On February 11, 2025, the United States Department of the Treasury’s Office of Foreign Assets Control (OFAC), the United Kingdom’s Foreign Commonwealth and Development Office (FCDO), and Australia’s Department of Foreign Affairs and Trade (DFAT) jointly sanctioned Zservers, a Russia-based bulletproof hosting (BPH) services provider, for its role in supporting ransomware attacks by the LockBit ransomware gang. LockBit, which historically has been one of the most prolific Ransomware-as-a-Service (RaaS) groups, was disrupted in a large, coordinated U.S.-U.K. takedown last February that is still having a meaningful impact in the ransomware space.
BPH providers allow customers to pay for web hosting anonymously, and are generally lenient on the content they allow clients to host. While many website creators have good reason to remain anonymous, BPH providers naturally attract controversial or even criminal users. For instance, darknet markets, sites facilitating prostitution and sex trafficking, and phishing sites set up to steal customers’ information by mimicking legitimate business’ websites often rely on bulletproof hosting providers to stay up and running.
Below, we’ll look at Zservers’ on-chain activity and more information about why the group was sanctioned.
Zservers: A key enabler of ransomware operations
OFAC added two Russian nationals, Aleksandr Sergeyeevich Bolshakov and Alexander Igorevich Mishin (including one cryptocurrency address associated with him), and Zservers itself (including 3 cryptocurrency addresses associated with it) to its Specially Designated Nationals (SDN) list. OFAC’s designation also includes aliases that were used to advertise Zservers’ services on darkweb forums.
In its designation notice, the U.K. Government characterized Zservers as “a key component of the Russian cybercrime supply chain” that “provides vital infrastructure for cybercriminals as they plan and execute attacks against the UK.” In addition to Bolshakov and Mishin, FCDO and DFAT also designated four additional Zservers employees, as well as its U.K. front company, XHOST Internet Solutions LP. Ransomware attacks in the U.K., including those targeting hospitals, have been a persistent priority for cybersecurity policy.
Zservers has servers in Russia, Bulgaria, the Netherlands, the United States, and Finland, and offers server admin, support, equipment, and custom configuration services, according to its homepage.
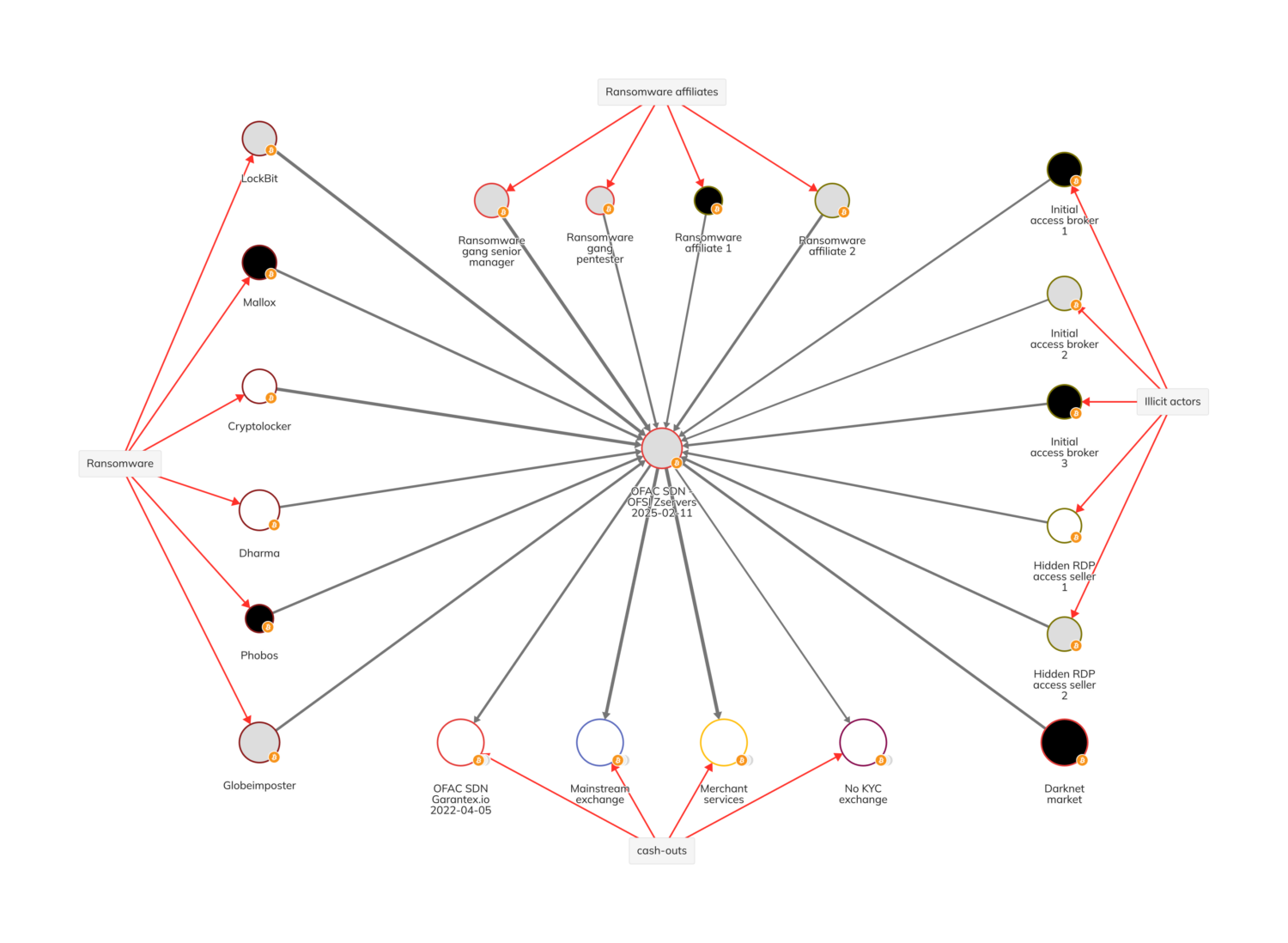
Zservers’ on-chain activities
In the Chainalysis Reactor graph below, which captures a portion of Zservers’ direct exposure to illicit actors, we see that a variety of actors have sent funds to Zservers for their services, such as ransomware groups and affiliates. For example, multiple different ransomware affiliates — beyond LockBit, the only group cited in today’s designations — sent funds to Zservers. Chainalysis data shows that Zservers has cashed out at OFAC-sanctioned Garantex, merchant services, and no-KYC exchanges. In addition to Zservers’ nested infrastructure, we are able to use Reactor to visualize its at least $5.2 million in on-chain activity and thorough connectivity to the high-risk and illicit entities described in today’s designations.
Law enforcement collaboration to disrupt ransomware gangs
Today’s coordinated sanctions against Zservers highlight the critical role played by international law enforcement cooperation in combating ransomware and disrupting infrastructure providers who facilitate on-chain cybercrime. By combining resources and intelligence, law enforcement agencies can effectively dismantle these complex cybercriminal networks that operate across borders.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

