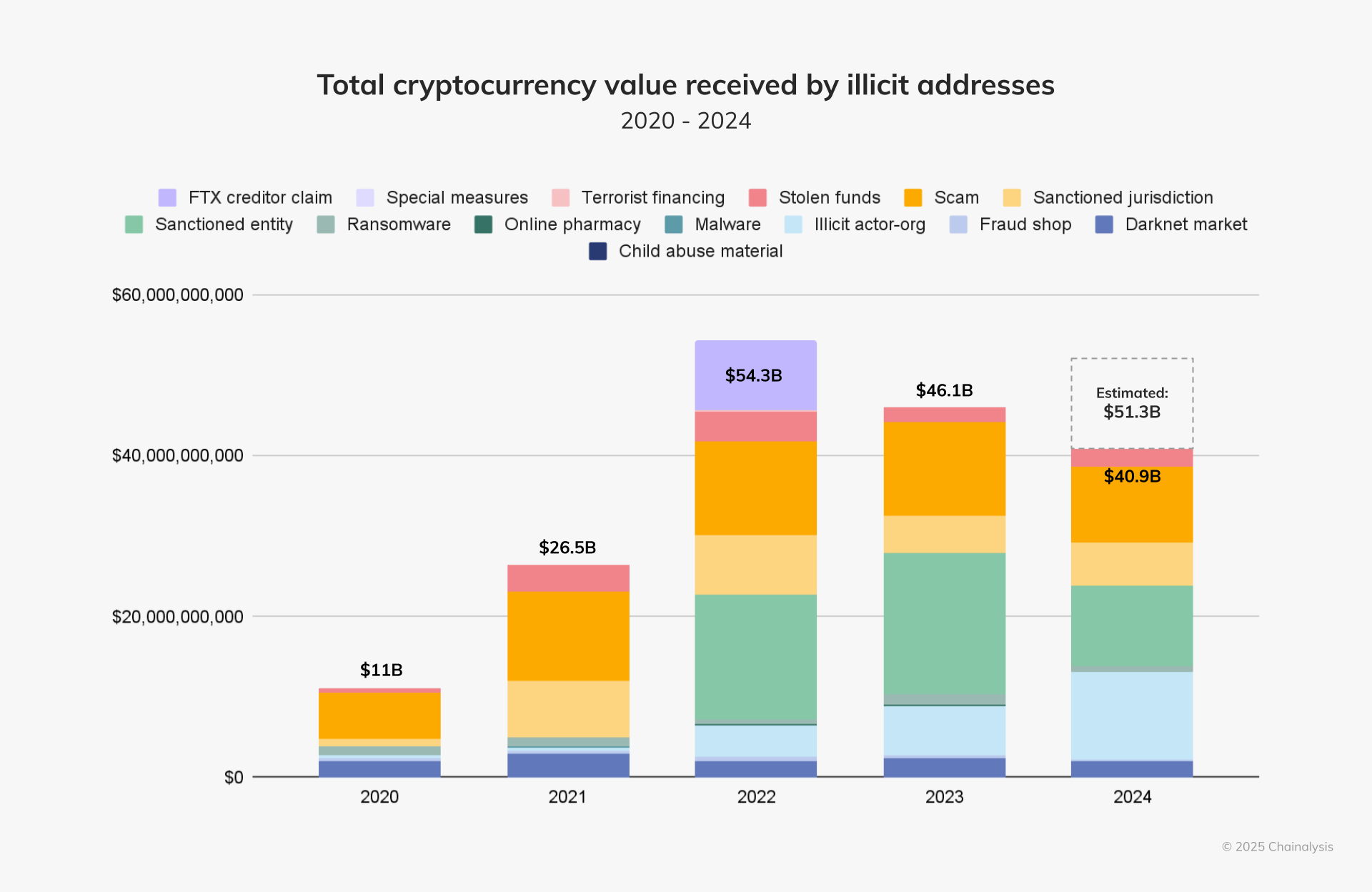
Our latest crypto crime report reveals a staggering $40 billion in illicit activity, yet this figure represents only part of a more complex criminal landscape. Criminal actors attempt to obscure their activities by moving funds between cryptocurrency and traditional financial systems, making detection and investigation more challenging.
A prime example is Operation Destabilise, where the UK’s National Crime Agency (NCA) disrupted a multi-billion dollar Russian money laundering network with ties to over 30 countries. The investigation revealed how criminals attempted to use cryptocurrency to move proceeds from traditional crimes. This interconnected nature of modern financial crime underscores why law enforcement must be equipped with the necessary tools and training to effectively identify, track, and seize illicit funds across both cryptocurrency and traditional financial systems.
The Chainalysis Asset Seizure Certification (CASC), our latest live certification, ensures law enforcement professionals develop a foundational understanding of the asset seizure process. This course combines traditional investigative techniques with cutting-edge blockchain expertise, providing hands-on training with our technology. From managing recovery seeds to handling evidence, CASC provides actionable, clear guidance every step of the way, including practical training with Reactor, Wallet Scan, and other key technology integrations such as Cellebrite.
Authorities worldwide have demonstrated that cryptocurrency seizures are both possible and effective in combatting crime. Notable examples include IRS-CI’s seizure of $3.36 billion of illicit funds tied to the Silk Road hack in 2021 and the UK’s largest Bitcoin seizure of £3 billion. Despite these successes, investigators often face significant obstacles to asset seizure, including limited training opportunities, reliance on unverified tools, and time-consuming manual processes that can delay investigations.
Seizing cryptocurrency: Lessons from the field
Even as cryptocurrency seizures become more common, investigators continue to face significant technical and operational challenges. Phil Larratt, former Senior Manager at the NCA and Director of Global Services at Chainalysis, recounts his experience: “When we first began encountering recovery seeds during operations, we lacked specialized tools and training. This meant potential delays to act quickly and missed opportunities for securing evidence.”
These challenges generally fall into three critical areas, discussed below, that investigators must address:
- Foundational crypto knowledge and handling evidence while maintaining chain of custody
- Navigating the technical complexity of crypto wallets and their underlying structures
- Tracing funds across multiple blockchains and through various obfuscation techniques
Foundational crypto knowledge and handling evidence while maintaining chain of custody
Possessing a robust understanding of crypto is crucial when handling evidence. Officers must be able to recognize crypto artifacts like recovery seeds and wallet addresses to effectively investigate crimes with crypto elements. For example, a seed phrase is a series of random words generated by a cryptocurrency wallet that secures access to the funds in that wallet. Proper identification of these artifacts enables investigators to follow established chain of custody procedures, ensuring evidence remains admissible throughout the investigation and legal process.

Navigating technical complexity of crypto wallets and their underlying structures
Dan Poar, a former detective in the UK and now a Senior Manager at Chainalysis, explains: “In many cases, investigators are overwhelmed by the sheer complexity of crypto wallets and derivation paths”. A seed phrase generates a master private key, which can then derive multiple addresses within the wallet. However, without understanding the correct derivation paths and knowing all the blockchains and wallets where the seed phrase has been used, investigators often miss opportunities to locate and seize all associated funds. What should be a straightforward seizure can become an iterative and laborious search, potentially leaving illicit funds undiscovered. Even when funds have been moved, these recovery seeds remain valuable evidence, helping attribute wallet control to specific individuals or criminal networks – but only if investigators have the right tools and training to properly analyze them.
Tracing funds across multiple blockchains and through various obfuscation techniques
Even after locating funds, investigators must still prove these assets are tied to illicit activity by tracing them from source to destination. Criminals attempt to hide their tracks using mixers, tumblers, and cross-chain bridges, while the rapid pace of digital transactions means even the slightest delays can result in the permanent loss of valuable assets. This is where comprehensive and trusted blockchain intelligence becomes crucial. Chainalysis provides investigators with industry-leading visibility across blockchains, exchanges, and services, enabling a complete, real-time, and actionable view of digital asset movements even when criminals attempt to obfuscate them. With this data advantage, combined with advanced blockchain analysis software and effective training, law enforcement can track, trace, and build strong cases for seizing illicit crypto funds.
The Chainalysis solution: Powerful technology and expert-led training
Chainalysis has developed an integrated solution that combines blockchain investigation software with specialized training to help law enforcement identify, trace, and seize crypto assets effectively. At the core of our solution are two powerful capabilities:
Chainalysis Reactor, the industry’s most comprehensive blockchain investigation software, enables investigators to follow the money wherever it leads. Even when the funds have been obscured or withdrawn, Reactor helps investigators track assets across blockchains, identify on- and off-ramps, and uncover real-world identities vital intelligence for building cases.
Wallet Scan, a new Chainalysis Labs innovation, revolutionizes wallet recovery by automating the discovery of derivation paths. This eliminates the need to manually reconstruct wallets, allowing investigators to focus on recovering assets instead. As Phil Larratt notes: “Wallet Scan would have been a game-changer, enabling us to identify and seize assets in real time. Moreover, even empty wallets can provide valuable opportunities to attribute illicit activity, helping investigators develop intelligence, secure evidence, and strengthen cases.”

Real-world impact
Investigators using Chainalysis have achieved significant successes in asset recovery:
-
- Recovering previously missed funds
“Wallet Scan helped us recover $11.4M in funds that had been missed during a wallet reconstitution back in 2019. At the time, several derivation paths were unknown—something Wallet Scan identified in minutes.” - Locating all associated assets from a large number of seeds
“Thanks to Wallet Scan, our bureau successfully seized over €4 million in crypto. It simplified an otherwise daunting task of recreating wallets from a large number of recovery seeds, ensuring no assets were overlooked. The ability to convert these Wallet Scan jobs into a graph also provided a critical advantage, allowing us to present evidence to suspects while they were still in custody.” - Real-time asset identification during an operation
“During a home search we located a seed phrase in a safe. We fired up Wallet Scan in situ and located $8 million of BTC. That value has since grown to approximately $14 million and will be returned to the victims.”
- Recovering previously missed funds
Looking ahead
Governments worldwide are enacting new legislation to address the unique challenges of crypto asset seizures. For example, the UK recently implemented new powers to seize crypto assets used by criminals, reflecting the growing recognition of crypto in asset recovery strategies. When executing these powers, ensuring personnel safety and managing risk remain top priorities for law enforcement. The added complications of dealing with recovery seeds in high-pressure environments make effective training and access to reliable tools essential.
The CASC, combined with powerful technology like Reactor and Wallet Scan, provides law enforcement with a complete solution for effectively handling crypto investigations and asset seizures. CASC is delivered by Chainalysis experts — a global team of over 120 multi-disciplinary professionals with extensive law enforcement and cryptocurrency experience — ensuring investigators are equipped with both the knowledge and practical skills needed for successful asset recovery. As Poar emphasizes: “The ability to trust your tools in high-pressure environments can make all the difference. CASC training ensures investigators are equipped to act decisively, even in the most complex cases.”
Take the next step
Join our growing community of certified law enforcement professionals equipped to handle cryptocurrency seizures. With CASC, you will learn how to:
- Identify when and how to seize crypto assets
- Secure and manage wallets safely
- Handle recovery phrases and digital evidence correctly
- Follow best practices for on-scene investigations
- Conduct safe and effective fund recovery
For agencies that want to enhance their crypto investigative capabilities beyond training, Chainalysis Global Services offers expert-led solutions, from complex investigations to tailored advisory support.

