The ransomware landscape experienced significant changes in 2024, with cryptocurrency continuing to play a central role in extortion. However, the total volume of ransom payments decreased year-over-year (YoY) by approximately 35%, driven by increased law enforcement actions, improved international collaboration, and a growing refusal by victims to pay.
In response, many attackers shifted tactics, with new ransomware strains emerging from rebranded, leaked, or purchased code, reflecting a more adaptive and agile threat environment. Ransomware operations have also become faster, with negotiations often beginning within hours of data exfiltration. Attackers range from nation-state actors to ransomware-as-a-service (RaaS) operations, lone operators, and data theft extortion groups, such as those who extorted and stole data from Snowflake, a cloud service provider.
In this chapter, we’ll explore these developments and their implications, including a variety of case studies — LockBit, Iranian ransomware strains, Akira/Fog, and INC/Lynx — that exemplify this year’s trends.
Ransomware activity shifts halfway through the year
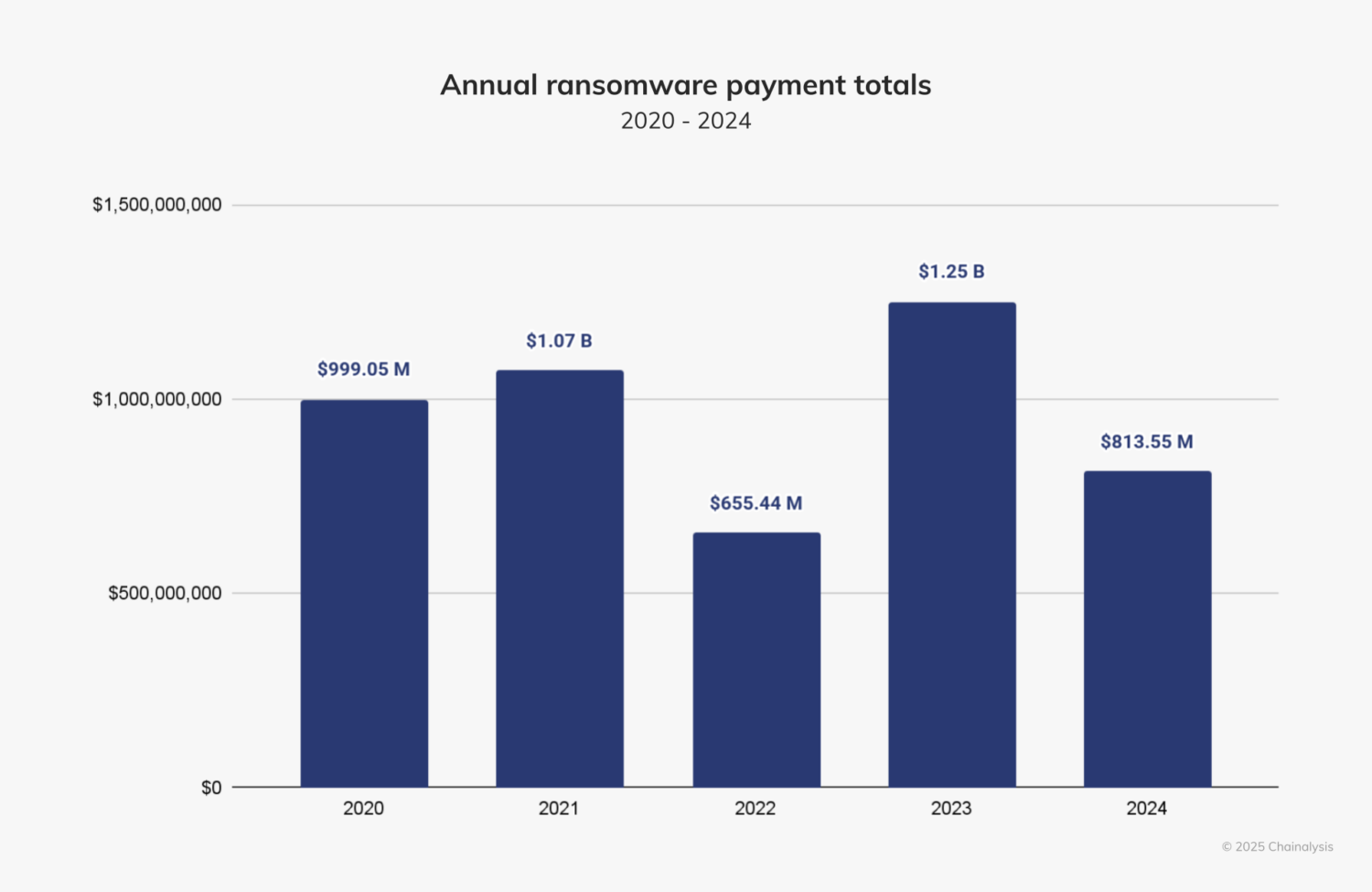
In 2024, ransomware attackers received approximately $813.55 million in payments from victims, a 35% decrease from 2023’s record-setting year of $1.25 billion, and for the first time since 2022, ransomware revenues declined.
As we noted in our mid-year crime update, value extorted by ransomware attackers between January and June 2024 had reached $459.8 million, approximately 2.38% higher than the value extorted over the same time period in 2023. H1 2024 also saw a few exceptionally large payments, such as the record-breaking $75 million payment to Dark Angels.
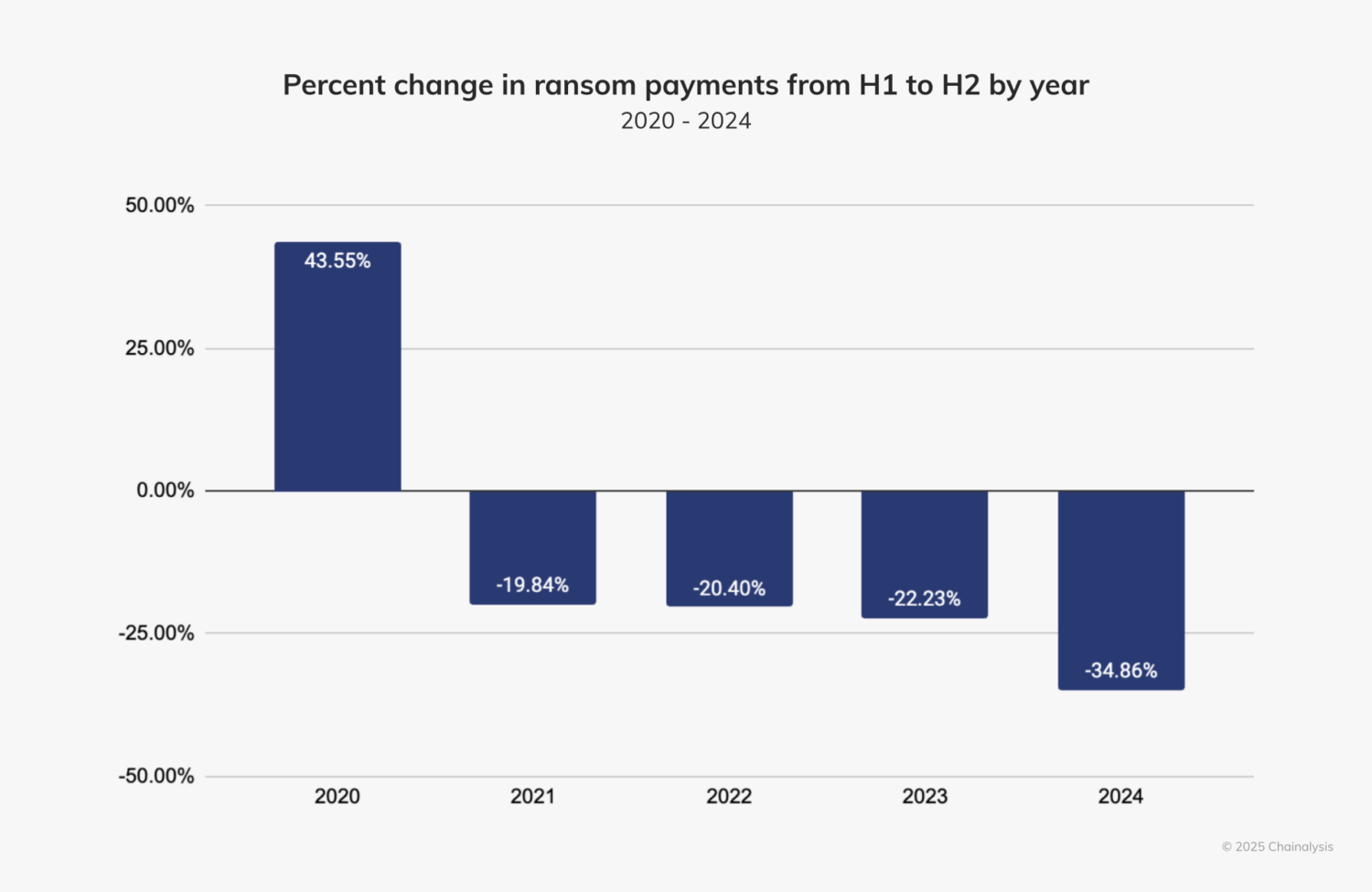
Despite its small half-over-half (HoH) increase, we expected 2024 to surpass 2023’s totals by the end of the year. Fortunately, however, payment activity slowed after July 2024 by approximately 34.9%. This slowdown is similar to the HoH decline in ransom payments since 2021 and the overall decline during H2 2024 in some types of crypto-related crime, such as stolen funds. Notably, the decline this year is more pronounced than in the last three years.
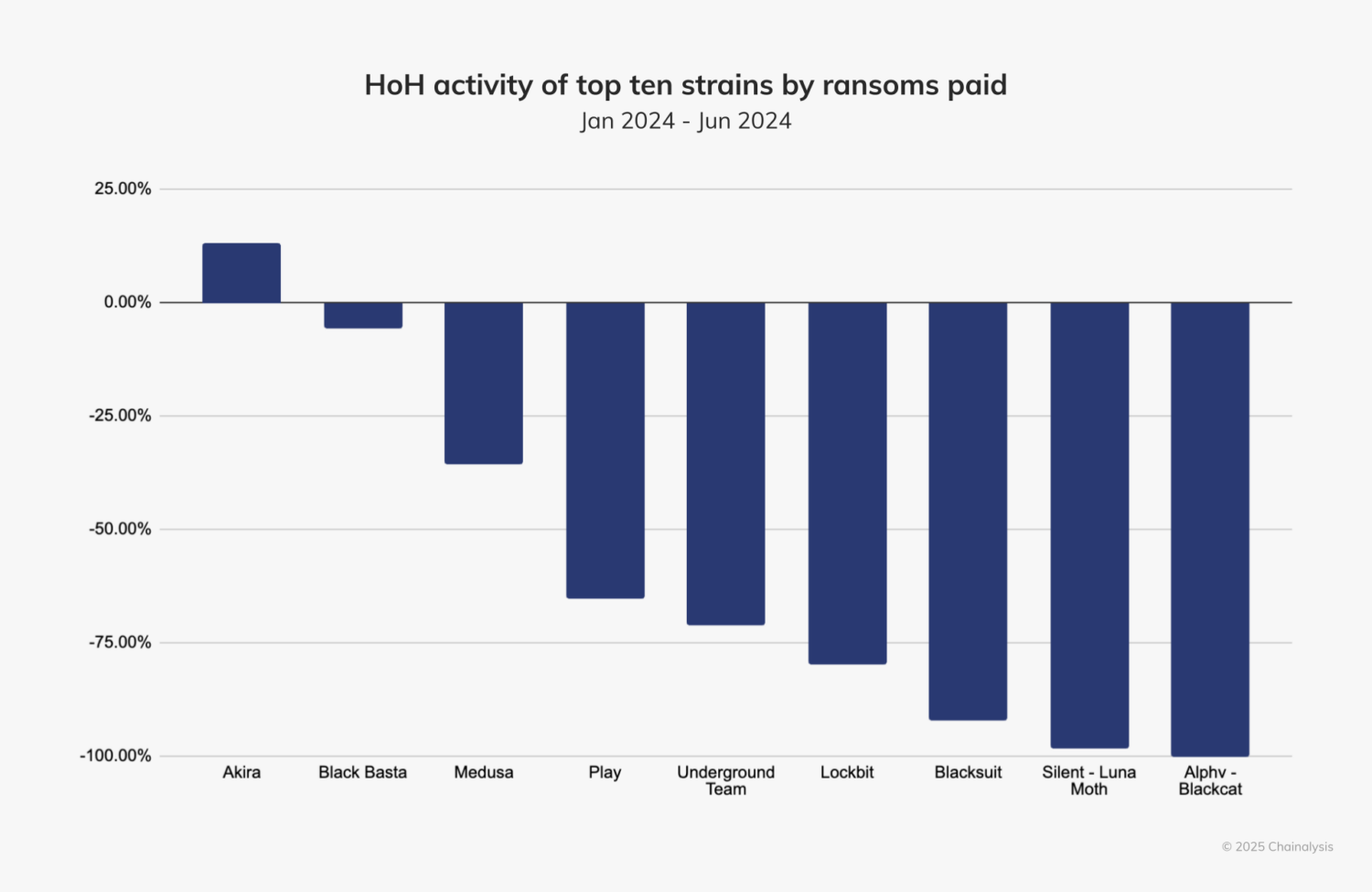
A closer examination of the top 10 ransomware strains in terms of H1 revenue provides valuable insights into the groups driving these HoH trends. As we see in the below chart, Akira, which has targeted more than 250 entities since March 2023, is the only H1 top 10 ransomware strain to have ramped up its efforts in H2 2024. LockBit, which was disrupted by the United Kingdom’s National Crime Agency (NCA) and the U.S. Federal Bureau of Investigation (FBI) in early 2024, saw H2 payments decrease by approximately 79%, showcasing the effectiveness of international law enforcement collaboration. ALPHV/BlackCat, which had been among 2023’s top grossing strains, exit scammed in January 2024, leaving a void in H2.
As Lizzie Cookson, Senior Director of Incident Response at Coveware, a ransomware incident response firm, told us, “The market never returned to the previous status quo following the collapse of LockBit and BlackCat/ALPHV. We saw a rise in lone actors, but we did not see any group(s) swiftly absorb their market share, as we had seen happen after prior high profile takedowns and closures. The current ransomware ecosystem is infused with a lot of newcomers who tend to focus efforts on the small- to mid-size markets, which in turn are associated with more modest ransom demands.”
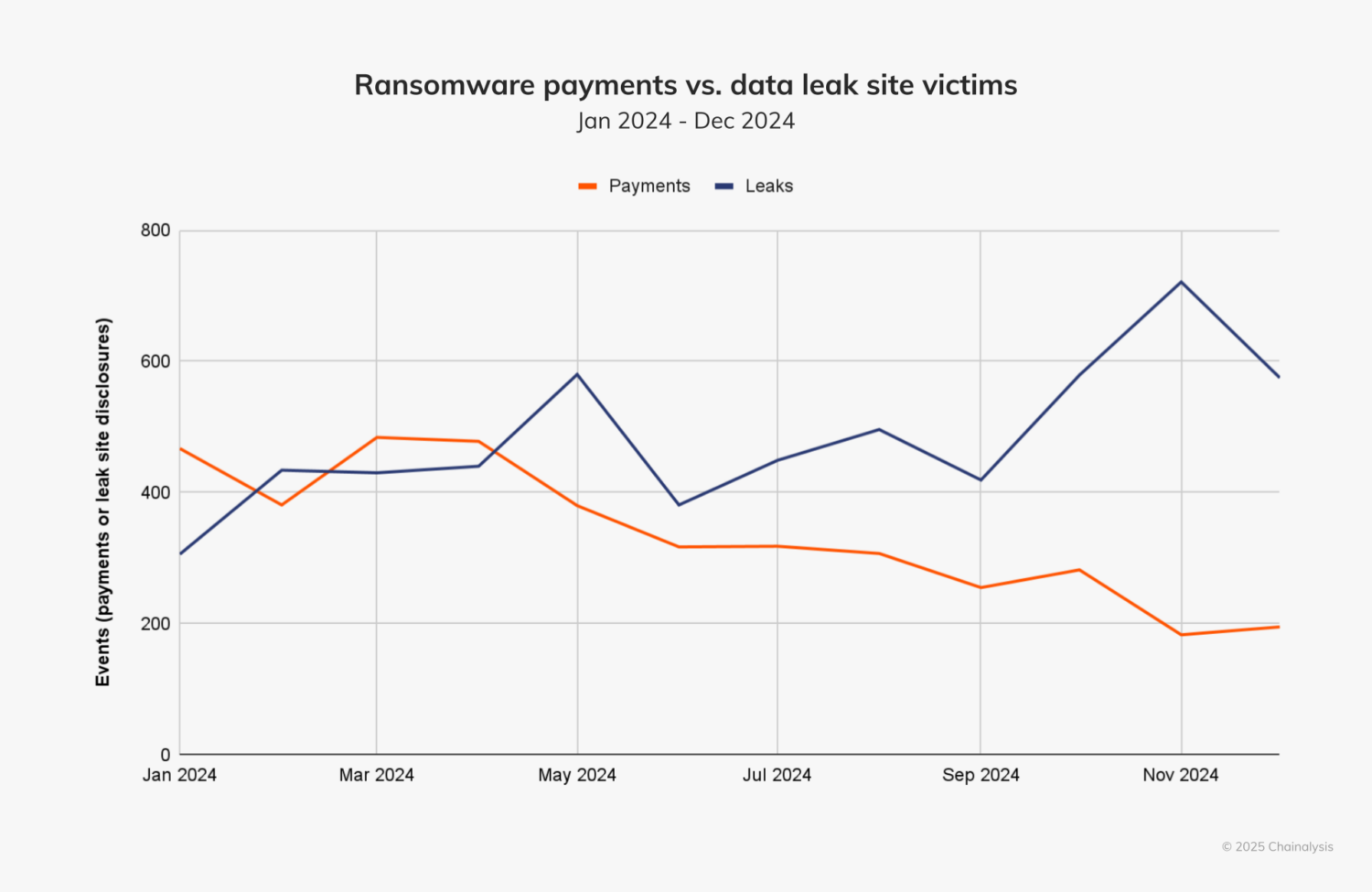
To further contextualize what may have driven H2’s decrease in ransomware payment activity, we first looked at data leak sites, which could be a proxy for ransomware events. In the below chart, we can see that the number of ransomware events increased into H2, but on-chain payments declined, suggesting that more victims were targeted, but fewer paid.
Source: ecrime.ch
Data leak sites posted more victims in 2024 than in any year prior. Not only were there more alleged victims, but, according to Allan Liska, Threat Intelligence Analyst at Recorded Future, there were 56 new data leak sites in 2024 — more than double the number Recorded Future identified in 2023. However, there are some caveats to consider with data leak site information and what it suggests about the ransomware ecosystem.
Corsin Camichel, Threat Researcher at eCrime, shared more information on the legitimacy of leaks. “We have observed leak site posts claiming organizations, only to fail on a deeper analysis. For example, we have seen claims for multinational organizations, but in reality, only a smaller subsidiary was impacted. More than 100 organizations got listed on two or more data leak sites in 2024. The ‘MEOW’ leak site plays a big role in this, seeming to compromise websites and list data taken from web servers or databases.” Another reason for the inverse relationship between ransomware payments and data leak site victims shown above could be that threat actors have been caught overstating or lying about victims or reposting claims by old victims. “The LockBit operators played games to pretend to stay relevant and active after a law enforcement action called ‘Operation Cronos,’ as they re-posted many previously listed claims again or added attacks that happened a long time ago, some even over one year ago,” Camichel added.
Liska also shared with us information about illegitimate victims posted to data leak sites, stating, “This is especially true of LockBit, which, in a bid to remain relevant after being ostracized by much of the underground community post law enforcement action, has published as high as 68% repeat or straight up fabricated victims on its data leak site.”
In the aftermath of the LockBit disruption and BlackCat’s exit scam, another interesting phenomenon has been the rise of RansomHub RaaS, which absorbed a lot of the displaced operators from LockBit and BlackCat. RansomHub posted the highest number of victims in 2024, according to Camichel, and despite only emerging in February 2024, ranked in the top 10 strains for 2024, according to on-chain data.
Incident response data show that the gap between the amounts demanded and paid continues to increase; in H2 2024, there was a 53% difference between the two factors. Reporting from incident response firms suggests a majority of clients opt not to pay altogether, which means the actual gap is larger than the below numbers suggest.
We spoke to Dan Saunders, Director, Incident Response, EMEA at Kivu Consulting, a cybersecurity incident response firm, to learn more about this victim resilience. “According to our data, around 30% of negotiations actually lead to payments or the victims deciding to pay the ransoms. Generally, these decisions are made based on the perceived value of data that’s specifically been compromised,” he stated. Similarly, Cookson noted that, thanks to improved cyber hygiene and overall resiliency, victims are increasingly able to resist demands and explore multiple options to recover from an attack. “They may ultimately determine that a decryption tool is their best option and negotiate to reduce the final payment, but more often, they find that restoring from recent backups is the faster and more cost-effective path,” she added. Final payment amounts typically ranged from $150,000 to $250,000, regardless of initial demands.
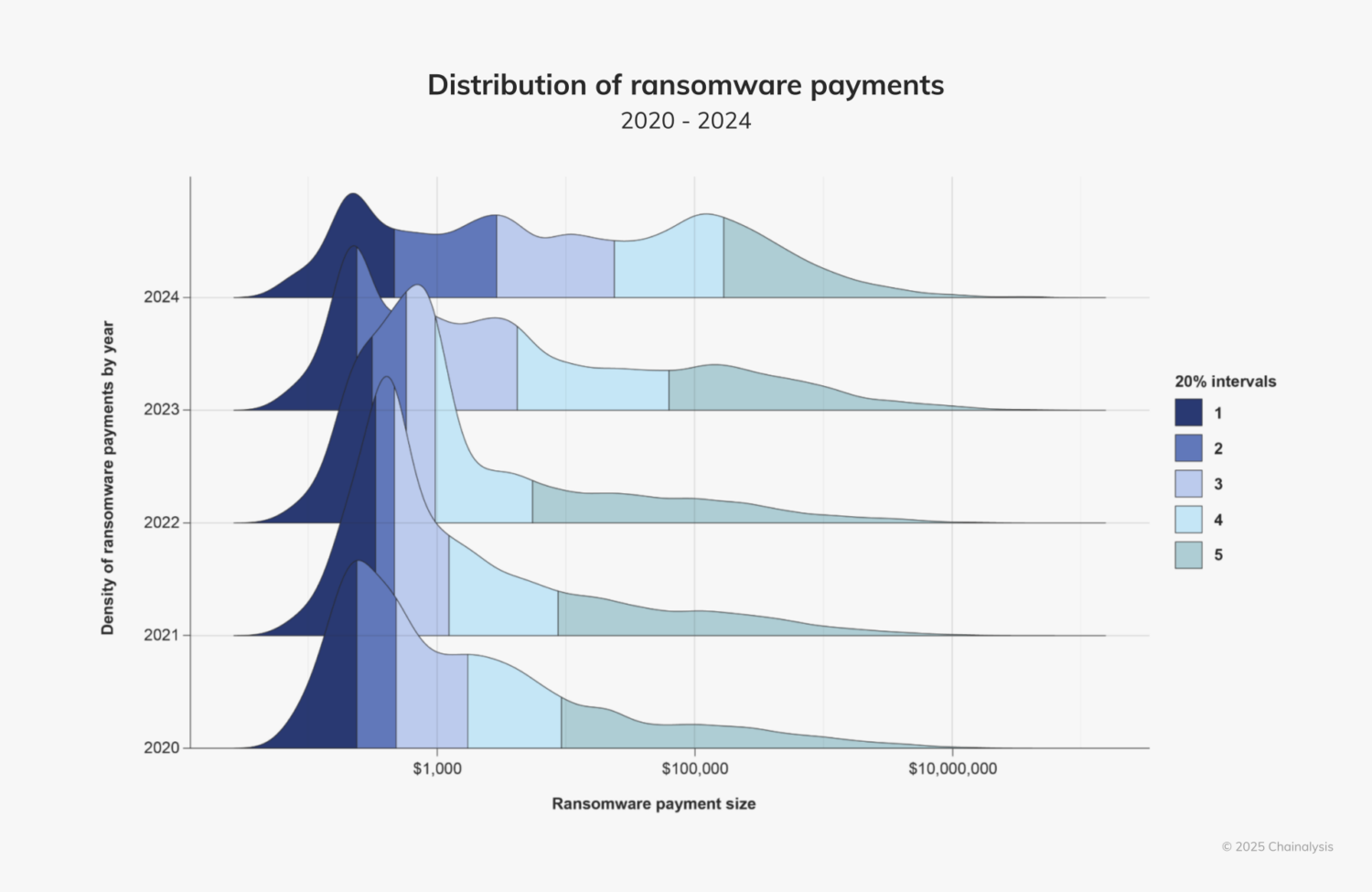
When looking at the figure below, we can see the evolution of ransomware payment distributions into 2024. In 2020, there was a long tail but a single hump to ransomware payments, but in 2024, there were three classes of ransomware actors. Some, such as Phobos, have average payments clustering at less than $500 – $1,000. There is another cluster around $10,000 and a third with payments north of $100,000, some of which reached $1 million. We also see more events at the higher end of the distribution, meaning proportionately greater attacks in excess of $1 million.
This segmentation reflects the shift in the ransomware actor landscape that Cookson observed, with smaller groups dominating low- and mid-value payments, while the outlier 7-8 figure ransoms push the distribution rightward toward the third class of payments.
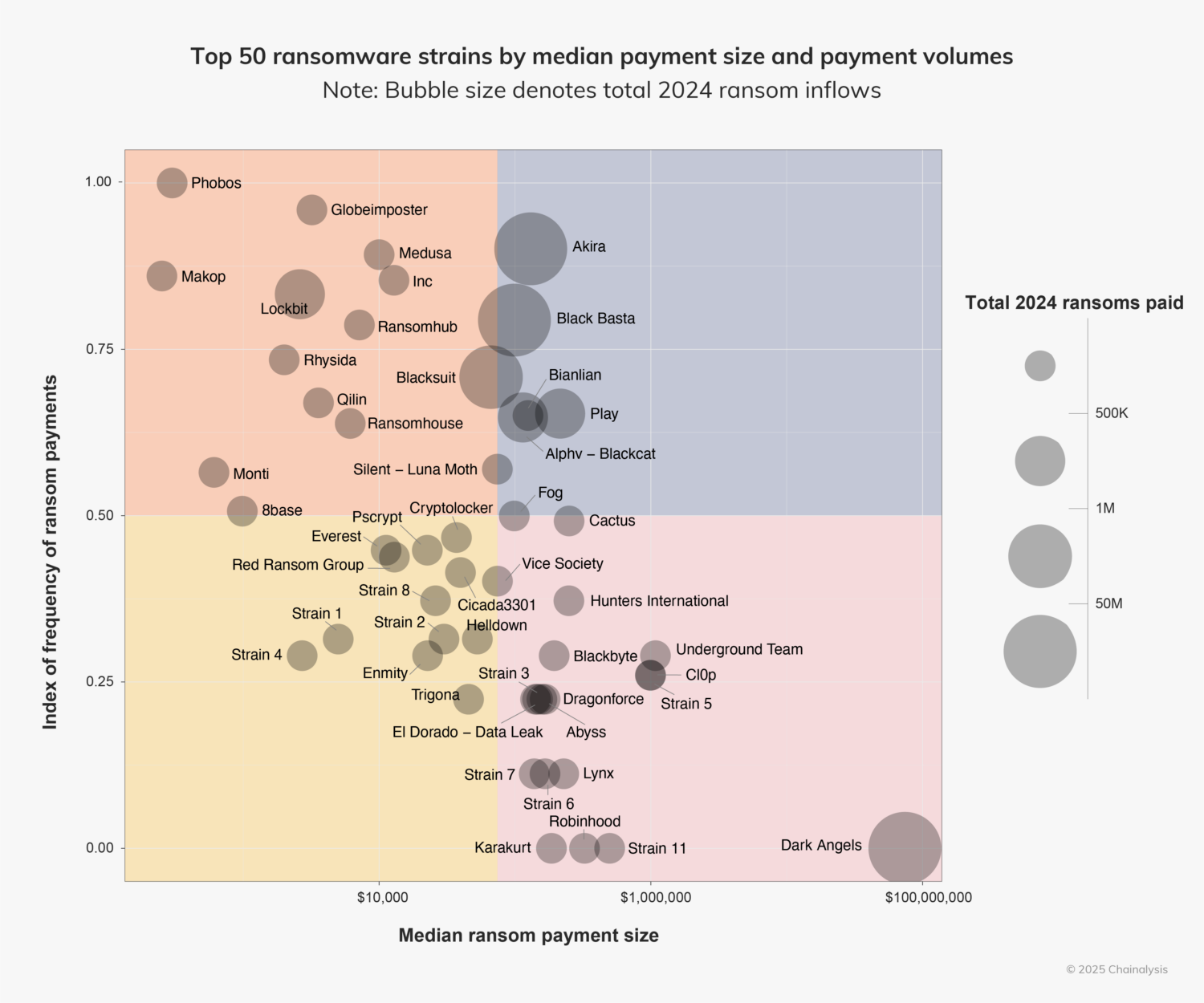
In the below chart, we can see which strains were the worst in terms of total value extorted (bubble size), median payment size (X axis), and an index of extortion events (Y axis).
Ransomware off-ramping: Where do the funds go?
Understanding ransomware laundering methods offers critical insights into post-exploit threat actor behavior, enabling law enforcement to respond more efficiently and, in some cases, anticipate future actions based on established patterns.
In the below chart, we see that ransom funds primarily flowed through centralized exchanges (CEXs) (used to off-ramp funds), personal wallets (to hold funds), and bridges (to attempt to obscure the movement of funds). We note a substantial decline in the use of mixers in 2024. Historically, mixing services routinely captured between 10% and 15% of ransomware quarterly money laundering flows. The decline of mixing among ransomware actors over the years is very interesting and a testament to the disruptive impact of sanctions and law enforcement actions, such as those against Chipmixer, Tornado Cash, and Sinbad. In place of mixers, we have noted ransomware actors increasingly rely on cross-chain bridges to facilitate their off-ramping. In contrast, CEXs continue to be a mainstay of the ransomware offramping playbook, with 2024 seeing a slightly above-average reliance on these types of services (39% versus 37% for the period between 2020 and 2024).
It’s worth calling out the substantial volumes of funds being held in personal wallets. Curiously, ransomware operators, a primarily financially motivated group, are abstaining from cashing out more than ever. We attribute this largely to increased caution and uncertainty amid what is probably perceived as law enforcement’s unpredictable and decisive actions targeting individuals and services participating in or facilitating ransomware laundering, resulting in insecurity among threat actors about where they can safely put their funds.
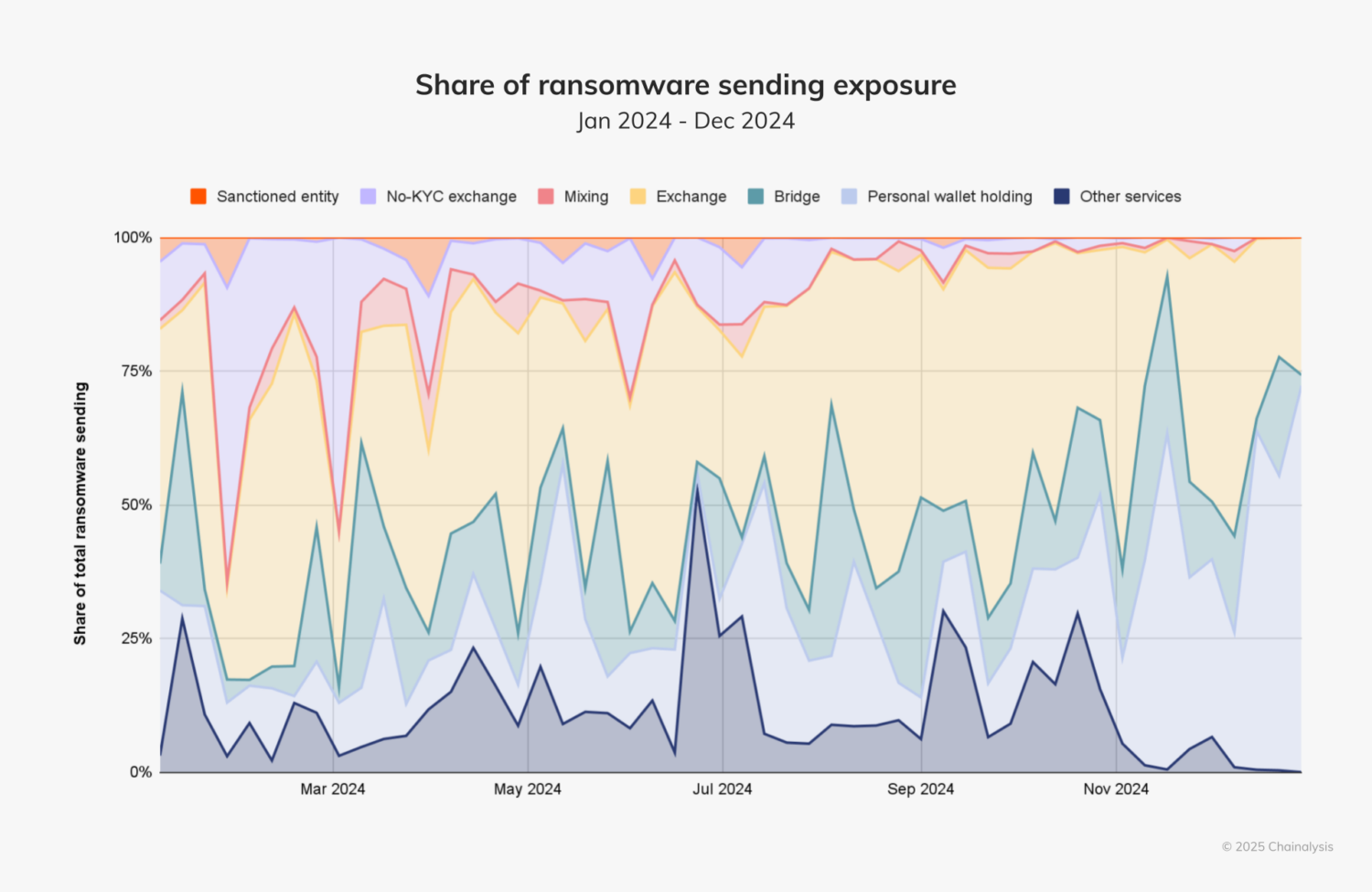
While numerous factors are likely behind any one of the trends visible in the chart above, the decline in the use of no-KYC exchanges since October 2024 may be attributed to the designation of Russia-based exchange Cryptex and the German Federal Criminal Police (BKA)’s seizure of 47 Russian language no-KYC crypto exchanges — both in September 2024. The timing of those enforcement actions, coupled with the period when ransomware inflows to no-KYC exchanges dwindled, is conspicuous.
Ransomware case studies
Panev’s arrest and its impact on LockBit’s operations
Between 2019 and 2024, Israeli-Russian dual citizen Rostislav Panev allegedly played a crucial role in supporting LockBit. He is accused of developing several tools for the group, including one that enabled attackers to print ransom notes from any printer connected to compromised systems, for which he was reportedly paid around $230,000 in bitcoin (BTC). While Russian nationals, including LockBit’s administrator Dimitry Yuryevich Khoroshev, have previously faced sanctions for their roles in these attacks, it is important to recognize that ransomware is truly a global threat, involving actors from around the world. Panev is currently in Israel awaiting extradition to the United States, where he is wanted for conspiracy to commit fraud, cybercrime, wire fraud, and other offenses.
In the Reactor graph we can see, per the indictment, the transfer of roughly $5,000 in BTC from Khoroshev on a biweekly basis beginning in 2022. Then, from July 2023 through early 2024, approximately $10,000 in BTC was transferred to Khoroshev on a monthly basis.
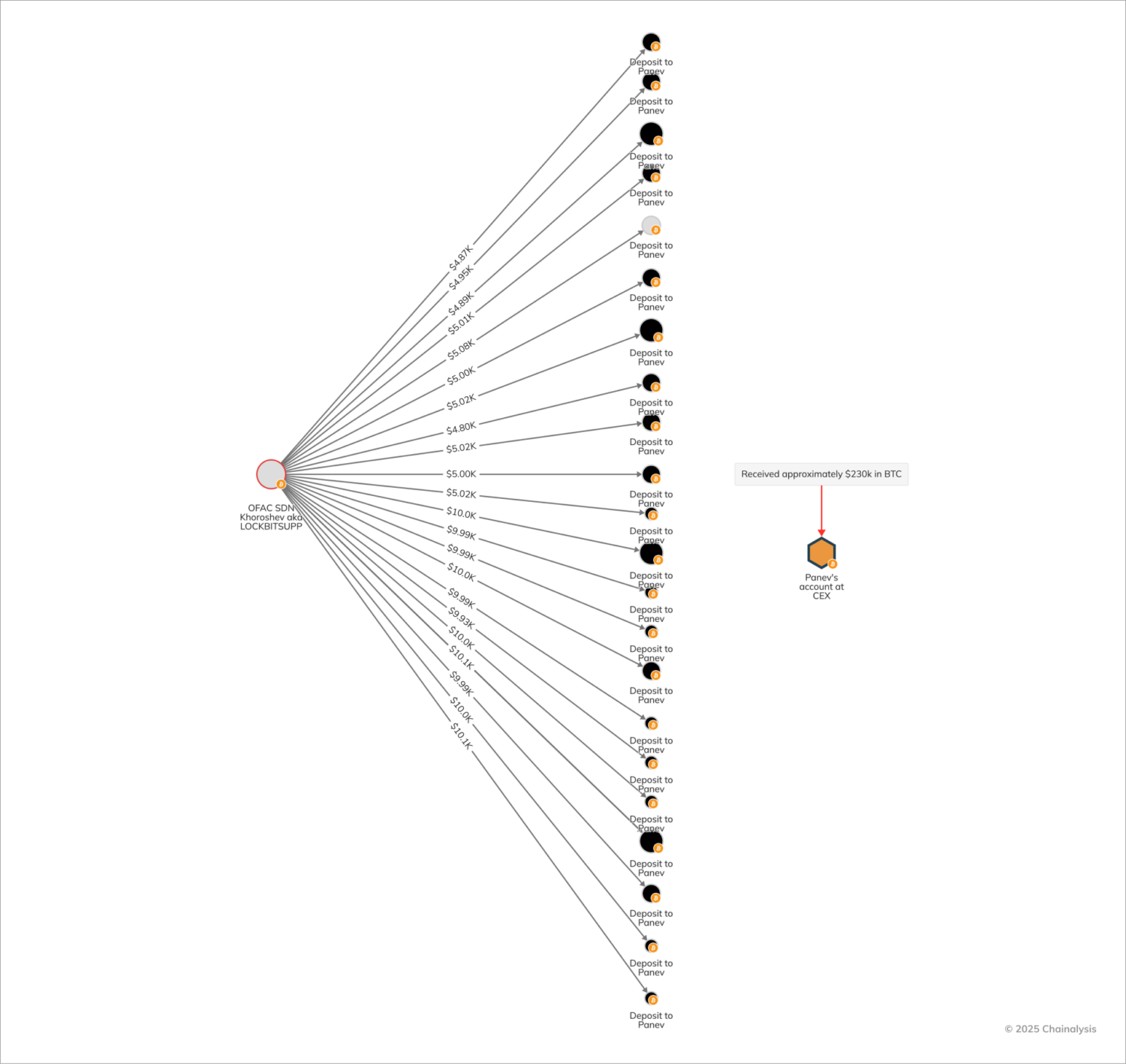
Panev’s arrest potentially marked a significant blow to LockBit’s ability to reconstitute, and highlighted that, even years after a crime has been committed, blockchain’s transparent and immutable nature continues to empower law enforcement to trace illicit activities and disrupt transnational cybercrime syndicates. The LockBit takedown and Panev’s arrest were major victories in 2024 and sparked a shift toward a more fragmented and less coordinated ecosystem.
Iranian ransomware involvement
In addition to Russian-speaking cybercriminals, within the past several years, Iranian nationals have also been sanctioned by the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) for their involvement in facilitating and conducting ransomware attacks. We’ve also previously noted on-chain evidence of LockBit affiliates working with Iranian ransomware strains and depositing funds at an Iranian exchange.
Fortunately, through our on-chain analysis, we can identify Iranian actors as they rebrand or switch to a different RaaS. As we see in the below Chainalysis Reactor graph, we tied four different ransomware strains to the same Iranian threat actor, who likely also deployed a popular RaaS strain. We also see the reuse of deposit addresses at multiple global exchanges, connecting these seemingly disparate strains — not only to each other, but also confirming the operator’s Iran ties.
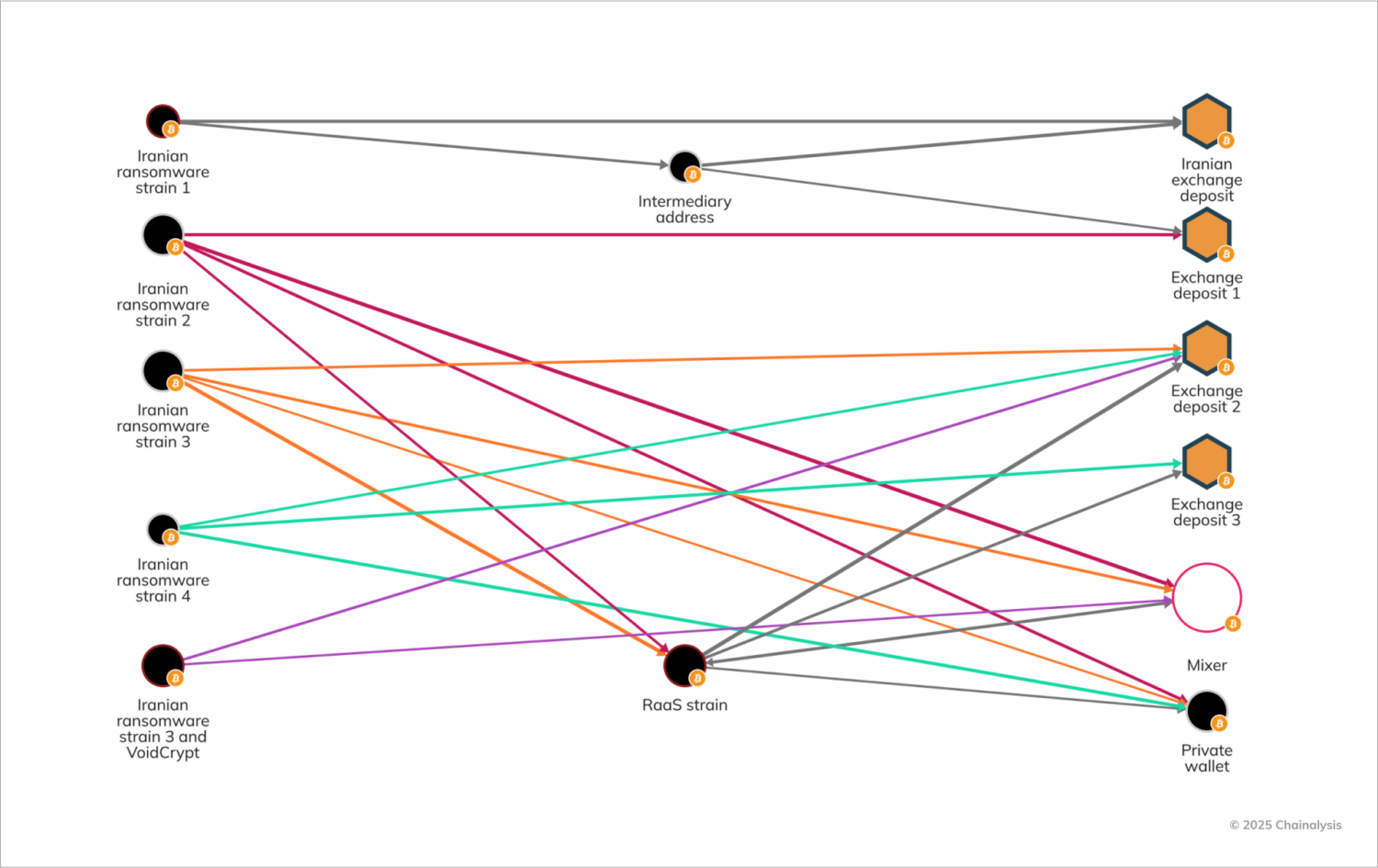
Major strains rebranding, launching offshoots
Since Akira’s emergence, it has proven successful in exploiting vulnerabilities — particularly in enterprise environments — and has gained traction with a number of high-profile attacks. As we mentioned above, Akira is the only top 10 ransomware strain to have ramped up its efforts in H2 2024.
In September 2024, Fog, a new ransomware strain, entered the scene, and has since demonstrated an ability to target critical vulnerabilities, much like Akira. Both groups have primarily focused on exploiting VPN vulnerabilities, which allows them to gain unauthorized access to networks and consequently deploy their ransomware.
Both Akira and Fog have used identical money laundering methods, which are distinct from other ransomware strains, further supporting a connection between them. For instance, the following Chainalysis Reactor graph shows that several wallets operated by Akira and Fog have transferred funds to the same no-KYC exchange.
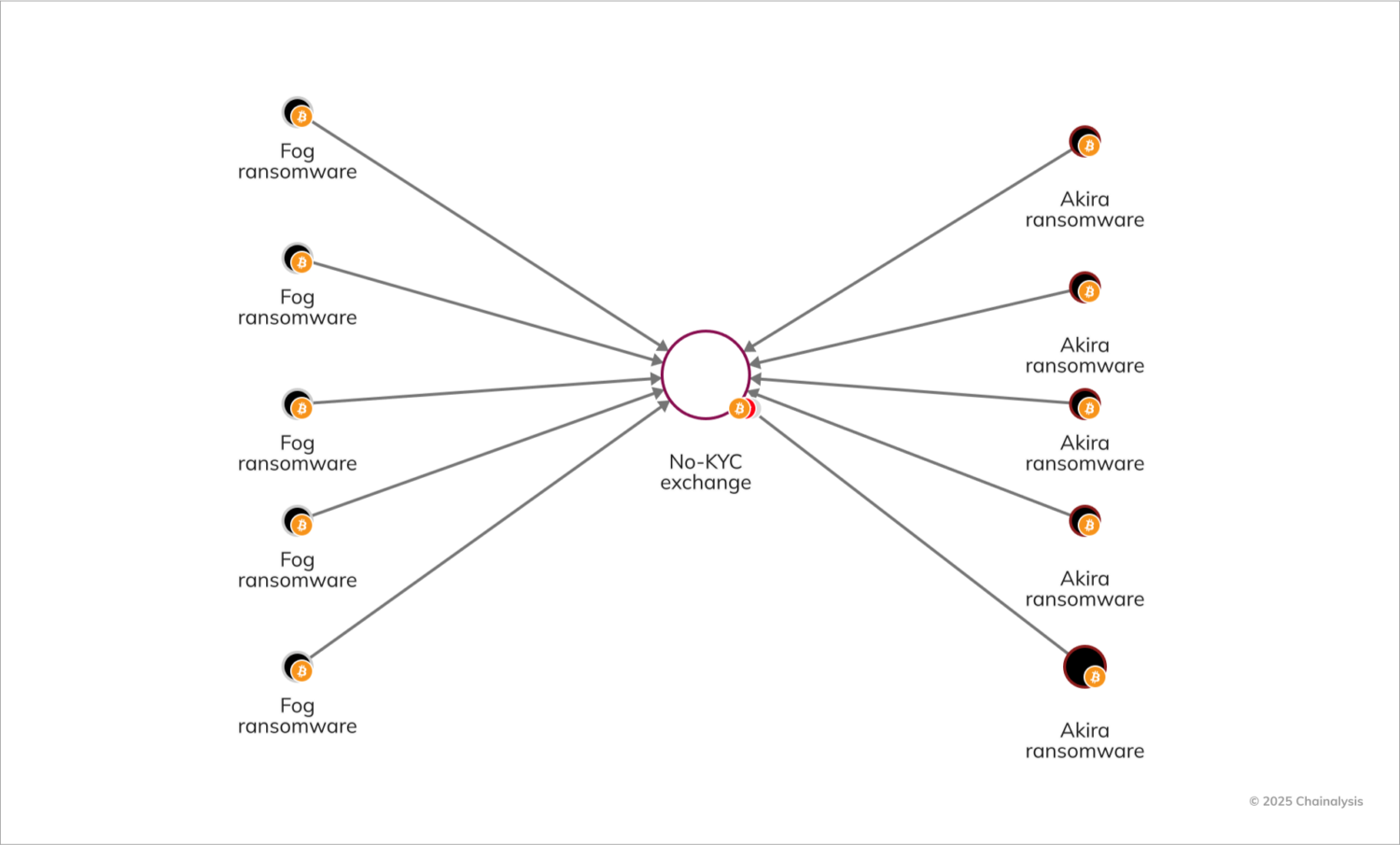
In addition to Akira’s relationship to Fog, we have also discerned links between the INC and Lynx ransomware variants by examining similar on-chain behaviors. Cybersecurity researchers have also noted the two strains’ shared source code.
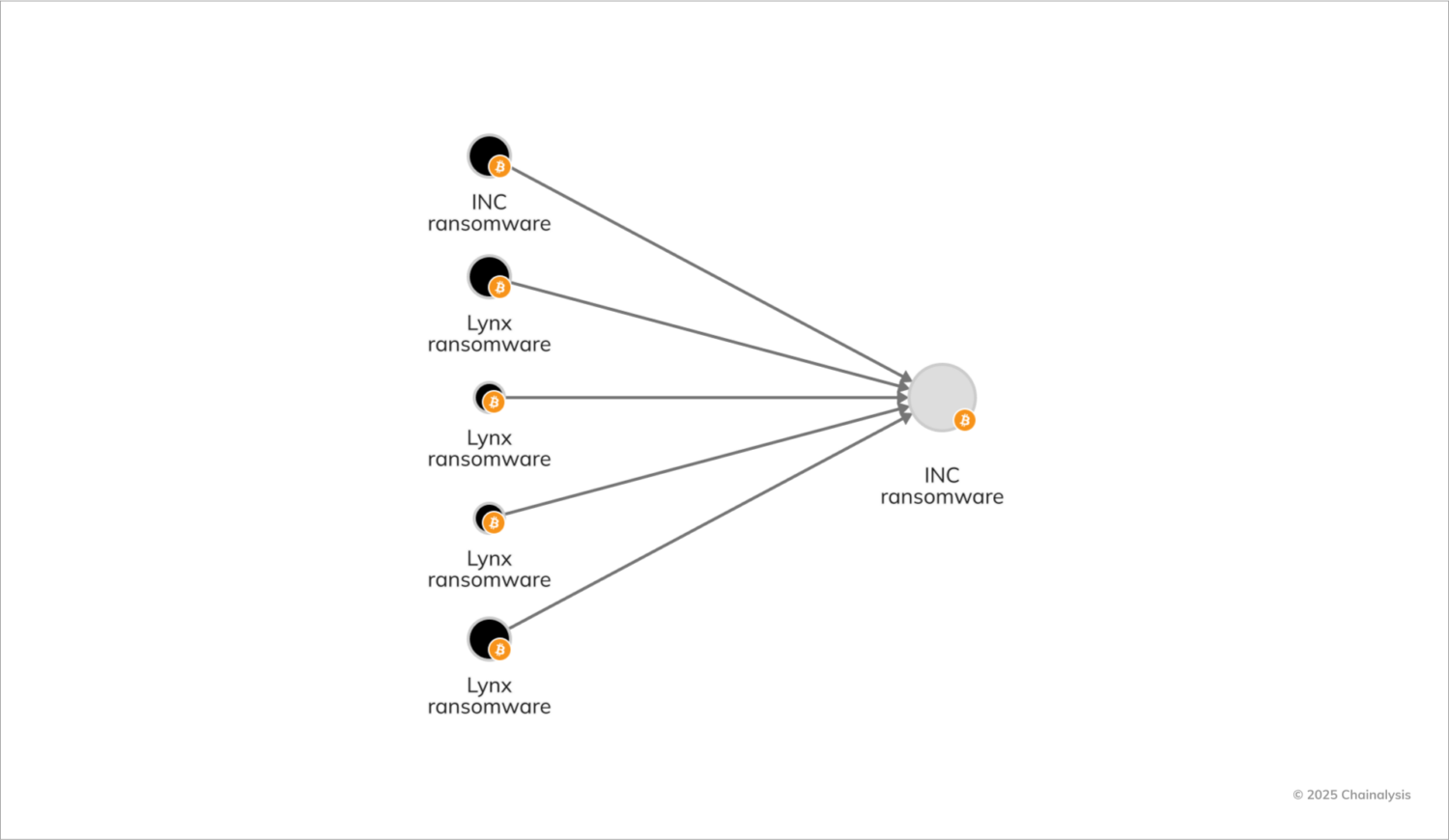
These overlapping relationships illustrate a broader trend within the ransomware ecosystem: the continuous evolution of cybercriminal strategies in response to increased law enforcement scrutiny.
Navigating an evolving threat landscape
Ransomware in 2024 reflected shifts driven by law enforcement action, improved victim resilience, and emerging attack trends. Crackdowns and collaboration with incident response firms and blockchain experts helped disrupt many ransomware groups, reducing their profitability. Victims also demonstrated greater resistance to ransom demands, widening the gap between demands and payments.
Financial strategies continue to adapt under law enforcement pressure, although malicious actors face increasing difficulties laundering payments from victims. Sustained collaboration and innovative defenses will remain critical to building on the progress made in 2024.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

