Just over a decade ago, few people understood the emerging technologies surrounding cryptocurrency and blockchain, and even fewer investigators knew how to evaluate blockchain data and follow funds tied to crypto crime. Since then, the crypto landscape has evolved extensively, with criminals discovering new ways to leverage blockchain technology for nefarious purposes. In 2023 alone, illicit crypto addresses received at least $24.2 billion.
The transparency of the blockchain allows government agencies and law enforcement to track and trace criminal activity more easily than fiat currencies. With the increasing adoption of crypto worldwide, it’s critical that analysts and investigators leverage comprehensive blockchain data for lead generation, conduct crypto investigations, and operationalize their insights to disrupt illicit on-chain activity.
As criminal tactics grow more complex, Chainalysis continues to refine its end-to-end investigative blockchain analysis offerings. Our Chainalysis Crypto Investigations Solution supports everything from triaging initial reports of illicit crypto activity to investigating and seizing assets. This post showcases our latest innovations through the lens of a romance scam case.
Discover valuable leads and build compelling cases
In 2023, romance scams more than doubled in revenue, highlighting their devastating financial and emotional impact on victims. Also known as “pig butchering scams” for the way bad actors say they “fatten up” their victims to extract the most possible value, the scammer develops a relationship with their victim until they eventually persuade the victim to invest money in a fake investment opportunity.
Beginning with the discovery phase, here’s a hypothetical case study for how law enforcement can leverage Chainalysis to thoroughly investigate a crypto-related romance scam.
Rapid Lookup: Assess and escalate critical crypto insights
An officer interviews a victim who recounts losing thousands in crypto to a romance scammer. After gathering the victim’s account, the officer collects the crypto addresses where the victim sent funds and uses Rapid Lookup, a mobile-friendly web app, to conduct a quick assessment and verify this information.
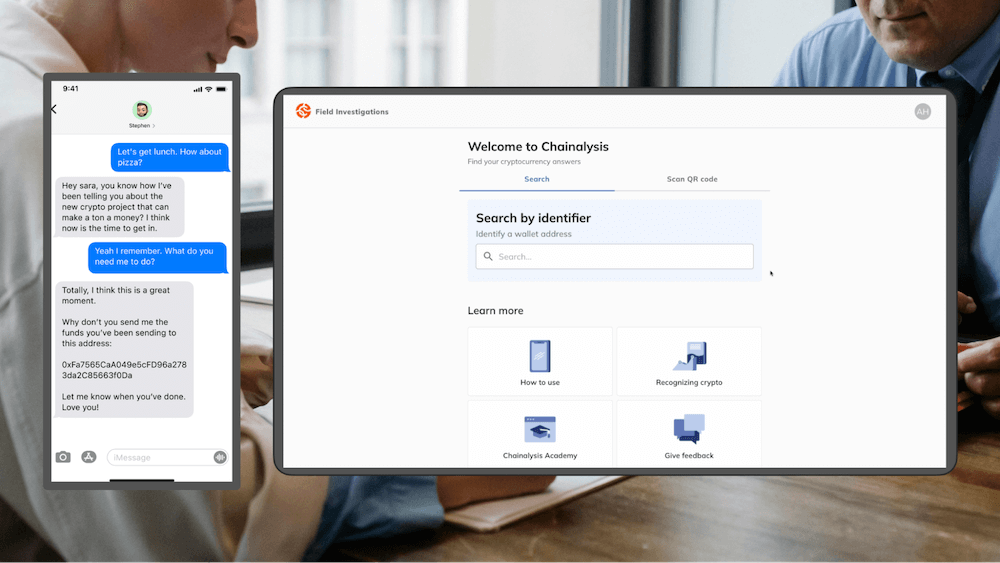
On entering the crypto address, Rapid Lookup reveals insights into associated on-chain activity. Here, the address is categorized as a “scam,” corroborating the victim’s story.
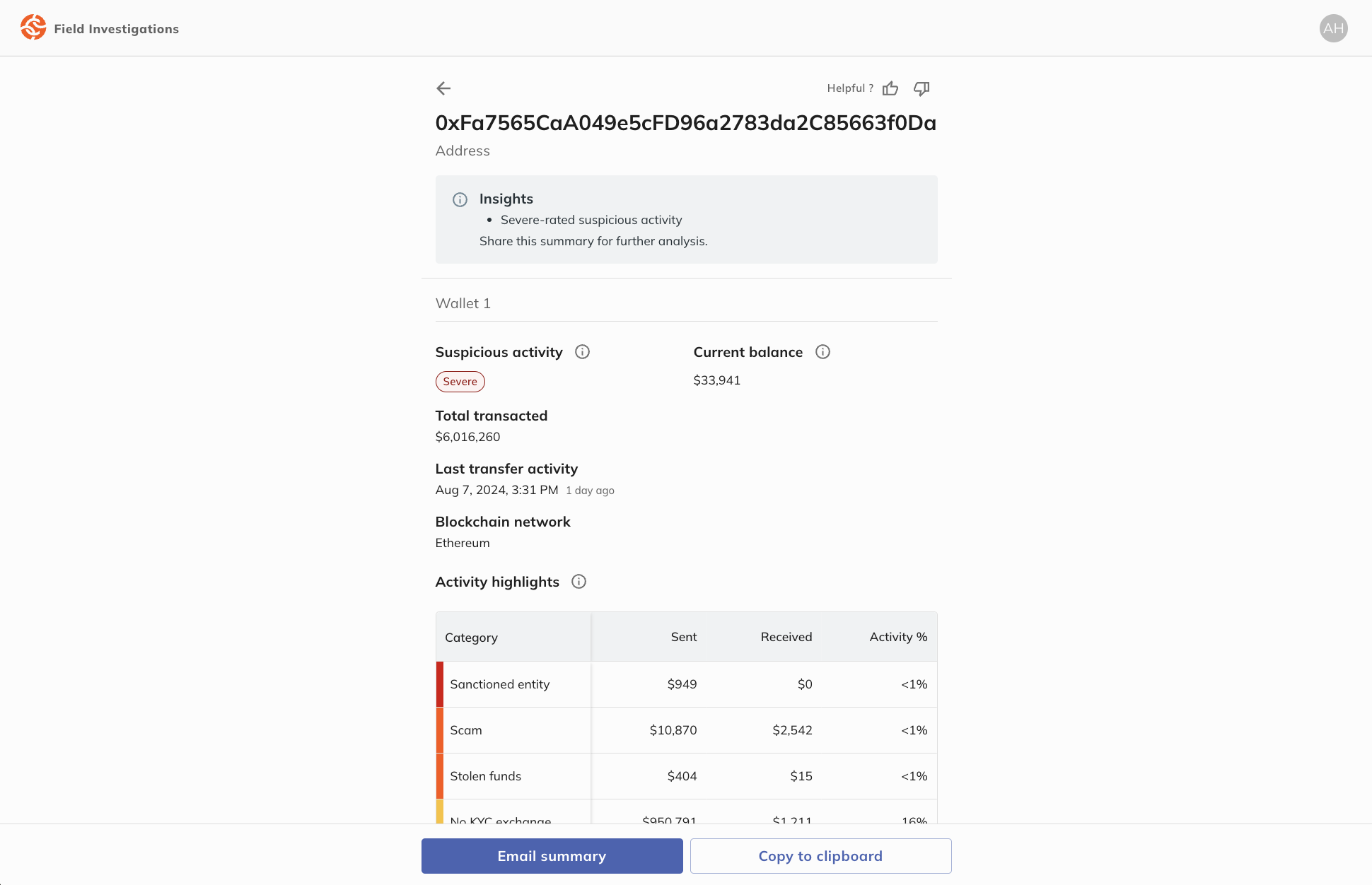
The search results also reveal the total amount transacted by this address and its Suspicious Activity level, driven by interactions with darknet markets, stolen funds, and more. Rapid Lookup is powered by industry-leading blockchain intelligence that connects real-world entities to on-chain activity, providing a clearer understanding of the entities and services behind wallets.
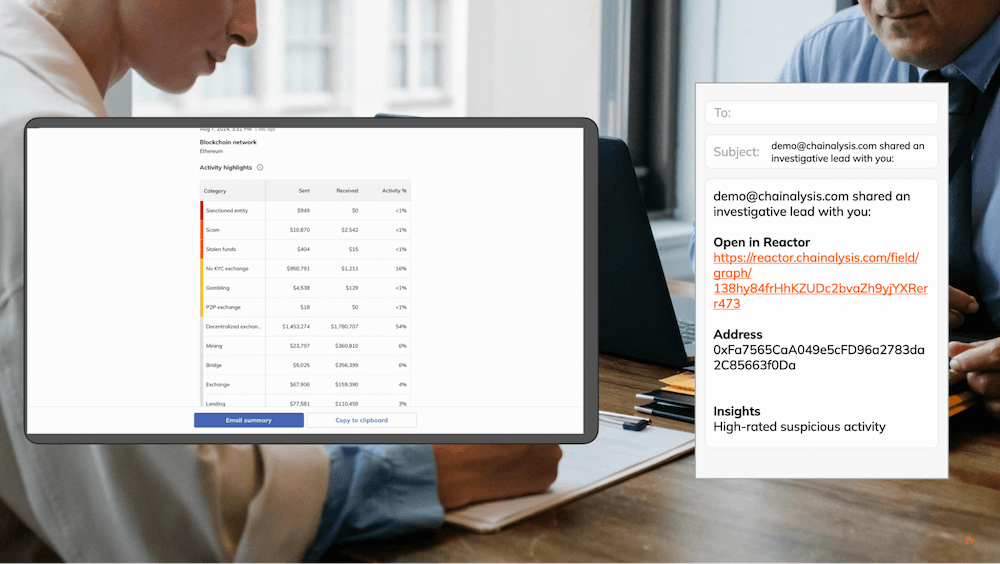
Examining the wallet’s activity more closely, the officer sees it received funds from sanctioned entities and likely off-ramped most of its balance at a crypto exchange. The officer escalates these findings in an email summary to an internal agency investigator for further review.
Analyze crypto activity and grasp the big picture
After triaging the initial information, the investigator analyzes the transactions; this can be a complicated process given the sophisticated methods criminals use to obscure their activity.
In this case, the investigator finds that the suspect sent crypto to a piece of bridging infrastructure called Socket.tech. Bridges are protocols executed via smart contracts that help move crypto from one blockchain to another and in our case, used to obfuscate funds.
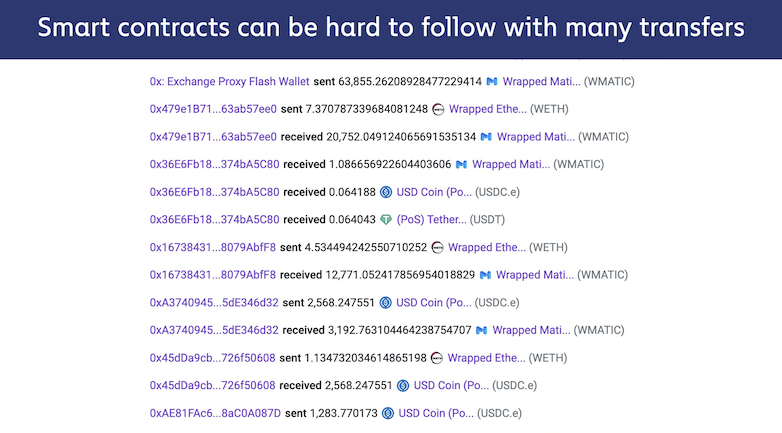
Investigations involving bridges can be complex due to the multiple transfers involved in a single step.
Transaction Explorer: Gain instant clarity on any transaction
The newly launched Transaction Explorer simplifies complex transactions, providing intuitive interpretations and the ability to automatically trace cross-chain bridge activity. Leveraging indexed blockchain data from Transpose, Transaction Explorer interprets on-chain data for over 180 million bridge transactions across hundreds of unique bridge protocols as well as decentralized exchanges.
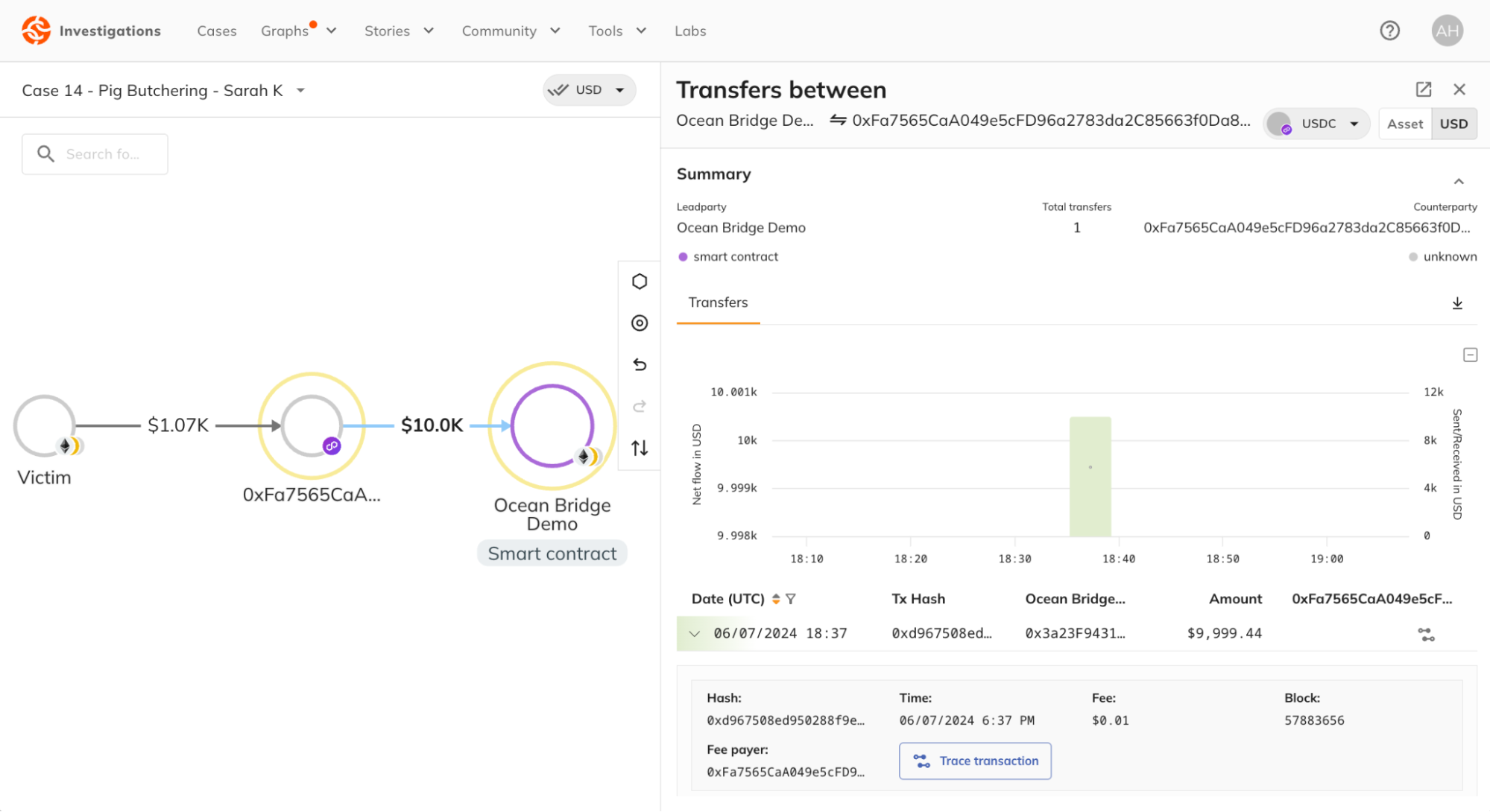
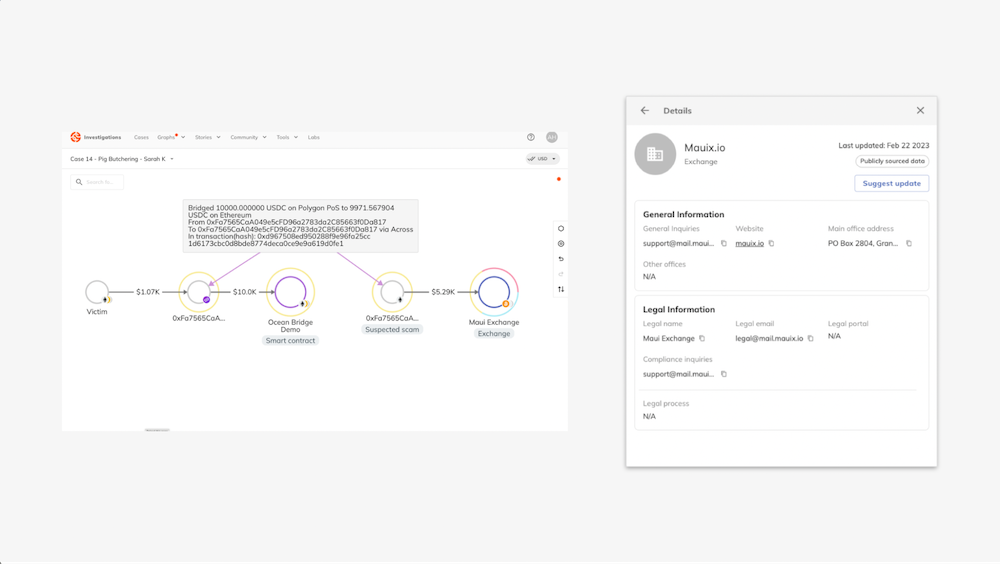
The investigator sees a $10,000 transfer made from the suspect to Socket.tech on the Polygon network. Transaction Explorer automatically follows the funds through the bridge, with all relevant information presented in one place.
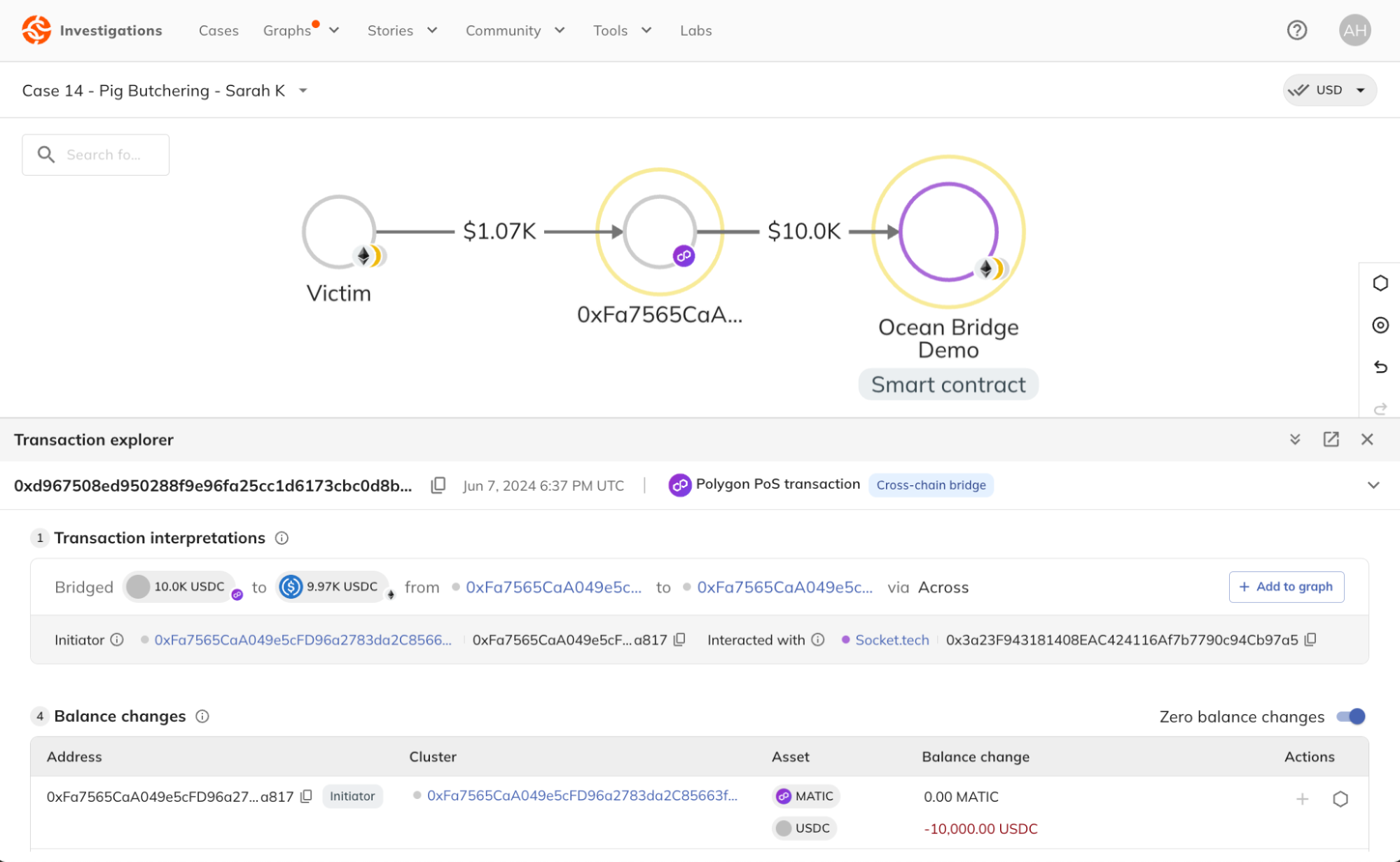
Transaction Explorer shows a summary of how the suspected scammer bridged $10K in USD Coin (USDC) from Polygon to Ethereum using the Across protocol.
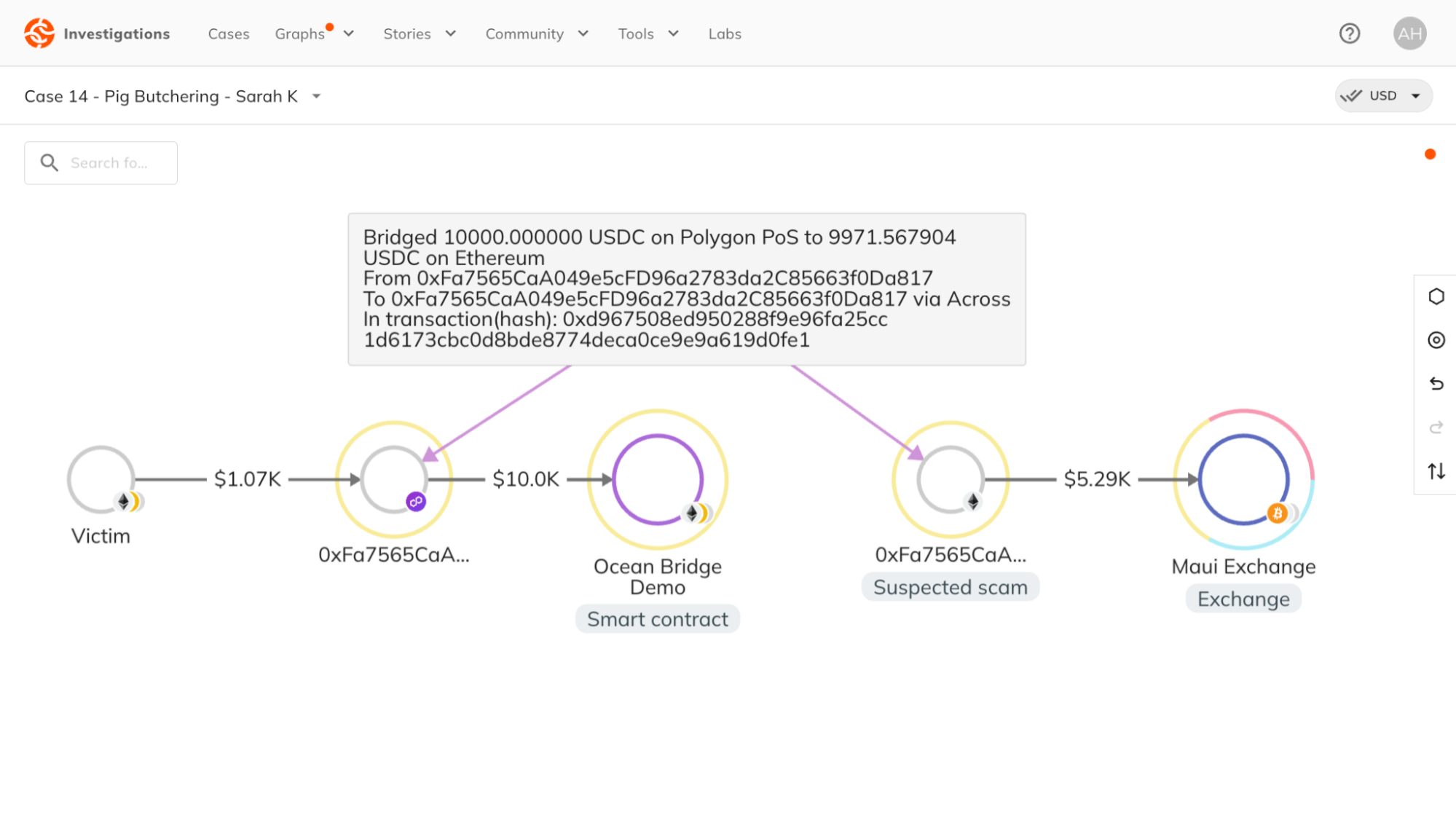
The investigator adds the destination wallet to the graph, automatically generating an annotation with details of the bridged transaction and transaction IDs. Continuing to trace the funds, the investigator discovers the wallet sent $5.29K in USDC to Maui Exchange.
For a deeper dive into how Transaction Explorer clarifies any transaction, join this upcoming webinar.
Signals: Suspected categorical insights to assist investigations
Often, investigators trace funds and encounter unknown on-chain entities. Signals appear as suspected category labels, an example of which is shown in the graph above.
Signals surfaces preliminary insights on these entities based on their activity, providing a new layer of entity intelligence useful for generating leads, supporting inquiries, and validating hypotheses. Currently, Signals includes insights for over 1.1 million clusters, with more added regularly.
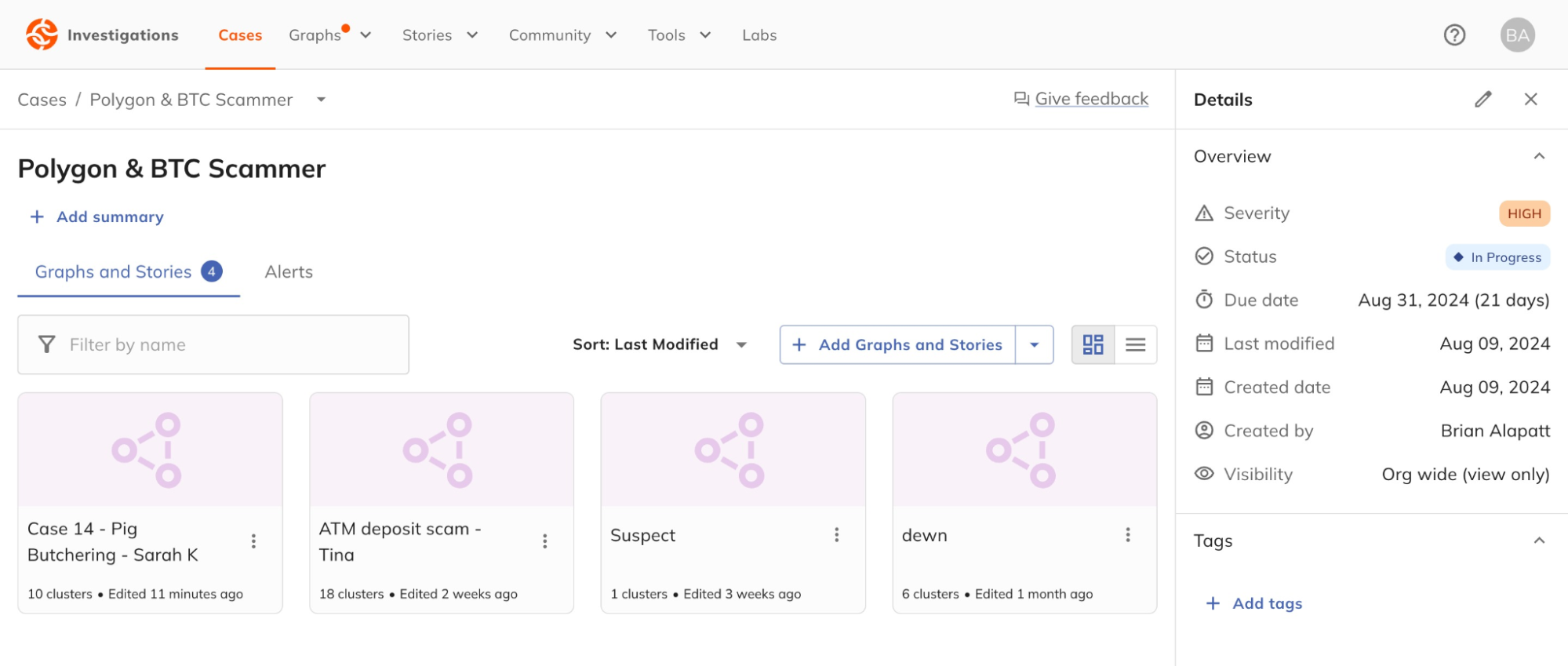
Case Workspace: Enhance team collaboration
Organizing digital evidence for multiple cases can be challenging, especially when collaborating across departments. Case Workspace allows investigative teams to organize, share, and collaborate on cases. Teams can share data and artifacts such as graphs, stories, and alerts, and assign case names, severity levels, statuses, due dates, and tags to document and prioritize their efforts.
Solving the most complex challenges with Chainalysis Labs
As criminals continue to adapt their methods, staying ahead requires constant innovation. Chainalysis Labs serves as an R&D hub for the latest innovations in blockchain intelligence. From an experimental environment, Labs offers eligible customers the opportunity to preview and test out some of the most cutting edge capabilities before they go to market.
Let’s explore how the latest Labs functionality can help resolve more complex investigative challenges and bring resolution to our case.
Bitcoin Transaction Search: Locate specific transactions based on time, date, amount
Mixers and tumblers can obfuscate the flow of funds, leading to investigative dead ends. Bitcoin transaction search helps investigators overcome these challenges by filtering and locating specific transactions using over 45 relevant search parameters, including time, date, amount, and transaction fingerprints.
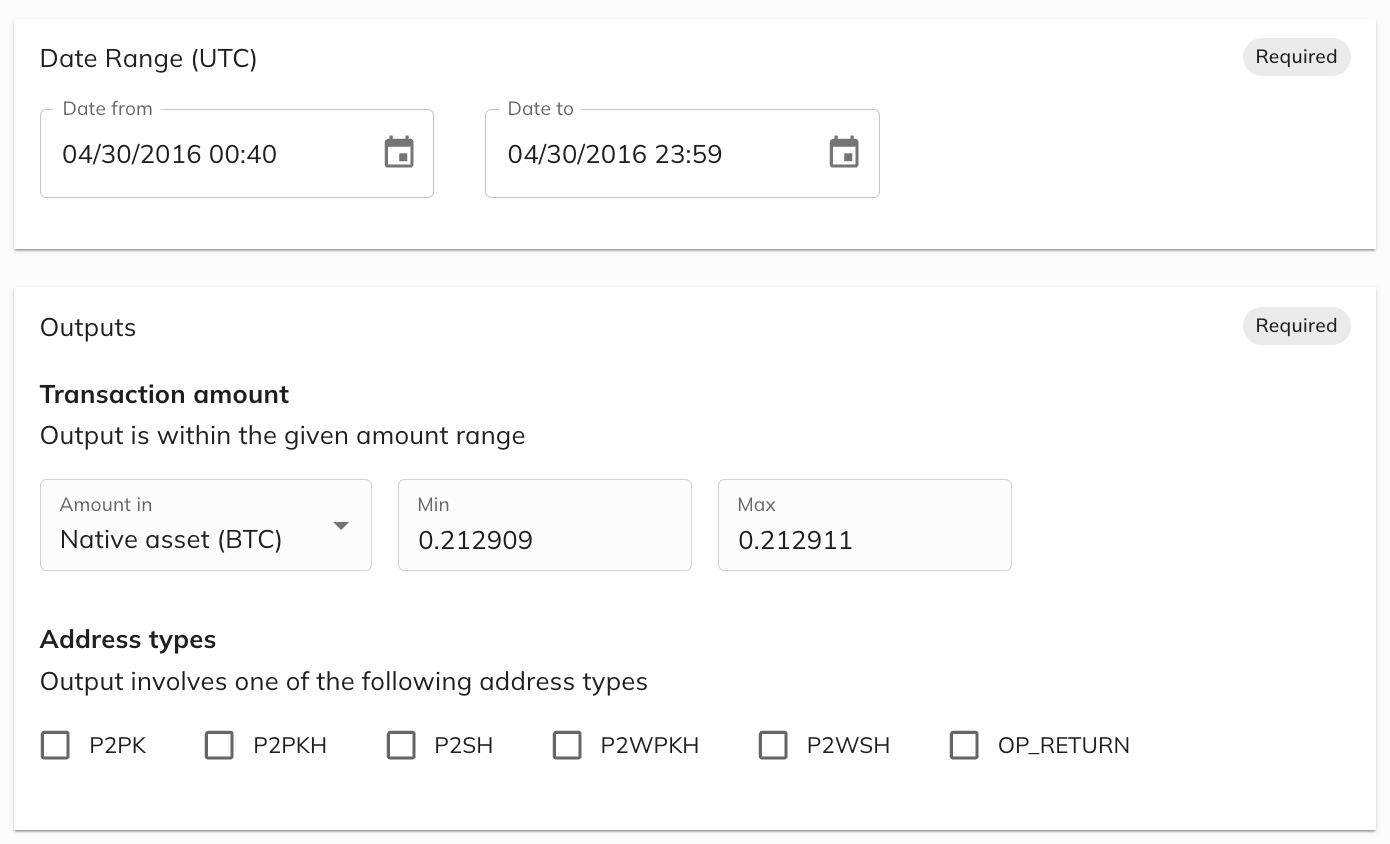
This feature is particularly useful for manual demixing workflows where specific transaction outputs need to be identified based on the available information. For example, investigators can pinpoint the exact transaction matching the details of an illicit transfer, making it easier to trace the flow of funds through complex money laundering techniques.
Advanced Demixing: Trace obscured transactions
Chainalysis has also continued to refine its automated demixing capabilities for select use cases, making it possible for law enforcement to more easily simplify the complexities of tracing obscured crypto transactions that were previously investigative roadblocks.
For specialized case support involving obfuscation techniques, please contact our expert team.
Pursue criminals and safeguard communities
In this case, the investigator discovers Maui Exchange was the final destination of the suspect’s funds and swiftly takes action to prevent further movement. Let’s look at the capabilities Chainalysis offers for pursuing criminals at this phase of the investigation.
Service Provider Inquiry: Streamline communication with Virtual Asset Service Providers
Using Service Provider Inquiry — previously known as Directory — the investigator requests the suspect’s KYC information from the exchange and requests that the funds be frozen before the criminal can move them.
The investigator uses this KYC data to conduct a records check of law enforcement databases, potentially securing enough evidence to obtain a warrant for seizing illicit funds.
Wallet scan: Quickly check a seed phrase for all associated wallet activity
During a search warrant execution, investigators may find seed phrases and other actionable evidence. With many popular cryptocurrency wallets, a single seed phrase can link to millions of addresses, making it a needle-in-a-haystack challenge.
Wallet Scan, developed by Chainalysis Labs, streamlines this process. Investigators quickly identify asset seizure opportunities by assessing all associated wallets, including balances and historical activity.

Wallet Scan operates securely offline, maintaining the chain of custody. This information is never stored by Chainalysis. It scans funds across 35 popular wallets and 15 blockchains, providing visibility to millions of addresses at scale.
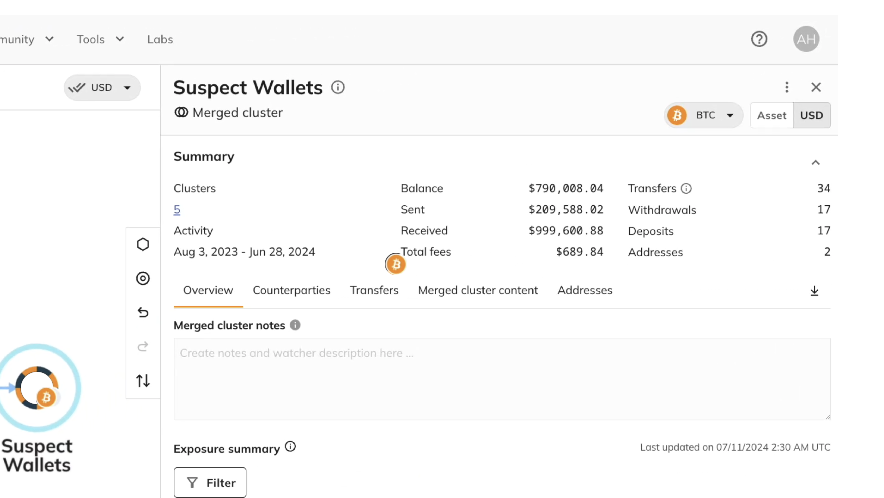
Bringing it back to our romance scam example, we can see how Wallet Scan can reveal further insights. Here, it shows $790K worth of illicit funds on addresses tied to the seed phrase. Investigators seized the funds, arrested the suspect, and provided restitution for the victim.

Advance your investigations with Chainalysis
Government agencies and investigators tackle the complexities of crypto-enabled crime with a holistic crypto investigations solution. From quickly discovering leads to tracing specific illicit activity, navigating through obfuscation tactics like cross-chain bridges, and seizing assets, Chainalysis advances and accelerates your investigative efforts.