Last month, national leaders in the U.S. compared the global surge in ransomware events to the terrorism threat following the September 11 attacks. These comments came at the same time the U.S. Department of Justice voiced its intention to treat ransomware with the same urgency it does terrorism. Other leaders have also spoken out about the threat from ransomware and called for global action. I was struck by the parallel between counterterrorism and ransomware, having worked counterterrorism and technology matters for many years over my law enforcement career, and there are effective strategies we can apply from counterterrorism to the ransomware problem.
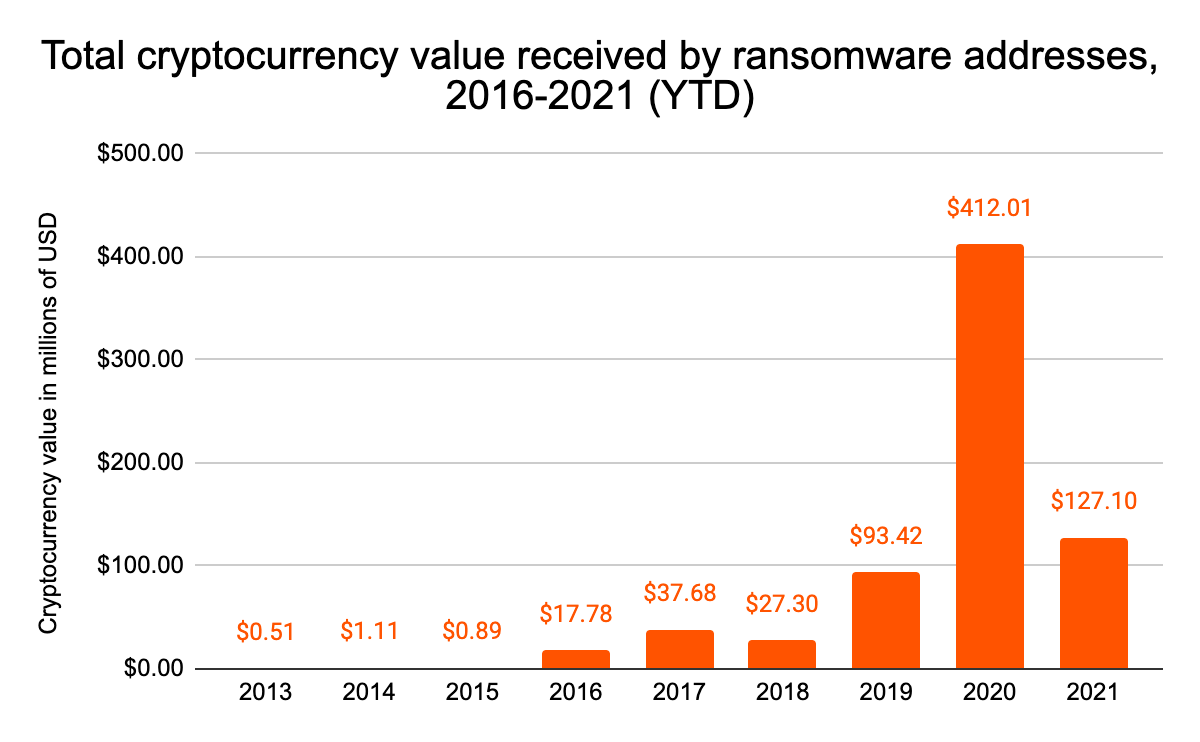
It’s no surprise government officials are drawing these comparisons given the size and scope of the growing ransomware threat. Based on our analysis of available blockchain data, in 2020 ransomware attackers successfully extorted at least $412 million from victim organizations, more than quadrupling their 2019 totals. Attackers show no signs of slowing down this year, having received more than $127 million in 2021 as of May 28. The worst may be yet to come, as July 3rd saw the beginning of perhaps the biggest ransomware attack yet, with REvil infecting over one million computers by exploiting a vulnerability in software used by IT provider Kaseya. REvil is currently demanding a blanket $70 million ransom to free all affected systems.
Keep in mind too that the true cost of ransoms is likely much higher given the inherent nature of underreporting for such crimes, not to mention the cost of rebuilding after attacks. For instance, the Ireland Health Service Executive (HSE) Director General is projecting costs of $600 million after suffering a ransomware attack more than six weeks ago.
Of course, as with terrorism, the stakes of ransomware go far beyond financial losses and business disruption. Attackers frequently target government institutions and organizations associated with critical infrastructure we all rely on, including banking, hospitals, energy facilities, and food businesses, which can lead to loss of life, both directly and indirectly. Much like terrorists, ransomware attackers leverage fear, chaos, and disruption to terrorize and coerce their victims to accomplish their objectives.
However, the parallels between ransomware and terrorism extend past the problem itself and into the solutions. At its core, the overlap boils down to the need for governments and private industry to increase the resources devoted to countering this threat and to find more effective ways to collaborate. Combined, these efforts will serve to disrupt supporting networks and raise the cost to ransomware attackers. This will diminish their ability to carry out future attacks and de-incentivize their illicit activity. We’ll explore these concepts below.
Raising the cost of ransomware attacks
Right now, many ransomware attackers are operating with impunity because the rewards outweigh the costs. We must find effective ways to de-incentivize future ransomware actors and raise the physical and financial costs to those conducting or enabling a ransomware attack. Until this equation changes, we are likely to see more ransomware attacks.
Attackers can make millions of dollars if they successfully target the right organization. Most of those behind the biggest ransomware strains operate in jurisdictions – like Russia and Iran – where they’re unlikely to face the consequences of their actions, even when identified. One successful attack helps fund the next attack and the cycle of exploitation repeats with increasing velocity, volume, and consequence. Additionally, these attacks serve to undermine and diminish confidence in the government and private sector’s ability to protect us and safeguard our information. Furthermore, the evolution of a sophisticated supply chain devoted to ransomware means it’s never been easier to carry out an attack.
The ransomware-as-a-service (RaaS) model allows relatively unsophisticated cybercriminals to “rent” access to top-tier ransomware strains in exchange for a small cut of any funds they extort. The abundance of third-party providers willing to sell attackers the technical infrastructure used for ransomware attacks makes ransomware a shockingly easy and low-cost crime. The barriers to entry and ability to conduct successful campaigns is now within the reach of many. What incentive is there to stop?
The situation is somewhat analogous to the global scourge of terrorism, though the motivations are different — most terrorists are driven by ideology, as opposed to ransomware attackers who claim to only want money. Similar to ransomware attackers, terrorists have historically relied on surprise, third-party facilitators, and lax jurisdictions to operate successfully. Obtaining the anticipatory intelligence of terrorist plots, identifying terrorist actors, disrupting those facilitation networks, and eliminating safe havens have allowed allied nations to not only hold terrorists accountable but also prevent future attacks. Arrests, seizures, and prosecutions have had an impact. Combined, these actions have served to raise the overall cost of terrorism to the point where some attacks were no longer viable or lead some to conclude it was not worth the risk. The same can be done for ransomware.
Too many agencies lack the data, tools, and capacity to effectively investigate ransomware. Nevertheless, the third party supply chain which has made ransomware attacks so easy to carry out represents ransomware’s biggest vulnerability. As General Stanley McCrystal stated while discussing the strategies of modern defense, “It takes a network to defeat a network.”
Because the individuals who make up this supply chain network are located all over the world, they are also increasingly vulnerable to targeting and disruption. Let’s look at a few examples.
- RaaS affiliates. Ransomware developers rely on affiliates to carry out attacks using their software. But unlike the developers themselves, affiliates can be located anywhere, and tend not to be clustered in uncooperative jurisdictions. For instance, while the operators of the notorious, now-defunct NetWalker ransomware strain were believed to be located in Russia, one of its most prolific affiliates was a Canadian national. In January 2021, authorities announced they were able to arrest him and eventually bring down the strain’s entire global operation.
- Third-party tools. Ransomware attacks often require or can be enhanced by the use of digital tools and infrastructure provided by illicit third party vendors, many of whom take payment in cryptocurrency. These tools include but aren’t limited to bulletproof web hosting, hacking tools and exploit kits, and services like on-demand DDOS attacks. As of May 2021, Chainalysis had observed a large increase in cryptocurrency sent to these types of providers from ransomware addresses. By monitoring and disrupting the vendors who have previously received cryptocurrency funds from ransomware operators, authorities can proactively identify potential campaigns as they are building and hopefully prevent future attacks from happening. There may also be opportunities for authorities to quietly take over these services temporarily in order to gather evidence on ransomware attackers, similar to what we saw recently with ANOM, an anonymous messaging app favored by criminals. Such undercover and honeypot operations not only can result in arrests and the mapping of criminal networks, but also serve to undermine confidence among criminals.
- Money laundering services. After a successful extortion, ransomware attackers must try to move stolen cryptocurrency to a place where it can be stored safe from seizure or converted into fiat. They typically do this by sending funds to mixers, low-compliance Know Your Customer (KYC) exchanges, or disreputable over the counter (OTC) brokers. There are plenty of examples of authorities shutting down cryptocurrency services that function as unregistered money service businesses or money laundering service providers. Even within a transnational criminal organization that specializes in ransomware attacks, authorities can slow down ransomware operations by targeting the organization’s money launderers, such as Ukraine did against the the cash-out and money laundering side of CLOP. Law enforcement and regulators need the resources to increase these efforts. This can also facilitate the recovery of assets for victims.
The ransomware supply chain extends around the world giving a host of governments ample opportunities to disrupt the operations of key players and follow the money. Of course, this doesn’t mean we should forget about ransomware developers and the lax jurisdictions from which they operate. Governments should look for ways to promote capacity building and incentivize these jurisdictions to stop letting ransomware attackers operate with impunity within their borders. In some cases, sustained diplomatic actions and sanctions will be required to impact these ransomware safe havens.
However, while raising the cost of ransomware attacks is the key to prevention, no single country, agency or company can do it alone.
Collaboration is key
Governments, law enforcement, regulators, financial institutions, and cryptocurrency businesses around the world must work together to enact the practices and policies necessary to disrupt and raise the cost of ransomware attacks. Again, we’ve seen collaboration enhance counterterrorism efforts in several key ways:
- International cooperation. Joint investigations, operations, and training exercises have raised the counterterrorism capabilities of military, law enforcement, and intelligence agencies around the world.
- Intelligence sharing. Frameworks and use of international terror watchlists have enabled allied agencies to share important information quickly and securely.
- Public-private partnerships. Private sector businesses have proven to be invaluable allies in counterterrorism efforts, especially in the areas of timely threat reporting, technology, and data analysis.
These same strategies can be applied to ransomware. Take threat reporting and watchlisting for example. If governments and cryptocurrency businesses brought together all of the intelligence they have on who’s carrying out and enabling ransomware attacks, they could put together a robust library of the most prolific operators, affiliates, third-party vendors, and money laundering service providers, along with the cryptocurrency data associated with these persons and entities (e.g., addresses and transaction histories). This combined threat reporting and resulting watchlist of known or suspected ransomware actors would give organizations around the world a shared understanding of who’s driving the most ransomware attacks at any given time, help all parties respond to attacks faster, and support efforts to arrest and sanction the worst offenders.
Public-private partnerships are key here, as governments will rely on blockchain analysis providers and cybersecurity firms for much of the data they would need to compile a cyber ransomware watchlist and shared standards. The Institute for Security and Technology’s Ransomware Task Force has already proven invaluable here in setting out frameworks for ransomware attack response and prevention, as well as disseminating up-to-date research on the latest ransomware trends.
Ransomware existed before the advent of cryptocurrency, but cryptocurrency has become the principal method chosen by ransomware actors to finance their operations and pay others along the way for their illicit support services. As a result, blockchain analytics of cryptocurrency becomes the unifying data set that cuts across all of these activities and empowers investigators to identify ransomware actors and the global ransomware supply chain network. Raising the cyber, cryptocurrency literacy, and investigative capabilities among government and private sector partners is key to any ransomware strategy.
Training and capacity building are areas where public-private partnerships will be important to implementing an effective strategy. Federal law enforcement agencies have made huge strides in their ability to investigate cryptocurrency-related crimes in recent years But while ransomware may be conducted globally, the impact is felt locally. The next step is to provide global training, resources, and capacity building to agencies at the state, regional, and local levels as well so they too may join the fight to effectively respond to and combat ransomware.
Want to learn more about how Chainalysis can help your organization battle ransomware? Contact us today.
We can turn the tables on ransomware
Right now, the ransomware situation feels chaotic and a bit scary, with new attacks occurring daily and responses with varying levels of success. The early days of developing a counterterrorism strategy following the September 11 attacks felt very similar. However, with time, effort, and — crucially — collaboration, we developed strategies that worked and they have had a measurable impact. To counter the threat from ransomware requires collaboration, vigilance, and sustained effort.
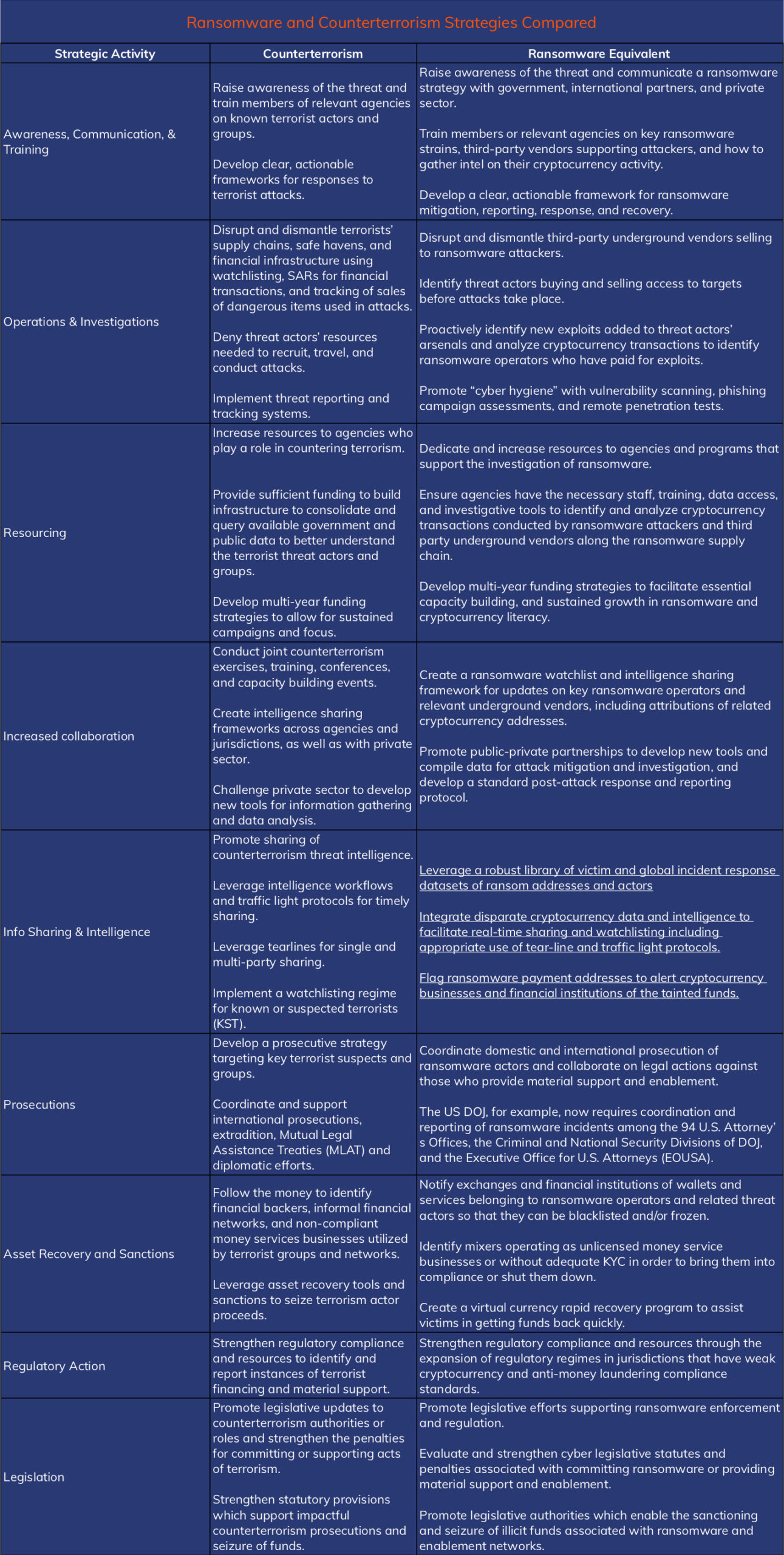
I understand I’ve thrown a lot of information at you in this blog. The below table provides a consolidated look at some of the counterterrorism strategies and how they could potentially be applied to ransomware, including some I wasn’t able to comprehensively cover in the blog.