Last week, the United States sanctioned several groups and individuals due to their association with disinformation campaigns coordinated by the Russian government. A few of those sanctioned utilized cryptocurrency in their criminal endeavors, and their wallet addresses were included in their entries on OFAC’s Specially Designated Nationals and Blocked Persons List (SDN List). The case is an important reminder of the sanctions risk that exists where adversarial governments take advantage of cryptocurrency, but disinformation campaigns aren’t the only example. As we explore in our 2021 Crypto Crime Report, ransomware attacks can also carry a risk of sanctions violations.
In October 2020, perhaps prompted by the massive uptick in ransomware attacks rocking both the public and private sector, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) released an advisory alert warning that making ransomware payments could be a sanctions violation for victims or companies that facilitate payments for victims. The facilitation point is important, as there’s a robust industry of consultants who help ransomware victims negotiate with and pay ransomware attackers. The alert cited examples of ransomware creators and attackers who have been put on the OFAC sanctions list, such as the two Iranian nationals who laundered proceeds from the SamSam ransomware strain. October’s alert bolsters previous government guidance not to pay ransomware attackers, as this incentivizes future attacks. However, this alert goes a step further in warning that ransomware victims and consultants who help them make payments could face the heavy penalties associated with sanctions violations.
But how big is the sanctions violation risk in ransomware? We looked back at all ransomware payments Chainalysis has tracked since 2016 and calculated the percentage of payment volume that was associated with sanctions risks.
We counted all ransomware payments that meet any of the three criteria below as constitutive of sanctions violation risk:
- Payments to addresses identified by OFAC as belonging to sanctioned individuals (note: this includes payments made before the addresses were actually sanctioned).
- Payments to addresses connected to ransomware strains whose creators have been sanctioned by OFAC.
- Payments to addresses connected to ransomware strains associated with cybercriminals based in heavily sanctioned jurisdictions such as Iran and North Korea.
Those criteria cover the following ransomware strains:
- SamSam: OFAC designated cryptocurrency address.
- Ouroboros: Linked to Iranian actors.
- VoidCrypt: Linked to Iranian actors.
- Sorena: Linked to Iranian actors.
- Pay2Key: Linked to Iranian actors.
- WannaCry 1.0, WannaCry 2.0: Linked to North Korean actors.
- NotPetya: Associated with sanctioned actors in Russia.
- CryptoLocker: Associated with sanctioned actors in Russia.
- Bitpaymer: Speculated to be associated with sanctioned group Evil Corp.
- Locky: Speculated to be associated with sanctioned group Evil Corp.
- Doppelpaymer: Speculated to be associated with sanctioned group Evil Corp.
- WastedLocker: Speculated to be associated with sanctioned group Evil Corp.
- Clop: Disputed, but speculated to be associated with Evil Corp.
Based on those designations, we found that 15% of all ransomware payments made in 2020 carried a risk of sanctions violations. This was quite low compared to some previous years.
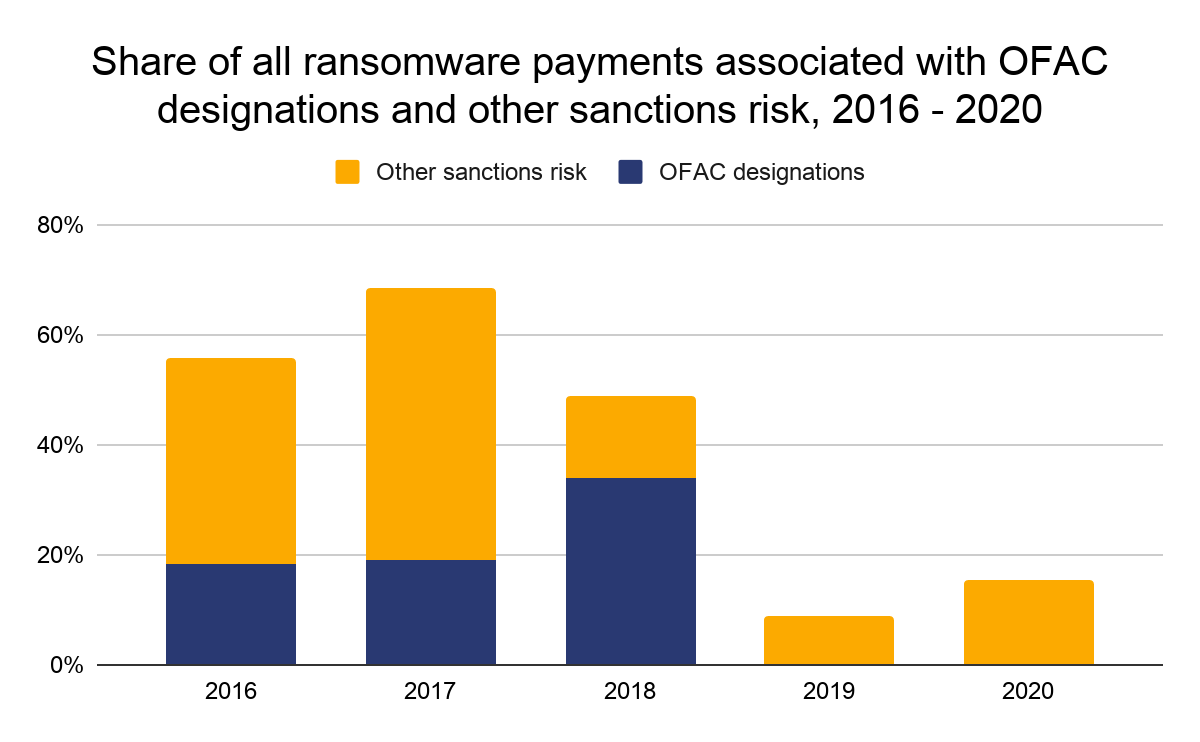
While the rate of sanctions risk in ransomware payments has declined from much higher figures in 2018 and prior, keep in mind how much ransomware payments overall increased in 2020. That means the dollar figure for ransomware payments with sanctions risk skyrocketed last year. Below, we show the yearly volume of ransomware payments that constitute sanctions violation risk, broken down by strain.
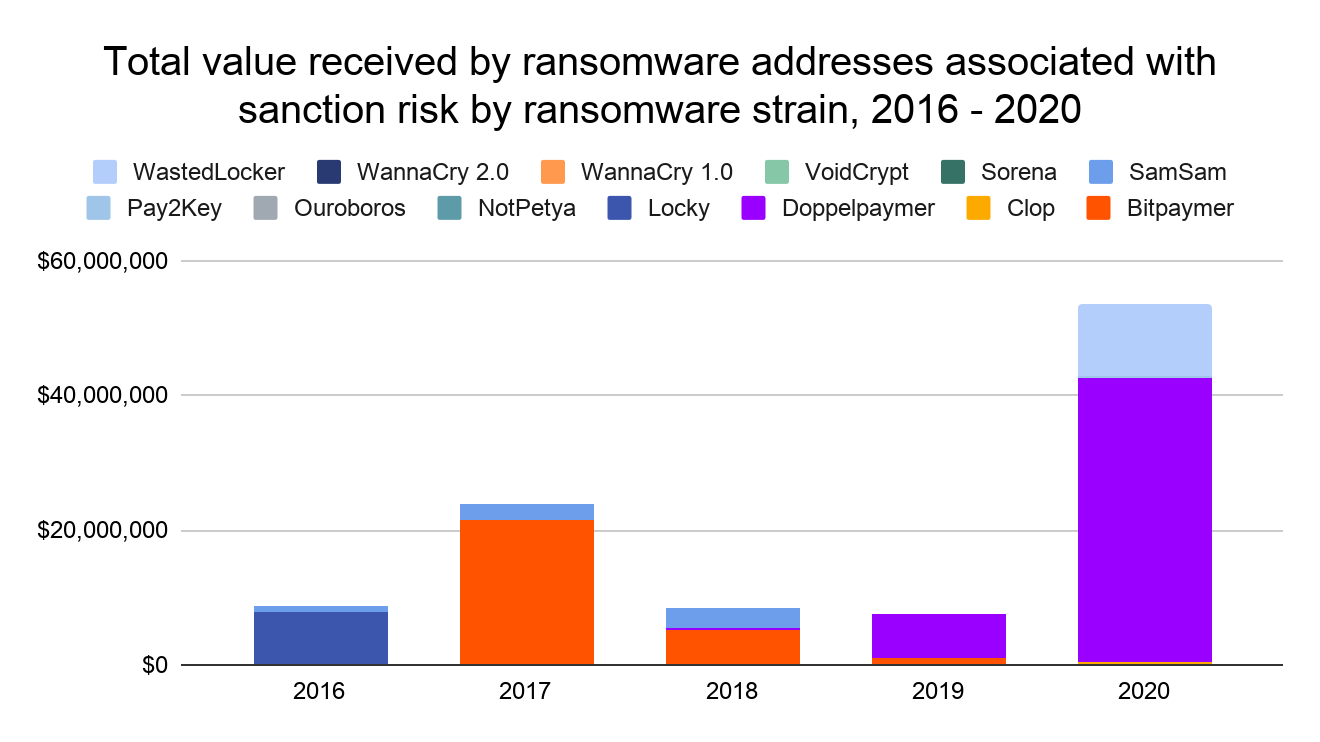
Overall, more than $50 million worth of cryptocurrency that victims paid out to ransomware addresses that we’ve identified carried sanctions risk in 2020, nearly all of which was composed of payments to Doppelpaymer and WastedLocker specifically. In previous years, Bitpaymer, SamSam, and Locky have also been responsible for a high volume of ransomware payments associated with sanctions risk.
It’s also worth noting that exchanges and other cryptocurrency businesses could be at risk for any funds they receive from ransomware addresses in general, but especially those associated with sanctions risk.
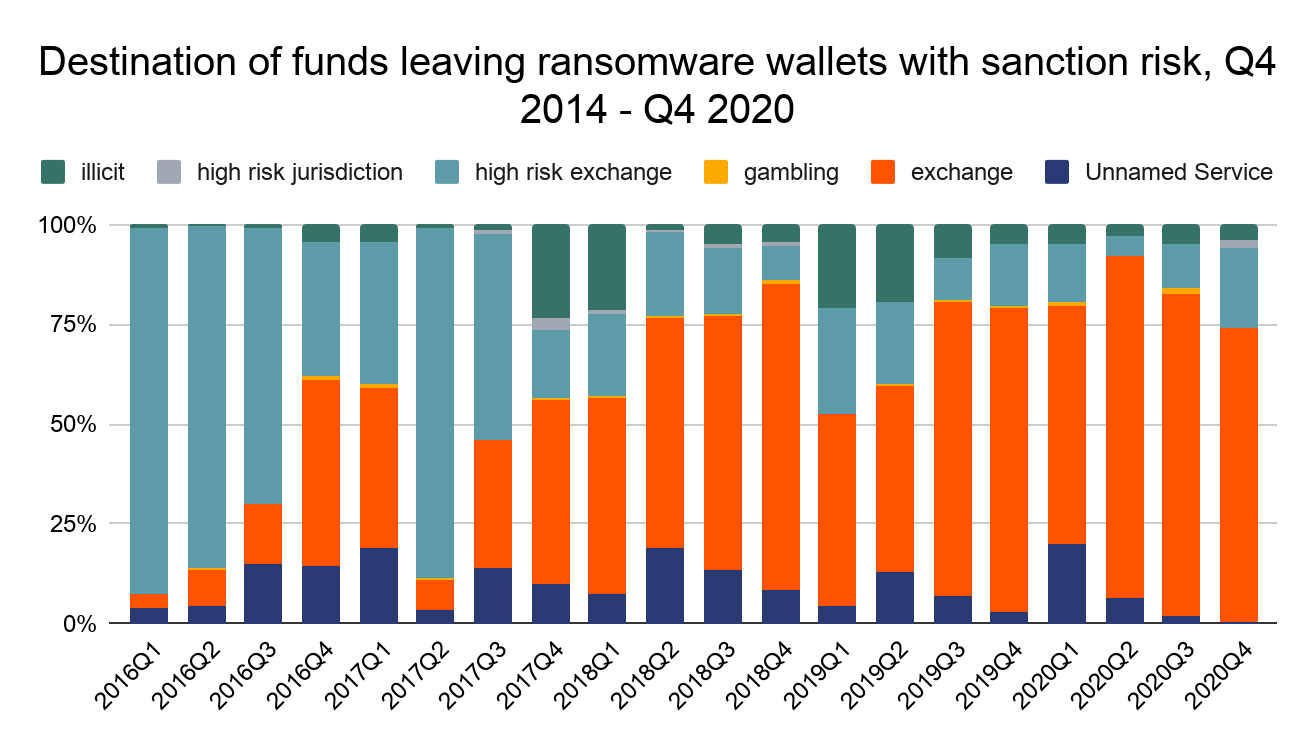
Overall in 2020, mainstream exchanges received more than $32 million from ransomware strains associated with sanctions risks.
Dealing with a ransomware attack is hard enough without victims having to worry about penalties and reputational damage down the line if it turns out they committed a sanctions violation for paying a ransom. We encourage all ransomware victims to work with a lawyer specializing in sanctions and financial crime before paying off an attacker and report the attack to law enforcement.
This blog is an excerpt from the Chainalysis 2021 Crypto Crime Report. Click here to download the whole thing!
