New updates, 8/8/23: Exploiter returns portion of funds, Curve Finance posts bounty to identify them
Less than a week after several liquidity pools on Curve Finance were exploited in a multi-million dollar scheme, the hacker returned 4,820 alETH and 2,258 ETH to Alchemix, worth around $12.7 million. These transactions were accompanied by an encrypted message, in which the hacker wrote, “I saw some ridiculous views, so i want to clarify that I’m refunding you not because you can find me, it’s because I don’t want to ruin your project, maybe it’s a lot of money for a lot of people, but not for me, I’m smarter than all of you. . .” NFT lending protocol JPEG’d also confirmed receipt of the majority of its stolen funds, worth around $10 million.
On August 6, 2023, Curve Finance announced on Twitter that the established deadline for the hacker to voluntarily return the remainder of the funds had passed. Thus, the company extended its bounty offer of $1.85 million to anyone able to uncover the hacker’s identity.
Original post: Analysis of Curve Finance liquidity pool hack
On July 30, 2023, several liquidity pools on Curve Finance were exploited, resulting in approximately $70 million in losses and triggering panic within the DeFi ecosystem. These hacks occurred due to a vulnerability in Vyper, a third-party Pythonic programming language for Ethereum smart contracts used by Curve and other decentralized protocols. Since then, several white hat hackers and MEV bot operators have helped recover some of the funds, which means the actual value lost may end up being lower than the total currently reported. Below, we’ll share what we know so far about the hack.
How did the exploit occur?
Vyper’s similarity to Python has made it an attractive entry point for developers into the DeFi ecosystem. According to Vyper, its 0.2.15, 0.2.16, and 0.3.0 versions contained issues making some smart contracts vulnerable to re-entrancy attacks, in which attackers can trick the contracts into incorrectly calculating balances, allowing them to steal funds held by the contracts’ protocols.
The massive hack began with an exploit of NFT lending protocol JPEG’d’s pETH-ETH pool for $12 million. However, that attacker appears to have been front-run by an MEV bot, which identified the attacker’s desired exploit and executed a similar transaction before the original occurred, in what may have been a white hat hacking effort.
Soon after, a series of separate attacks hit other pools, including Alchemix DAO’s alETH-ETH for $20 million ($17 million in ETH and $3 million in ERC-20s), Metronome DAO’s sETH-ETH for $1.6 million, and Curve’s CRV/ETH pool for $18 million. Curve’s CEO, Michael Egorov, then confirmed on Telegram that $22 million worth of CRV tokens was drained from Curve’s swap pool.
MEV bots have been heavily involved in front-running attempted hacks on Curve, resulting in the largest MEV block rewards in Ethereum’s history. In some cases, MEV bot operators have acted as white hats and returned funds taken from Curve in front-runs of malicious transactions, but the extent of this activity isn’t yet known. One MEV bot operator in particular, c0ffeebabe.eth, has been prolific in front-running exploits. This white hat hacker front-ran exploiters and returned funds in past incidents such as the April 2023 bug in the SushiSwap router contract. In the case of Curve, c0ffeebabe.eth successfully exploited around $5.3 million from its CRV/ETH pool and around $1.6 million from its Metronome msETH pool, and later returned the funds to both affected protocols.
We can see some of these movements on the Chainalysis Reactor graph below:
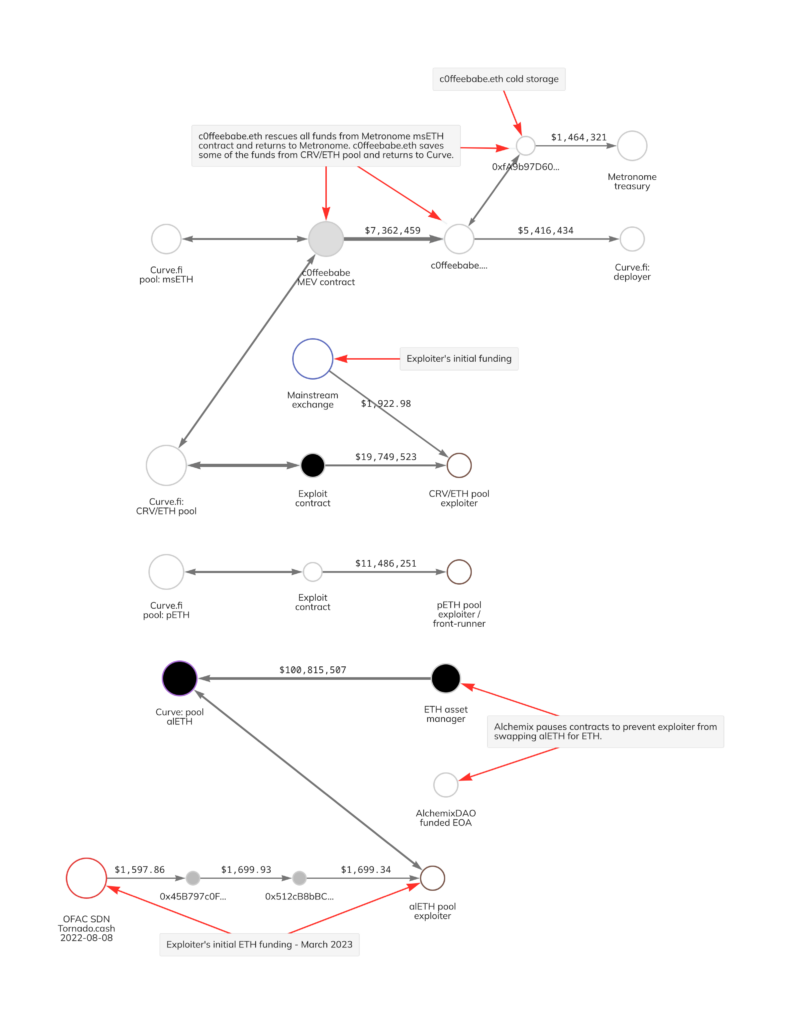
The aftermath of Curve’s exploit
After news broke of the hacks, CRV declined 5%. This decline, along with the risk that malicious hackers in possession of millions’ worth of CRV could sell into the token’s now-illiquid market, triggered fears of contagion effects for some DeFi protocols. In particular, the lending protocol AAVE appears to be at risk of incurring debt due to Egorov’s massive and well-known borrow position secured by CRV token collateral.
At this time, Curve has not detailed any recovery plans, but publicly advised its users to withdraw funds from Vyper-based pools. We have labeled all addresses relevant to the Curve hacks in Chainalysis products and will continue to provide updates on the situation when possible.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

