Yesterday, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) added ten Iranian nationals and two businesses to its Specially Designated Nationals (SDN) List for their role in ransomware and other forms of cybercrime. More specifically, OFAC says the designated entities are associated with Iran’s Islamic Revolutionary Guard Corps (IRGC), a branch of Iran’s armed forces that the U.S. and others have designated as a terrorist organization. Two of the individuals, Ahmad Khatibi Aghada and Amir Hossein Nikaeen Ravari, also had cryptocurrency addresses included as identifiers in their designation. Concurrently, the Department of Justice filed charges against three of the individuals named by OFAC.
This designation marks an important step in the fight against Iran-affiliated ransomware attacks, a growing threat we detailed in our research earlier this year and one in which the Iranian government has likely played a role. The individuals and organizations sanctioned today are also associated with several cyber campaigns cybersecurity experts have long had their eyes on and previously linked to Iranian government actors, including APT 35, Charming Kitten, and Phosphorous.
Below, we’ll explore some of the ransomware activity associated with the entities designated today, and share the cryptocurrency addresses OFAC has attributed to them.
Iranian nationals’ ransomware campaigns extorted $230K in Bitcoin
All six cryptocurrency addresses included as identifiers for the entities sanctioned by OFAC today are Bitcoin addresses. Our analysis suggests that all six were likely used to extort funds from ransomware victims which, according to OFAC, included healthcare providers and schools based in the U.S.
Collectively, these six addresses received over $230,000 worth of Bitcoin between 2015 and 2022. Furthermore, a majority of that Bitcoin was sent to the same place following a successful attack: Nobitex, the largest cryptocurrency exchange in Iran. We can see an example of this on the Chainalysis Reactor graph below.
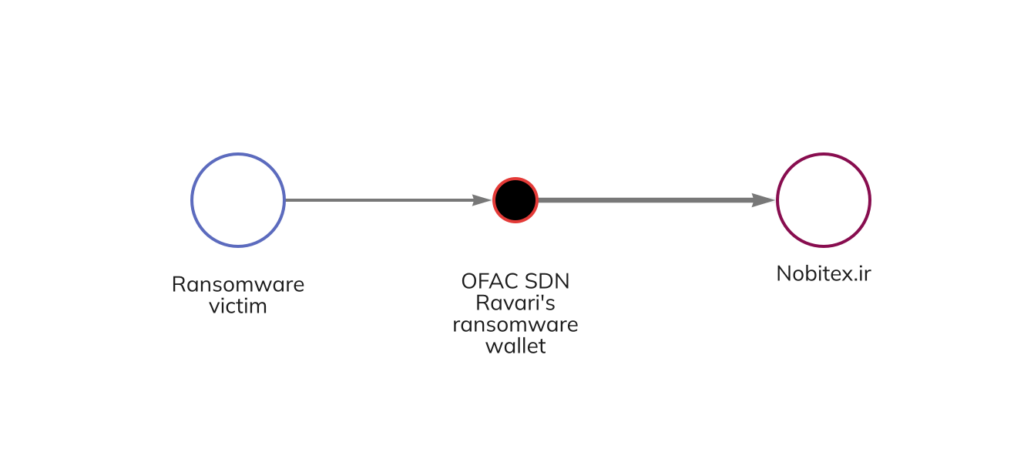
The other addresses identified in today’s designations follow similar transaction patterns.
Iranian nationals’ Bitcoin addresses named in today’s OFAC designation
Below, we list the Bitcoin addresses included in today’s OFAC designation for their malicious cyber activities, grouped by the specific individual with whom they’re associated.
Ahmad Khatibi Aghada:
- 1H939dom7i4WDLCKyGbXUp3fs9CSTNRzgL
- bc1q3y5v2khlyvemcz042wl98dzflywr8ghglqws6s
- bc1qx3e2axj3wsfn0ndtvlwmkghmmgm4583nqg8ngk
Amir Hossein Nikaeen Ravari
- bc1qsxf77cvwcd6jv6j8d8j3uhh4g0xqw4meswmwuc
- bc1q9lvynkfpaw330uhqmunzdz6gmafsvapv7y3zty
- bc1qpaly5nm7pfka9v92d6qvl4fc2l9xzee8a6ys3s
- 1H939dom7i4WDLCKyGbXUp3fs9CSTNRzgL (Note: OFAC lists this address twice, once in association with Aghada and once in association with Ravari — we have therefore included it under both names)
All addresses included in the designation have been labeled accordingly in all Chainalysis products.
Fighting nation state-affiliated ransomware
While DOJ officials pointed out that the ransomware attacks carried out by those designated today were likely conducted “on the side” for personal gain, it’s still significant that individuals connected to the IRGC targeted American critical infrastructure with the tacit approval of the Iranian government. Today’s designations and indictments, as well as the cybersecurity advisory released alongside them, represent a strong step towards stopping Iran-affiliated cyberattacks.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
