Covid-19 has already had a major impact on cryptocurrency activity, both legal and illegal. Last week, we shared data and analysis on how the pandemic has affected scamming specifically, concluding that while it’s given some scammers new material for fooling victims, it’s caused significant decreases to cryptocurrency scam revenue overall. But while scams make up the majority of criminal activity in cryptocurrency, ransomware may be the biggest concern in this ongoing public health crisis.
Hospitals and other healthcare organizations are a longstanding favorite target of ransomware attackers, as they can’t afford to lose access to vital, often sensitive patient data and therefore are considered more likely to pay up. With healthcare organizations stretched to the limit dealing with Covid-19, ransomware attacks now can be even more damaging.
Given the extra leverage attackers may have against healthcare providers, not to mention other companies feeling pressure from the economic downturn caused by Covid-19, some cybersecurity experts have warned of a possible increase in ransomware attacks. We dug into the data and talked to an expert in the field to learn if those warnings are coming true.
Ransomware payments appear stable so far
The middle of a pandemic is the worst possible time to be hit with a ransomware attack, especially for healthcare providers. So far, the on-chain data suggests ransomware attacks — or, at least, ransomware payments — have decreased significantly since the Covid-19 crisis intensified in the U.S. and Europe in early March.
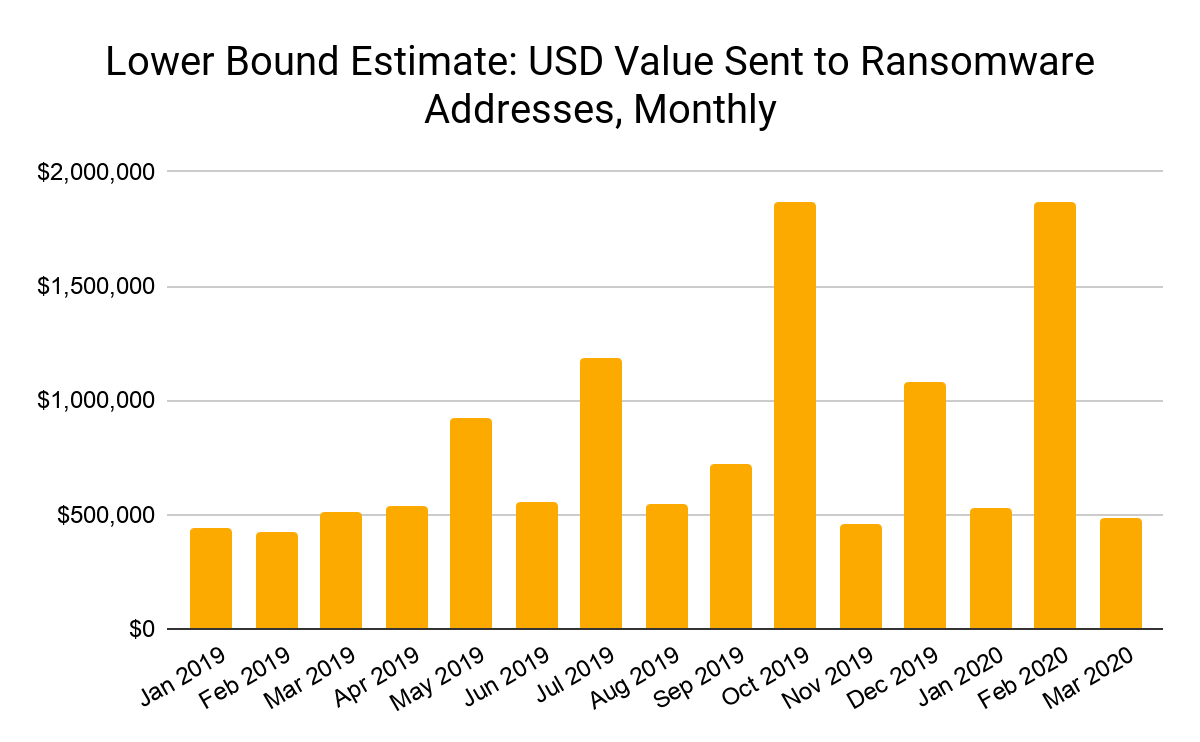
The number of unique active ransomware entities, which we define as a ransomware address or cluster of linked addresses who have received payment in the last month, also dropped significantly in March.
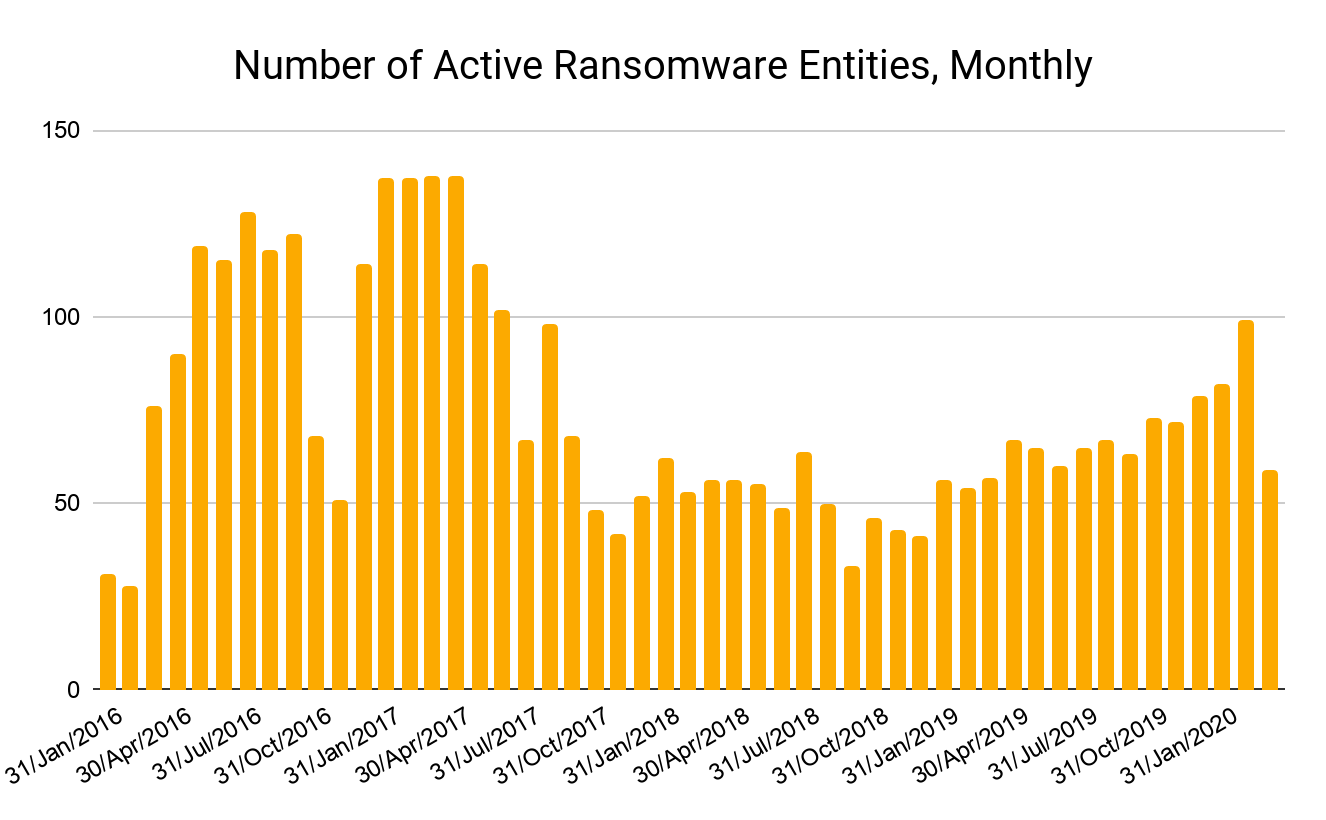
However, we can’t rely on on-chain data to tell the entire story on ransomware. Many businesses simply pay ransomware attackers’ demands and move on without reporting it to avoid revealing that they were victims. If businesses don’t report or otherwise publicize their ransomware attacks, we have no way of tagging the attackers’ addresses as associated with ransomware, skewing the data.
Due to that underreporting, we generally assume aggregated ransomware payment statistics are underestimates. We reached out to Bill Siegel, CEO of Coveware, a ransomware incident response firm, to learn more about the on-the-ground situation and put the on-chain trends we’re seeing in context.
Despite higher stakes and changes in nature of some attacks, ransomware overall hasn’t increased
Bill confirmed what the on-chain data shows at a high level: Covid-19 doesn’t appear to have spurred more ransomware attacks. “I haven’t seen a major material increase in attacks. Healthcare providers remain a frequent target, but the stakes are much higher now,” he said. Indeed, while some ransomware groups indicated they would lay off healthcare providers for the duration of the crisis, this appears not to be true, as ransomware strains like Ryuk were deployed against them in recent days. “More people will probably care if a big hospital is attacked and patient care is impacted, but criminals don’t seem to care.”
So, what has changed? The biggest shift Bill sees is in the phishing emails ransomware attackers use to fool victims into downloading the malware that encrypts their files. “There’s been a gargantuan explosion of phishing emails related to Covid-19. People are getting so many legitimate emails from their employers and vendors about the virus that ransomware attackers have an opportunity to blend in.”
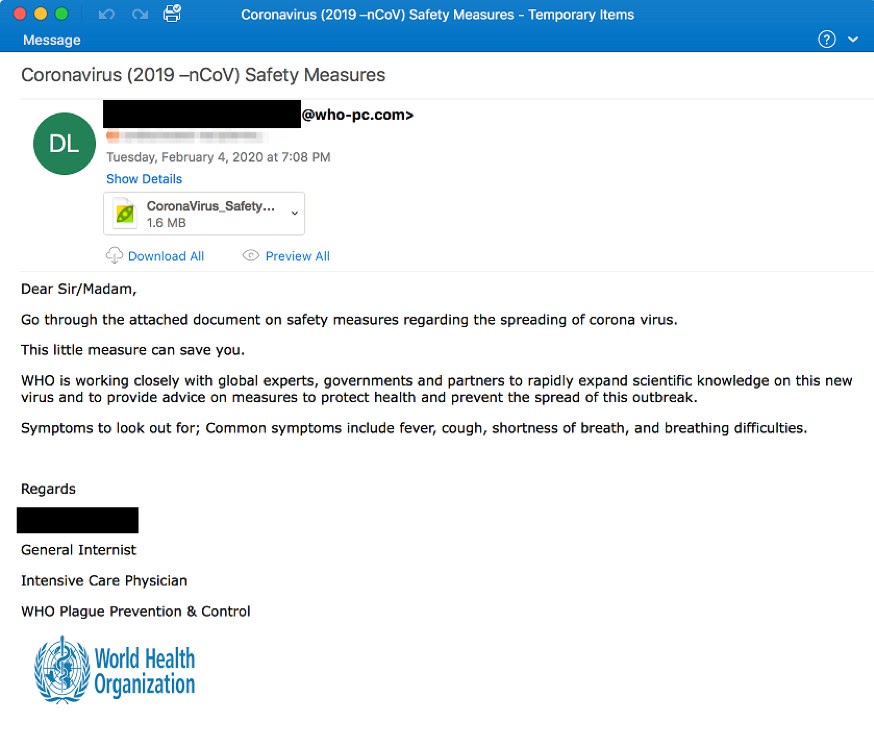
We discussed a similar phenomenon last week when we examined how Covid-19 is impacting cryptocurrency scams. Cryptocurrency scammers are also referencing Covid-19 in their phishing emails; the difference is scammers solicit cryptocurrency “donations” rather than trick victims into downloading malicious software.
Bill also points out that the shift to remote work necessitated by the pandemic opens more opportunities for ransomware attackers. “When people work remotely, they’re using remote desktop protocol more, which has always been the number one attack vector for ransomware.” The move to remote work has opened up schools in particular to increased attacks. “Schools are a common target, but more so in July and August when they’re under pressure to get ready for the new school year. Now that they’re all having to figure out remote work on the fly, they’re being attacked more than they usually would at this time of year.”
Finally, Bill notes that there’s been an uptick in ransomware attacks using a technique known as “Mamba,” which unlike a typical attack doesn’t actually use malware to encrypt the victim’s files. Instead, during a Mamba attack, the attacker simply breaks into the victim’s network, encrypts their files with a commercial encryption software product like Jetico, and withholds the password that can unlock the files. The hacker typically then installs a program to prevent the affected computers from booting up normally and instead delivers a ransom note with an email address the victim can contact to pay up. “We’re not sure why Mamba attacks would be increasing now, but my personal theory is that skilled programmers who’d normally be at work have more time on their hands at home now,” explained Bill.
Which ransomware strains are active during Covid-19?
Based on a combination of blockchain data and public reporting, below is a summary of the ransomware strains that have been especially active during the Covid-19 crisis.
Netwalker
Description: One of the most active strains in targeting healthcare organizations during Covid-19
Attacks during Covid-19 crisis: Attacked Champaign Urbana Public Health District (CHUPD). Attempted to attack hospitals in Spain.
Maze
Description: Group promised not to attack healthcare providers during Covid-19 crisis but has since done so anyway.
Attacks during Covid-19 crisis: Attacked Hammersmith Medicines Research (HMR), a UK-based firm currently testing Covid-19 vaccines. Maze attackers published HMR employees’ personal information when the firm refused to pay ransom.
Doppelpaymer
Description: Group promised not to attack healthcare providers during Covid-19 crisis and appears to have not done so yet. However, the group attacked other firms and leaked sensitive documents in retaliation for non-payment.
Confirmed attacks during Covid-19 crisis: Attacked and has published data stolen from Visser Prevision, a contractor who works with Lockheed Martin, SpaceX, and Tesla.
Ryuk
Description: Ryuk has continued to attack healthcare organizations during the Covid-19 crisis, as confirmed by Sophos researchers and others.
Confirmed attacks during Covid-19 crisis: SentinelOne research head Vitali Kremez says Ryuk has targeted ten healthcare organizations since the Covid-19 crisis began, including two independent hospitals and one group managing nine hospitals. No details on a specific attack have emerged yet.
CoronaVirus
Description: New strain. Its primary goal appears to be information theft rather than ransom generation, according to BleepingComputer. Strain is distributed through fake company posing as a legitimate Windows system utility provider.The name is the only connection to Covid-19.
Confirmed attacks during Covid-19 crisis: No specific attacks or targets confirmed yet.
We will continue to monitor for new attacks, but for the time being, it appears most major ransomware strains remain active and that many continue to target healthcare organizations.
Stay on guard
For the time being, we should be thankful that ransomware attackers don’t appear to be more active than usual. However, for healthcare organizations especially, the stakes of ransomware have never been higher. Organizations need to go out of their way to follow best practices to protect against ransomware attacks, such as backing up files, keeping their security software up to date, and ensuring employees know to verify emails are from a sender they recognize before downloading any attachments.
If you’d like to learn more about how Covid-19 is impacting ransomware, cryptocurrency scams, and other forms of crypto crime, sign up for our latest webinar, airing live on Wednesday April 15 at 11AM ET.
