In many ways, the inherent transparency of blockchains makes cryptocurrency investigations easier for law enforcement than financial investigations involving fiat currency. Blockchains act as a permanent, publicly viewable ledger of nearly all cryptocurrency transactions, making it possible for investigators to track funds’ movements between cryptocurrency addresses, something that simply isn’t possible with fiat currency.
However, cryptocurrency addresses are pseudonymous, which means investigators need reliable data attributing those addresses to services and organizations in order to draw actionable insights from blockchains’ transaction records. Incorrect or absent address attributions and misunderstandings of how cryptocurrency businesses handle funds can lead investigators to false conclusions, so it’s important that investigators use best-in-class blockchain analysis tools to limit these mistakes and carry out successful analyses. Below, we’ll examine three of the most common mistakes investigators can make in cryptocurrency investigations when faulty or incomplete blockchain data leads them astray.
Failure to identify mixers
Mixers are services that obfuscate the path of funds by pooling cryptocurrency from multiple users, and giving each one back an amount from the pool equal to what they initially put in, minus a small service fee. Everyone ends up with a “mix” of the funds everyone else put in, which makes it more difficult to connect the inputs to an output on the users’ transactions. Criminals frequently use mixers in an effort to hide the illicit origins of their cryptocurrency.
Mixers aren’t a dead end in blockchain analysis — investigators can often continue to follow funds even if they’ve moved through these obfuscatory services. However, investigators need to know they’re dealing with a mixer in the first place in order to do that, but they can’t unless they’re using a blockchain analysis tool that’s tagged the addresses in question as belonging to a mixer. Let’s look at a real-world example to show what can go wrong if mixers aren’t properly identified.
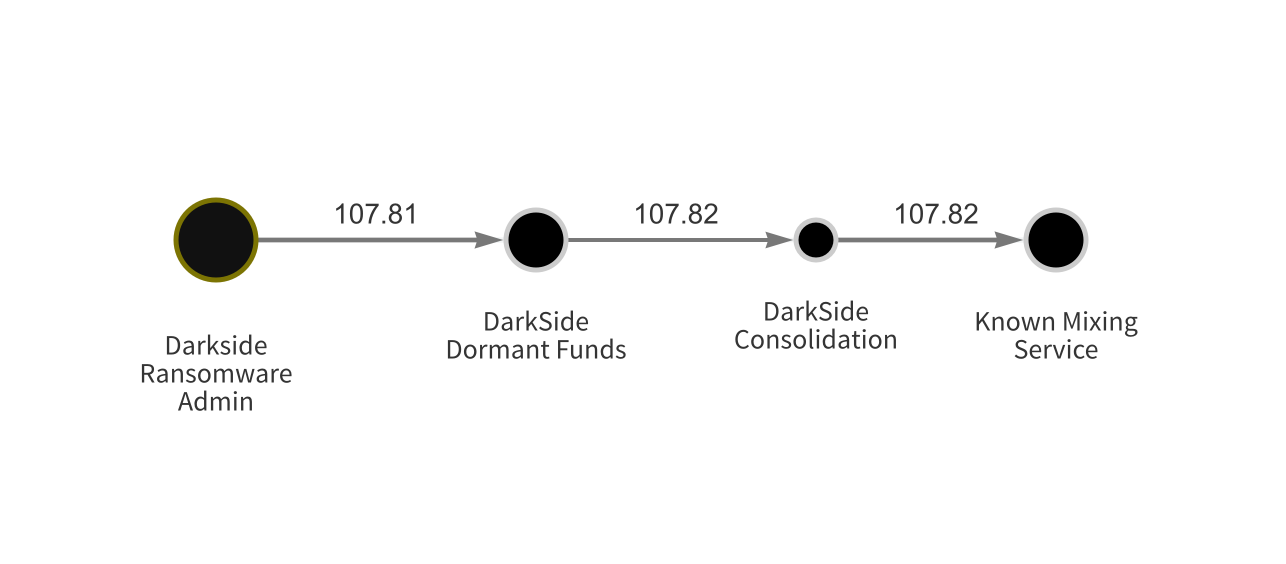
The Chainalysis Reactor graph above shows recent transactions carried out by an administrator of DarkSide, the ransomware strain behind the May 2021 attack on Colonial Pipeline. Soon after the attack, the administrator moved funds to an intermediary wallet we’ve labeled “DarkSide Dormant Funds,” where they sat until October 21, 2021. On that date, the funds were moved to a second intermediary wallet (DarkSide Consolidation) and roughly one hour later moved to a mixer, whose name we can’t reveal as the investigation is ongoing.
It’s possible to see this activity in Reactor because Chainalysis has previously identified the receiving address on the final transaction seen above as belonging to the mixer in question. However, if users attempted to analyze this transaction using a public block explorer or a blockchain analysis tool that hasn’t cataloged the receiving address as part of a mixer, they wouldn’t be able to tell what’s happening. Instead, they would see funds moving to several different addresses in quick succession, in a pattern resembling a peel chain.
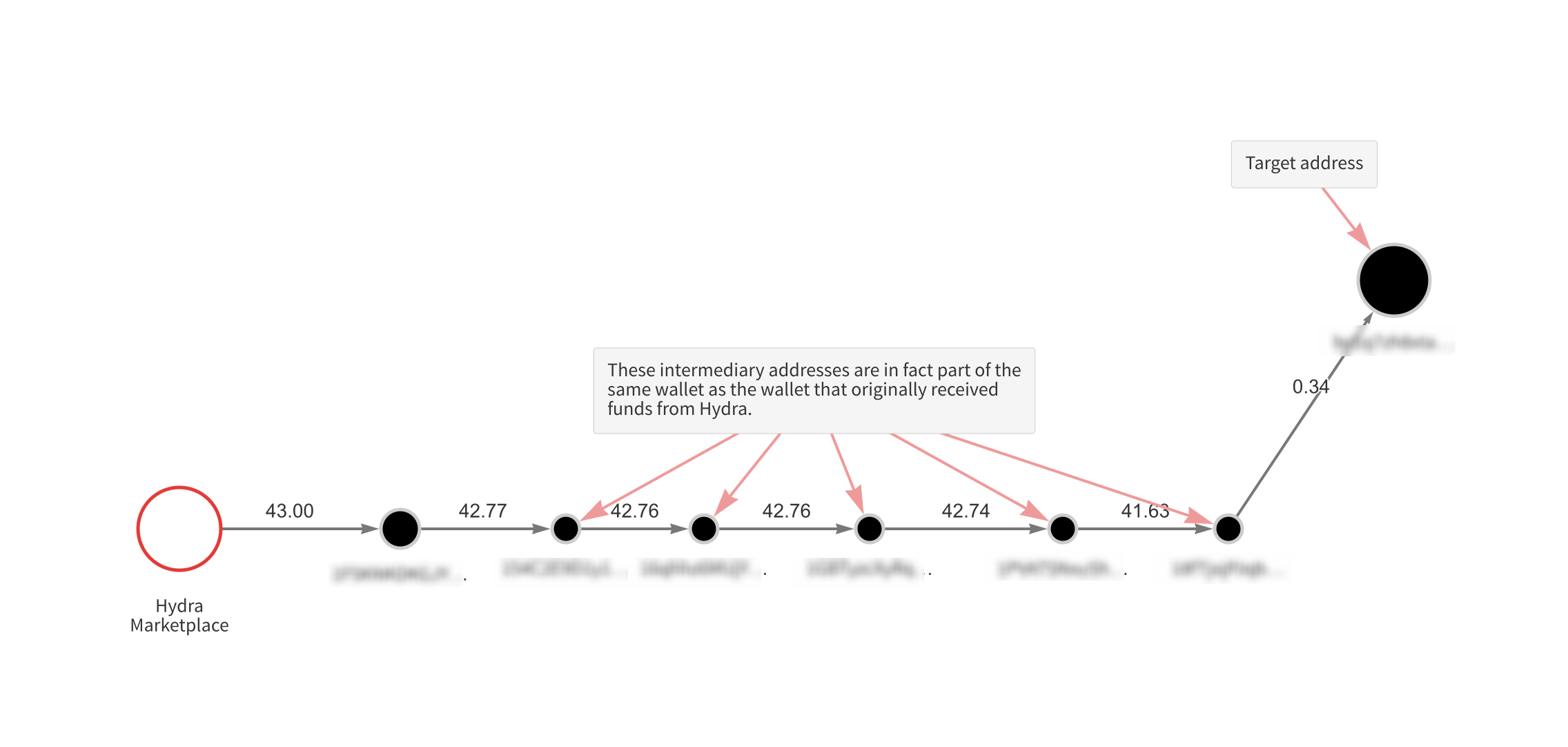
A peel chain is a transaction pattern commonly seen in blockchain analysis, in which funds appear to move through several intermediate addresses. In reality though, those intermediate addresses are part of a single wallet, and are created automatically to receive the leftover change that results from certain transactions. In the case of an unidentified mixer, the intermediate addresses are part of the mixer itself rather than a wallet, and the new addresses are made not to receive trades, but instead to distribute funds to new addresses also hosted by the mixer, from which they can be distributed to the mixer’s users. Peel chain-like patterns stemming from unidentified mixer usage have likely contributed to the belief that peel chains themselves are an obfuscatory technique for criminals seeking to launder cryptocurrency. In reality, while cybercriminals may often take advantage of the confusion they can cause investigators, peel chains are a naturally occurring pattern arising from how cryptocurrency wallets are designed to collect change from transactions.
Recent reporting characterizing DarkSide’s fund movements as merely being part of a peel chain suggest that investigators may have used a blockchain analysis tool that didn’t catalog the addresses of the mixer DarkSide administrators used. Those investigators likely reached the incorrect conclusion that DarkSide’s funds have been collected in one or more self-hosted wallets, when in reality they’ve been mixed and sent to the DarkSide administrator at a new address. Those investigators also appear to have continued following funds — funds no longer under DarkSide administrators’ control — as they left the mixer and went to services like exchanges. This may have resulted in erroneous subpoenas, wasting the time and resources of both the investigators and the exchanges.
Attempting to trace funds through a service
As we saw in the examples above, criminals often move cryptocurrency through intermediary wallets in an attempt to throw investigators off the trail. These transactions are relatively easy to trace with most blockchain analysis tools, as investigators can rely on the blockchain to show them which new address received funds following each transaction. However, investigations become trickier when funds hit a service like an exchange, as it’s impossible to trace where funds are sent after they’ve arrived at a deposit address hosted by a service. The blockchain alone – without attribution data like Chainalysis data – is no longer a reliable source of truth at this point.
Why is this? It has to do with how services manage users’ cryptocurrency. When someone sends cryptocurrency to their deposit address at a service, the cryptocurrency doesn’t just sit at that address. Instead, the service moves it around internally as needed, pooling and co-mingling it with the funds of other users as needed. For instance, many exchanges keep portions of deposited funds in cold wallets disconnected from the internet for security reasons. This idea holds true in the fiat world as well — if you deposit a $20 bill at an ATM and then withdraw $20 one week later, you’re not going to receive the exact same bill you originally had.
Of course, blockchains don’t know that services’ internal fund movements aren’t ordinary transactions as we understand them — they get recorded in the ledger just like any other transaction. Therefore, it doesn’t make sense to continue following funds once they’ve been deposited at a service, as the owner of the deposit address isn’t usually the one moving them after that point. Only the exchange itself knows which deposits and withdrawals are associated with specific customers, and that information is kept in the exchange’s order books, which aren’t visible on blockchains or in Chainalysis’s data platform.
In order to prevent investigators from mistakenly following funds after they’ve been deposited at a service, Chainalysis Reactor doesn’t show the outgoing transaction history for individual service deposit addresses.
Novice investigators using public block explorers or blockchain analysis tools without this safeguard sometimes end up sending erroneous subpoenas asking for information on exchanges’ internal addresses, leading to wasted time and resources.
Failure to identify nested services and merchant services providers
Nested services are cryptocurrency services that operate using addresses hosted by larger exchanges in order to tap into those exchanges’ liquidity and trading pairs. Over-the-counter (OTC) brokers are a common example though many of them operate as standalone services. Clients of merchant services providers operate in a similar way. Merchant services providers allow mainstream businesses to accept cryptocurrency as payment for products and services, similar to payment processors in the fiat world. The businesses using the merchant services providers are analogous to the nested services described above, in that they receive cryptocurrency using addresses hosted by another business. That means that investigators can draw false conclusions in cryptocurrency investigations if they trace funds to an address that isn’t properly labeled as belonging to a nested service or merchant services provider.
We saw an example of this in June 2021, when some news outlets reported that addresses associated with ransomware strain Ever101 sent funds to an address belonging to RubRatings, an adult website that accepts cryptocurrency payments. This finding was false. Ever101 had in fact sent funds to a deposit address hosted by a merchant services provider of which RubRatings was also a client.
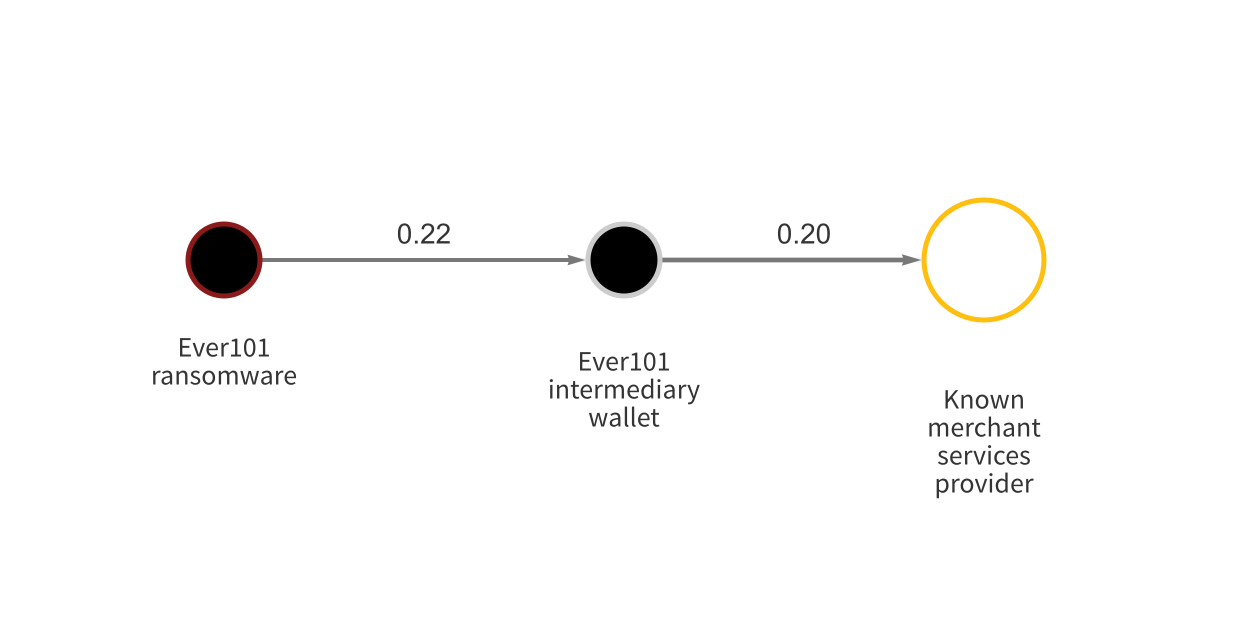
Investigators were led astray because they used a blockchain analysis tool that mislabeled all addresses in the merchant services provider’s wallets as belonging to RubRatings, not realizing that RubRatings was one of many clients receiving funds at addresses hosted by the merchant services provider. That error led to false news reports, and could have led law enforcement to mistakenly subpoena RubRatings rather than the merchant services provider, who may have been able to provide more information on the account using the address in question.
Maps need accurate labels
Think of the blockchain as a map that shows you where cryptocurrency moves. It’s useful, but by default, the blockchain is a map where none of the countries are labeled, which makes its actionability limited. As the blockchain data platform, Chainalysis fills out the map, providing the labels that allow investigators to understand who’s in control of funds when they move to a specific address. If labels are inaccurate, investigators will waste time and resources chasing down inaccurate leads. The mistakes we describe above mostly boil down to incorrect or absent labeling, and show why it’s so important for investigators to evaluate blockchain analysis providers’ track record of attributing cryptocurrency addresses to the correct services — their ability to accurately label the map. Blockchain analysis tools are only as good as their underlying data.
If you’d like to learn more about Chainalysis’ constantly growing blockchain dataset and how it gives investigators reliable, actionable insights, please contact us here.
