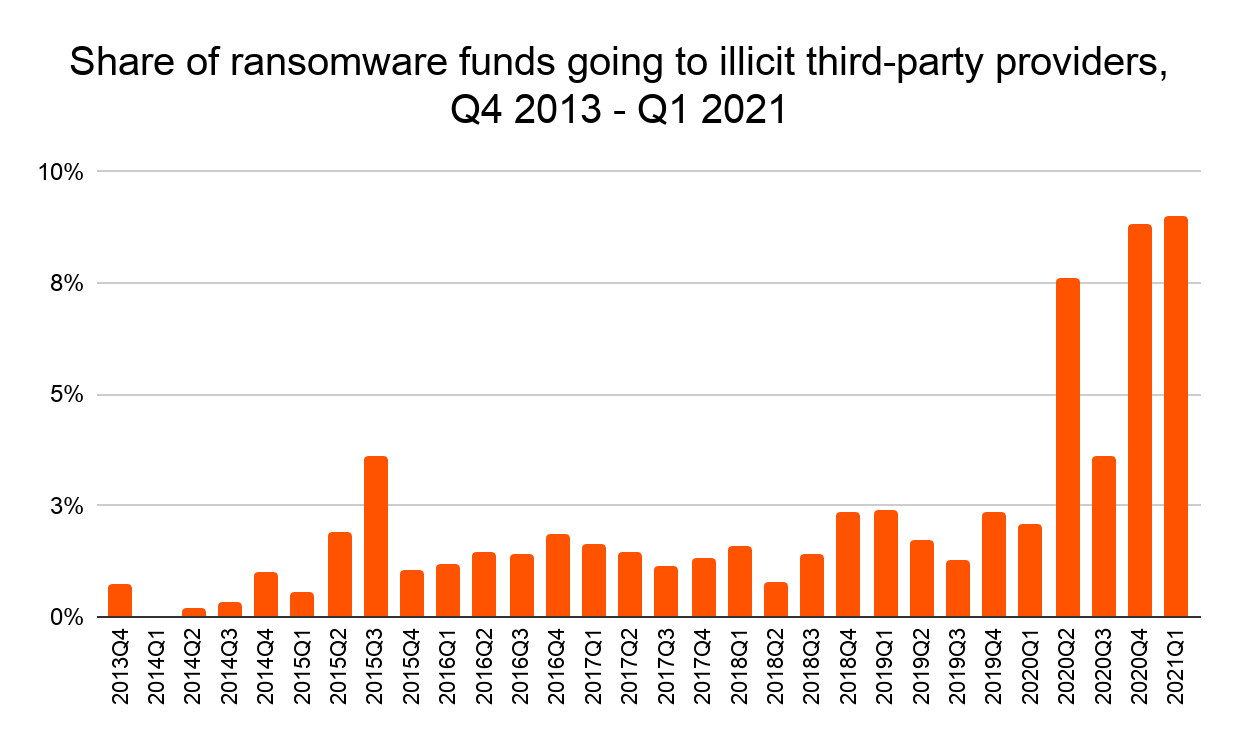
Prior to 2020, illicit third-party services rarely accounted for more than 3% of funds sent from ransomware addresses. Since then, they’ve increased significantly, often accounting for as much as 9% of spending. Keep in mind too that from 2020 on, the raw total of funds sent from ransomware addresses has increased significantly, meaning these figures represent significant increases in dollars spent on illicit services by ransomware attackers.
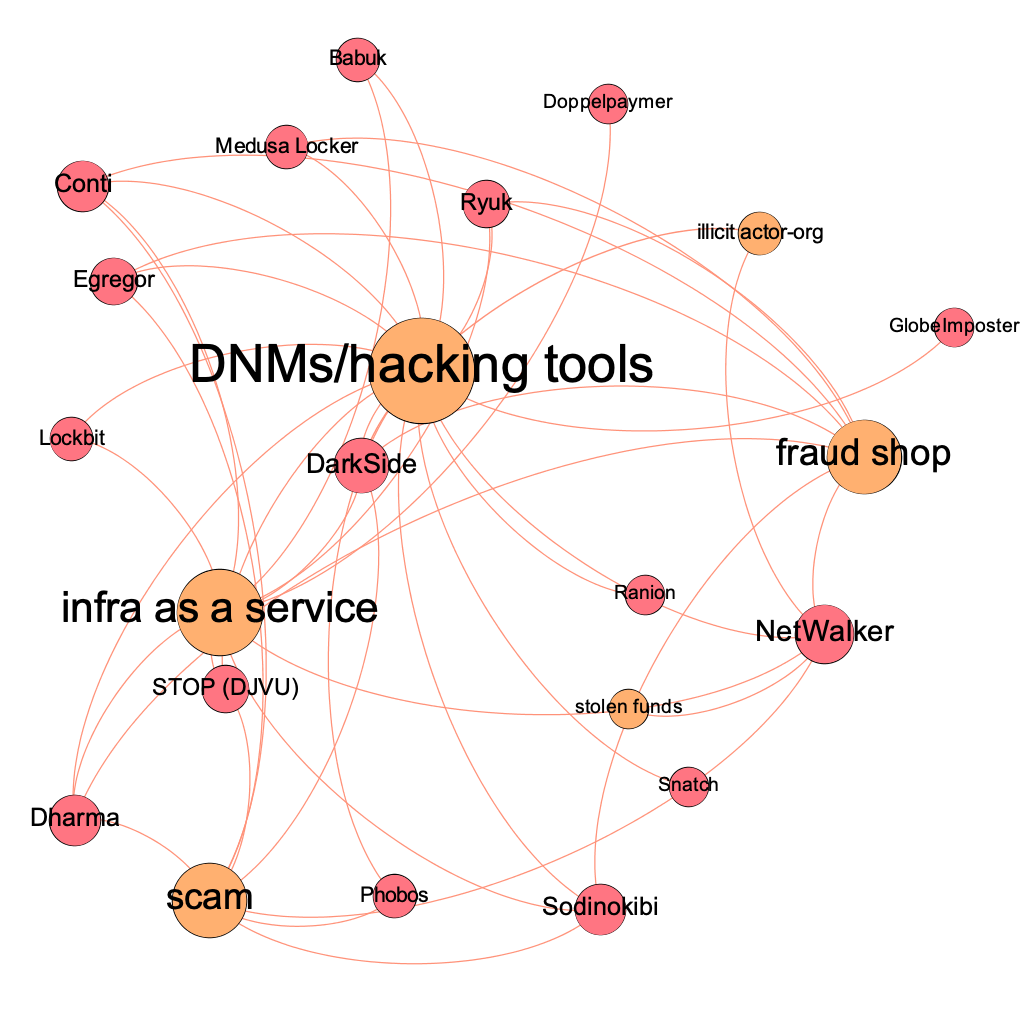
All of these third-party vendors enable ransomware attackers to target bigger organizations more effectively, and their increasing usage could be one reason for the higher ransom payments we’ve been seeing since 2020. Blockchain analysis reveals that these illicit service providers have become the connective tissue of the ransomware ecosystem. In the network chart below, for instance, we show how different types of providers in the aggregate connect many of the most prolific ransomware strains based on cryptocurrency transaction history.
The Chainalysis Reactor graphs below provide more granular examples of this phenomenon. In the first, we see multiple ransomware strains sending funds to a popular bulletproof hosting provider.
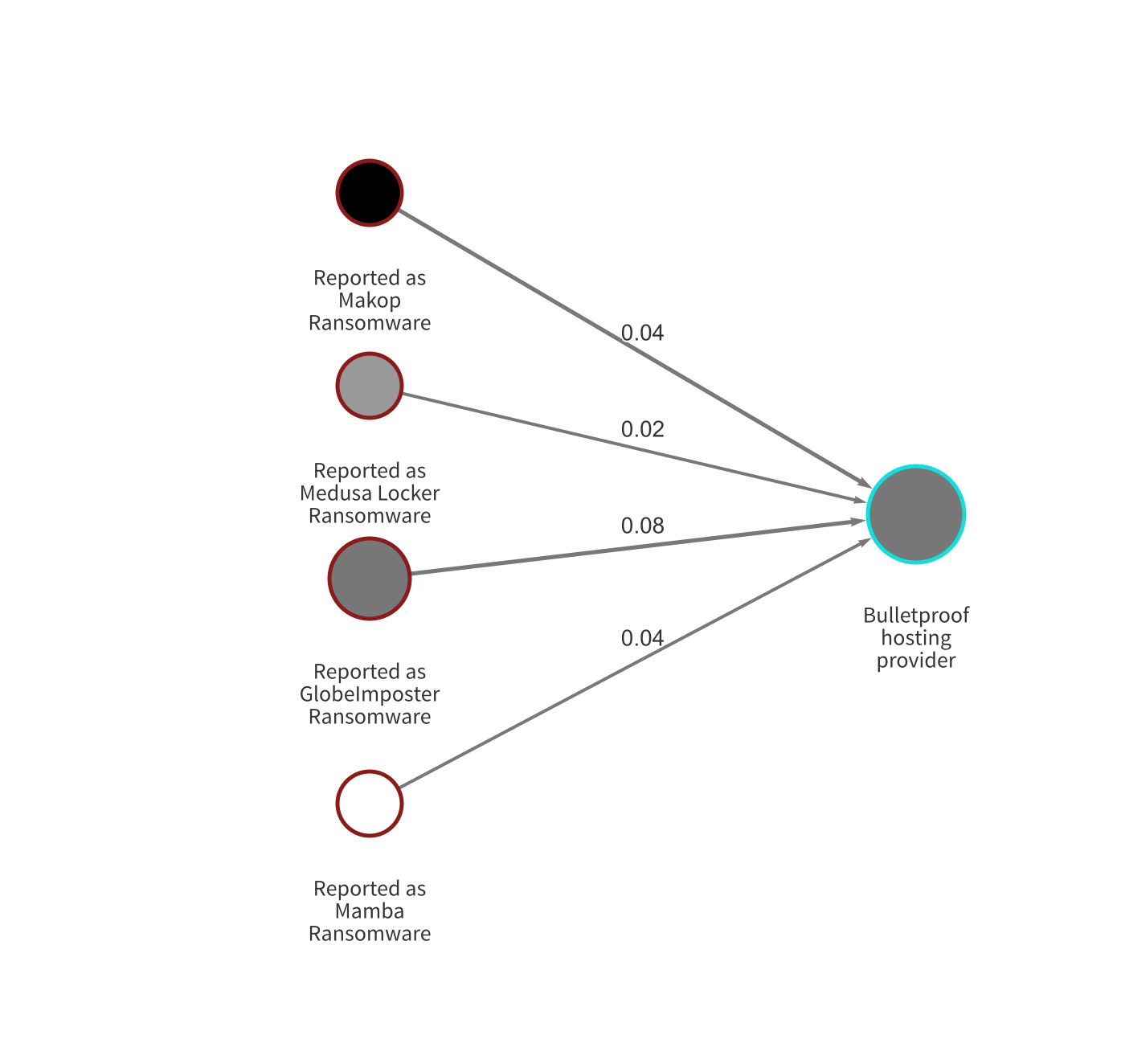
In the second, we see other strains transacting with two Malware as a Service providers.
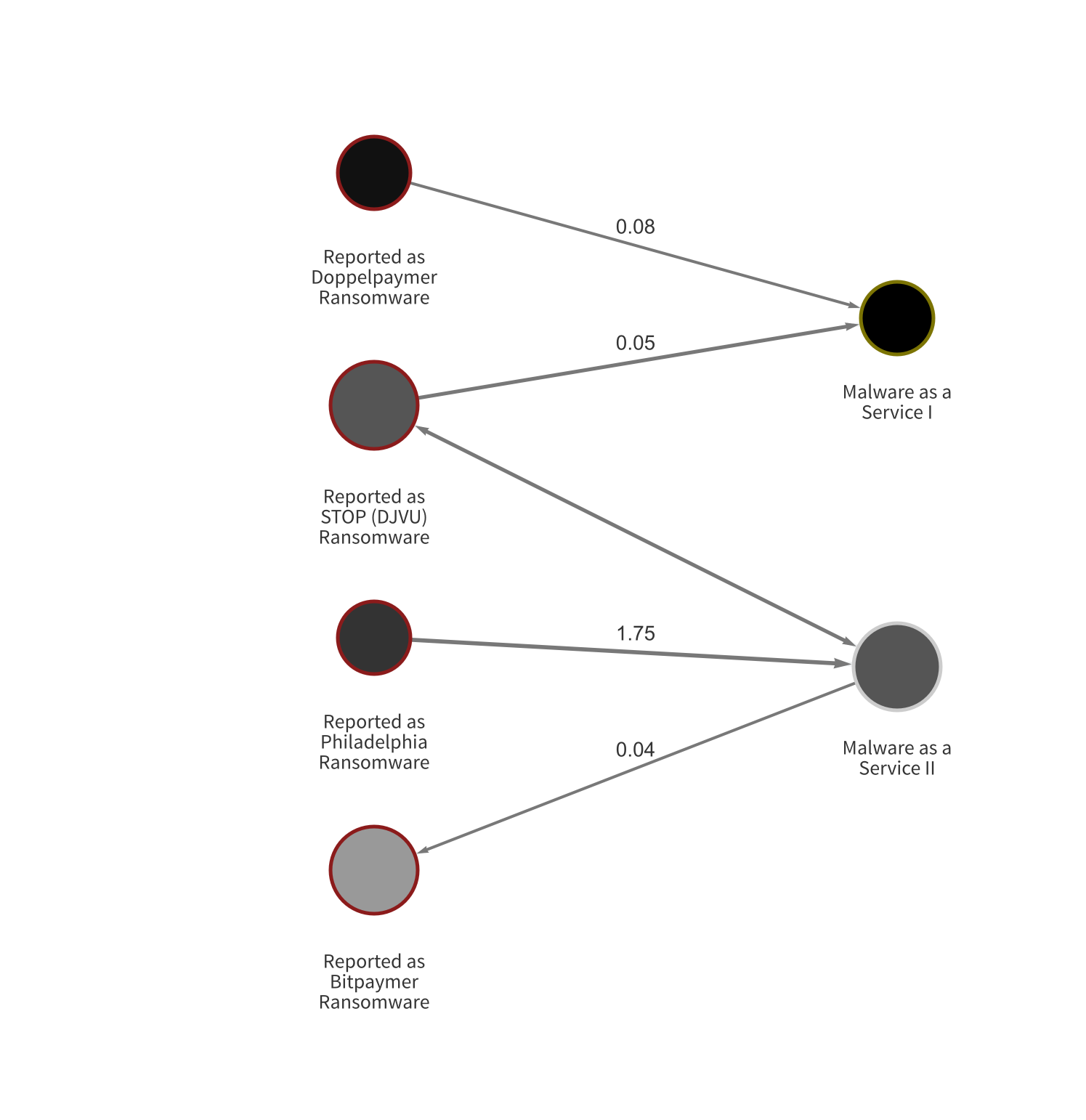
If ransomware attackers continue to have access to advanced infrastructure and tools provided by third-party vendors, we expect ransom payment sizes to continue increasing. Law enforcement and cryptocurrency businesses must work together to take down not just the attackers themselves, but also the providers of tools facilitating attacks.
More ransomware attacks from Russian-affiliated cybercriminals
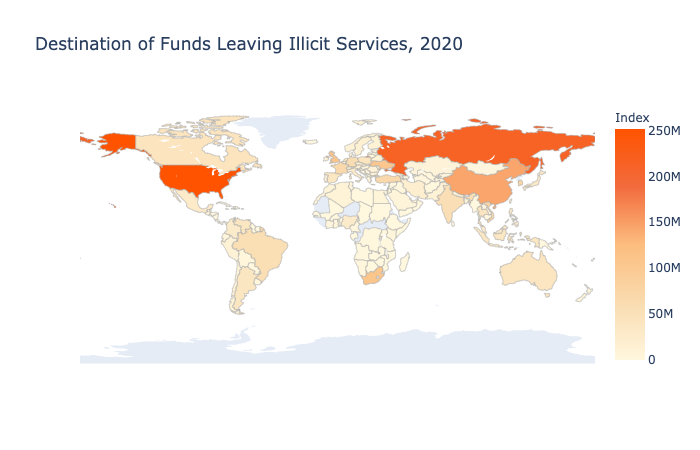
As we covered above, many ransomware strains are associated with sanctioned cybercriminal groups based in or affiliated with Russia, such as the notorious Evil Corp, whose leadership reportedly has ties to the Russian government. Generally speaking, cybercriminals affiliated with Russia and other Russian-speaking countries in the Commonwealth of Independent States (CIS) — an intergovernmental organization of former Soviet countries — have been among the most prolific in the world. Russian-affiliated services received more cryptocurrency from illicit addresses than those in any other country, suggesting that Russian-affiliated cybercriminals were the year’s biggest financial beneficiaries of cryptocurrency-based crime. Much of this activity was driven by Hydra, a Russia-based darknet market, which in addition to drugs sells stolen data that can be useful to ransomware attackers.
In 2021, ransomware strains associated with Russia and other CIS countries are accounting for a larger share of overall ransomware activity. We show this on the graph below by comparing activity in 2020 and 2021 for two categories of ransomware strains:
- Strains associated with Evil Corp.
- Strains with code that prevents encryption if the ransomware detects the victim’s operating system is located in a CIS country. These strains can generally be assumed to have originated in Russia or other CIS countries.
The numbers are clear: Taken together, these ransomware strains are accounting for more activity in 2021 compared to 2020.
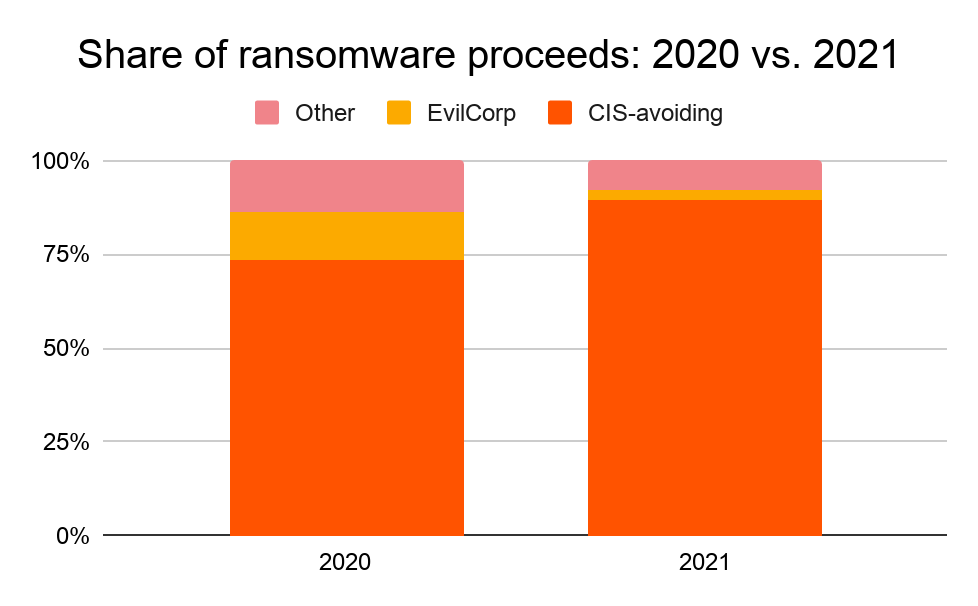
In 2020, roughly 86% of ransomware proceeds studied could be attributed to ransomware strains that are either associated with Evil Corp or are designed to avoid CIS countries. So far in 2021, that figure is at 92%.
The U.S. government is already taking the threat of Russian cybercrime seriously, as President Biden announced several new sanctions against Russian groups and individuals following the SolarWinds hack earlier this year. The data on ransomware specifically suggests that blockchain analysis, as well as collaboration with other firms throughout the cryptocurrency industry, will be crucial to fighting cybercrime from groups aligned with Russia and other hostile nation states.
This blog is an excerpt of our upcoming mid-year update on ransomware. Sign up here to have the full report emailed to you when it comes out. We’ll also be hosting a webinar on mid-year ransomware trends on Tuesday, May 25 at 11am ET.
