Malicious actors targeting crypto assets continue to employ diverse tactics to steal user funds, including private key theft, smart contract exploitation, price manipulation attacks, and more. In recent years, scammers have increasingly turned to crypto drainers. Drainers have unfortunately affected many crypto users large and small, including celebrities like Mark Cuban and Seth Green. Some of these crypto drainers have stolen several million dollars from victims, which we detail below.
Keep reading to learn more about:
- What are crypto drainers?
- The impact of crypto drainers
- Bitcoin’s first crypto drainer
- How to avoid crypto drainers
What are crypto drainers?
A crypto drainer is a phishing tool designed for the web3 ecosystem. Instead of stealing the usernames and passwords of victims, the operators of drainers often masquerade as web3 projects, enticing victims into connecting their crypto wallets to the drainer and approving transaction proposals that grant the operator control of the funds inside the wallet. If successful, drainers are able to directly steal users’ funds instantly. Operators of drainers often promote their fake web3 sites in Discord communities and on compromised social media accounts.
Below is an example of a drainer posing as the SEC, which we identified in January 2024 shortly after the SEC’s legitimate Twitter/X account was compromised. This crypto wallet drainer prompted users to connect their wallets to claim fake tokens through an airdrop.
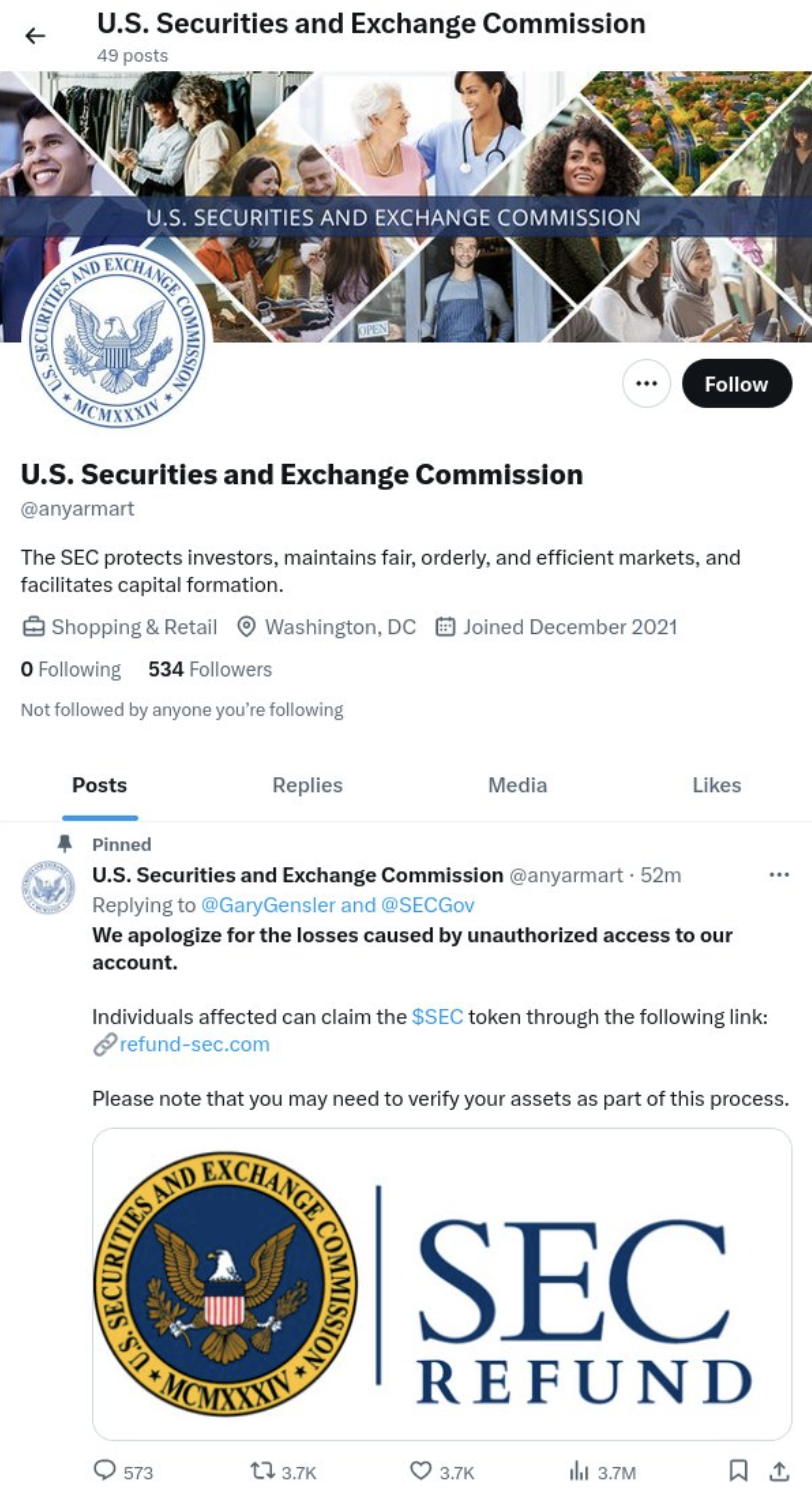
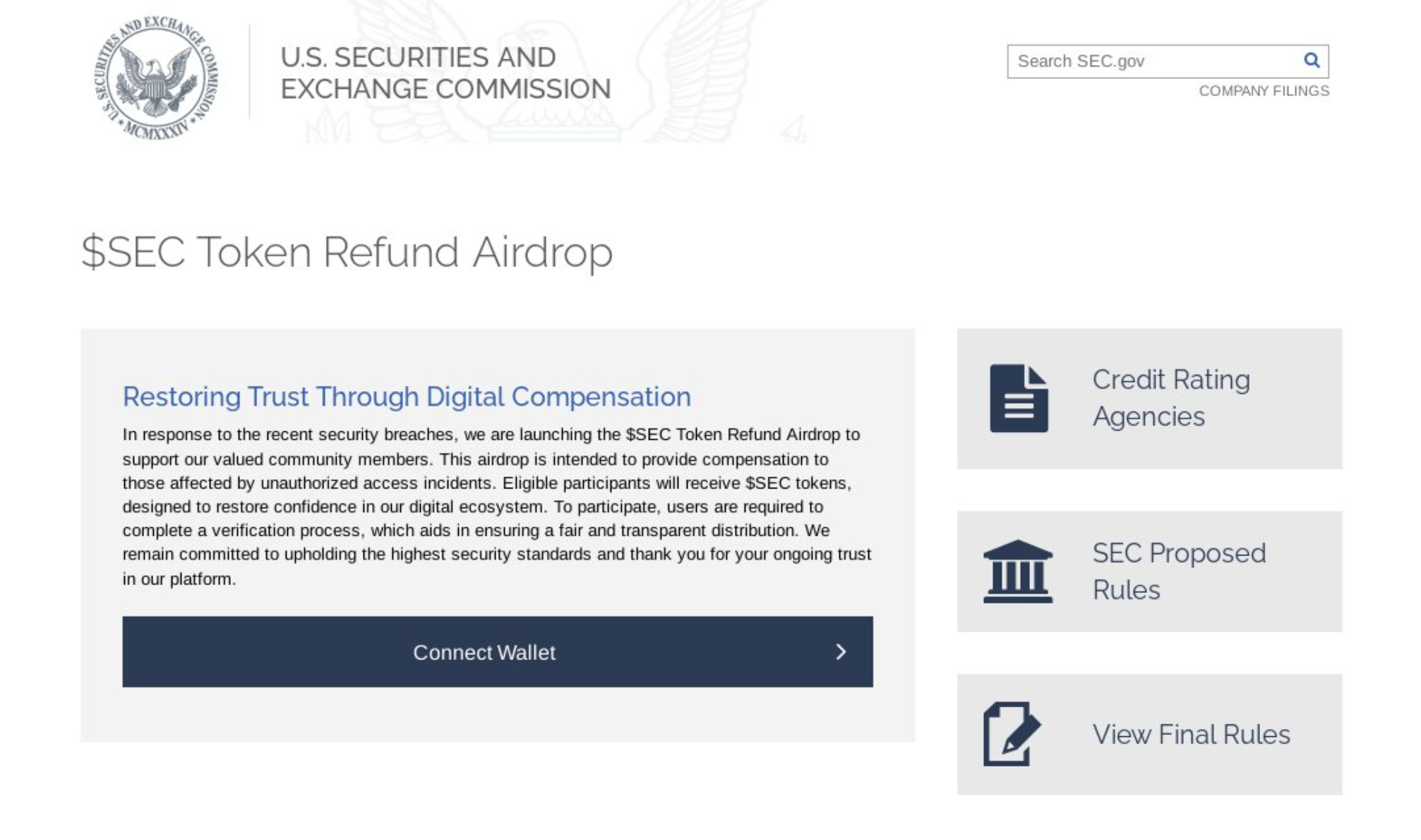
The impact of crypto drainers
It is difficult to track total amounts stolen by drainers, given that many crypto drainer scams are not reported. However, we are able to analyze the activities of the drainers that were initially reported by Chainalysis customers as phishing schemes and others with similar behaviors that we maintain in our database.
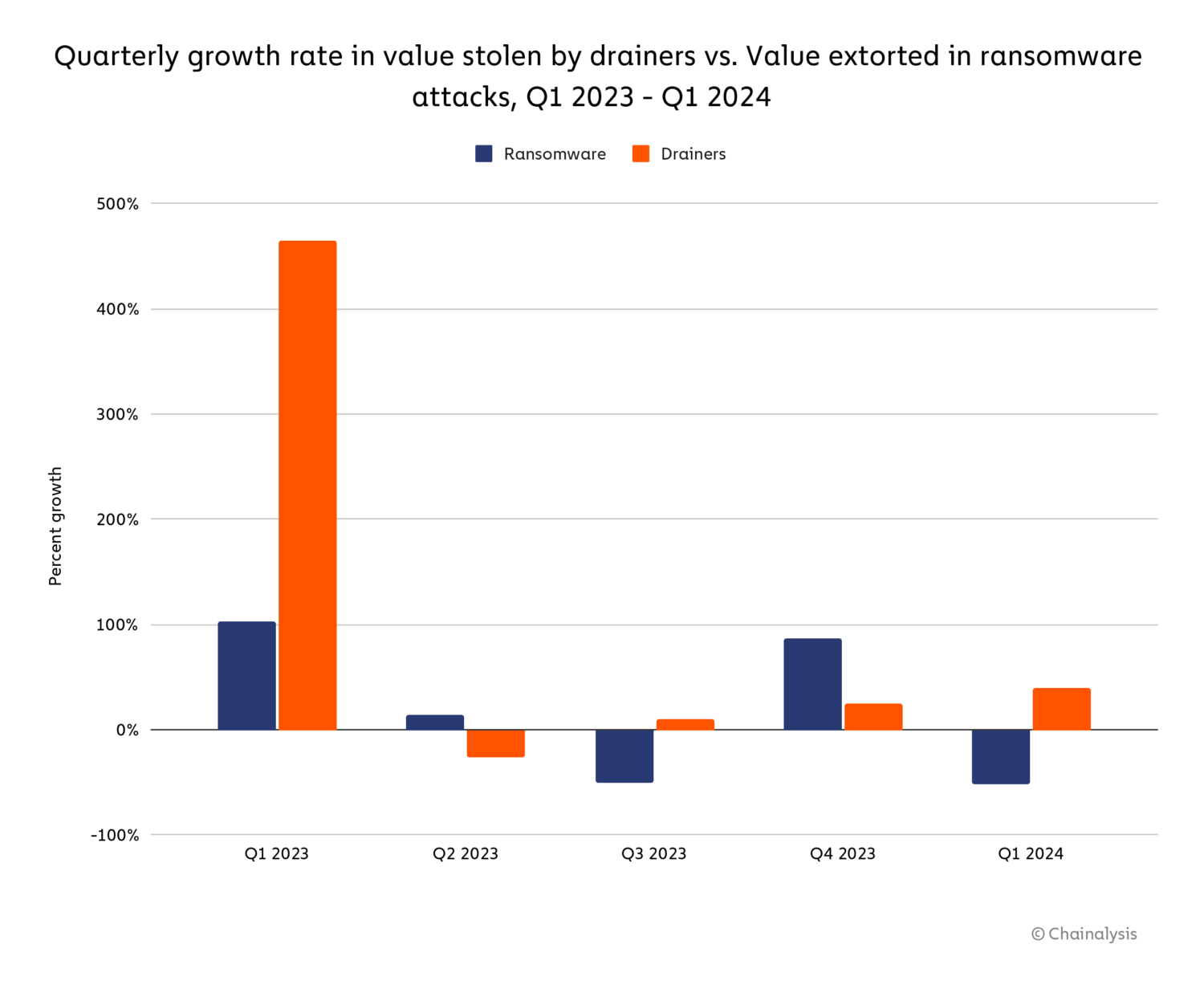
As we see below, the quarterly growth rate in value stolen by these drainers has even exceeded value stolen by ransomware, a category of crime which we’ve identified as particularly fast-growing in recent years.
After stealing digital assets from a victim’s wallet, cybercriminals operating drainers typically use various crypto services to launder the funds or potentially convert them into cash. In the next graph, we see that funds sent by drainers to mixing services to achieve these aims have risen since 2021, whereas funds sent to centralized exchanges have decreased. Certain drainers appear to also be using gambling services, though on a much smaller scale.

Additionally, in 2022 and 2023, drainers sent most of their stolen funds to various DeFi projects such as decentralized exchanges, bridges, and swap services — this is because all of the assets stolen by drainers are easy and practical to transfer within DeFi, unlike Bitcoin.
Bitcoin’s first crypto drainer
Currently, most drainers operate within the Ethereum ecosystem. However, we recently identified an unusual drainer on the Bitcoin blockchain. The operators of this drainer created a fake web page masquerading as Magic Eden, the main NFT platform for Bitcoin Ordinals. As of April 2024, this drainer has stolen approximately $500,000 in more than 1,000 malicious transactions.
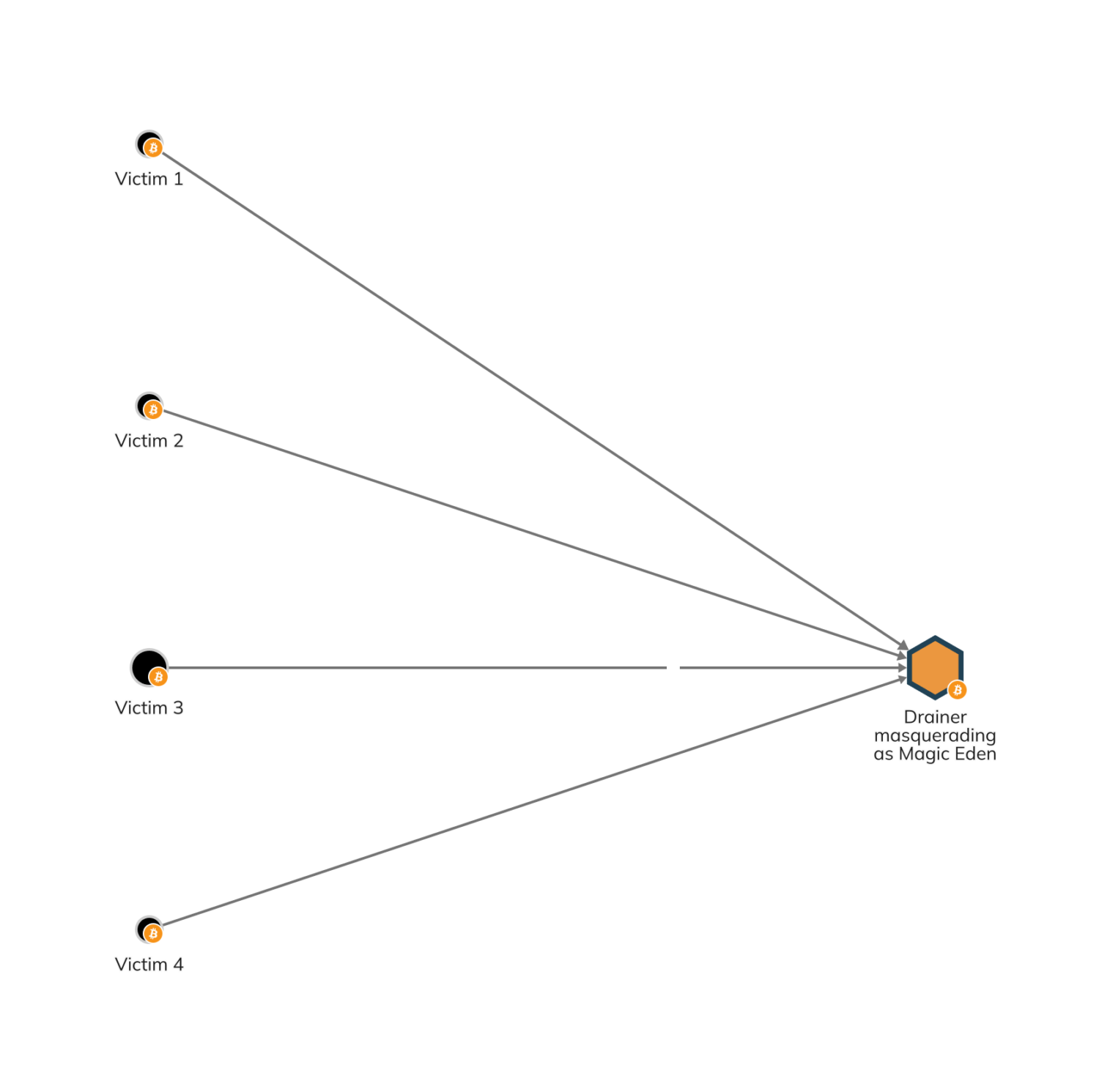
Although Bitcoin isn’t as widely used as other assets for web3 services, several other Bitcoin drainers have already exploited communities of Ordinals traders.
How to avoid crypto drainers
As criminals operating crypto drainers become more sophisticated, it will be increasingly important for web3 projects and users to implement various security measures to protect against this malicious activity:
- Web3 security extensions such as Wallet Guard can identify phishing pages and websites, and assess security risks associated with cryptocurrency wallets.
- Users can reduce exposure to drainers by using an offline wallet to store valuable or large volumes of assets, and only transferring funds to a hot wallet when needed.
- Ecosystem participants should be wary of links promoted in chat rooms or on social media, which may not be associated with a project’s official account.
- If a private wallet user needs to connect to an unfamiliar web3 site, the user can create a temporary wallet that doesn’t contain any assets and connect it to the site.
- If a victim’s assets are stolen by a drainer, the victim can cancel incomplete transactions.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

