Agencies like the Office of Foreign Assets Control (OFAC) of the U.S. Department of the Treasury and its equivalents in other countries implement sanctions through the targeting of countries, regimes, individuals, and entities that are considered threats to national security and foreign policy. Traditionally, sanctions enforcement relies on the cooperation of mainstream financial institutions, but some bad actors have turned to cryptocurrency to circumvent these third party intermediaries, giving policymakers and sanctioning bodies new challenges with which to grapple. However, cryptocurrency’s inherent transparency, along with the willingness of compliant cryptocurrency services — in particular, the many centralized exchanges that function as the link between crypto and fiat — have demonstrated that sanctions enforcement is possible in the crypto world.
In this section, we’ll look at how the U.S. government’s crypto-related sanctions strategy has evolved over time, examine the types of entities that it has sanctioned so far, and analyze the impact of those sanctions on the entities themselves and the wider crypto crime ecosystem.
OFAC’s cryptocurrency-related sanctions are on the rise since 2021
2018 saw OFAC’s first crypto-related sanctions, when it designated two Iranian nationals associated with the SamSam ransomware strain and included Bitcoin addresses linked to the individuals as identifiers on their Specially Designated Nationals And Blocked Persons (SDN) List entries. For the next two years, virtually all cryptocurrency addresses included as sanctions identifiers were personal wallet addresses controlled by individuals, with an average of two addresses per crypto-related designation in 2018, four in 2019, and nine in 2020.
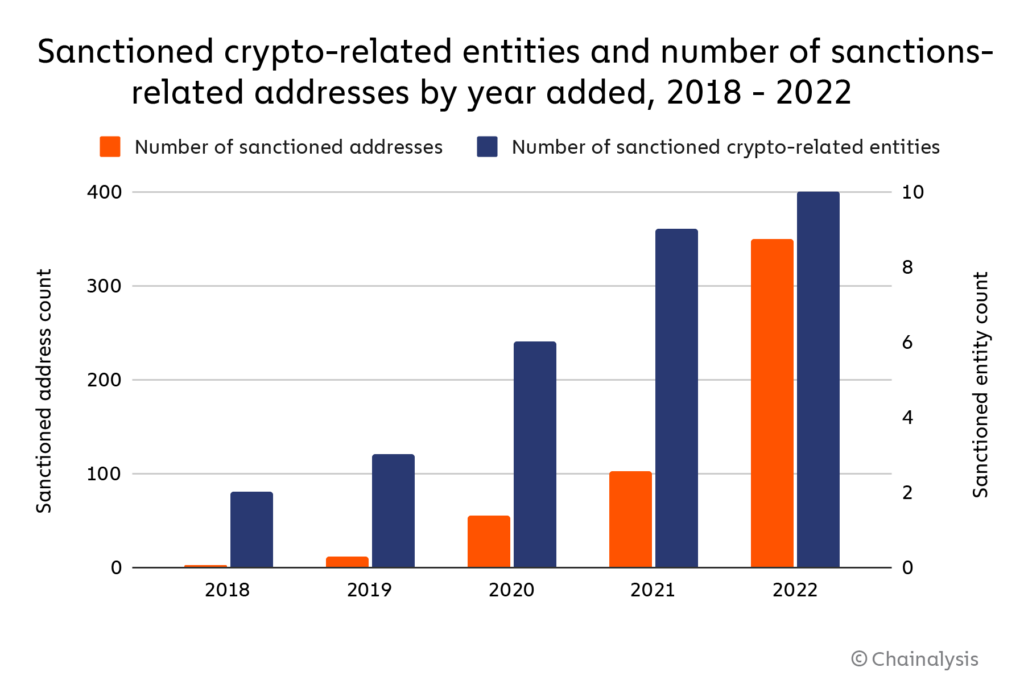
That changed starting in 2021 though, when OFAC began to designate entire crypto services as opposed to just individual bad actors — overall, the average number of addresses per sanctioned entity reached 35 by 2022, with some designations containing over 100 cryptocurrency addresses as identifiers. As seen below with the expanding funnel of sanctioning activity, OFAC’s efforts have increased across three dimensions, targeting larger entities/services, more diverse service types, and doing so for a wider array of reasons.
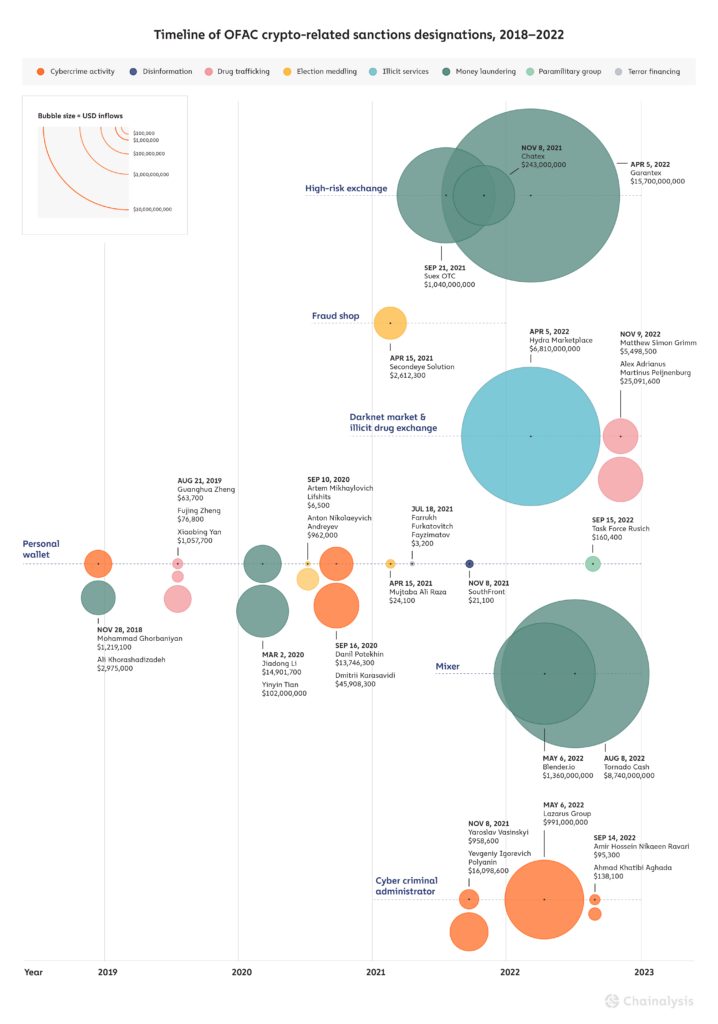
2022 has seen some of OFAC’s biggest cryptocurrency service designations to date. Three in particular are notable not just due to their size, but also in how each highlights unique challenges in enforcing OFAC sanctions against different types of crypto entities: darknet market Hydra, decentralized mixer Tornado Cash, and Russia-based cryptocurrency exchange Garantex. But before we get into those, we’ll provide an overview of all crypto-related sanctions designations over the last year.
Sanctioned crypto-linked entities in 2022: Who they are and what they do
Here’s the breakdown of the individuals and entities with cryptocurrency nexuses sanctioned in the U.S. in 2022, along with the reason OFAC sanctioned them.
| Name | Reason for sanction |
|---|---|
| Lazarus Group | Hacking/crypto theft on behalf of North Korean government |
| Ahmad Khatibi Aghada | Ransomware |
| Amir Hossein Nikaeen Ravari | Ransomware |
| Alex Adrianus Martinus Peijnenburg | Drug trafficking |
| Matthew Simon Grimm | Drug trafficking |
| Hydra Marketplace | Darknet market and money laundering |
| Garantex | Money laundering |
| Blender.io | Money laundering |
| Tornado Cash | Money laundering |
| Task Force Rusich | Russian paramilitary group in Ukraine |
OFAC sanctioned a relatively even mix of individuals and different types of entities in 2022, citing activity such as cybercrime (including ransomware), drug trafficking, money laundering, and in the case of Task Force Rusich, participation in Russia’s invasion of Ukraine. Again, this diversity of entities represents a huge change compared to OFAC’s pre-2021 designations, which were all against individuals and, at the blockchain level, comprised of only a relatively small number of personal wallets.
Exploring pre and post-designation activity for three of 2022’s most notable sanctioned entities: Hydra, Garantex, and Tornado Cash
In order to examine the effects of sanctions on illicit cryptocurrency activity, let’s look at how a few of 2022’s most notable sanctioned entities behaved before and after their OFAC designations. We’ll analyze three services: Hydra, Garantex, and Tornado Cash. First, some brief background on each:
- Hydra was the largest darknet market in the world until its servers were seized by German police, concurrent with its designation by OFAC in April 2022, effectively shutting down the marketplace. Based in Russia, Hydra not only facilitated drug sales, but also offered money laundering services to cybercriminals, including ransomware attackers.
- Garantex is a high-risk crypto exchange based in Russia and was sanctioned at the same time as Hydra for similar money laundering activity. Unlike Hydra, Garantex continues to operate following its designation.
- Tornado Cash is a decentralized mixing service on the Ethereum blockchain that was sanctioned in August 2022 (and again in November) for facilitating money laundering, primarily in relation to funds stolen in cryptocurrency hacks by cybercriminals associated with North Korea. Tornado Cash is currently the only DeFi protocol to have been sanctioned by OFAC — all other designations have been centralized services or personal wallets. As a DeFi protocol, no person or organization can “pull the plug” as easily on Tornado Cash as they could with a centralized service, which has led to questions around the feasibility of sanctioning the service and who, if anyone, can be held responsible for criminal activity it facilitates.
On-chain data can tell us more about the types of entities transacting with these services prior to their sanctions designations.
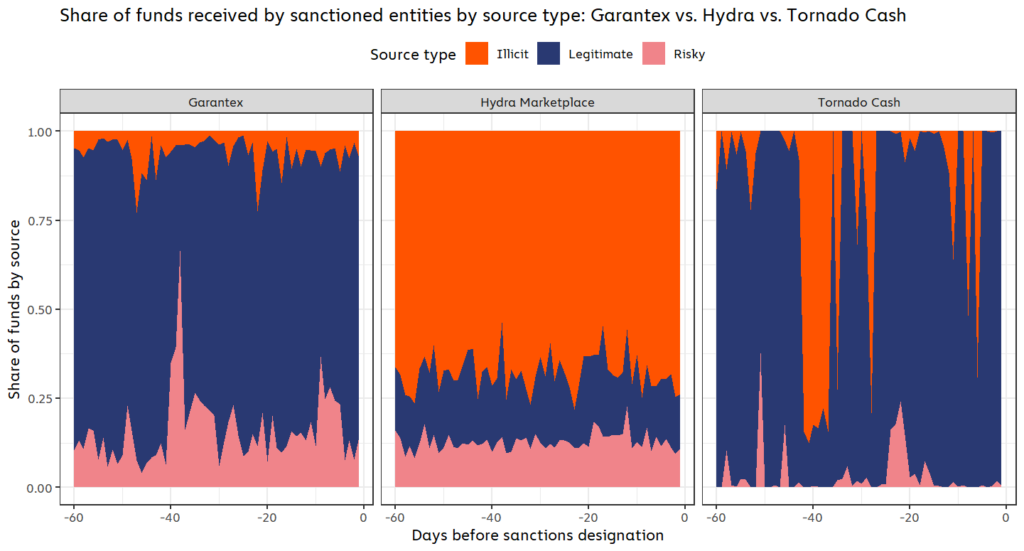
Note: Illicit transaction activity refers to transactions in which one or more counterparty addresses are associated with an illicit entity, such as a darknet market or ransomware attacker. Risky activity refers to transactions in which one or more counterparty addresses are associated with a risky entity, such as a high-risk exchange or gambling service. Legitimate activity refers to transactions in which one or more counterparty addresses are associated with entities that are not inherently criminal or risky, such as personal wallets or exchanges.
The chart above shows the breakdown of each sanctioned entities’ source of incoming funds in the 60 days prior to their designations based on whether the sending wallets were associated with legitimate, illicit, or risky activity. A few things stand out:
- Hydra had by far the most criminal activity of the three services, with 68.2% of all incoming funds coming from illicit addresses, and 12.6% coming from risky addresses.
- Garantex, on the other hand, saw 6.1% of its inflows come from illicit sources and 16.1% from risky sources. 6.1% may sound like a small share of inflows, but it actually puts Garantex firmly on the riskier end of the spectrum for exchanges — over the same 60-day period, centralized exchanges as a whole received on average just 0.3% of funds from illicit addresses.
- 34% of all funds sent to Tornado Cash came from illicit sources, but this number fluctuated greatly depending on the day, with most illicit funds coming in brief spikes.
Let’s dig deeper into the specific types of illicit entities that sent funds to each of these sanctioned services.
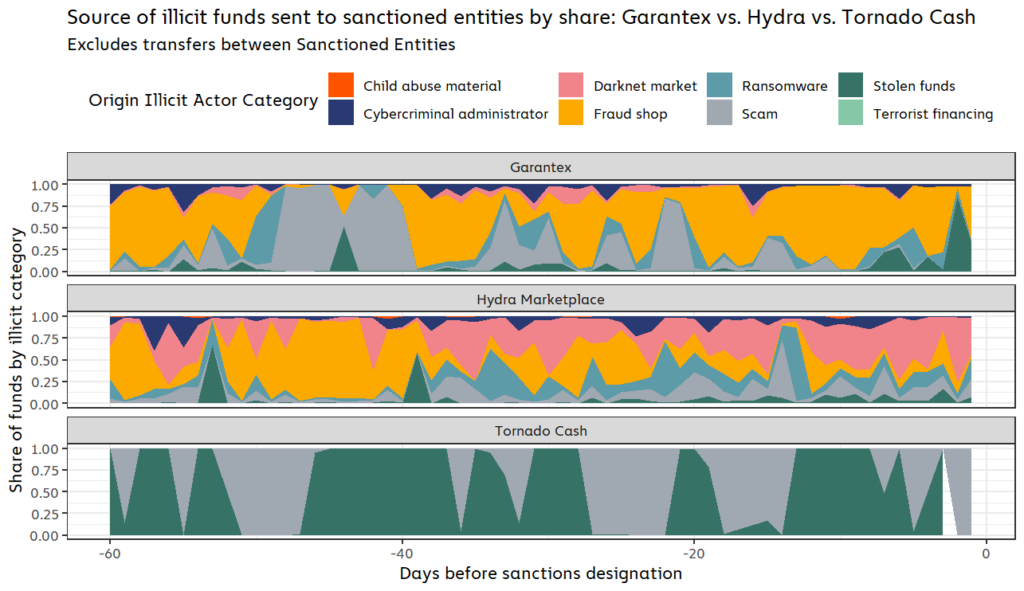
Garantex and Hydra both received funds from a wide array of illicit actors in the 60 days leading up to their sanctions designations, including fraud shops, scams, and most notably, ransomware. During this time period, Hydra received roughly $176,000 worth of cryptocurrency from ransomware addresses, representing 2.2% of all funds sent by any ransomware address. Garantex was even worse, taking in $931,000 from ransomware addresses, or 11.6% of all funds sent by ransomware addresses. The numbers underscore how crucial these services — especially Garantex — have been to enabling ransomware attacks. We must also note that these dollar figures may grow as we continuously identify more ransomware-related wallets over time.
Tornado Cash’s illicit activity was concentrated to just two forms of cybercrime: Crypto hacks and scams. While not apparent from the graph above, we should note that stolen funds make up nearly all of that total, at 99.7% of all illicit funds received during the entire 60-day time period. The inflows of stolen funds come in periodic spikes, which in turn drive the spikes in overall illicit inflows to Tornado Cash that we saw in the previous graph. The Harmony Bridge hack, which occurred in June 2022, roughly 45 days before Tornado Cash’s sanctions designation, accounted for 65.7% of the mixer’s total stolen fund inflows during this period. This pattern of isolated, unique events, contrasts with the more constant flow of illicit activity from services such as darknet markets, which produce a steady stream of funds.
How did sanctioned entities behave post-designation? It depends.
On-chain data shows that each of the three sanctioned services were affected differently by their designations. The charts below show cryptocurrency inflows for Garantex, Hydra, and Tornado Cash in the 60 days before and after they were sanctioned.
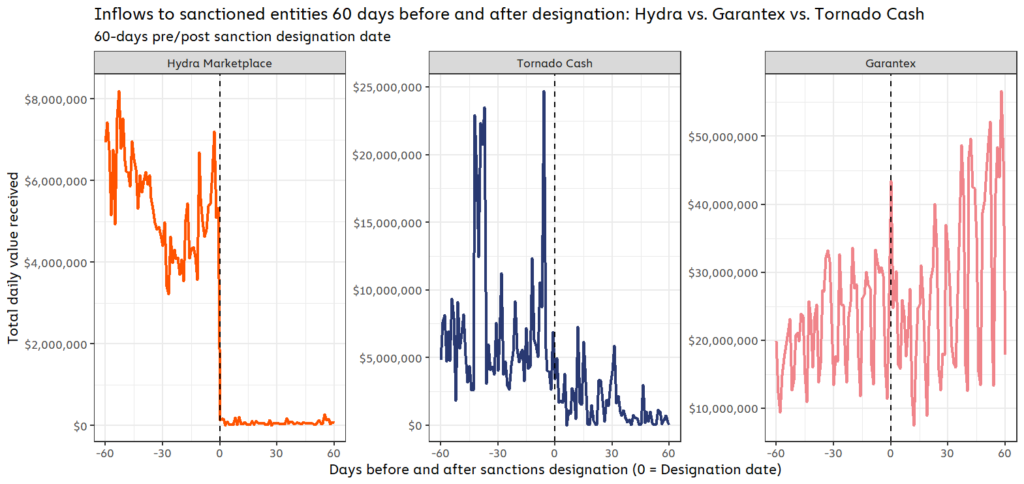
On one end of the spectrum, we have Hydra. Its inflows dropped to zero as soon as it was sanctioned because the service was also seized in a coordinated law enforcement action at the same time.
On the other end of the spectrum is Garantex, which wasn’t seized upon being sanctioned, and actually saw its crypto transaction volume steadily increase post-designation. For example, in the four months up through April when Garantex was sanctioned, the high risk exchange had averaged $620.8 million in monthly inflows. After the sanctioning event, Garantex’s inflows rose considerably, with an average of approximately $1.3 billion in monthly inflows through October. This is most likely due to the fact that Garantex and most of its users are based in Russia. The Russian government has not enforced U.S. sanctions, leaving users not subject to U.S. jurisdiction with virtually no incentive to stop using Garantex. In fact, Garantex explicitly stated its intent to continue operating in social media posts immediately following the designation.
Tornado Cash falls in the middle of the spectrum, as its activity dropped significantly after being sanctioned, but hasn’t ceased completely. As we discussed previously, Tornado Cash runs on smart contracts that can’t be taken offline the way a centralized service can, so there’s nothing except the legal consequences of sanctions violations stopping anyone from using it. However, the Tornado Cash website that acted as a front-end for easy access to the mixing service was taken down, making it more difficult to access. And, as a global service, Tornado Cash likely had more users who could face consequences for violating U.S. sanctions, or who would be cut off from using other services if their wallets displayed exposure to Tornado Cash following its designation.
Digging deeper into these aggregate inflow patterns, we also see that different types of counterparties reacted differently to each service’s sanctions designation. We’ll leave Hydra out here, as we already saw above that its inflows dropped to zero due to the seizure of its darknet site infrastructure.
Here’s how inflows to Garantex from different types of services and entities changed following its sanctions designation.
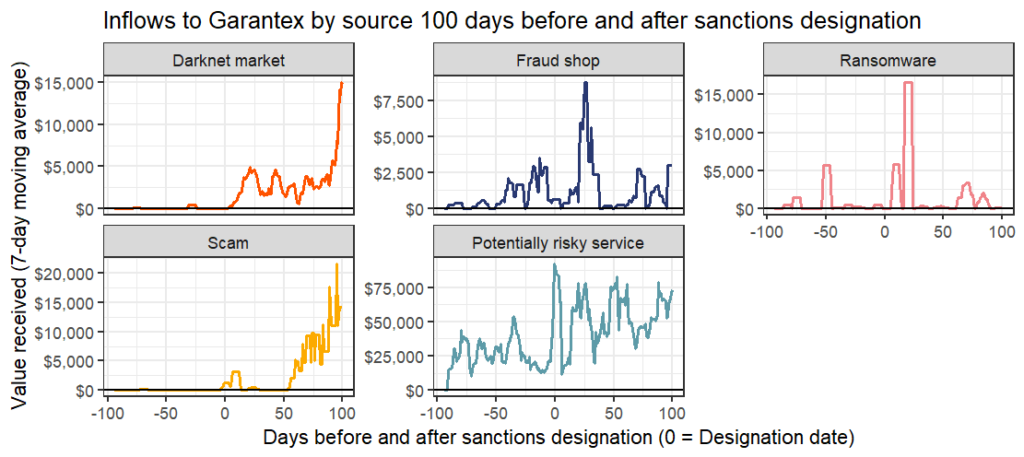
Most of Garantex’s counterparties continued to use the service at roughly the same levels they did before the exchange was sanctioned, apparently unperturbed by the designation. In fact, darknet markets and scammers actually sent more funds to Garantex following the designation, perhaps reassured that the exchange would be unlikely to try and curb their activity.
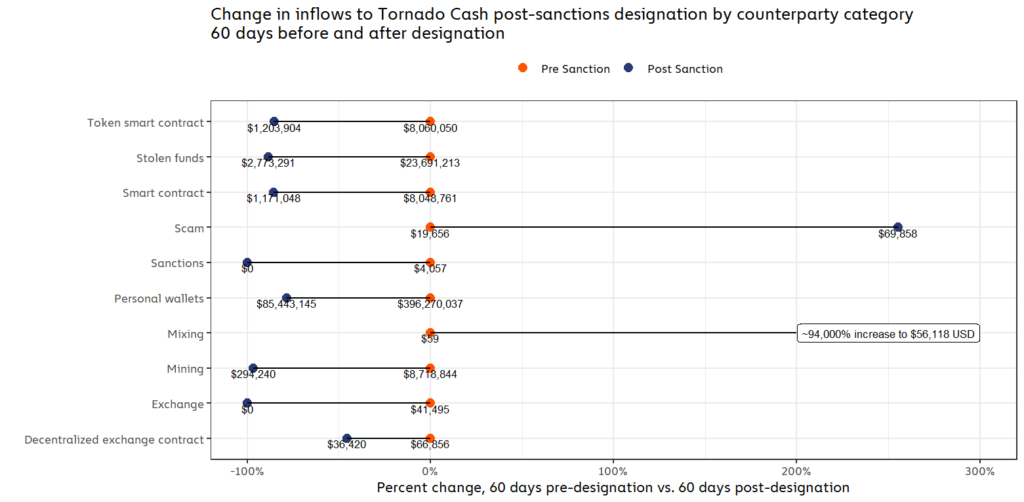
Tornado Cash, on the other hand, saw drops in inflows from virtually every category, the exceptions being an increase in funds sent from scammers and mixing services. However, despite the percentage increases, neither category had sent a particularly high volume of funds to Tornado Cash before its sanctions designation anyway. And, in the case of scams, the increase was the result of a single YouTube-based liquidity bot scam that saw inflows over four deposits, and likely does not reflect a wider trend.
Did sanctions affect criminal users of designated services?
Four of the entities sanctioned in 2022 were designated at least in part due to their provision of money laundering services to other criminals, such as ransomware attackers, scammers, and hackers. Those services were:
- Hydra
- Garantex
- Blender.io (another mixer)
- Tornado Cash
It follows that one goal of those sanctions would be to disrupt the criminals who relied on those services for money laundering. Did this end up happening in practice? Or, put another way, if I was a crypto criminal who relied on one (or more) of these money laundering services, did I see less revenue than expected after that service was sanctioned?
We attempt to answer this question below by quantifying the average difference between actual inflows and expected inflows for illicit entities who used the money laundering services listed above prior to their designations. In order to calculate expected inflows, we used inflows to other illicit services in the same criminal categories who did not use those sanctioned money laundering services as a control group. These other illicit services help to establish a revenue baseline for the two months following each money laundering service’s sanctions designation. [1] We found that illicit entities who used sanctioned services saw significant lost potential revenue across nearly every crypto crime category in the two months following the sanctioning event — for example, the average darknet market who had previously sent funds to one of the sanctioned services saw an estimated $25,000 less revenue in the two months following that service’s designation than they likely would have had the service not been designated.
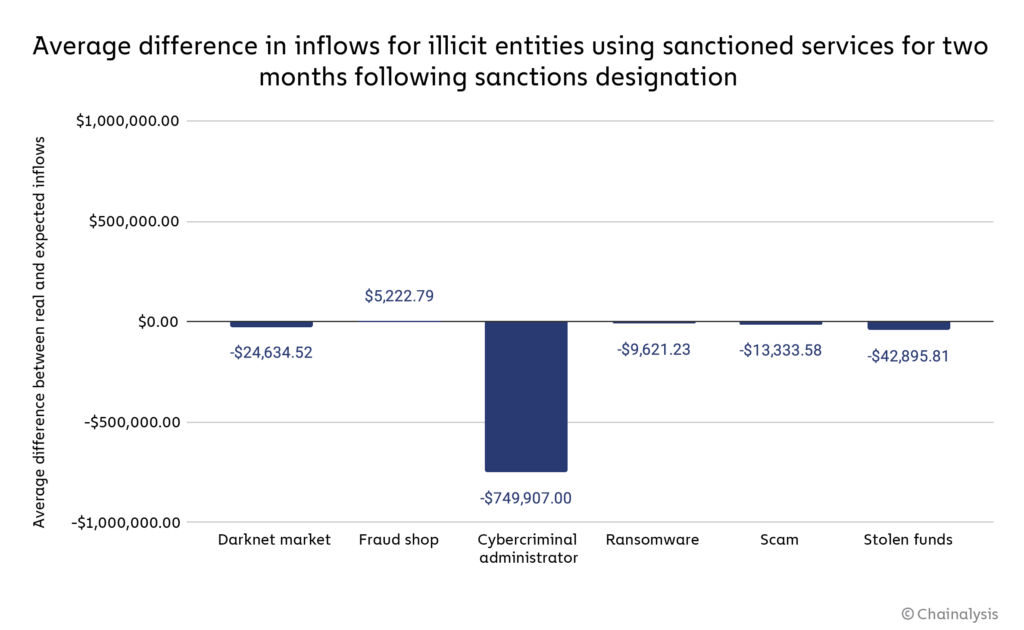
The most-affected category were cybercriminal administrators, who on average saw an estimated $750,000 decrease in revenue due to the sanctioning of money laundering services they had previously used. The one exception to this trend was fraud shops, who on average saw nearly $5,000 more revenue than we would estimate absent the sanctioning of a money laundering service counterparty.
It’s important to keep in mind that the graph above shows only the average estimated change in revenue for counterparties of sanctioned money laundering services. With several distinct entities in each category who had previously used those money laundering services, the estimated total losses by category are much higher.
| Illicit category | Number of entities | Average inflows change | Total revenue change for category |
| Darknet market | 11 | -$24,634.52 | -$270,979.67 |
| Fraud shop | 10 | $5,222.79 | $52,227.91 |
| Cybercriminal administrator | 20 | -$749,907.00 | -$14,998,139.98 |
| Ransomware | 6 | -$9,621.23 | -$57,727.38 |
| Scam | 23 | -$13,333.58 | -$306,672.24 |
| Stolen funds | 42 | -$42,895.81 | -$1,801,624.08 |
We should caveat these findings by noting that, while we’ve taken steps to control for other factors and analyze only the revenue changes brought on by the sanctioning of their money laundering services, there could be other reasons these dependent entities’ revenue might have changed following the sanctions designations. We should also emphasize that we’re only looking at changes to revenue in the two months following the money laundering services’ designations — it’s entirely possible and even likely that any revenue hits to illicit entities will be temporary, and that they’ll soon find alternative money laundering services that haven’t been sanctioned. Nonetheless, our findings suggest that sanctions against money laundering services did in fact disrupt the illicit entities who relied on those services, at least temporarily, and impacted their bottom line.
Key takeaways: Impact of 2022 crypto sanctions depends on jurisdiction and technical constraints
New technologies and forms of value transfer change the landscape of financial crime enforcement. OFAC is learning this first-hand, and has broken new ground in the last two years with its efforts to move beyond individuals and designate cryptocurrency services that facilitate money laundering and other harmful forms of crypto-based activity. The three examples we focused on above show how different variables impact agencies’ ability to levy sanctions against those services.
First, the case of Hydra teaches us that sanctions can be extremely effective against entities with key operations in cooperative jurisdictions. Hydra’s servers were located in Germany — German law enforcement coordinated with U.S. agencies, and moved to seize Hydra’s servers, striking a fatal blow to the organization, in addition to the sanctions levied by OFAC on the darknet market.
Second, the case of Garantex shows what happens when there is an absence of international cooperation. While Garantex has been largely cut off from the compliant exchange ecosystem, Russia has declined to enforce sanctions against the service, so it continues to operate mostly unencumbered. This case shows that it is difficult to effectively sanction entities whose home jurisdictions have no formal cooperation channels with OFAC.
Finally, the case of a decentralized service like Tornado Cash is more complicated. While its front-end website was taken down, its smart contracts can run indefinitely, meaning anyone can still technically use it at any time. That suggests sanctions against decentralized services act more as a tool to disincentivize the service’s use rather than cutting off usage completely. In the case of Tornado Cash, those incentives appear to have been powerful, as its inflows fell 68% in the 30 days following its designation. That’s especially important here given that Tornado Cash is a mixer, and mixers become less effective for money laundering the less funds they receive overall.
These case studies provide a model of how OFAC and its international equivalents can approach sanctions designations against different kinds of crypto-related entities. It will be interesting to see how these patterns develop as sanctioning bodies continue to improve their ability to effectively target sanctions against different kinds of illicit cryptocurrency services, in partnership with other agencies in the U.S. and internationally.
Endnotes:
[1] Interventions always need to factor in what would otherwise have been. In this case, we used data on the non-counterparties of sanctioned services to estimate what total on-chain aggregate revenue inflows for counterparties might have looked like absent a sanctioning event. Non-counterparties are those entities that sent no funds to sanctioned entities in the two months before they were sanctioned. Counterparties are those entities that did send funds to sanctioned entities prior to the sanctioning event (over a two-month window).
We assume that, within a given category of illicit activity (say, darknet markets), counterparties are roughly comparable to non-counterparties, and differ largely in their counterparty status.
This assumption lets us compare the inflows (which we can think of as akin to revenue for a criminal enterprise or actor) of counterparties relative to the performance of non-counterparties in the months following a sanctioning event, and reveal how counterparties may have performed had their service not been sanctioned. For example, if a counterparty of a sanctioned service received 10% more aggregate revenue inflows after a sanctioning event, that can look like the sanctions had a counterproductive effect. However, if entities of a similar type that were not counterparties to the sanctioned service grew by 50%, then we have reason to suspect that the 10% growth seen by counterparties was actually less than it would have been if sanctions had not been used.
The difference in post-sanctioning performance of counterparties and non-counterparties helps us estimate (directionally) and with modest precision the degree of under or over performance of sanctioned entity counterparties. To reach this final step, we take the difference between the average counterparty percent change in on-chain inflows by category and subtract the same measure for non-counterparties. We then use this percentage point value to weight the total amount of USD inflows to each category of sanctioned entity counterparty, ultimately providing a single best guess about the degree to which sanctioning interrelates with counterparty on chain activity.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

