2023 so far has been a year of recovery for cryptocurrency after a chaotic 2022, with prices of digital assets like Bitcoin up over 80% on the year as of June 30. And that’s not the only good news for the industry. Our data shows that cryptocurrency-related crime is down significantly this year. Check out the graph below, which shows cumulative daily inflows to legitimate, risky, and illicit services for 2023 compared to previous years.
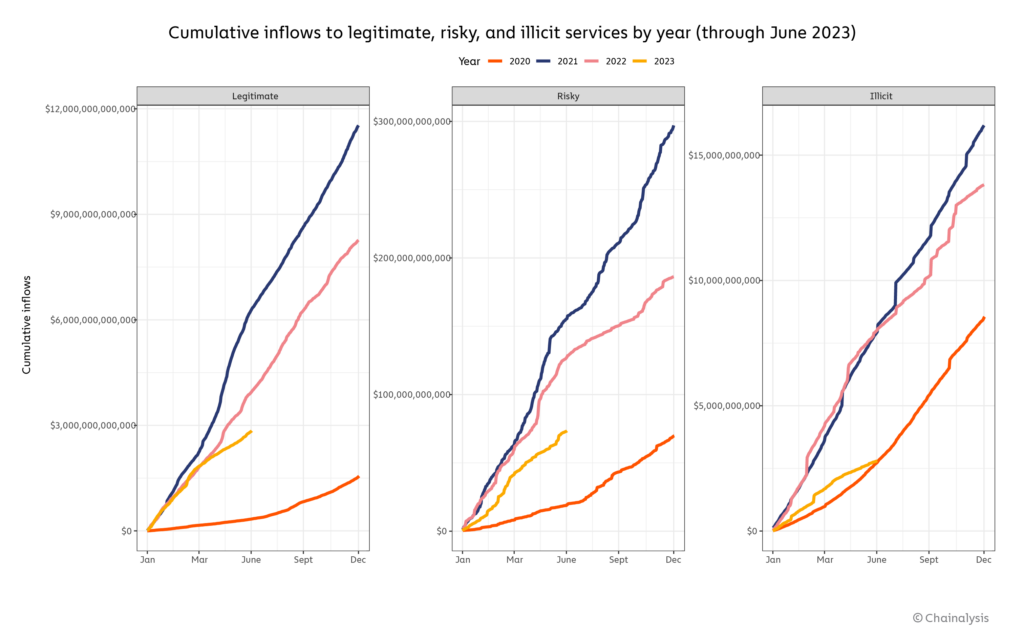
Through the end of June, crypto inflows to known illicit entities – not including inflows to entities that have been sanctioned or subject to special measures – are down 65% compared to where they were at the same time in 2022. Inflows to risky entities (made up primarily of mixers and high-risk exchanges) are down 42%. Of course, transaction volumes are down across the board, but declines are much less severe for legitimate services, which have seen just a 28% drop in inflows. In other words, there’s been a market pullback, but illicit crypto transaction volume is falling much more than legitimate crypto transaction volume.
Which specific forms of cryptocurrency-based crime are declining the most?
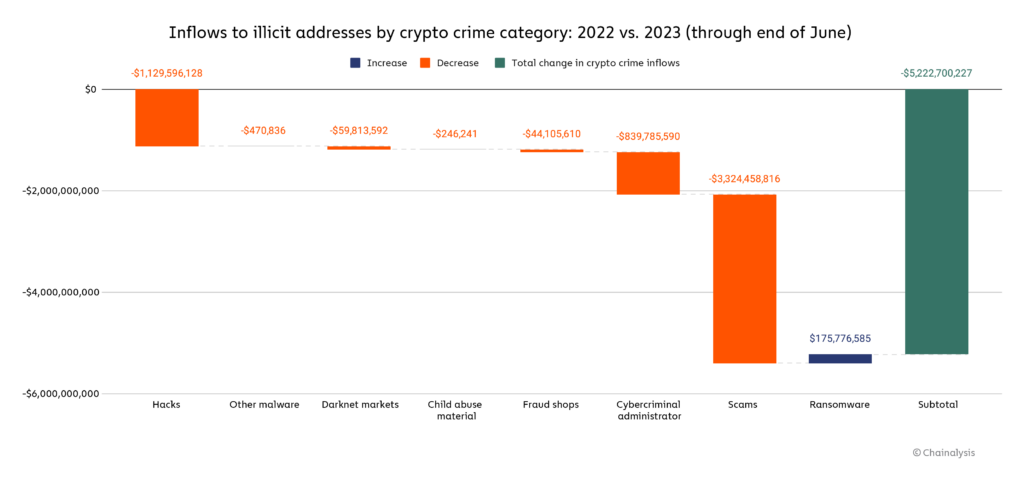
Inflows to illicit addresses are down in nearly every category, but no form of crypto crime has suffered more than scams. Through June, crypto scammers have taken in nearly $3.3 billion less in 2023 than they did in 2022, for a total of just over $1.0 billion on the year. Ransomware, on the other hand, is the only form of cryptocurrency-based crime on pace to grow in 2023, with attackers having extorted $175.8 million more than they did at the same time in 2022. This year over year growth likely means the reversal of the positive downward ransomware trend we saw in 2022. We’ll look more closely at 2023’s scamming and ransomware activity below to learn more about why they’ve declined and increased respectively in 2023.
Cryptocurrency scam revenue plummets as two of 2023’s biggest scams abruptly disappear
Scams are nearly always the highest-revenue form of cryptocurrency-based crime, and while that’s the case so far in 2023, total scam revenue has plummeted compared to last year. Through the end of June, crypto scammers have pulled in 77% less revenue than they did through June of 2022 — and keep in mind as well that 2022 itself saw a large drop in revenue compared to 2021. However, this year’s decline is arguably more notable because it comes at a time when crypto asset prices are going up. Usually, positive price movements translate to higher scam revenue, likely because increased crypto market exuberance and FOMO make victims more susceptible to scammers’ pitches. But 2023’s drastic scam decline bucks that long-standing trend.
Why is scam revenue down so much? Check out the chart below, which shows total daily crypto scam revenue and revenue for the ten largest crypto entities identified as scams by Chainalysis.
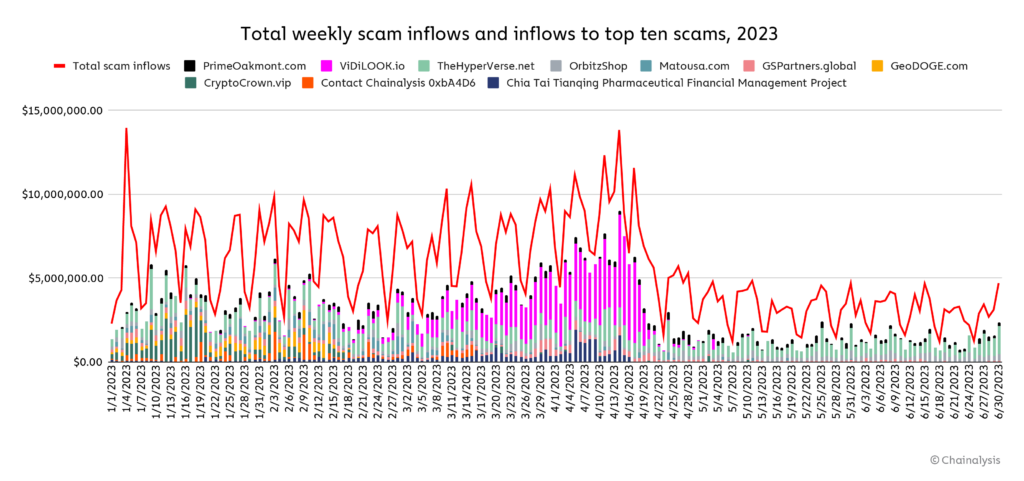
We can see here that the category’s revenue decline is largely driven by the sudden disappearance of two large-scale scams: VidiLook and, to a lesser degree, Chia Tai Tianqing Pharmaceutical Financial Management. Both scams follow the typical investment scam model of offering outsized returns on any cryptocurrency “invested” by users, but VidiLook does so with a unique twist, paying users its native VDL token in return for watching digital ads, which it then claims users can stake for large rewards.
Source: YouTube
Both VidiLook and Chia Tai appear to have exit scammed, as they’ve moved all cryptocurrency out of their primary wallets and ceased deposits and withdrawals for users. We can see how VidiLook’s exit scam unfolded on the Chainalysis Reactor graph below.
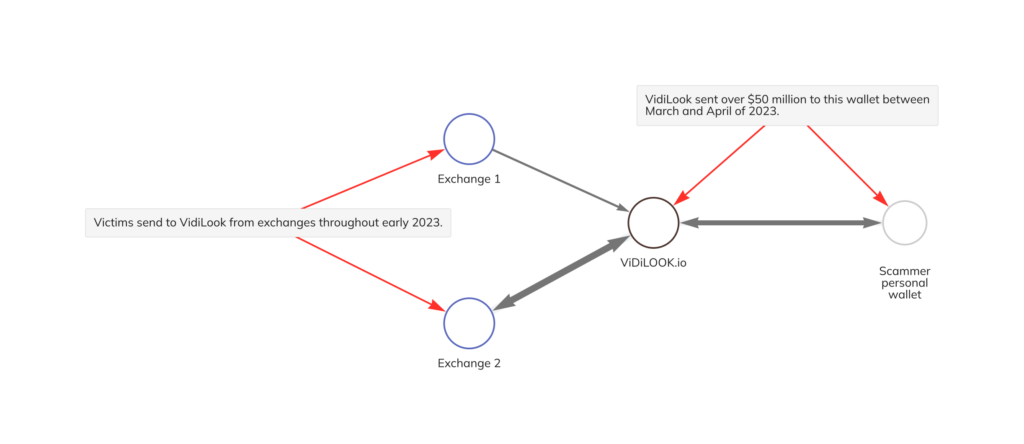
After receiving stolen funds from victims throughout the beginning of 2023, VidiLook sent over $50 million in USDT_TRX to the personal wallet on the right side of the graph during the months of March and April 2023, with most being sent after VidiLook’s reported exit scam in mid-April.
VidiLook’s exit scam isn’t surprising, but what is surprising is that total scam revenue remains so low after its decline. Ordinarily, we’d expect new scams to fill the void. But despite low overall scam revenues this year, VidiLook serves as an example of why cryptocurrency businesses, users, and law enforcement must remain vigilant — VidiLook bilked victims out of over $120 million worth of cryptocurrency in just a few months, highlighting the damage a single effective scam can do in a short period of time.
It’s also worth noting that while crypto scam revenue is significantly down as a whole, one type of scam has taken a much smaller hit than others.
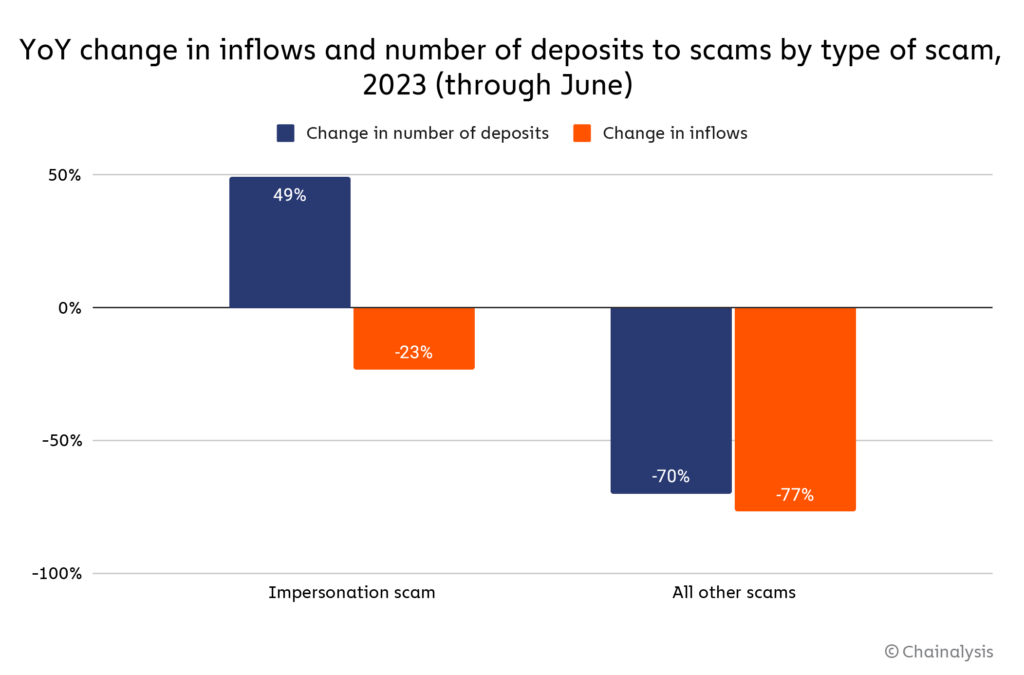
Impersonation scams, in which fraudsters impersonate a law enforcement officer or some other kind of authority figure to extort money from victims, have seen just a 23% decline in inflows so far in 2023, compared to 77% for scams as a whole. Worse yet, the number of individual transfers to impersonation scam addresses has actually increased 49% year over year, suggesting that more people have fallen victim to impersonation scams in 2023, even if the total amount lost is lower. Those data points go to show that even with total scam revenue down, law enforcement and crypto compliance teams can’t rest on their laurels.
Ransomware rising as big game hunting makes a comeback
Ransomware is the one form of cryptocurrency-based crime on the rise so far in 2023. In fact, ransomware attackers are on pace for their second-biggest year ever, having extorted at least $449.1 million through June.
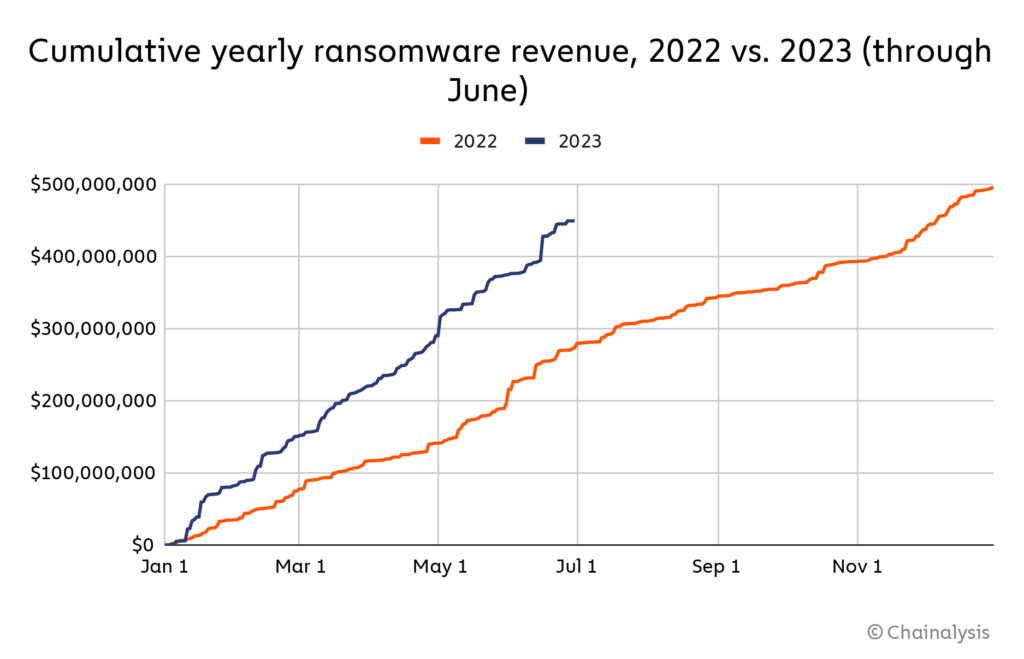
If this pace continues, ransomware attackers will extort $898.6 million from victims in 2023, trailing only 2021’s $939.9 million.
When we published our annual Crypto Crime Report in February, we were pleased to report that 2022 ransomware revenue had plummeted significantly compared to 2021. Why the reversal in fortunes? For one thing, big game hunting — that is, the targeting of large, deep-pocketed organizations by ransomware attackers — seems to have bounced back after a lull in 2022. At the same time, the number of successful small attacks has also grown. Both trends are evident on the chart below, which shows how the distribution of ransomware payment sizes has changed since 2020.
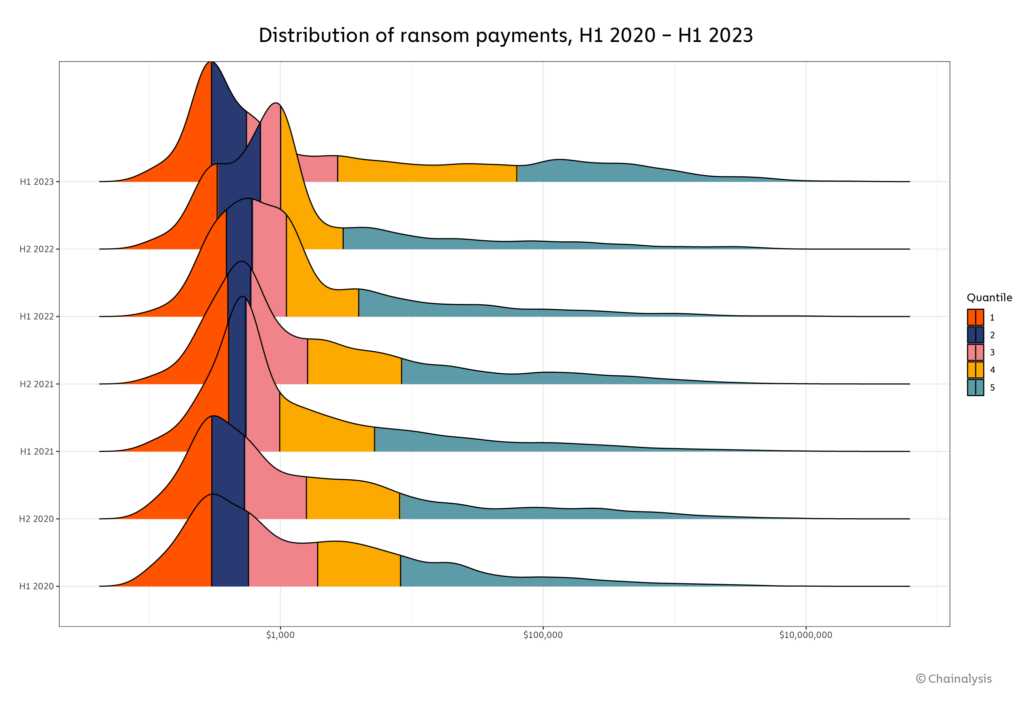
On the left side of the graph, we see an increase in the number of very small ransomware payments in 2023, while the number of very large payments on the right side has also grown substantially. The payment size distribution has also extended to include higher amounts compared to previous years. In other words, we’re seeing growth in ransomware payments at both ends of the spectrum. Below are a few ransomware strains whose average and median payment sizes reflect those extremes.
| Strain name | 2023 average payment size | 2023 median payment size |
| Dharma | $265 | $275 |
| Phobos | $1,719 | $300 |
| Stop/djvu | $619 | $563 |
| BlackBasta | $762,634 | $147,106 |
| ALPHV/Blackcat | $1,504,579 | $305,585 |
| Cl0p | $1,730,486 | $1,946,335 |
At the top of the chart, we see low-level RaaS strains like Dharma and Phobos, which are typically used in spray and pray attacks against smaller targets and can be deployed by relatively unsophisticated actors. At the bottom, we see bigger, more sophisticated strains like BlackBasta and Cl0p, which tend to be choosier with targets, hitting bigger organizations for more money. Both types of strains have been more active this year than in 2022.
Experts at cybersecurity and incident response firm Kivu have seen 2023’s changes in ransomware patterns first-hand, especially the growth in payment sizes. “These notable shifts in figures directly align with the growing number of extremely high initial demands, ranging in the tens and hundreds of millions of USD,” said Kivu General Counsel and Risk Officer Andrew J. Davis.
We previously attributed the 2022 decline in average ransom size to improved cybersecurity and data backup practices by large organizations, as well as law enforcement efforts, increased availability of decryptors, and sanctions against services offering cashout services to ransomware gangs. Those developments hurt attackers’ big game hunting efforts and enabled many victims to weather ransomware attacks without paying. That still appears to be true to some degree, as Davis told us lots of organizations are still refusing to pay in 2023. However, he also posited that the non-payment trend may be prompting ransomware attackers to increase the size of their ransom demands, perhaps with the intention of squeezing the most money possible out of the firms still willing to pay ransoms. To that end, Davis also noted an increase in more extreme extortion techniques, such as harassment of employees from victim firms who have not yet paid.
We also can’t discount the role of the Russia-Ukraine War in last year’s ransomware decline, as the conflict likely displaced ransomware operators and diverted them away from financially inspired cyber intrusions. We’ve previously reported that the majority of ransomware revenue goes to strains with Russian ties, and it stands to reason that the conflict disrupted ransomware operators’ ability to conduct attacks or perhaps even their mandate for such attacks. For example, Google reported earlier this year that the Cuba ransomware gang had pivoted from financially motivated crimes to espionage. It is clear the ransomware ecosystem has rebounded in 2023 both in terms of payments and attacks, with record-setting incident numbers. The data serves as an important reminder that ransomware remains a significant threat, and that businesses should continue to shore up their cybersecurity and data backup procedures for added protection.
2023 is off to a good start
With the exception of ransomware, Chainalysis data shows that crypto crime as a whole is in sharp decline in 2023. This decrease in inflows to illicit addresses shows that the efforts of both the private and public sectors are paying off — law enforcement pressure appears to be dampening criminal activity, while crypto businesses are doing their part in protecting users from scams and preventing the hacks that have been such an issue in previous years, especially for DeFi protocols. However, the persistent scourge of ransomware demonstrates the need to remain vigilant. We’ll continue to monitor these trends, share updates as possible, and look forward to sharing our year end findings in our next Crypto Crime Report.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

