Yes and no.
All transactions are public
Almost a billion transactions have already taken place, and anyone can view any of them on a block explorer.
Every user is pseudonymous
Nothing ties a user to a transaction except a bitcoin address – a cryptographically generated string of characters that looks like this:
3JT9t1spEZ73CNmQviecrnyiWrnqRhWNLx
Users can share this address with others to receive bitcoin, or they can use the private key associated with it to send some. This functions as the user’s pseudonym.
The blockchain is transparent, but hard to read
Consider the following bitcoin transaction:
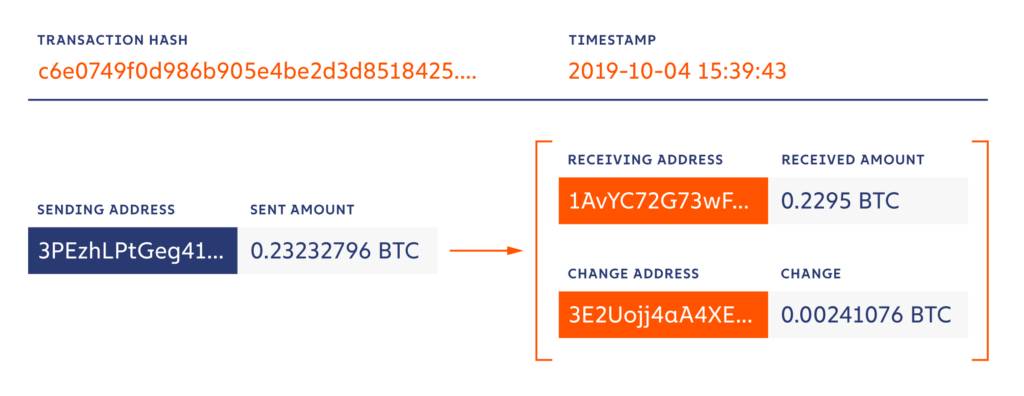 When it was confirmed, a lot of details were made public automatically:
When it was confirmed, a lot of details were made public automatically:
- The transaction hash (TxID). The 32 byte hash that uniquely identifies the transaction.
- The sending address. The pseudonymous entity that sent the BTC.
- The receiving address. The pseudonymous entity that received the BTC.
- The change address. The unspent BTC that was returned to the sending entity in a newly created address.
- The Unix timestamp. The record of when the block – the collection of transactions that included the one above – was confirmed and added to the blockchain. (Time between transaction initiation and block confirmation: 5 to 45 minutes.)
- The amounts sent and received.
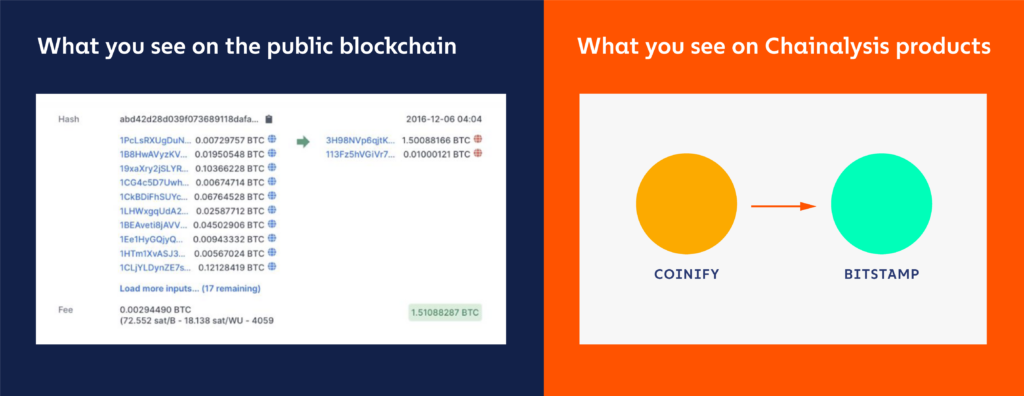
That data may be public, but it’s not very insightful; it begs more questions than it answers. For example:
- Who are the pseudonymous entities? Are they cryptocurrency exchanges, merchant processors, or darknet markets?
- Why are they transacting? Is it a payment, an investment, or a smart contract?
- How much value are they transacting? Hundreds, thousands, or millions of dollars/euros/etc. worth of cryptocurrency?
Helping organizations answer these questions is Chainalysis’s speciality.
How do we connect bitcoin addresses to real-world entities?
 Our attribution process has three stages:
Our attribution process has three stages:
- Clustering. A cluster is a collection of addresses we have determined are controlled by the same entity. To figure out what addresses belong in each cluster, we run algorithms over the blockchain’s entire history. We also employ a number of strategies to analyze co-spends, change addresses, behavioral patterns, peel chains, and advanced obfuscation techniques.
- Identification. Once a group of addresses has been clustered, we identify the entity that owns the cluster using manual and automated techniques.
- Categorization. We then label the entity according to the type of service they provide their level of risk.
These results are fed into our investigation, compliance, and investment tools. These tools make blockchain activities easy to understand, analyze, and see.
Why bother with Bitcoin tracing?
Bitcoin is used for a number of legitimate activities, such as:
In contexts like these, Chainalysis helps businesses build investment strategies, financial institutions offer crypto services, and government agencies oversee regulated activity.
Bitcoin is also used for illicit activities, including crimes like:
- Scams
- Ransomware
- Money laundering
- Child exploitation
- Terrorist financing
- Sanctions evasion
- And darknet market activity
All of which we cover in our annual Crypto Crime Report.
In these (less savory) contexts, Chainalysis helps businesses trace stolen funds, cryptocurrency companies comply with anti-money laundering policies, and law enforcement agencies identify criminal entities.
How do investigators stop bitcoin crimes?
With a combination of technical expertise and graphing technology. Both are typically necessary; without training, an investigator may end up with graph like the following:
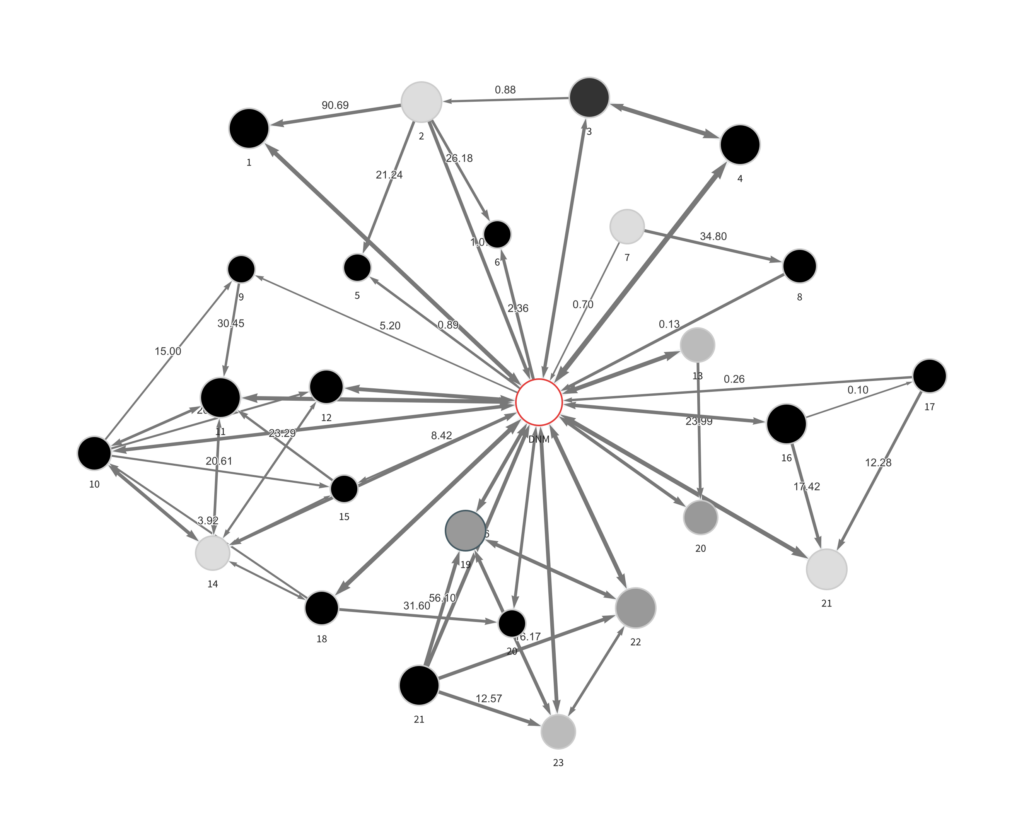
But with better knowledge of blockchain analytic techniques, an investigator could organize that same graph much more meaningfully.
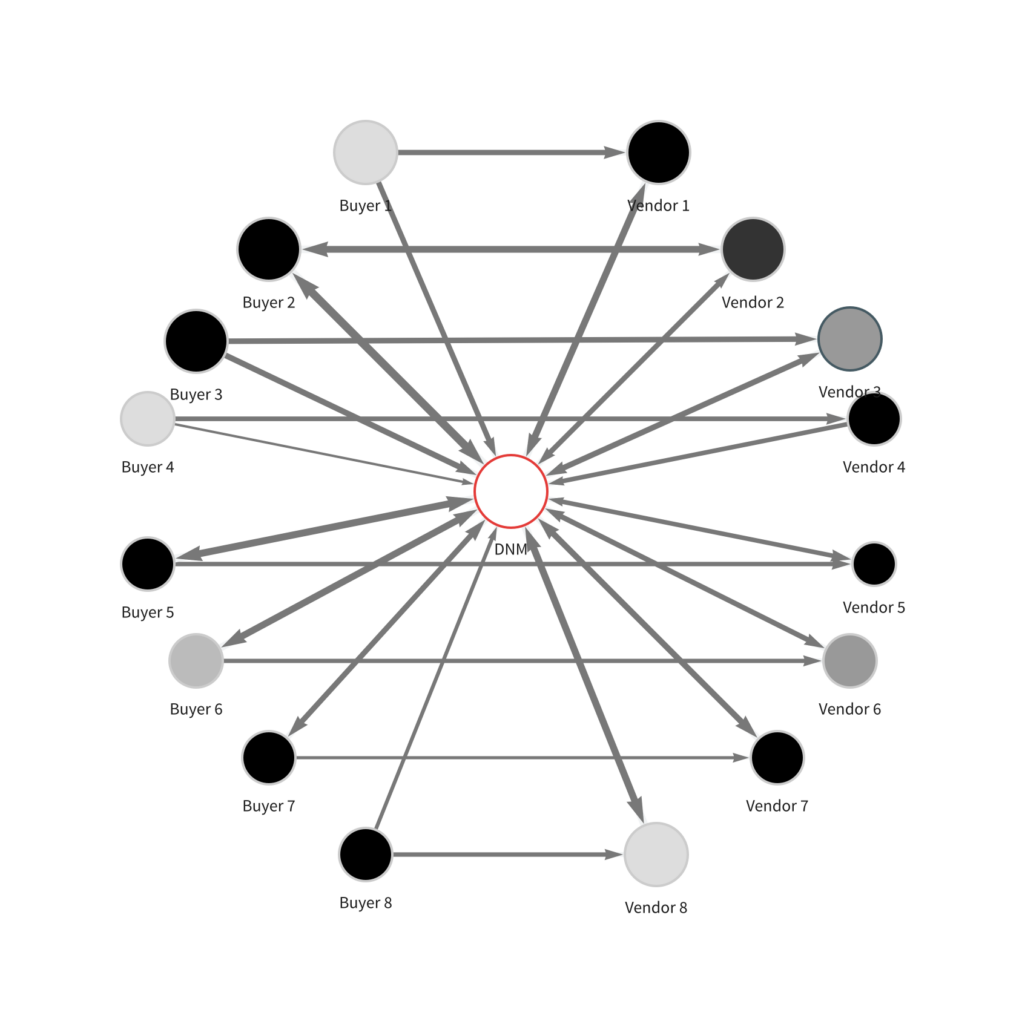
In the revised graph, we can see the transaction relationships between eight drug buyers and vendors, each of which have ties to the same darknet market. These relationships exceed $3 million in Bitcoin sent and received – a pattern indicative of drug trafficking.
Using Chainalysis Reactor, investigators can dig much deeper into these clusters’ activity. For example, here are the sending and receiving exposures of the darknet market identified above:
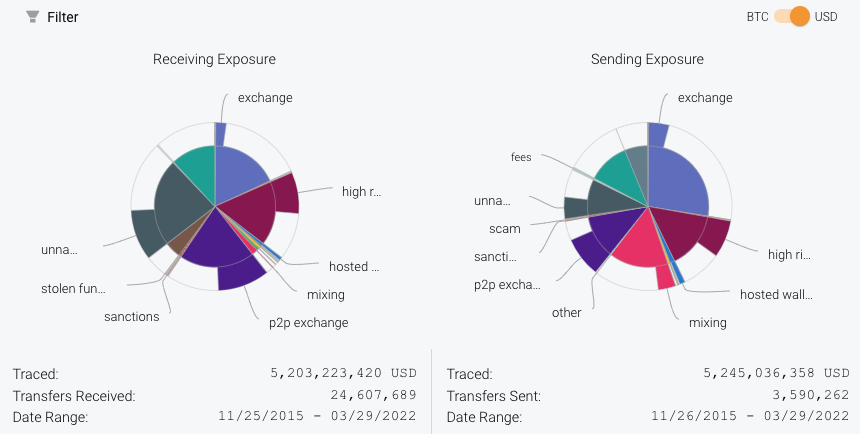
By clicking on one of those categories, investigators can see the main entities with whom the darknet market is transacting — one of the many ways in which investigators can generate leads.
Blockchain analysis: A key to trust in cryptocurrency
Blockchain analysis is critical to stop crime and build trust in cryptocurrency. That’s why customers in over 70 countries use Chainalysis products to build safely, fill compliance gaps, and solve cases with confidence.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.