This blog is an excerpt from the Chainalysis 2021 Crypto Crime Report. Click here to download the whole thing!
Lazarus Group is a cybercriminal syndicate working on behalf of the North Korean government. Lazarus has been responsible for numerous cryptocurrency exchange attacks, such as the 2019 UpBit hack, which netted them more than $49 million worth of cryptocurrency. Overall, the group is believed to have stolen more than $1.75 billion worth of cryptocurrency in the time it’s been active. Experts believe proceeds from Lazarus Group hacks go toward North Korea’s nuclear weapons program, so combatting their activity is of utmost importance for international safety and stability. That’s why in 2020, the U.S. government took actions such as sanctioning two Chinese nationals who helped Lazarus Group launder funds stolen in multiple cryptocurrency hacks, and filing forfeiture complaints against 280 cryptocurrency addresses associated with Lazarus Group hacks.
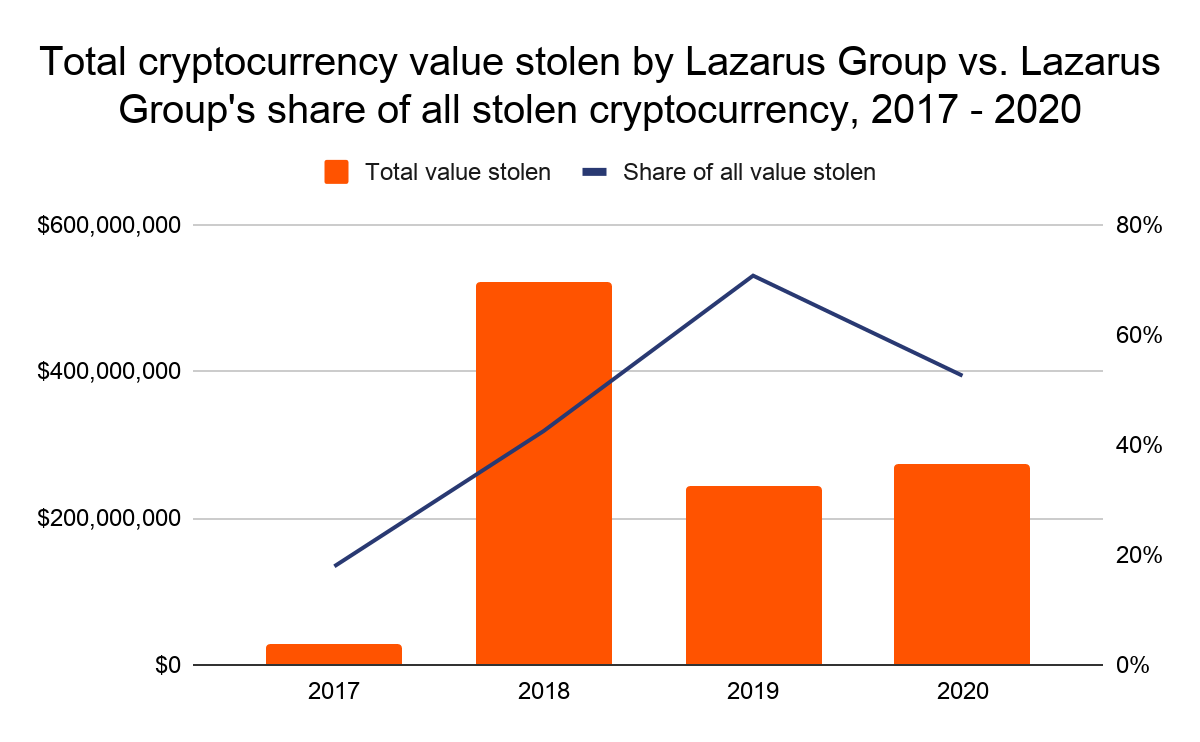
However, Lazarus Group still managed to pull off the biggest cryptocurrency theft of the year, and third-largest of all time, stealing roughly $275 million worth of cryptocurrency from the exchange KuCoin. The $275 million represents over half of all cryptocurrency stolen in 2020. According to KuCoin’s CEO, the hack occurred after cybercriminals gained access to the private keys to the exchange’s hot wallets. Soon after, he claimed that the exchange had recovered $204 million worth of the stolen funds.
We were able to attribute this hack to Lazarus Group due in part to the KuCoin hackers’ use of a specific money laundering strategy Lazarus has frequently used in the past. The strategy involves sending stolen funds to mixers in structured payments of the same size — usually an amount just below a round number in Bitcoin — that can be higher or lower depending on the size of the total amount to be laundered. Lazarus typically waits for each payment’s output to be confirmed by the mixer before sending a new one, allowing them to minimize losses in the event the mixer fails. Once the funds are mixed, Lazarus Group then typically sends funds to OTC brokers on one of a few exchanges. The KuCoin hackers utilized this strategy for portions of the funds stolen. This, along with other pieces of evidence we’re unable to share at this time, helped us identify Lazarus Group as the culprits. Additionally, two deposit addresses to which Lazarus Group sent stolen cryptocurrency this year also received funds stolen in the Harvest Finance hack, leading to speculation that Lazarus Group may have carried out that attack as well. However, this is still unconfirmed.
One new aspect of the KuCoin hack was how Lazarus Group used DeFi platforms to launder a portion of the stolen funds. DeFi platforms allow users to swap one type of cryptocurrency for another without a centralized platform ever taking custody of the users’ funds. The lack of custody means that many DeFi platforms believe they don’t have to take KYC information from customers, making it easier for cybercriminals to move funds with greater anonymity. The Reactor graph below gives an example of how exactly Lazarus Group used DeFi platforms to launder a portion of the funds stolen from KuCoin.
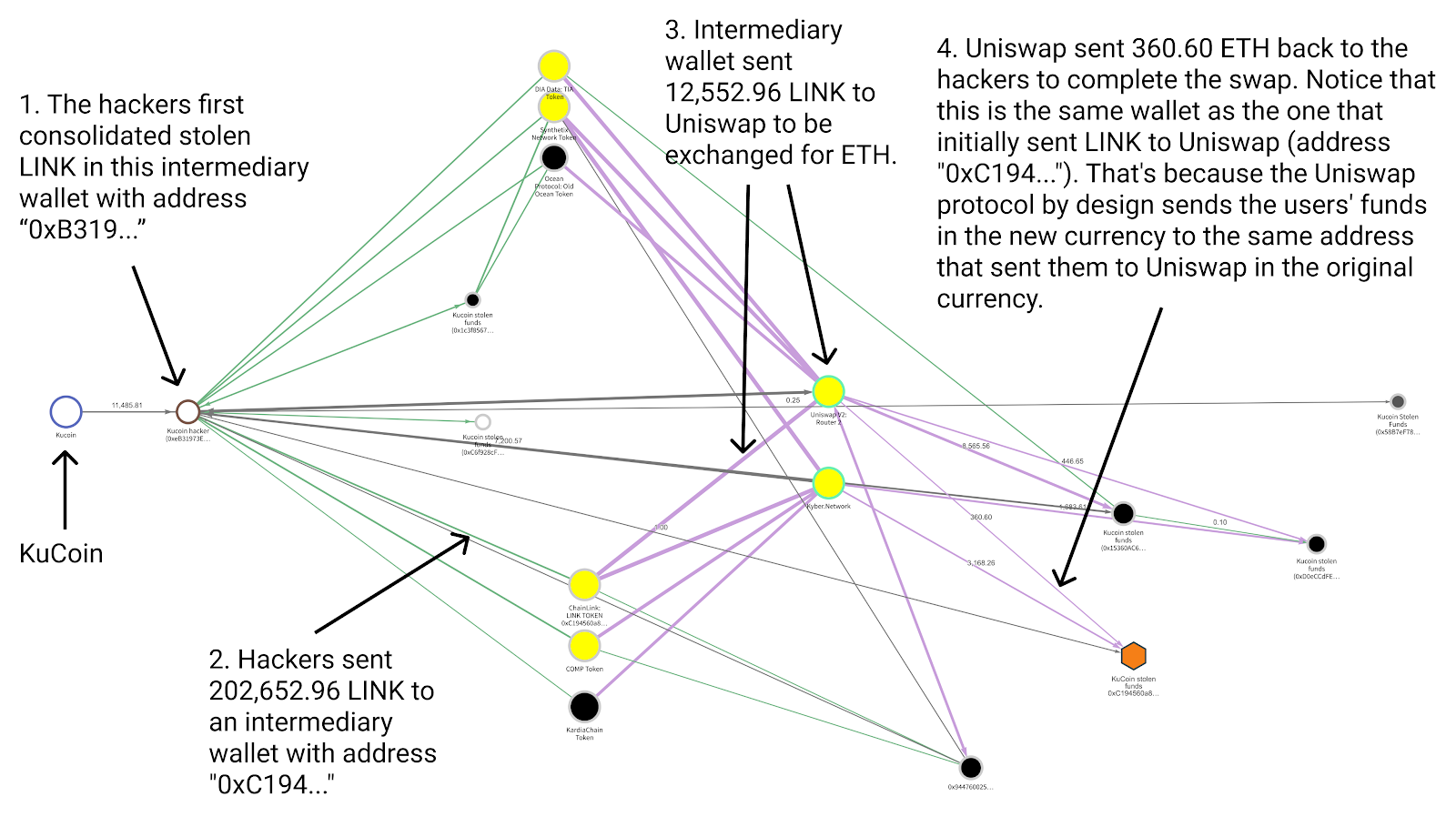
The cybercriminals first moved stolen LINK from their initial wallet to an intermediary, and from there sent it to Uniswap to be traded for ETH. As a DeFi platform, Uniswap allows users to swap between ETH and several types of ERC-20 tokens without Uniswap ever taking custody of the funds, meaning that users don’t have to provide KYC information. Users simply send funds to Uniswap from one address, and receive the equivalent amount back (minus minimal fees) at the same address in the token of their choice. So, in this case, the Kucoin hackers sent 12,552.96 LINK to Uniswap from the address “0xC194…” and received 360.60 ETH back to the same address. If investigators didn’t already know that the hackers controlled the wallet that sent and received these funds, it would have been difficult to trace the funds’ movements and spot the swap. As we can see on the graph, the hackers carried out many similar DeFi transactions using other types of tokens stolen in the hack.
The use of DeFi platforms represents a shift in Lazarus Group’s money laundering strategy. The graph below shows the breakdown of the types of services the group has sent stolen funds to over the last few years.
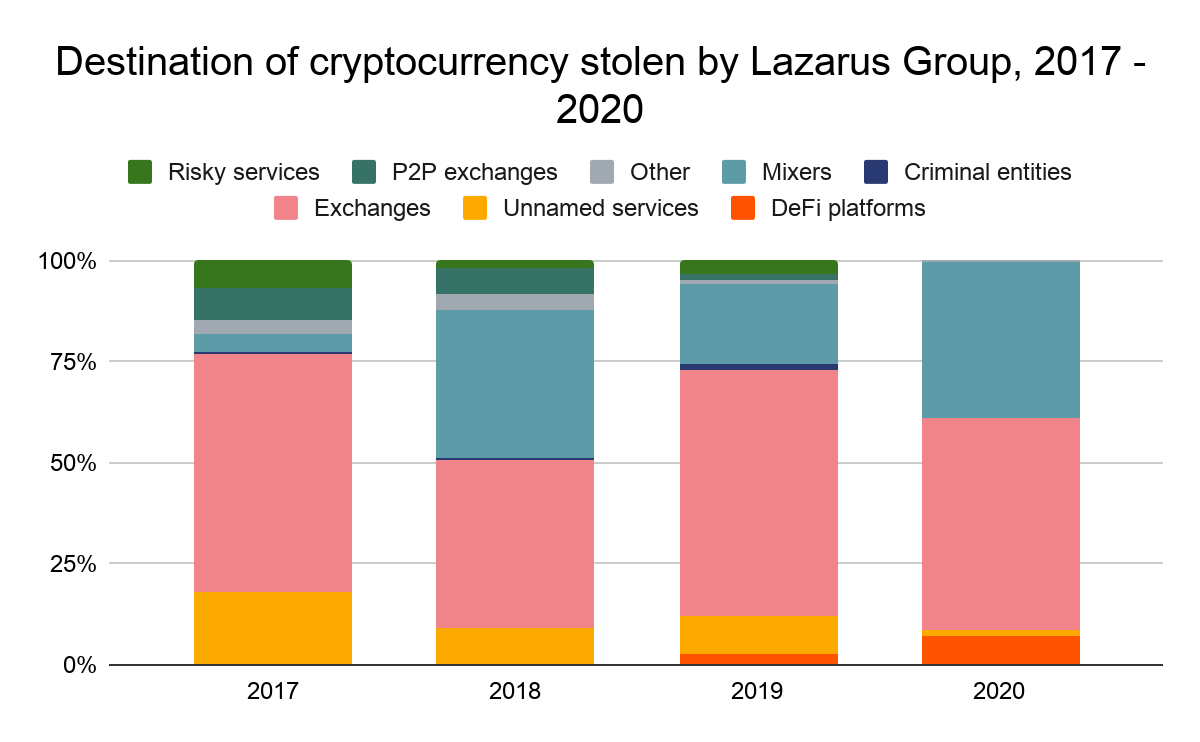
Lazarus Group’s use of DeFi platforms nearly doubled in 2020. The other trend that jumps out is the group’s declining use of mainstream exchanges. While exchanges received the vast majority of funds stolen by Lazarus Group in 2019, much of that volume went to mixers in 2020. This may be a result of increased security efforts by exchanges following the DOJ’s civil complaint against in August, which highlighted how Lazarus Group hackers frequently moved stolen funds through exchanges and OTC brokers using addresses nested at exchanges.
However, even if Lazarus Group isn’t sending as high a percentage of funds to services, they’re using more and more unique deposit addresses at services to launder funds. This trend accelerated in September 2019 and has continued since. Lazarus Group typically favors deposit addresses at a group of 20 different exchanges. In the chart below, we show the growth of deposit addresses at those exchanges that have received funds from Lazarus Group since 2018.
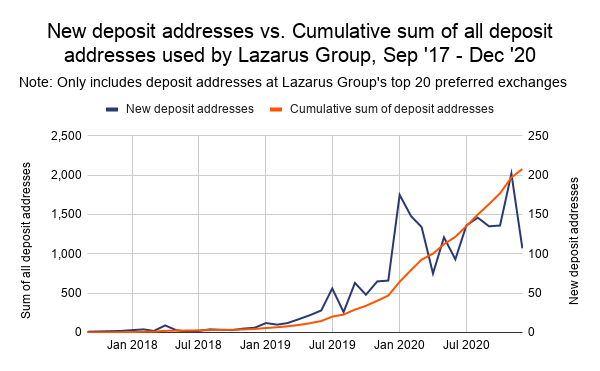
In December 2019, Lazarus Group had 470 separate cryptocurrency addresses at its top 20 exchanges that had received at least $1,000 worth of stolen cryptocurrency. By the end of December 2020, that number had risen to 2,078. This suggests that Lazarus Group is spreading its funds around more to mitigate the risk of any one address being identified and frozen. It also fits a pattern of adaptability on the part of Lazarus Group — each year, their money laundering strategy changes as services improve their security efforts.
We can’t say for sure how many of these addresses are directly controlled by Lazarus and how many are controlled by OTC brokers and other nested service providers moving funds on behalf of Lazarus. However, we try to approximate it below by analyzing the activity of all service deposit addresses that have received more than $1,000 worth of cryptocurrency from Lazarus Group addresses in 2020, looking at the total value they’ve received from those addresses versus the share of all funds they’ve received that come from criminal sources.
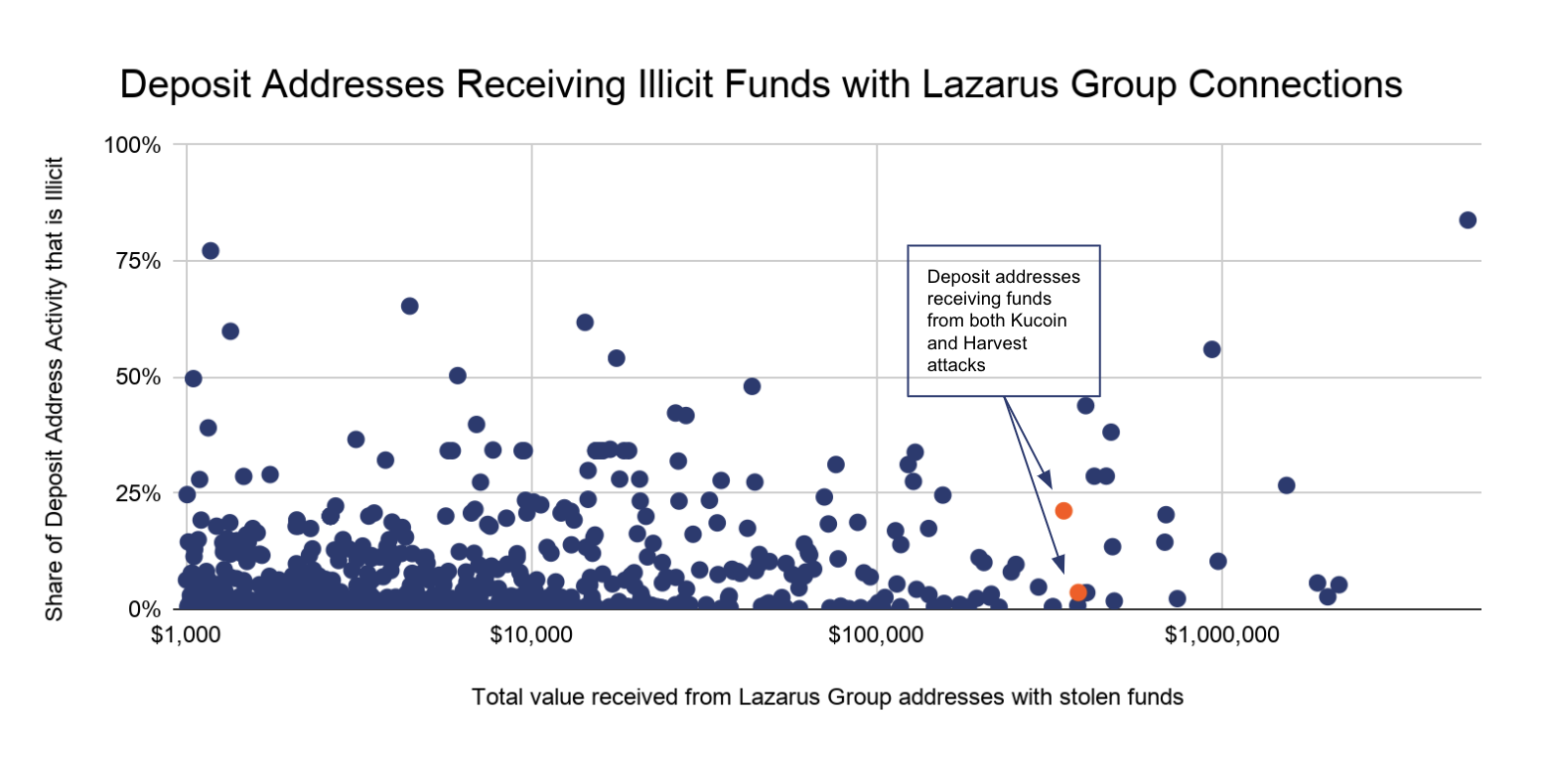
The majority of the funds go to deposit addresses that have received large sums from Lazarus Group and other criminal addresses, but whose overall activity is mostly non-illicit, and may therefore appear safe at first glance. Those addresses likely belong to nested services mostly processing legitimate transactions, rather than to wallets only moving illicit funds. That trend underlines the importance of exchanges digging into the details on the transactions carried out by nested services on their platforms — even large nested services for whom risky transactions make up a low share of total activity can be moving hundreds of thousands on behalf of rogue state actors like Lazarus Group, making them much more dangerous than they first appear.
This blog is an excerpt from the Chainalysis 2021 Crypto Crime Report. Click here to download the whole thing!
