This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
On May 7, 2021, Colonial Pipeline, an oil pipeline company that supplies energy to the southeastern United States, fell victim to a ransomware attack, forcing it to temporarily cease operations. Within hours of the attack, Colonial paid a ransom of 75 Bitcoin — worth roughly $4.4 million at the time — to DarkSide, the Russia-based cybercriminal group responsible for the attack. Six days later, Colonial was able to resume operations, but during that time, the shutdown combined with panic buying as the news spread resulted in fuel shortages in several areas.
One month later, there was good news: The Department of Justice announced that it had managed to seize $2.3 million worth of Bitcoin from Colonial’s ransom payment following an FBI investigation. Chainalysis is proud to say that our tools aided the FBI, and that we can now share details of how investigators tracked the funds following the attack.
Let’s start by looking at the ransom payment itself and the initial movement of funds using Chainalysis Reactor.
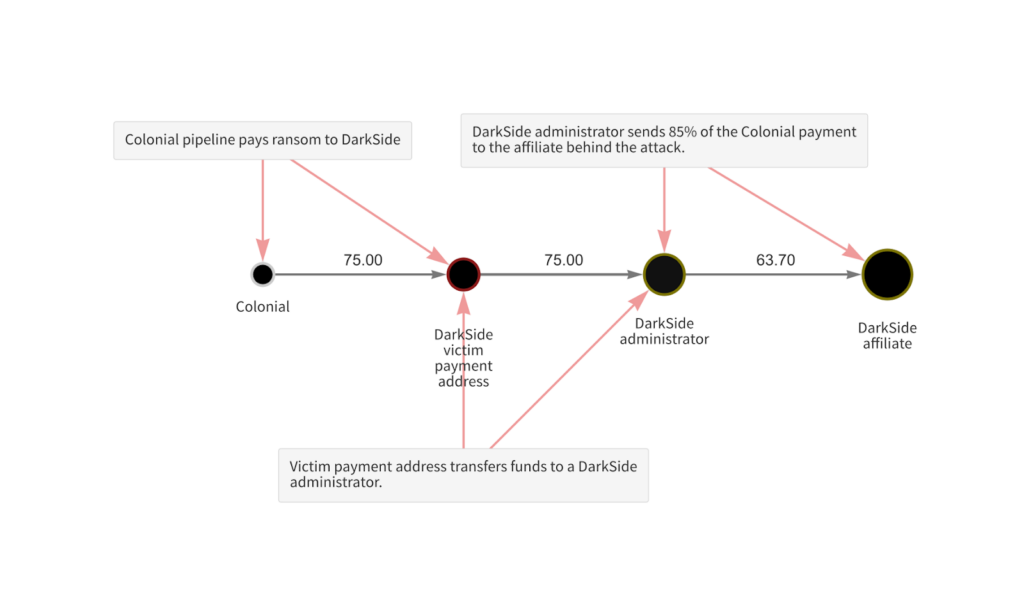
First, on the left, we see the initial payment of 75 Bitcoin from Colonial to the address provided by the attackers. Soon after, that address transferred the funds to an address controlled by DarkSide’s administrators, who then sent 63.7 Bitcoin — 85% of Colonial’s payment — to the affiliate who controlled the attack. That point is key — DarkSide operates on the Ransomware as a Service (RaaS) model, meaning the affiliates who carry out the attack effectively “rent” usage of DarkSide’s technology from the core group of administrators who created and manage the ransomware strain itself. Administrators take a small cut of the payment from each successful attack in return, as we see above.
Interestingly, the affiliate in question had previously received payments from addresses associated with NetWalker, another ransomware strain operating on the RaaS model that was disrupted by law enforcement in January 2021.
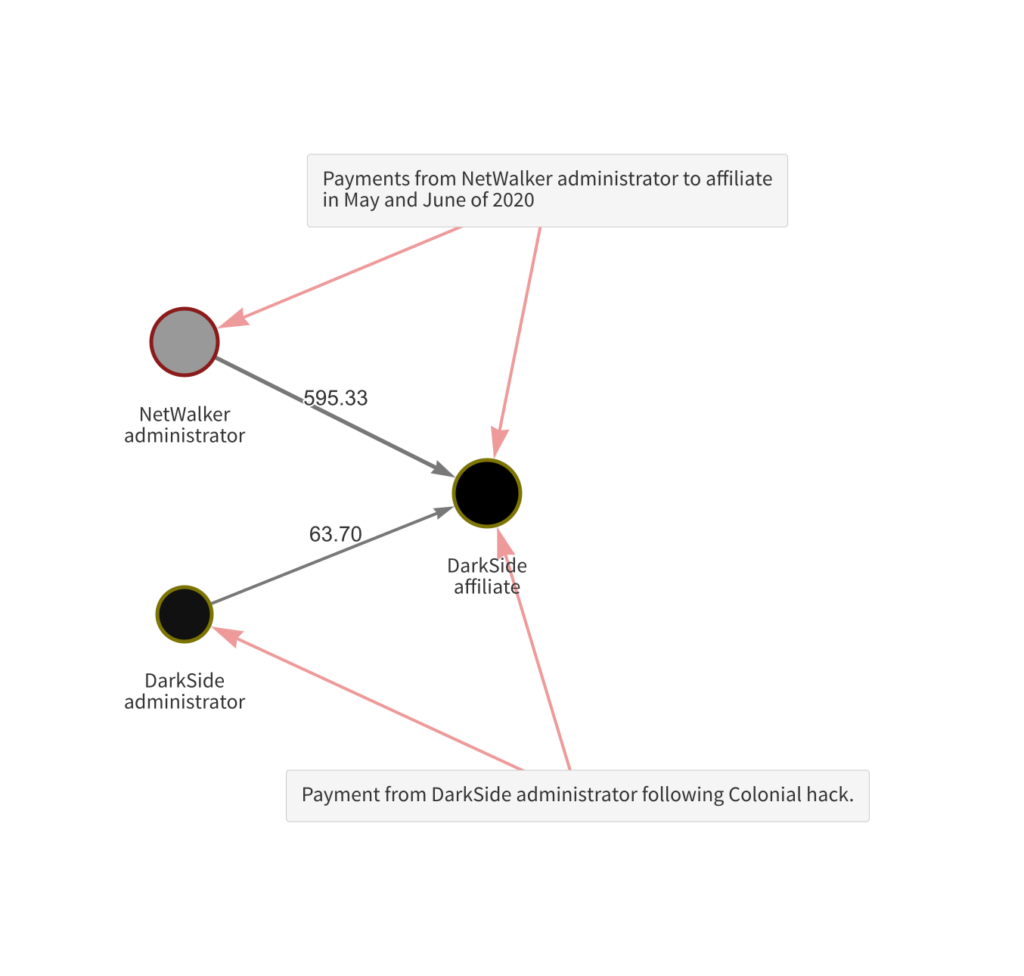
The affiliate received a total of 595.3 Bitcoin from the NetWalker administrator in a series of four payments in late May and early June of 2020, suggesting that they may have also carried out attacks for that strain as well. This wouldn’t be surprising, as we’ve noted other instances of affiliate overlap between ransomware strains in the past.
After tracking the funds to the affiliate’s address, FBI investigators were able to seize the funds on May 28, 2021.
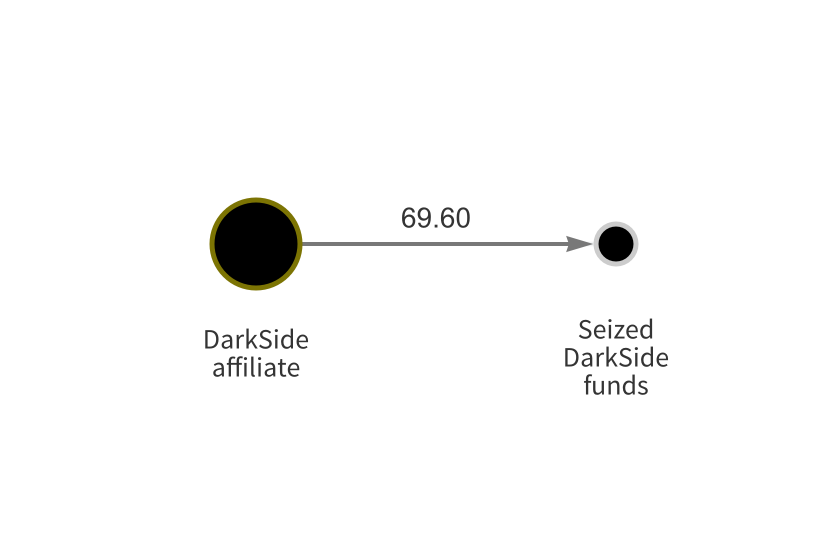
The seizure represents a huge step forward in the fight against ransomware, and especially ransomware strains that attack our critical infrastructure. We continue to monitor the movement of funds using our tools so that we can provide helpful insight to authorities as they investigate further and, hopefully, seize the remainder of the funds.
This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making investment decisions.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
