Approval phishing is a scamming tactic that has existed for many years. But whereas approval phishing scammers have historically targeted wide swaths of crypto users through the proliferation of fake crypto apps, romance scammers (also known as pig butchering scammers) appear to have adopted this technique to great effect in recent years.
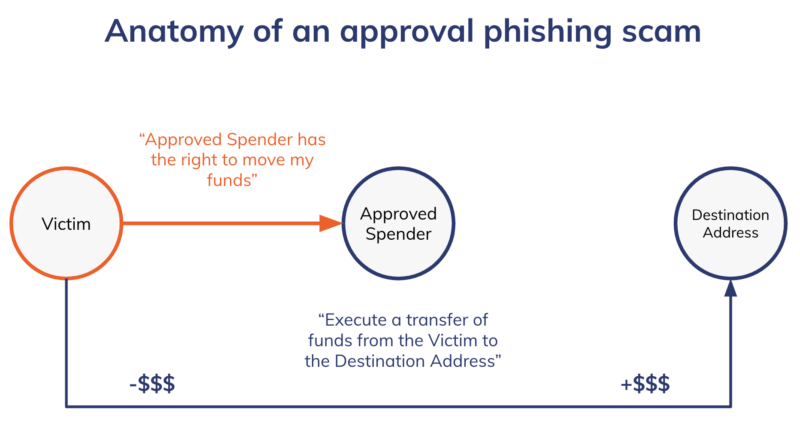
Approval phishing differs from other crypto scams in a small but important way. Typically, scammers trick victims into sending them cryptocurrency, usually through a phony investment opportunity or by impersonating somebody else. But in an approval phishing scam, the scammer tricks the user into signing a malicious blockchain transaction that gives the scammer’s address approval to spend specific tokens inside the victim’s wallet, allowing the scammer to then drain the victim’s address of those tokens at will. Some victims have lost tens of millions to these scams.
It’s important to note that in general, approval phishers send the victim’s funds to a separate wallet from the one granted approval to make transactions on the victim’s behalf. The on-chain pattern typically proceeds as follows:
- Victim address signs transaction approving second address to spend its funds
- Second address, which we’ll refer to as approved spender address, executes transaction to move funds to a new destination address
In general, if transactions unfold in this manner, and the approved spender address is the initiator of the draining transaction, rather than the victim address as we’d expect in a non-malicious transaction, it’s likely an instance of approval phishing. However, further investigation would be necessary to know for sure.
Many decentralized apps (dApps) on smart contract-enabled blockchains, like Ethereum, require users to sign approval transactions giving the dApps’ smart contracts permission to move funds held by the user’s address. Approvals granted to secure dApps are generally safe because properly designed smart contracts can only use that approval when directed to do so by the user, or when such approval is required in the normal functioning of the dApp. In those cases, we would generally expect the dApp user’s address to be the one initiating the transaction to spend the funds. But, approval phishers can take advantage of the fact that many crypto users are used to signing approval transactions — the trick is in what permissions are given, and the trustworthiness of the party receiving that permission. For instance, one approval phishing scam saw fraudsters promote a bogus story of a Uniswap approval phishing scam, and set up a fake Etherscan page where users could check their transaction approvals by connecting their wallets and signing an approval transaction to see if they’d fallen victim — that last transaction was the core of the actual approval phishing scam.
However, research suggests that approval phishers are now more and more targeting specific victims, building relationships with them and using tactics associated with romance scams to convince victims to sign approval transactions. Metamask lead product manager Taylor Monahan (aka @tayvano_) has tracked romance scam-style approval phishing on a custom Dune Analytics dashboard.
We identified a set of 1,013 addresses involved in what appears to be targeted approval phishing by starting with a smaller list of approval phishing addresses whose owners are known to be using romance scam tactics. We then identified other addresses connected to those in the initial list that had executed similar transactions, effectively allowing us to build out a more complete network of interconnected approval phishers’ on-chain activity. We estimate that victims of the addresses we started with, plus those we identified based on their distinct pattern of activity, have lost approximately $1.0 billion to approval phishing scams since the start of our dataset in May 2021. While it’s important to note that this $1.0 billion total is an estimate based on on-chain patterns, and that some of it could represent laundering of funds already controlled by the scammers, this figure is likely just the tip of a much larger iceberg. Romance scams are notoriously underreported, and our analysis began from a limited set of reported instances.
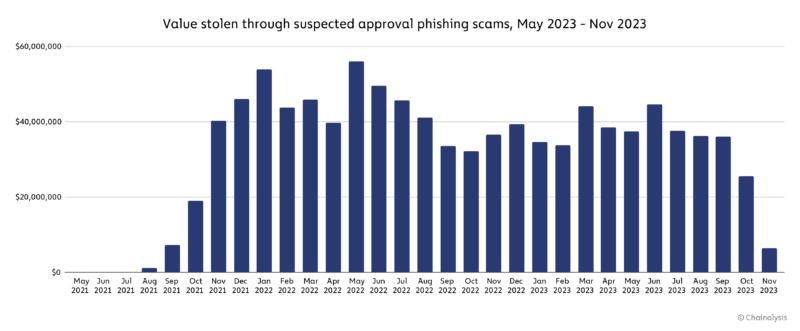
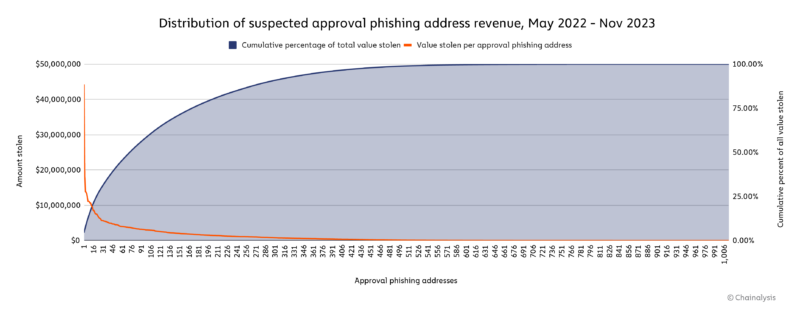
The suspected approval phishing scammers we’re tracking saw their revenue peak in May 2022. Overall, 2022 saw victims lose an estimated $516.8 million to approval phishing, versus just $374.6 million in 2023 through November. Like many forms of cryptocurrency-based crime, the vast majority of approval phishing theft is driven by a few highly successful actors. We can see this on the distribution graph below, which shows the approval phishing revenue of our 1,013 addresses during the time period studied, and the cumulative share of all value stolen through approval phishing by the addresses in our sample in descending order.
The most successful approval phishing address likely stole $44.3 million from thousands of victim addresses, representing 4.4% of the total estimated stolen during the time period studied. The ten largest approval phishing addresses combined account for 15.9% of all value stolen during the time period studied, while the 73 biggest account for half of all value stolen.
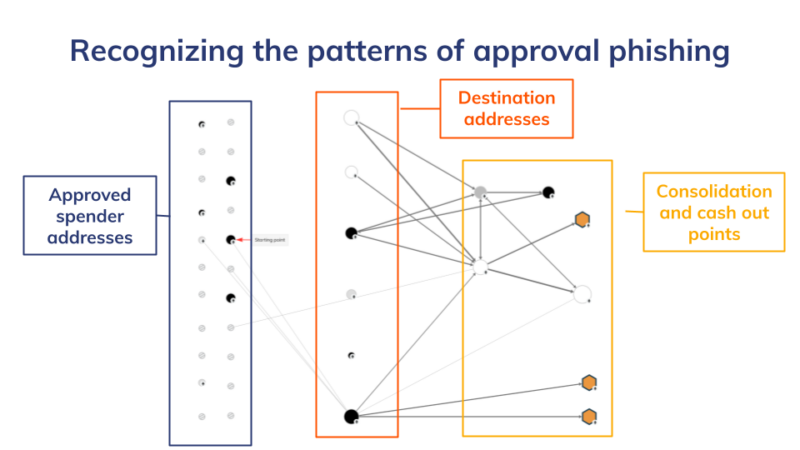
We believe that the industry can address the approval phishing scam problem in a variety of ways, from user education to employing pattern recognition tactics similar to those we used to compile this data. Generally speaking, the relevant addresses and wallets in approval phishing scams are:
- Approved spender wallets victims are tricked into designating as approved to spend funds in their wallet
- Destination addresses to which victim funds are drained
- Consolidation addresses where funds drained from many victims are gathered
Funds are typically moved from consolidation addresses to cash out points — primarily centralized exchanges — as we see on the graph below.
Based on the patterns identified above, exchange compliance teams could monitor the blockchain for suspected approval phishing consolidation wallets with heavy exposure to destination addresses. They could then see in real time when those wallets move funds to their platform, and then could take steps such as automatically freezing the funds or reporting to law enforcement. More broadly, the industry can work to educate users not to sign approval transactions unless they’re absolutely sure they trust the person or company on the other side, or understand the level of access they’re granting.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, investment, regulatory or other professional advice, nor is it to be relied upon as a professional opinion. Recipients should consult their own advisors before making these types of decisions. Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information herein. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.