Crypto-related compliance is crucial for the stability and trustworthiness of the crypto industry. As the number of cryptocurrency users continues to grow, the outlook for custodial cryptocurrency businesses remains positive. But as history has shown us, these businesses — especially centralized exchanges (CEXs) — still face major risks around security and compliance.
In the past year, several regional CEXs were hacked, including Japanese exchange DMM Bitcoin ($305 million) and Indian exchange WazirX ($235 million). At the same time, some major international exchanges have faced fines for compliance issues, highlighting ongoing regulatory scrutiny in the sector. This is likely to become a more frequent occurrence as regulators seek to further codify and enforce crypto-specific regulations.
Of course, avoiding hacks and fines from regulators are far from the only reasons to take security and compliance obligations seriously. They’re also crucial to building trust with new users — particularly as crypto becomes an increasingly popular asset class and retail investors seek out the stability and safety of CEXs to buy, sell, and trade crypto.
In this blog, we’ll look at components of cryptocurrency exchange compliance, examples of robust exchange compliance programs, and more.
Understanding cryptocurrency exchange compliance
A large part of crypto-related compliance focuses on securing the platform operations of crypto exchanges. This includes implementing local and international anti-money laundering and countering the financing of terrorism (AML/CFT) measures to prevent abuse of their products and services.
Following FATF recommendations
As a crypto exchange, the jurisdictions in which a business is registered, incorporated, and operates will determine the regulations it must follow. The Financial Action Task Force (FATF) is an international organization that protects the integrity of the global financial system by setting legal, regulatory, and operational standards around money laundering, terrorist financing, and proliferation financing. National- and regional-level regulations often mirror the FATF recommendations for money services businesses and other licensed services. These rules fall into three categories:
- Know your customer (KYC) requirements: These rules dictate the collection of identifying information from users for a range of reasons, such as confirming users are not subject to sanctions, blocking individuals residing in prohibited jurisdictions, and empowering proactive investigations in case of future suspicious activity. This information is essential for verifying user identities, reducing fraud, and ensuring compliance with regulatory requirements.
- Transaction monitoring: CEXs must monitor transactions on an ongoing basis for suspicious activity that could reveal money laundering, terrorism financing, or other forms of financial crime.
- Responding to risky activity: If monitoring transactions effectively, businesses will undoubtedly encounter some risky behavior requiring direct outreach to customers, updating records, and reporting suspicious activity to relevant enforcement bodies. This typically entails following the requirements laid out by the relevant jurisdiction’s anti-money laundering (AML) laws and policies.
We’ll cover each of these crypto exchange compliance areas below.
Components of crypto exchange compliance
Collecting Know Your Customer (KYC) information
KYC procedures are essential for CEXs to verify user identities, reduce the risk of fraud, and ensure compliance with laws and regulations. Implementing robust KYC processes involves collecting and verifying user information, utilizing identity verification technologies, and maintaining secure records. Below are some of the most common types of KYC information:
- Email address
- State-issued identification or driver’s license
- Date of birth
- Social security or national identification number
- Phone number
- Physical address
- Utility bill or similar document to act as proof of address
Keep in mind that there are no universal rules dictating exactly what information must be collected and when. In many jurisdictions, while it’s legal for an exchange to allow users to sign up and transact with just an email address, it’s still important to screen names. Failure to collect KYC information can be indicative of high-risk operations, exposing services to a range of operational, regulatory, and legal challenges. Most mainstream CEXs require more than just a name and email address — especially for users who transact in larger amounts.
Some exchanges collect a great deal of KYC information upon registration, whereas others employ a tiered system in which trading higher volumes of cryptocurrency requires more KYC and scrutiny. The right approach depends on the business model and customer base.
After businesses collect and securely store verified documents proving a users’ identities, they typically conduct sanctions screenings. The goal of this screen is to ensure that new users and their close associates are not subject to sanctions. Government bodies of multiple countries, including the Department of the Treasury’s Office of Foreign Assets Control (OFAC) in the U.S. and the Office of Financial Sanctions Implementation in the U.K., maintain their own sanctions lists. The easiest way to screen is to use a service like Thomson Reuters or Refinitiv. These services consolidate all relevant sanctions lists so that businesses don’t have to check each one individually or periodically.
Businesses can also use these services to conduct politically exposed person (PEP) screenings, which tell them if a user is a government official at higher risk for bribery or other forms of financial corruption, and adverse media screenings, which look across a variety of news sources for evidence that a potential user may be involved in criminal activity. In addition, as in TradFi, some CEXs have a dedicated investigations component whose remit is to respond to taskings of interest, and proactively identify, flag, and disrupt platform abuse and other suspicious activity.
Transaction monitoring and reporting
The continuous monitoring of transactions is important for detecting suspicious activities and ensuring compliance with regulatory requirements. By consistently monitoring transactions, CEXs can identify potential risks and take prompt action to mitigate them, maintaining platform integrity. Establishing automated reporting systems and maintaining accurate records are essential for filing required reports on time and staying compliant with regulatory standards.
Custodial crypto businesses typically monitor the transactions their users conduct from their addresses hosted on the business’s platform to confirm they aren’t sending or receiving funds from criminal entities. Between FATF members and FATF-style regional bodies, more than 200 countries have committed to FATF recommendations, which include keeping and sharing with the authorities records of any suspicious transactions, all transactions above a certain size, and instances where users may be attempting to conceal such activities.
Monitoring for criminal activity
To detect when users send to or receive funds from cryptocurrency addresses associated with illegal activities — such as those belonging to darknet markets, sanctioned entities, scammers, and other cybercriminals — businesses need robust monitoring solutions.
Chainalysis Crypto Compliance Solutions can provide alerts for when users are transacting with risky addresses. Exchanges are able to configure flexible risk rules across category thresholds, custom groups, and behavioral activities that create alerts for teams to review.
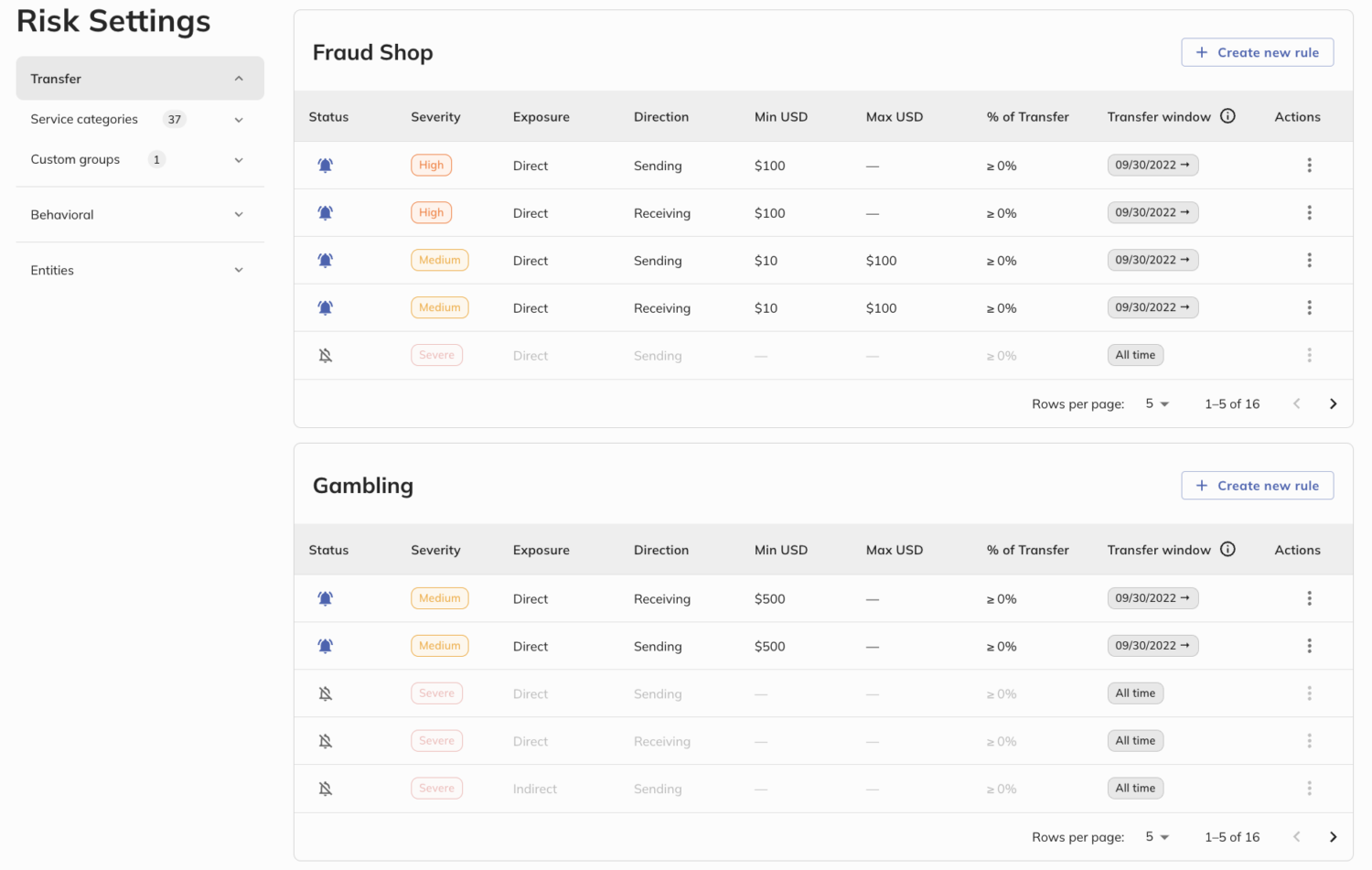
As Chainalysis continuously monitors transfers — even if exposures change in the future due to new activity — teams have the option to be alerted to keep the platform safe. Once alerted, teams are able to collaborate, manage cases, and determine if action should be taken for the user.
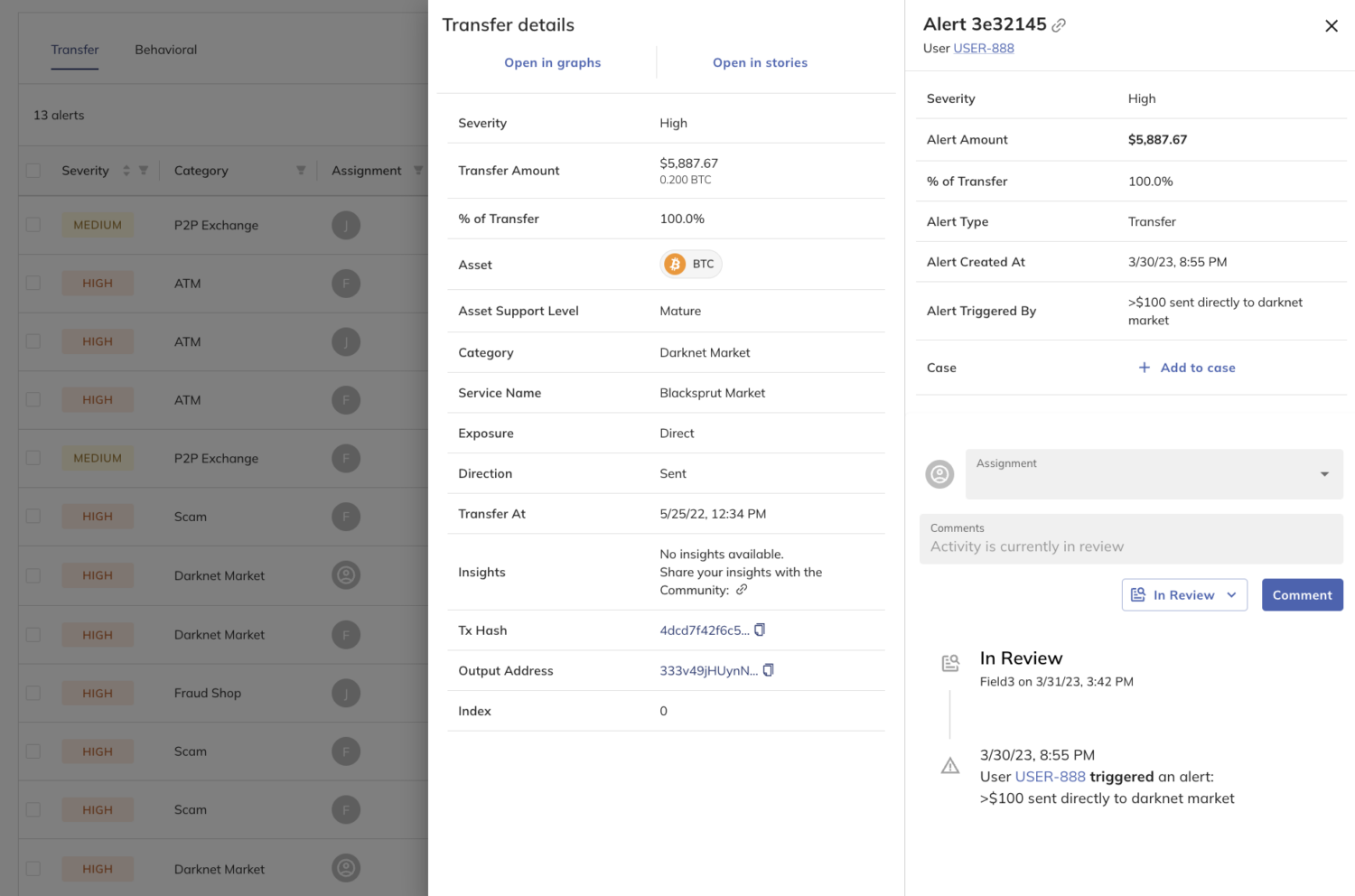
User views in Chainalysis provide insights into users’ activity and exposure, alerts, and more. If further investigation into activity is needed, Crypto Investigations Solution graphs and stories can be accessed directly from the alert, and can help businesses trace the funds to sources and destinations of their customers’ funds.

Reporting responsibilities
Most jurisdictions require businesses to file and report certain types of transactions. For instance, in the United States, FinCEN mandates that cryptocurrency businesses file Currency Transaction Reports (CTRs) for any cash deposits or withdrawals equal to or exceeding $10,000. Most FATF member countries have similar rules. Additionally, cryptocurrency businesses in FATF countries must comply with the “Travel Rule,” which requires Virtual Asset Service Providers (VASPs, which includes cryptocurrency exchanges) to verify their customers’ identities, and identify the originators and beneficiaries of transfers over 1,000 USD/EUR and transfer that information to their VASP counterparty, where one exists.
It’s also important to keep in mind that subnational authorities often impose their own additional rules. For instance, cryptocurrency businesses operating in New York State must obtain a unique license from the New York Department of Financial Services (DFS) and follow rules set by DFS around licensing, compliance, capital requirements, consumer protection, cybersecurity, and other provisions.
Suspicious activity reporting
As is true for traditional financial institutions, cryptocurrency businesses must keep records of and sometimes submit reports on transactions that, while not explicitly associated with illegal activity or in violation of the FATF recommendations, may suggest such activity or are otherwise suspicious. Examples include:
- Payment structuring. Sometimes called “smurfing,” payment structuring refers to conducting multiple transactions at amounts just below those that would trigger reporting requirements. For instance, if a U.S. user makes multiple transfers to an address at another service of just below $3,000 worth of cryptocurrency, businesses might need to report it, as it could represent an attempt to circumvent the Travel Rule.
- Velocity increases. A “velocity increase” refers to an instance of a user suddenly and drastically increasing their trading activity. For example, a user who quickly goes from trading once per week to trading twenty times per week could necessitate further investigation.
- Common counterparties. Take note of any unknown addresses that numerous users are transacting with, especially at large volumes. For instance, if a business notices that, in the last month, 20 of its users have begun sending funds to an address not associated with any known service, it’s worth noting it for future investigation and analysis in case more suspicious activity occurs later.
- Anomalous activity. Anomalous activity refers to any sudden change in a user’s trading behavior out of the ordinary, especially large increases in volume. For instance, if a business operates an exchange and a user who has been trading roughly $100 worth of cryptocurrency per week suddenly makes $10,000 worth of transactions in a week, the business should record and possibly report that activity as suspicious.
Taking a risk-based approach to responding to suspicious activity
Exchanges should consider implementing a plan that addresses all possible scenarios for detecting suspicious activity — including gray areas and workflows for assessing unforeseen scenarios — and translate them into well-documented policies and procedures for their compliance teams.
There’s no single blanket compliance policy that will work for every exchange. Below are a few considerations for effectively assessing risk.
Understand risk tolerance and tailor responses to risk levels
Assessing an organization’s risk tolerance is a good starting point, and from there, exchanges can consider the relevant responsive actions for all forms of suspicious activity based on how much risk they introduce. The amount of risk a suspicious or illicit transaction introduces depends largely on the amount of funds transacted and the severity of the risky counterparty.
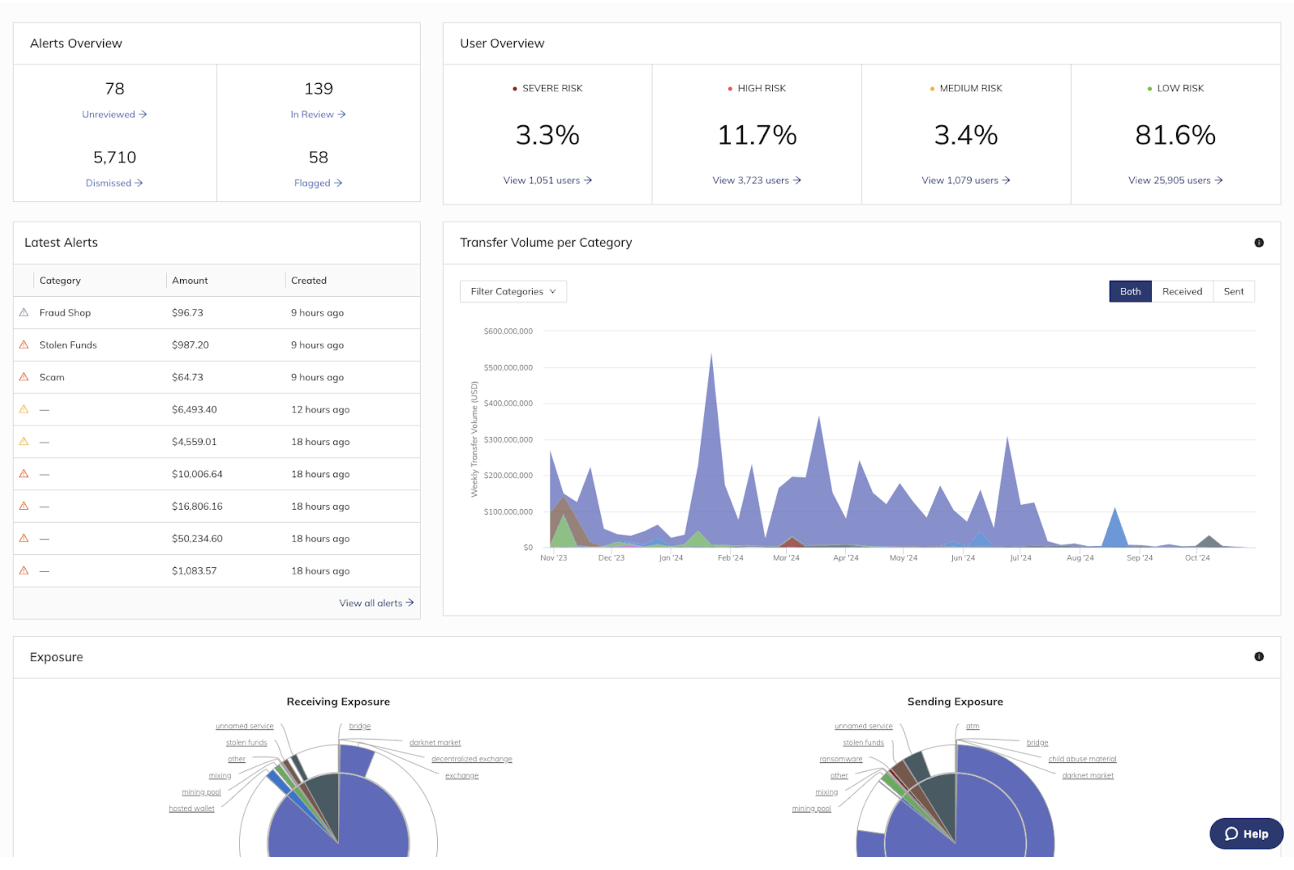
Chainalysis Compliance Solutions provides dashboarding to help services obtain a high-level view of their entire business platform’s crypto transaction monitoring efforts. It provides visibility across alerts, users, exposure, transfer volume, and more.
Implementing graduated responses
Most exchanges respond in one or several of the following ways when users conduct a potentially risky transaction, depending on the level of risk introduced and previous risky activity exhibited by the user:
- Contacting the customer directly for an explanation of the transactions before deciding whether or not to take action
- Freezing the user’s funds
- Restricting the user from transacting larger amounts that would trigger the next KYC tier (if the business is indeed using a tiered KYC collection system)
- Banning the user from the platform

Again, no single policy makes sense for every exchange; it is therefore important to determine in advance which of those responses a business will employ depending on the riskiness of the activity in question.
Automatic monitoring and reporting
If a user’s activity is deemed suspicious for a business to take any of the above actions, it is likely that the business must file a Suspicious Activity Report (SAR) with FinCEN, or the equivalent organization in the relevant jurisdiction. SARs are mandatory in these scenarios, and must be filed with the appropriate body within 30 days of the suspicious activity. This means that, as a business grows, it may eventually need an automated transaction monitoring system to keep up with suspicious activity and file SARs in a timely manner. As with traditional financial institutions, most cryptocurrency businesses with substantial transaction volumes and a functioning compliance policy typically file a large number of SARs.
Check out our webinar on how to file SARs as a cryptocurrency business.
Regular security audits
Frequent security audits are essential for identifying vulnerabilities that could be exploited for unauthorized access or fraud. By regularly reviewing systems, protocols, and transaction histories, exchanges can stay ahead of potential threats, ensuring compliance with regulatory standards and enhancing user trust.
Security literacy and training
Providing ongoing security training to staff strengthens the first line of defense against suspicious activity by ensuring that employees are well-equipped to recognize and respond to potential threats. This literacy extends beyond IT staff, empowering all team members to follow best practices in handling sensitive data and safeguarding user information.
Maintaining accurate documentation and record-keeping
Accurate documentation is crucial in tracking suspicious activity and meeting compliance standards, especially when backed by copies stored both online and offline. By implementing a thorough record-keeping system, CEXs can maintain reliable access to historical data for audits and investigations, even in cases of system failure or data corruption.
Implementing IP blocking
Implementing IP blocking has also become a central part of an effective compliance program, particularly with regards to mitigating sanctions risk. Multiple OFAC enforcement actions in recent years have cited deficient IP blocking programs, so it is important to ensure that businesses are stopping users from accessing their platforms from prohibited jurisdictions.
Robust exchange compliance programs
Creating and maintaining a comprehensive compliance program requires continuous investment in technology and personnel. Key components include:
- Regular training: Ensuring compliance teams stays up-to-date with the latest regulations and best practices. We offer risk and regulation training designed to keep crypto businesses at the forefront of the latest crypto compliance technology.
- Continuous policy updates: Regularly reviewing and updating compliance procedures to adapt to evolving regulations and emerging risks. Our team of crypto policy experts regularly share updates designed to keep regulators, policymakers, and compliance professionals well-informed about global digital asset developments.
- Documentation: Maintaining detailed records of all compliance activities, decisions, and rationales.
- Timely reporting: Filing SARs with the appropriate regulatory body within the required timeframe when suspicious activity is detected.
Security for cryptocurrency businesses
Security is just as important as compliance when it comes to building a safe and sustainable cryptocurrency business. When they aren’t properly secured, digital asset platforms can be extremely vulnerable to cyberattacks and other threats. However, platforms that account for the main attack vectors compromised by hackers will likely be significantly safer. These attack vectors include:
- Private keys
- Deposit addresses
- API keys
We’ll explore all three in greater detail below.
Private keys
Hackers and other malicious actors (such as insider threats) may attempt to compromise a victim’s private keys in order to access their wallet, which controls the funds they have stored on the blockchain. This enables the attacker to transfer the funds from the victim’s wallet to anywhere.
Some of the ways in which private keys have been compromised before include:
- Infecting a server with malware that steals the private key
- Stealing a hardware security module (HSM) authentication token and forcing the HSM to sign a withdrawal transaction
- An authorized internal employee steals the private key
Today, institutions in the digital asset space are securing private keys using multi-party computation (MPC). MPC represents a powerful next step in private key security, and it’s even more effective if the keys are secured in hardware (i.e. Intel SGX, a chip-level hardware isolation enclave) and across multiple cloud providers.
MPC is a strong wallet solution, because it offers immediate access to digital assets while retaining the highest level of security. The fundamental capabilities of MPC eliminate the single point of compromise of the private key. At the same time, MPC’s distributed nature allows team members to require multiple authorizers for a transaction and sign transactions without being in the same location.
Deposit addresses
A deposit address is a long alphanumeric identifier that designates the public address of a wallet. To transfer funds to a counterparty, it’s necessary for both parties to exchange deposit addresses. Hackers target deposit addresses in a number of different ways :
- Installing fraudulent Chrome web extensions that hijack the web browser (man-in-the-browser attack)
- Spoofing the address while copy and pasting between the web browser and the wallet’s app
- Intercepting and modifying the deposit address while it’s being sent between counterparties on a messaging service (i.e. Telegram)
- Hijacking code on the exchange’s website to spoof the address at the origin
- Malware that hijacks the wallet interface, driver, or counterparty’s device
A number of methods have been utilized to mitigate the threat of deposit address compromise; some of the most common include test transfers, whitelisting, and hardware wallets.
API keys
Exchanges and liquidity providers often have users utilize API keys for automated access to their platforms. These credentials are vulnerable to traditional forms of malware, such as keylogging and phishing. API keys stored in trading software can also be stolen if the server or code repository is compromised.
In general, once a hacker obtains API keys, it’s possible for them to:
- Conduct unauthorized withdrawal of funds from an exchange.
- Manipulate the market using pre-funded assets on a compromised account.
Today, institutions use a variety of methods to protect API infrastructure, including chip-level hardware isolation. The unique security properties of chip-level hardware enclaves guarantee their confidentiality and execution integrity. This prevents hackers and solutions providers from accessing keys or spoofing the authenticity of deposit addresses to where funds are transferred.
It’s best to treat API keys similarly to private keys by splitting them up into MPC shares in addition to securing them in hardware. Recent developments in API security include the HMAC-MPC algorithm, which applies MPC to API key secret credentials — effectively enabling customers to access exchanges with distributed API keys and removing the single point of compromise.
If left unchecked, private keys, deposit addresses, and API keys can lead to serious security issues — including cyberattacks by hackers and even internal security breaches. But it’s possible to secure all three with a defense-in-depth approach, mitigating all attack vectors through multiple layers of software and hardware security.
The future of cryptocurrency security and exchange compliance
Crypto continues to gain traction worldwide, and appears poised to become a mainstream investment asset and medium of exchange. However, achieving this vision requires industry-wide efforts to implement robust consumer protection measures alongside rigorous compliance standards, much like those governing fiat currency. Following the steps outlined in this guide can help exchanges bolster security for current users and establish strong compliance frameworks — essential for driving broader adoption and fostering trust within the market.
Chainalysis offers a suite of compliance solutions and services to help exchanges navigate the complex regulatory landscape. To learn more about how we can support your compliance efforts, request a demo.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide compliance, legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

