New updates, 7/19/23: Multichain protocol ceases operations, CEO and sister arrested
A week after cross-chain bridge protocol Multichain experienced unauthorized withdrawals of more than $125 million, the team announced on Twitter that the company has ceased operations. After the company’s CEO, Zhaojun, was arrested by the Chinese police, the team said that they could not contact him and lost the platform’s MPC keys. However, Multichain continued to operate at limited capacity.
According to the tweet, Zhaojun’s family confirmed that the Chinese police also confiscated his computers, phones, and hardware devices. Additionally, Zhaojun’s sister is alleged to have transferred remaining funds on the platform to two addresses she controlled, reportedly for “asset preservation”: 0x1eed63efba5f81d95bfe37d82c8e736b974f477b and 0x6b6314f4f07c974600d872182dcde092c480e57b. The Chinese police quickly took her into custody, breaking contact between her and Multichain.
The Multichain team says they have decided to cease operations due to their lack of access to the platform and the suspicious activities that have since unfolded. Following their announcement, Multichain’s MULTI token experienced a decline of approximately 12%.
Original post: Analysis of Multichain hack or rug pull
On July 6, 2023, cross-chain bridge protocol Multichain experienced unusually large, unauthorized withdrawals in what appears to be a hack or rug pull by insiders, leaving many ecosystem participants perplexed. Multichain’s recent exploit, which resulted in losses of more than $125 million, is one of the biggest crypto hacks on record.
Cross-chain bridge protocols have proven lucrative targets for hackers, largely due to their experimental designs and the fact that they generally have large, centralized repositories of assets bridged by users to other blockchains. However, Multichain has recently experienced some notable issues unrelated to its protocol design, which have prompted public suspicions that this recent exploit may have been carried out by insiders. Below, we’ll share what we know so far about the Multichain exploit.
Unauthorized withdrawals from Multichain
More than $125 million worth of cryptocurrency was withdrawn from Multichain, with nearly $120 million of that total coming from Multichain’s Fantom bridge. Assets taken from the protocol include wrapped Ether (wETH), wrapped Bitcoin (wBTC), and USDC. Additionally, the attacker withdrew $666,000 from the Dogecoin bridge — resulting in a loss of 85% of total deposits — and $6.8 million from the Moon River bridge, which included funds in USDC and Tether.
We can see some of these movements on the Chainalysis Reactor graph below.
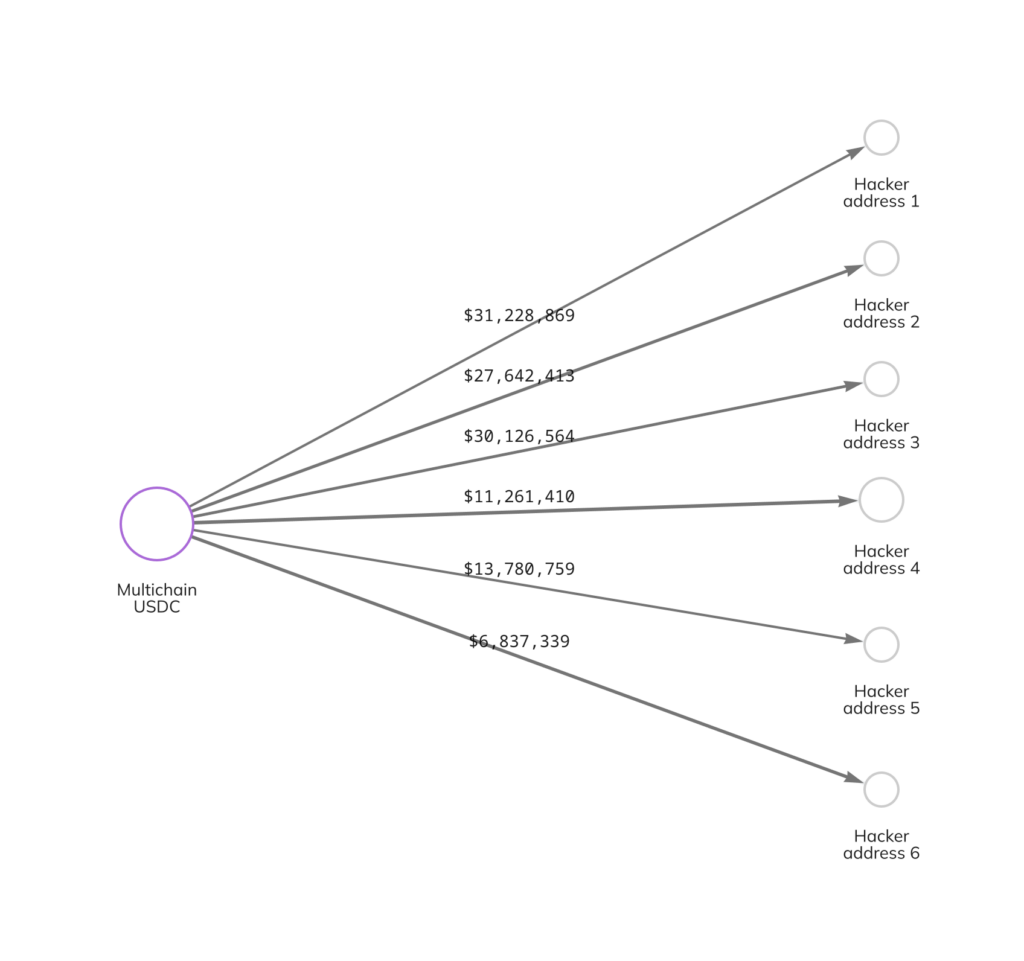
Multichain’s smart contracts are secured by a multi-party computation (MPC) system, which functions similarly to a multisignature wallet system. Instead of relying on private keys, MPC systems essentially split shards of a private key between many different parties who can then cooperate to execute transactions. However, like multisignature wallets, these systems are still vulnerable if an attacker is able to gain possession of a sufficient number of MPC keys. It is possible that the attacker gained control of Multichain’s MPC keys in order to pull off this exploit.
It’s also interesting that the attacker did not swap out of centrally controlled assets like USDC, which can be frozen by the issuing company (Circle, in the case of USDC), along with the addresses holding those assets. Most hackers typically seek to quickly swap funds for ones that aren’t vulnerable to those security measures. Indeed, Circle and Tether have both since frozen several addresses holding assets withdrawn from Multichain, preventing these funds from being transferred or swapped for other assets. In total, addresses frozen by the two stablecoin issuers hold approximately $65 million in assets stolen from Multichain.
Multichain’s recent problems have some suspicious of a rug pull
Multichain’s exploit is potentially the result of administrator keys being compromised. While it’s possible those keys were taken by an external hacker, many security experts and other analysts think this exploit could be an inside job or rug pull, due in part to recent issues suffered by Multichain.
The most obvious example is the disappearance of Multichain’s CEO, who is known by the alias Zhaojun. On May 31, 2023, Multichain revealed that it was unable to contact him, and thus couldn’t perform necessary technical maintenance on the platform. Soon, rumors spread about Zhaojun’s alleged arrest in China and confiscation of $1.5 billion of the protocol’s smart contract funds. Consequently, the existing team was forced to suspend services for more than 10 chains, including DynoChain, Redlight Chain, and Public Mint.
Multichain has also suffered from delayed transactions and other technical problems. In response to these inconveniences, Binance ended support for several tokens bridged on Multichain, effective on July 7, 2023.
The aftermath of Multichain’s exploit
After the large withdrawals, the Multichain team tweeted that they were beginning an investigation and urged users to pause transactions. A day later on July 7, the team followed up with a tweet that the protocol would be stopping service indefinitely. Unfortunately, scammers also went on Twitter to spread a phishing link and impersonate the Fantom Foundation in an attempt to trick affected users into claiming an “emergency FTM distribution.”
Although cross-chain bridge exploits can be difficult to predict, there may be several methods to mitigate risk and prevent similar exploits from occurring. One way is through rigorous code audits to help developers standardize projects and investors evaluate protocol viability. While the Multichain hack appears to have been the result of keys being compromised rather than faulty code, reputable audit reports often explicitly identify which parts of protocols are controlled by external addresses and therefore vulnerable to private key theft, which may help users better assess risk. Additionally, users of any protocol are able to conduct research before they transact.
We have labeled all addresses relevant to the Multichain hack in Chainalysis products and will continue to provide updates on the situation when possible.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
