On May 23, 2023, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) and South Korea’s Ministry of Foreign Affairs (MOFA) announced sanctions against several entities and individuals associated with illicit North Korean revenue generation schemes.
Three North Korean organizations were sanctioned for their role in North Korean hacking activity, including the 110th Research Center and its parent agency, the Technical Reconnaissance Bureau. Together, these two organizations oversee and support the hacking activity of units like Lazarus Group, which are responsible for much of the cryptocurrency hacking activity we’ve tracked over the last few years. Notably, OFAC states in its press release that the 110th Research Center was behind the 2013 DarkSeoul malware attack on South Korean government agencies, confirming the long held suspicions of many in the cybersecurity community.
OFAC and MOFA also sanctioned Chinyong Information Technology Cooperation Company, also known as Jinyong IT Cooperation Company, and its employee, Sang Man Kim, for their role in helping North Korean IT professionals find contract work overseas, some proceeds of which are sent back to North Korea to support its weapons development programs. OFAC and MOFA included cryptocurrency addresses in their designations related to this activity, and we’ll explore their activity in more detail below.
Tracking Chinyong IT and Sang Man Kim’s crypto activity
OFAC has previously discussed the role of North Korean IT workers in generating revenue for the country’s weapons program. Generally speaking, IT firms controlled by the North Korean government help the workers gain employment at overseas companies — usually in the tech industry but even sometimes at crypto firms — using false documents to conceal their true citizenship. In many cases, the workers are paid their salaries directly in cryptocurrency, which is then funneled back to North Korea.
Chinyong IT is one such government-controlled IT firm, and OFAC describes Sang Man Kim as an employee of its Vladivostok, Russia office. According to OFAC, Chinyong helped North Korean IT workers get jobs in Russia and Laos specifically, with Kim helping funnel funds back to North Korea. Analysis of the addresses controlled by Kim and Chinyong IT give us some insight into this process.
In total, OFAC lists six cryptocurrency addresses associated with Kim, all of which are deposit addresses at a large, mainstream exchange. Some of those addresses are Ethereum addresses that have also transacted using the Tether and USDC ERC-20 tokens, hence why eight deposit addresses are displayed below. MOFA also identified an additional address as belonging to the Chinyong IT organization. We can see some of the activity associated with those addresses below.
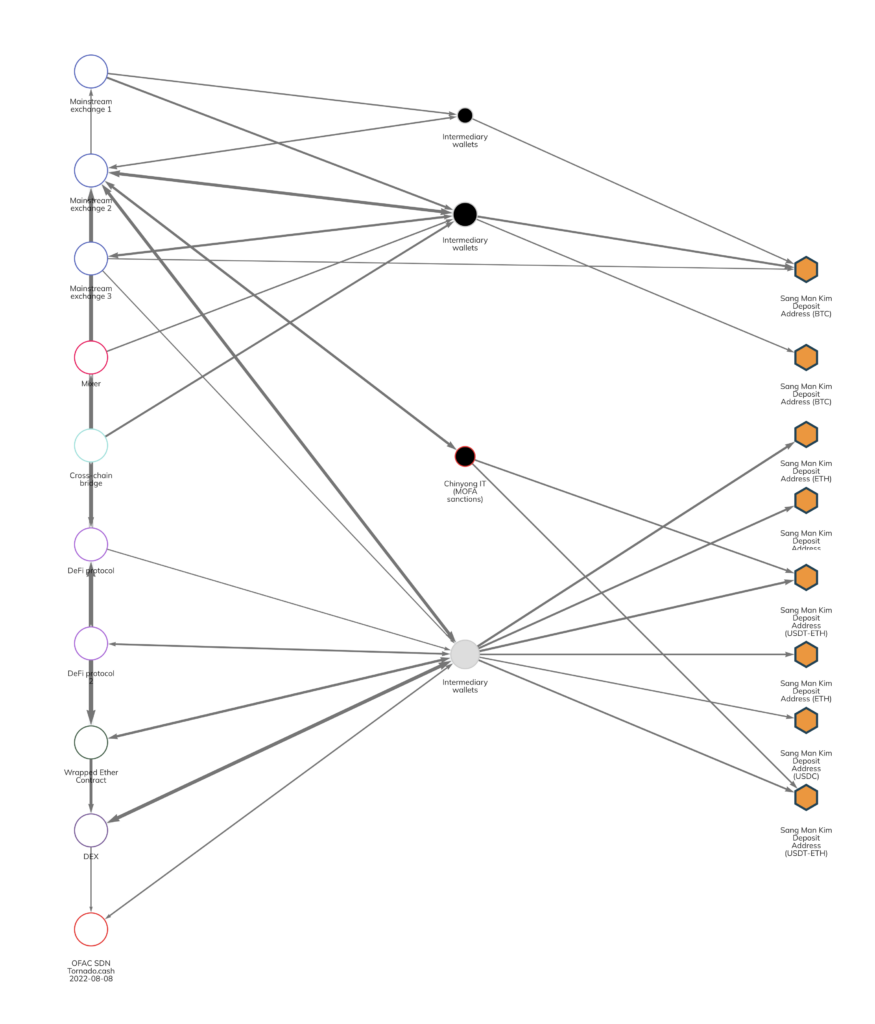
Kim’s exchange deposit addresses received over $28 million worth of cryptocurrency between 2021 and 2022 but are not currently active. As we see above, those funds have come from a variety of sources, including mainstream exchanges, mixers, and DeFi protocols. Funds typically travel from those services to Kim via intermediary personal wallets, including the personal wallet MOFA identified today as belonging to Chinyong IT.
It’s not clear from the information we have how all of these transactions fit together. For instance, it’s possible that individual IT workers were paid in fiat currency, exchanged that for cryptocurrency at services like those seen on the left side of our Reactor graph, and then funneled the funds to Kim. It’s also possible that the IT workers were paid in cryptocurrency directly. In that case, payments sent from the crypto businesses on the left side of the graph to personal wallets may represent payments made to North Korean IT workers they were fooled into hiring. It’s also possible that the graph contains instances of both transaction flows. Regardless, it’s clear that all funds eventually moved to Kim’s exchange deposit addresses, where he presumably converted them into fiat.
Sanctions are essential to stopping North Korea’s abuse of the cryptocurrency ecosystem
Sanctions like these are crucial in fighting North Korea’s exploitation of cryptocurrency. And while most analysis of North Korea’s cryptocurrency activity focuses on hacking, these sanctions also shed light on North Korea’s IT-earnings-to-crypto schemes, which have also proven lucrative. Finally, this round of sanctions, which came from collaboration between U.S. and South Korean agencies, also shows the importance of international cooperation in fighting this activity.
We commend OFAC and MOFA for their work here, and will be labeling all addresses they identified as associated with sanctioned entities in our products.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

