On May 7, 2024, the United States Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned Russian national Dmitry Yuryevich Khoroshev for developing and distributing ransomware through his Ransomware-as-a-Service (RaaS), LockBit. This action was in collaboration with the United Kingdom’s National Crime Agency (NCA), the U.S. Department of Justice (DOJ), the Federal Bureau of Investigation (FBI), and the Australian Federal Police. Khoroshev was also sanctioned by the United Kingdom’s Office of Financial Sanctions Implementation (OFSI), and Australia’s Department of Foreign Affairs and Trade (DFAT) in today’s action.
Earlier this year, the NCA, in collaboration with the FBI and international partners, disrupted LockBit by seizing many of its servers, public websites, and cryptocurrency, and obtaining decryptor keys for victims to safely recover their sensitive data. LockBit had earned over $120 million in ransom payments prior to Operation Cronos.
During the course of LockBit’s operations, Khoroshev, who went by the username LockBitSupp, profited personally from ransomware attacks and facilitated the company’s administrative activities. OFAC has since frozen Khoroshev’s assets and issued a travel ban.
Below, we’ll explore the crypto address included in today’s designations which Khoroshev used to conduct these illicit activities, and other addresses associated with LockBitSupp.
Khoroshev and LockBit’s on-chain activities
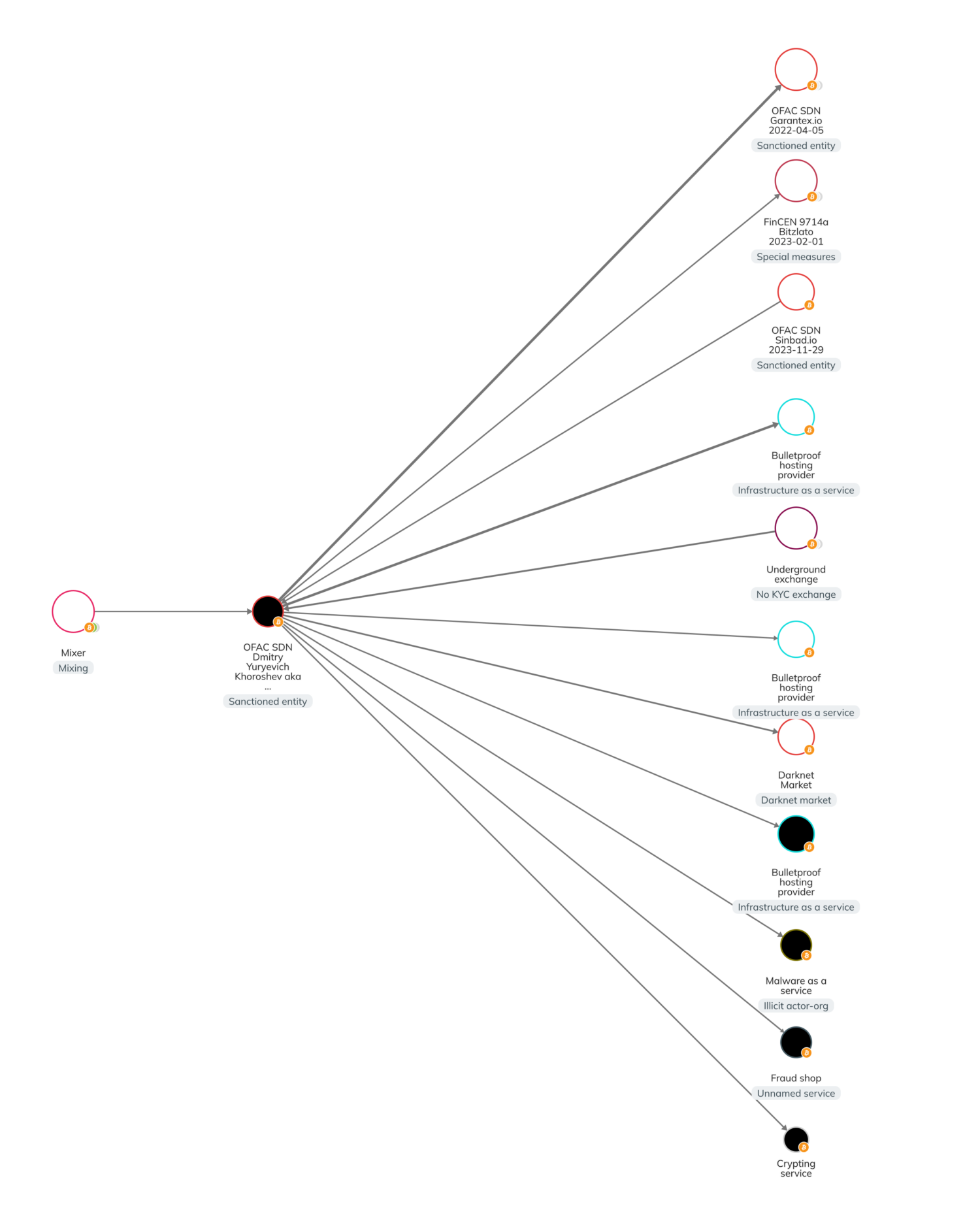
OFAC identified one crypto address, bc1qvhnfknw852ephxyc5hm4q520zmvf9maphetc9z, as being associated with Khoroshev. The Chainalysis Reactor graph below paints a more detailed picture of the on-chain activity of this address.
Starting on the left side of the graph, we see that Khoroshev received several thousands of dollars in crypto from a mixing service to his personal wallet. Khoroshev has also transferred funds to various illicit services, including OFAC-sanctioned services like Russian exchange Garantex, crypto mixer Sinbad, and Bitzlato, in addition to bulletproof hosting services, malware, fraud shops, and underground exchanges without KYC protocols.
In our earlier blog, we mentioned that LockBitSupp sponsored a contest, offering $1,000 in cryptocurrency to those who showed proof of a LockBit logo tattoo.

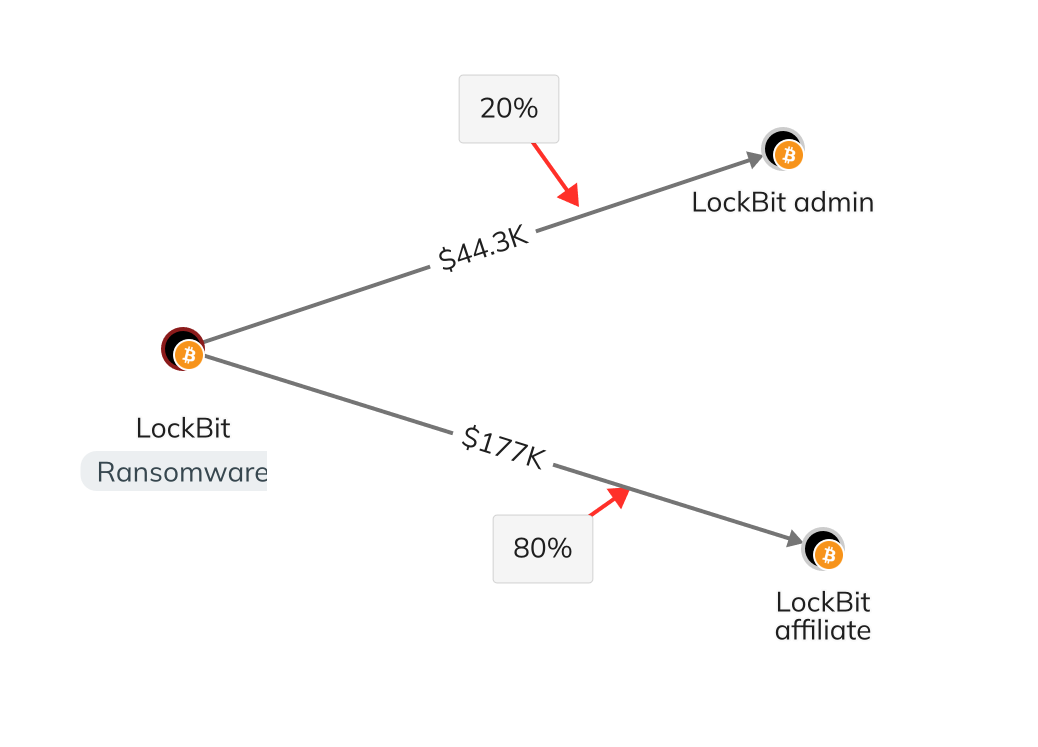
LockBit’s RaaS model typically offered affiliates 80% of its ransomware profits, and Khoroshev often pocketed the remaining 20%.
Using blockchain analysis tools, the NCA has identified and analyzed hundreds of active crypto wallets, including more than 2,000 Bitcoins — worth nearly $110 million — in LockBit ransomware proceeds that have not yet been spent or laundered.
Monitoring Russia-based ransomware crimes
As we recently identified in our 2024 Crypto Crime Report, ransomware payments hit a record high of more than $1 billion in 2023, with many ransomware groups operating out of Russia or linked to Russia. The rise in this illicit activity illustrates a need for law enforcement agencies to collaborate internationally and utilize blockchain analysis tools to disrupt these organizations.
The NCA stated to us, “The cybercriminal use of cryptocurrency in extortion schemes represents a significant threat, and ransomware is a national security issue in the U.K. Today’s action demonstrates how the NCA, working with our national and international partners, will continue to disrupt those such as Khoroshev who administer ransomware schemes and are a key enabler of the ransomware business model.”
We commend the NCA and the other agencies involved for their efforts today, and will continue to provide updates regarding Russia-based ransomware crimes when possible. We have labeled the relevant address as associated with the sanctioned entity in our product suite.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

