On Tuesday, September 21, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) issued an updated advisory on the sanctions risks associated with facilitating ransomware payments and the proactive steps companies can take to mitigate such risks. This advisory expands upon OFAC’s October 2020 advisory, which we wrote about on our blog at the time.
OFAC echoes many key points from the previous advisory, such as the fact that a company facilitating ransomware payments on behalf of a victim – including cryptocurrency exchanges – may violate OFAC regulations. While OFAC stops short of banning all payments, they offer three key updates in this advisory:
- Discouraging Ransom Payments: OFAC expressly advises against paying ransoms, echoing previous government warnings that paying ransoms encourages ransomware attacks.
- Prevention: Improving cybersecurity practices will be considered mitigating factors in the case of a sanctions violation.
- Reporting: Cooperating with OFAC and law enforcement will also be considered mitigating factors and victims can now report to an expanded group of government agencies.
In an effort to increase reporting, OFAC has clarified that if a company reports the incident to law enforcement and fully cooperates with them, as well as takes meaningful steps to improve their cyber security, OFAC will consider this to be a mitigating factor and sanctions violations involving ransomware attacks will likely be resolved with non-public responses, such as No Action Letters or Cautionary Letters, which do not carry monetary penalties.
Chainalysis data shows that ransomware attacks have increased considerably over the past year and a half. Ransomware payments rose more than 300% from 2019 to 2020, when they reached over $400 million worth of cryptocurrency. Based on available data, ransomware attackers show no signs of slowing down in 2021.
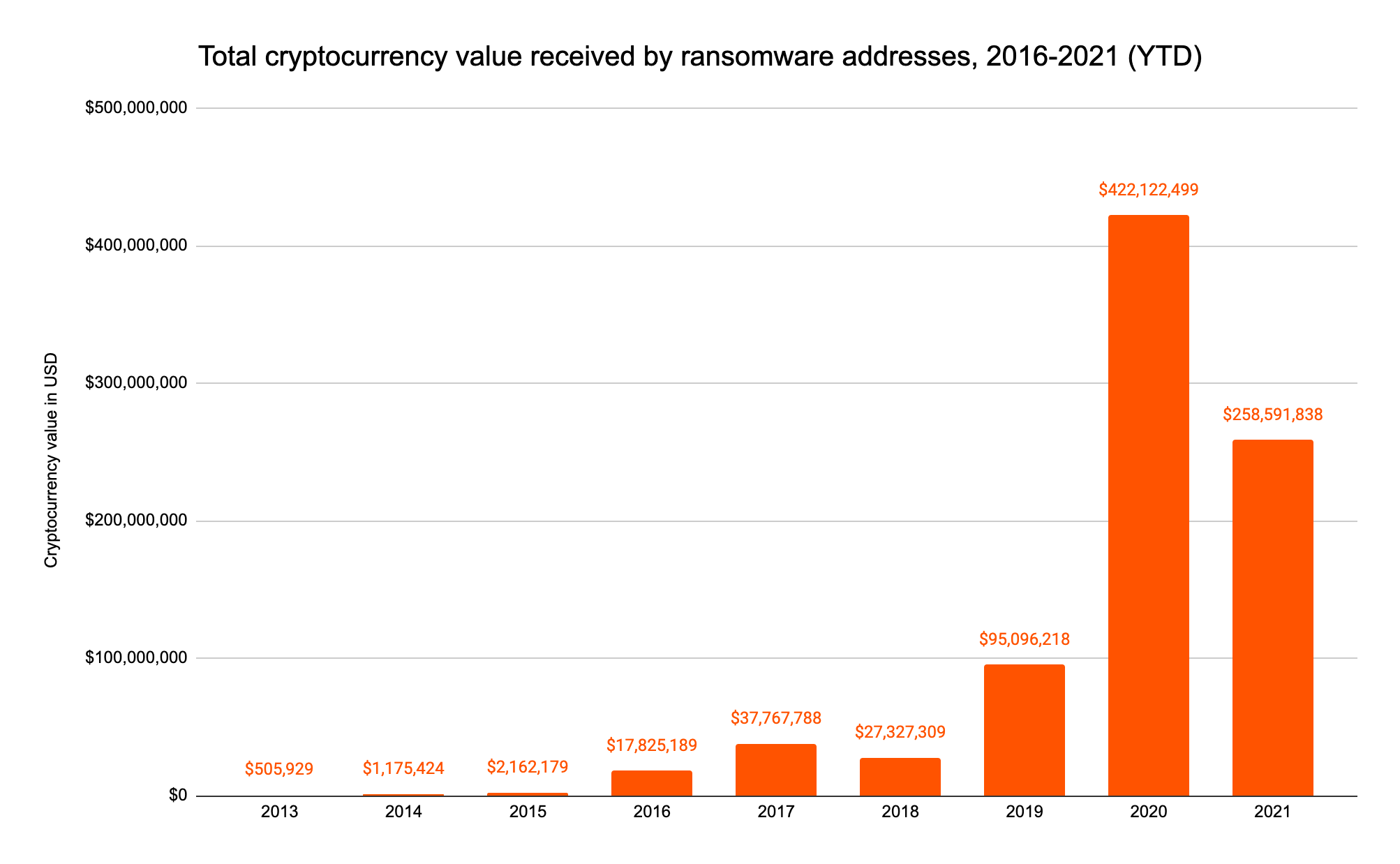
For more information on trends in ransomware, including a breakdown of strains with a sanctions nexus, read our Critical Mid-Year Update.
What OFAC’s advisory means for ransomware victims and cryptocurrency businesses
On Tuesday, September 21, in addition to releasing the updated advisory, OFAC announced that Russia-based cryptocurrency Over The Counter (OTC) broker Suex was designated pursuant to Executive Order 13694 and added to the Specially Designated Nationals and Blocked Persons (SDN) List, thereby prohibiting Americans from doing business with the company. The designation included a number of digital currency addresses as identifiers.
We are proud to share that Chainalysis tools aided in the investigation of Suex; read more about the investigation on our blog.
These designations mean that if a ransomware victim chooses to pay the ransom, they risk making a payment to a designated malicious cyber actor and engaging in a sanctions violation. In its last advisory, OFAC made it clear that ransomware victims and consultants who facilitate ransomware payments could face penalties associated with sanctions violations. While victims can apply for license applications to OFAC, they noted that applications would be reviewed on a case-by-case basis with a presumption of denial.
This means that companies that facilitate ransomware payments to sanctioned malicious cyber actors on behalf of US persons or businesses may result in sanctions violations for those US persons or businesses. In addition, US businesses, such as cyber security companies and cryptocurrency exchanges, may not facilitate ransomware payments to entities or individuals subject to US sanctions on behalf of non-US persons.
OFAC discourages paying ransoms or extortion demands
New in OFAC’s guidance is the explicit recommendation that companies not pay ransom or extortion demands. OFAC cites concerns that companies that facilitate ransomware payments on behalf of victims “not only encourage future ransomware payment demands but also may risk violating OFAC regulations.” Further, ransomware payments may threaten U.S. national security interests by enabling criminals and adversaries with a sanctions nexus to profit and advance their illicit aims. OFAC advises that “the U.S. government strongly discourages all private companies and citizens from paying ransom or extortion demands and recommends focusing on strengthening defensive and resilience measures to prevent and protect against ransomware attacks.”
Improving cybersecurity practices and cooperating with OFAC and law enforcement will be considered mitigating factors
OFAC outlines the factors they will consider in an enforcement response in the case of a sanctions violation, such as a paying ransom to a sanctioned ransomware actor. One of the mitigating factors outlined in this updated guidance is whether a company has taken meaningful steps to improve their cybersecurity practices, thereby reducing the risk of extortion. They specifically cite the cybersecurity practices highlighted in Cybersecurity and Infrastructure Security Agency’s (CISA) September 2020 Ransomware Guide as model steps a business can adopt. This new guidance is an important push for companies to improve their defensive and resilience measures, with the aim of reducing companies’ vulnerabilities to ransomware attacks and decreasing the number of attacks that occur. This will, in turn, reduce the risk of potential sanctions violations that occur when companies face the choice of whether to pay ransomware attackers.
While the October 2020 OFAC guidance had noted that a complete report of a ransomware attack to law enforcement would be considered a significant mitigating factor in determining enforcement actions in the case of sanctions violations, this updated guidance goes into much greater depth about what level of cooperation is sought and how OFAC will take this cooperation into consideration. For example, OFAC specifically states that they want reports of ransomware attacks to be made as soon as possible after the attack, self-initiated, and complete, and that reports may be made to law enforcement or other relevant U.S. government agencies, including CISA or the U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure Protection (OCCIP).
The clarification that sanctions violations will likely be resolved with non-public responses if companies cooperate with law enforcement is important because many companies have been reluctant to report ransomware attacks to law enforcement for fear of the reputational harm that might come to them if the attack became public. This has resulted in underreporting around ransomware attacks and without this information, law enforcement does not have the full picture of the ransomware ecosystem and cannot adequately prioritize and investigate ransomware actors. Improving law enforcement’s data around ransomware attacks is key to combating this threat.
Victims can report to an expanded list of government agencies
OFAC provides an expanded list of agencies victims can turn to in the case of a ransomware attack, payment, or any potential sanctions nexus in order to receive voluntary disclosure credit, and strongly advises all victims and those involved with addressing ransomware attacks to report the incident. They note that the sooner that incidents are reported, the more likely victims are to recover access to their data, and that by reporting attacks, victims provide “critical information needed to track cyber actors, hold them accountable, and prevent or disrupt future attacks.”
By providing more potential resources and highlighting the advantages to victims of reporting ransomware attacks, hopefully more victims will be encouraged to come forward and report incidents, which will allow for a more comprehensive picture of the threat and better equip law enforcement in their investigations.
How Chainalysis can help you mitigate your sanctions risk
In the event you’re attacked, or working with a customer who was attacked, you should collect as much evidence as possible, such as screenshots of ransom messages you receive, and send it to the appropriate government agencies so they can learn what strain of ransomware you’ve been hit with and start formulating a response. Because effort is measured in relation to possible violations, you should work directly with law enforcement, OFAC, and FinCEN.
Chainalysis KYT customers should set alerts to be notified if their users receive or send ransomware payments and report them to their regulators and law enforcement when applicable. For more information on how to set KYT alerts, see our Knowledge Base here.
