On December 4, 2024, the United Kingdom’s National Crime Agency (NCA) disrupted a multi-billion dollar money laundering network, which provided services to a wide range of illicit actors, including Russian and international elites, cybercriminals, and drug gangs. The NCA’s efforts, named “Operation Destabilise,” identified two Russian-speaking networks (Smart and TGR) leading these operations, which have thus far led to 84 arrests of individuals linked to these groups and the seizure of more than 20 million Euros in cash and cryptocurrency.
Today’s disruption was an internationally-coordinated effort, involving organizations including the U.K. Metropolitan Police Service, France’s Direction Centrale de la Police Judiciaire, the United States Department of the Treasury’s Office of Foreign Assets Control (OFAC), the Drug Enforcement Agency (DEA), and the Federal Bureau of Investigation (FBI), among others. This collaboration led to the arrest of another individual linked to Smart and TGR who facilitated global money laundering.
Additionally, OFAC sanctioned four entities and five individuals associated with TGR; OFAC included cryptocurrency addresses for two of the individuals:
- George Rossi (AKA Maksakov, Yury, Georgy Rossi, or Heorhii Rossi): A Ukrainian national who founded TGR Partners, is the director of TGR Corporate Concierge LTD, and likely controls the TGR Group.
- Elena Chirkinyan (AKA Yelena Norayrovna Chirkinyan or “Elle”): A Russian national who is Rossi’s direct subordinate, a partner at TGR Partners, the CEO of TGR Corporate Concierge LTD, and the manager of TGR DWC-LLC.
- Andrejs Bradens (AKA Andrejs Carenoks): A Latvian national associated with several TGR networks.
- Nikita Vladimirovich Krasnov (AKA “ACESCOM”): A Russian national who laundered cash and cryptocurrency on behalf of elite clients.
- Khadzhi Murat Dalgatovich Magomedov (AKA Magomedov or Murat): A Russian national who laundered cash and cryptocurrency on behalf of elite clients.
- TGR Partners: A Moscow-based organization founded by Rossi that provided services to a wide range of illicit actors, such as cryptocurrency trading, foreign exchange payments, and concierge services.
- TGR Corporate Concierge LTD: A U.K.-based network controlled by Bradens. Chirkinyan is its CEO.
- TGR DWC-LLC: A UAE-based network operated by Chirkinyan that provided services to help elites obscure the source of ill-gotten funds.
- Siam Expert Trading Company Limited: A Thailand-based network associated with Bradens.
- Pullman Global Solutions LLC (Pullman Global): A Wyoming-based organization owned by Bradens.
The cryptocurrency addresses in OFAC’s designation include a deposit address for Chirkinyan at a mainstream exchange (TDdbRFoBTEmE3qiR69Y6rKRSG1hoF65QaE) that has received over $146,000, and a high-volume wallet controlled by Magomedov (0x1999ef52700c34de7ec2b68a28aafb37db0c5ade) that has processed more than $200 million. The wallets have received high-value transfers, reflecting bulk cash transfers and transactions conducted on behalf of TGR clients.
Below, we’ll look at Smart’s and TGR’s on-chain activities and more details on why they were designated.
What are Smart and TGR?
Smart and TGR are Russian-speaking money laundering and financial facilitation networks that provided illicit services to various criminal groups and individuals, often facilitating the laundering processes that funded these crimes. They also helped Russian elites and designated individuals evade sanctions by providing access to financial markets that would otherwise be forbidden. For instance, Smart and TGR laundered money for the Kinahan Cartel, an Ireland-based organized crime syndicate that trafficked drugs and firearms, and was sanctioned by OFAC in 2022.
Smart is led by Ekaterina Zhdanova, whom OFAC also sanctioned in November 2023 for laundering hundreds of millions of dollars in crypto on behalf of Russian elites and criminal syndicates. She primarily worked with Magomedov and Krasnov, the latter of whom has been connected to high-turnover cryptocurrency wallets. Between late 2022 and the summer of 2023, Smart directly funded Russian espionage operations, according to the NCA’s press release. Additionally, Zhdanova and her associates helped numerous clients — including the Russia-based ransomware group Ryuk — obtain tax residency overseas, identification cards, and bank accounts to move ill-gotten funds.
TGR is run by Rossi, Chirkinyan, and Bradens. The organization advertised a variety of services, including legal support, project management, corporate concierge, and investments, as shown in the screenshot from their website below.
TGR also explicitly mentioned its involvement in cryptocurrency:
Both groups had strong links to the Russian financial sector and maintained networks spanning more than 30 countries.
Smart’s and TGR’s on-chain activities
Operation Destabilise determined that Smart, TGR, and their related networks often transferred money across borders by swapping cash and cryptocurrency. In some instances, Smart and TGR would receive funds in crypto from a client, facilitate a transfer in cash, and take a percentage of the amount. They would also follow a similar process in reverse, exchanging cash for crypto. It was unlikely that these clients would overlap, given that Smart and TGR were operating across 30 countries, and used a network of international controllers and couriers to actually perform the handovers.
The NCA also detailed that Smart and TGR provided illicit financial services on the streets in the U.K. to traditional crime groups by exchanging their cash proceeds for crypto, which they then used to further their criminal activities by paying for drugs to international cartels. Unfortunately, these networks enable serious crime in the U.K. and other countries, which threatens the country’s financial integrity and, in many cases, results in physical violence.
If we look more closely at Zhdanova’s on-chain activity, we can get a more detailed picture of how she operated Smart. In the following Chainalysis Reactor graph, we see that her personal wallets received several millions of dollars in cryptocurrency from a service provider via several intermediary wallets. Those funds then moved to two of Zhdanova’s exchange deposit addresses that OFAC highlighted in November 2023, one of which was hosted at a high-risk exchange and the other at a Russian exchange. Those deposit addresses likely represent cash-out points at services with limited or no AML/CFT controls in place. Multiple large deposits to Zhdanova’s personal wallet can be traced back to the service provider and were cashed out at these deposit addresses on the same day, demonstrating how Zhdanova was able to quickly move funds on behalf of her clientele.
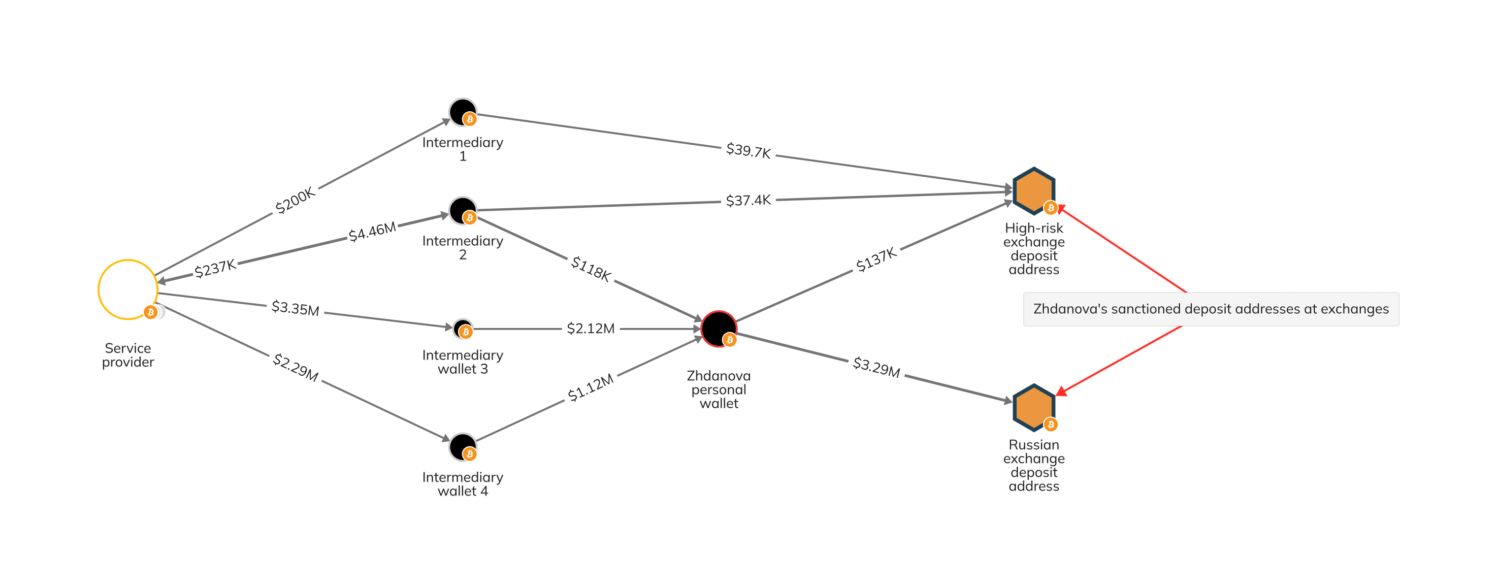
Are you a Reactor user? Click here to see this graph for yourself.
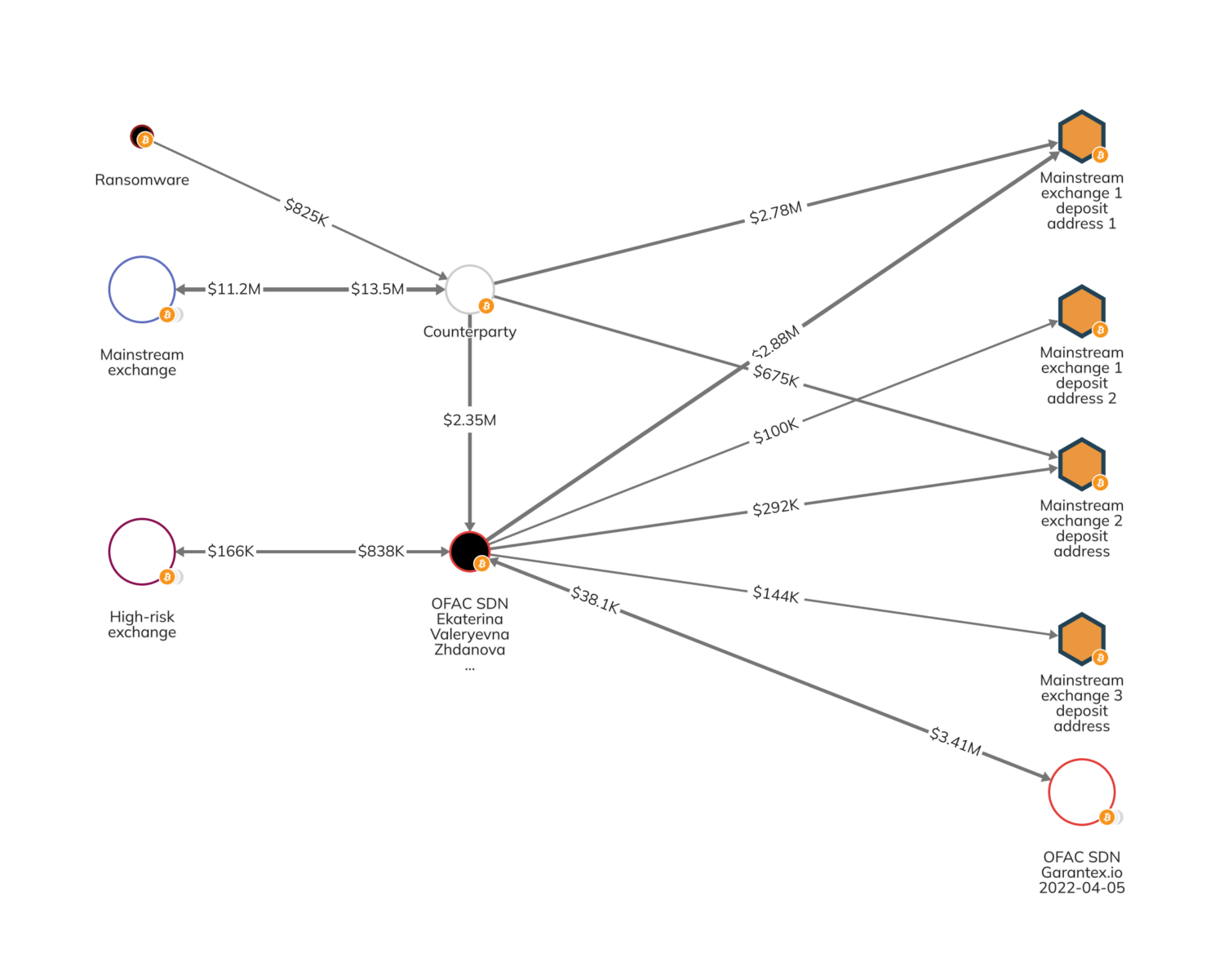
Zhdanova also laundered money on behalf of ransomware groups. The below graph shows that ransomware funds moved to Zhdanova’s wallet via a counterparty, after which she transferred millions of dollars to deposit addresses at mainstream exchanges and OFAC- and OFSI-sanctioned Russian Exchange, Garantex. This shows the breadth of her utilization of cryptocurrency throughout the ecosystem, leveraging mainstream exchanges and those with AML/CFT deficiencies to launder funds on behalf of cyber criminals, organized criminal groups, and others.
Monitoring Russia-based cryptocurrency laundering
The use of cryptocurrency for money laundering on behalf of international elites underscores the importance of cross-border collaboration to combat financial crimes. Today’s actions by the NCA, OFAC, and international partners demonstrate their commitment to safeguarding the international financial system by sanctioning illicit actors who abuse cryptocurrency and disrupting complex, transnational crime syndicates.
“Operation Destabilise started with the NCA investigating ransomware ransom payments on the blockchain, and has led us identifying two laundering networks who were operating using a methodology previously unknown to law enforcement. While these organisations have sought to exploit emerging technologies such as cryptocurrency to obscure their activities, the inherent traceability of blockchain has proven invaluable in unravelling their activities that operated on a truly global scale, moving billions of dollars for a range of different threat actors. Working closely with our U.K. and international partners, we have disrupted these networks at every level, from the Russians pulling the strings at the very top, to the U.K. cash couriers supporting harmful criminality in our communities,” said Will Lyne, Head of Cyber Intelligence at the NCA.
We will continue to share any relevant updates on this case as they become possible.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

