Sensitive content warning
This article will touch on topics of criminal activity that readers may find distressing, including Child Sexual Abuse Material. The intention is not to offend but to provide information. Proceed only if you are comfortable with potentially sensitive topics.
Key findings
- Reportings of China-based CSAM sites have increased since late 2023.
- A majority of wallet holders are purchasing a month’s access or more, up to and including nearly permanent access of ~20,000 days (equivalent to more than 54 years).
- Consistent with our past findings, CSAM vendors continue to leverage instant exchangers when cashing out.
- Scammers are adapting their on- and off-chain tactics, conducting shorter but more dynamic and lucrative scam campaigns.
- Pig butchering is the largest revenue-generating scam type YTD. One Myanmar-based scam compound first observed on-chain in 2022 has netted at least $101.22 million so far this year.
- Scammers for the most part continue to pivot away from broad-based ponzi schemes to more targeted campaigns like pig butchering, work from home scams, drainers, or address poisoning.
- We’re observing a rise in the use of Chinese language marketplaces and laundering networks. One such marketplace is Huione Guarantee, tied to the Cambodian conglomerate Huione Group, which connects buyers and sellers who often do little to mask the illicit nature of their transactions.
- Huione Guarantee has processed more than $49 billion in cryptocurrency transactions since 2021, significantly more than previously reported.
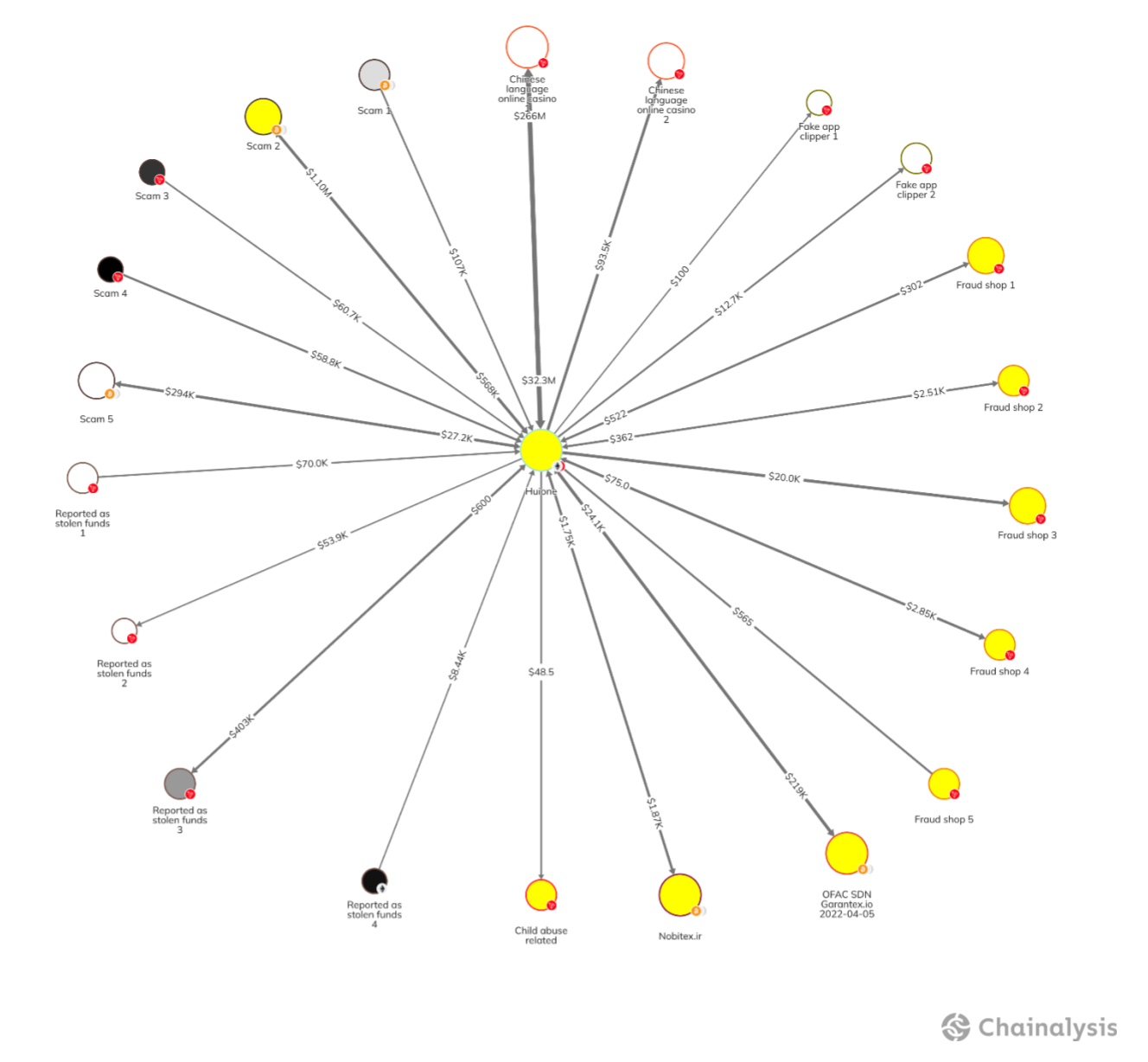
- Huione’s on-chain connections include pig butchering and other scams, addresses reported as stolen funds, the OFAC-sanctioned Russian exchange Garantex, fraud shops, CSAM, Chinese language gambling sites and casinos, and more.
In part 1 of our mid-year crime update, we discussed trends related to ransomware and stolen funds. While aggregate illicit on-chain activity declined by nearly 20% year-to-date (YTD), inflows from stolen funds nearly doubled, and annual ransomware payments are on track to be the largest ever in a single year.
In the second half of our update, we’ll examine on-chain activity related to the distribution and consumption of child sexual abuse material (CSAM), including on-chain analysis of payments that two CSAM vendors received, and what those amounts indicate.
Next, we’ll examine the latest trends in crypto scams. On- and off-chain activity shows that scammers are adapting their tactics and conducting shorter, but more lucrative and regenerative campaigns. We’ll discuss a notable scam syndicate — the highest grossing of 2024 so far — that highlights the move away from elaborate ponzi schemes toward more targeted campaigns like pig butchering in recent years.
“Pig butchering scams” are referred to as such for the way bad actors say they “fatten up” their victims to extract the most possible value. This usually involves building a romantic relationship over time with the victim via text message or dating apps until they push them to send money to a fake investment opportunity. In a dark twist, the scammers on the other end of those conversations are often individuals that have been kidnapped, trafficked to Southeast Asia, and forced to work in labor camps housed within large compounds to carry out pig butchering scams.
Last, we’ll look at Huione Guarantee, a $49 billion marketplace recently exposed for facilitating cybercrimes, including CSAM and pig butchering. Let’s get started.
China-based CSAM networks show signs of growth
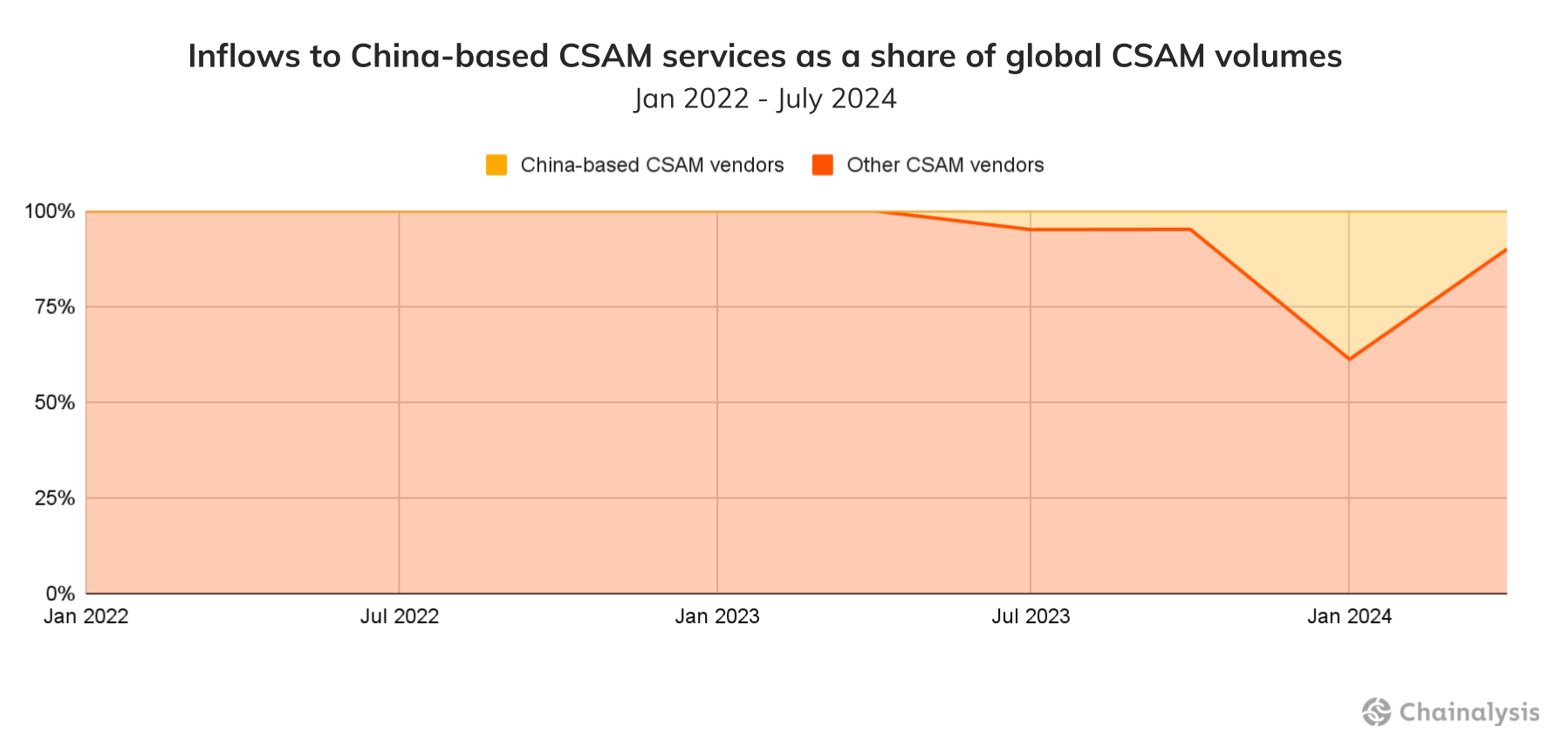
Reportings of China-based CSAM vendors have increased since late last year. The chart below shows the proportion of all CSAM activity associated with vendors denominating their activity in yuan compared to activity in other currencies. These sites provide a yuan conversion rate for crypto payments. Since roughly the end of 2023, China-based vendors have captured a larger share of global CSAM inflows, peaking so far at 38.8% of the total inflow amount in Q1 this year.
According to the Internet Watch Foundation (IWF), an organization dedicated to stopping CSAM online, it’s hard to determine why these networks are growing in China. “We are seeing an increase in the reporting of these types of sites,” says a spokesperson at the IWF. “Based only on the reporting pipeline, it is difficult to say definitively if there is an emergent trend or if these sites have existed for some time but gone unreported to authorities.” While the sites themselves may have existed for a while and gone unnoticed by the public, the on-chain infrastructure of these services is all relatively recent, with the oldest China-based wallet dating back to just July 18, 2023, and most of the other addresses coming from late 2023. At least in terms of the on-chain dimension, the timeframe for these wallets is suggestive of the idea that these services are emergent, represent a true trend, and are potentially not simply the product of a new reporting pipeline.
An on-chain examination of China-based CSAM vendors
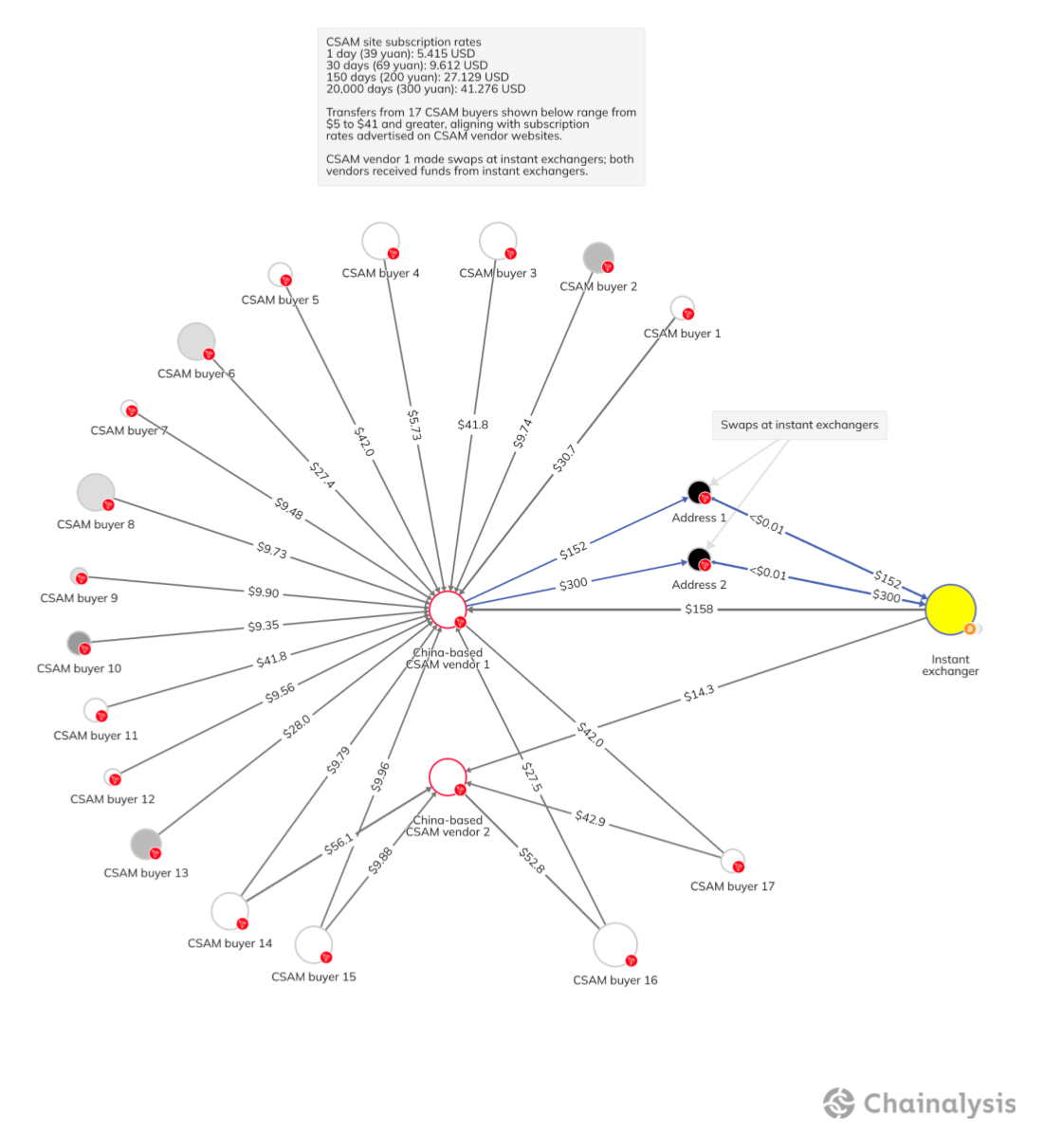
Numbers aside, it’s impossible to quantify the harm done by CSAM worldwide. Given its potential for redistribution, small purchases in the tens of dollars, as shown in the Chainalysis Investigations graph below, can still lead to the long-term exploitation of children.
The network depicted above includes two suspected CSAM vendors selling material in yuan. When referenced against the CSAM vendors’ subscription rates found on their websites, transfers to vendors from personal wallets indicate what kind of access CSAM buyers are purchasing. As noted, buyers can acquire a single day’s access to CSAM material from these vendors for just $5. They can also buy nearly permanent access (~20,000 days, that is, more than 54 years) for just $41. In this example, a majority of wallet holders are purchasing a month’s access or more. As for CSAM vendors, they’re taking advantage of instant exchangers when cashing out, consistent with our reporting earlier this year.
Scammers adapt on- and off-chain tactics; large pig butchering scam operations persist
With several billion in inflows, scams with a crypto nexus are mounting in 2024 and are one of the largest areas of illicit activity YTD. The most distinctive feature of this year’s scam landscape involves the rapid evolution of scammers’ on-chain footprint — the crypto wallets and addresses used to take scam victim payments — and the off-chain tools they use to manipulate their victims, like domains and social media accounts. This activity reveals how scammers are adapting on- and off-chain to conduct more devastating scams of shorter duration. To hedge against discovery and disruption, many of these operations regenerate or maintain many smaller, simultaneous campaigns that keep larger organized scam syndicates going.
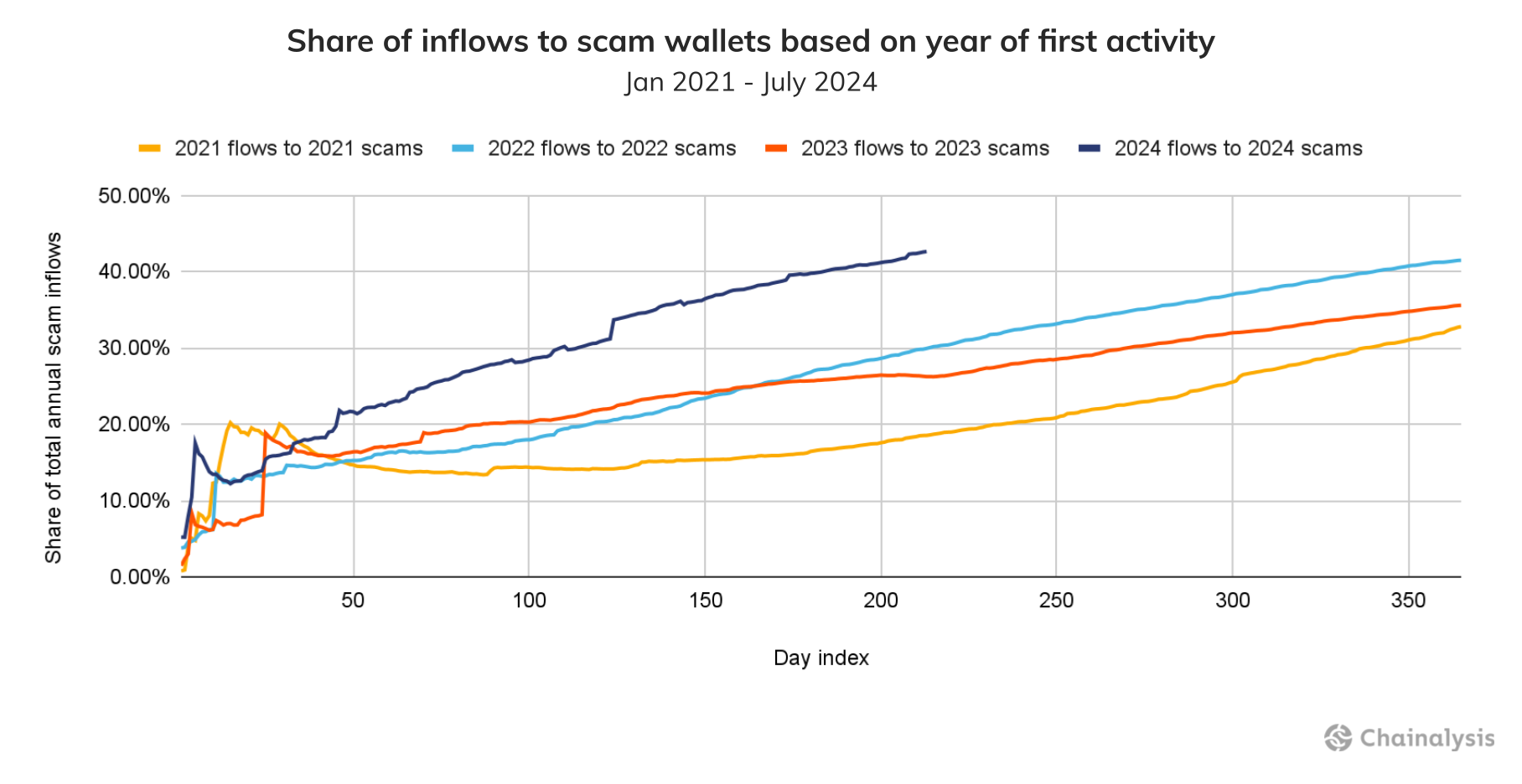
One remarkable feature of the 2024 scam landscape is how much of the total YTD scam inflows have gone to wallets that became active this year, suggesting a surge in new scams. The chart below examines the share of total scam revenue sent to wallets first seen in the year their respective scams received crypto. Notably, 43% of YTD scam inflows have gone to wallets that became active this year. This trend is significant as the next highest year, 2022, saw just 29.9% of total YTD flows go to wallets that became active that year.
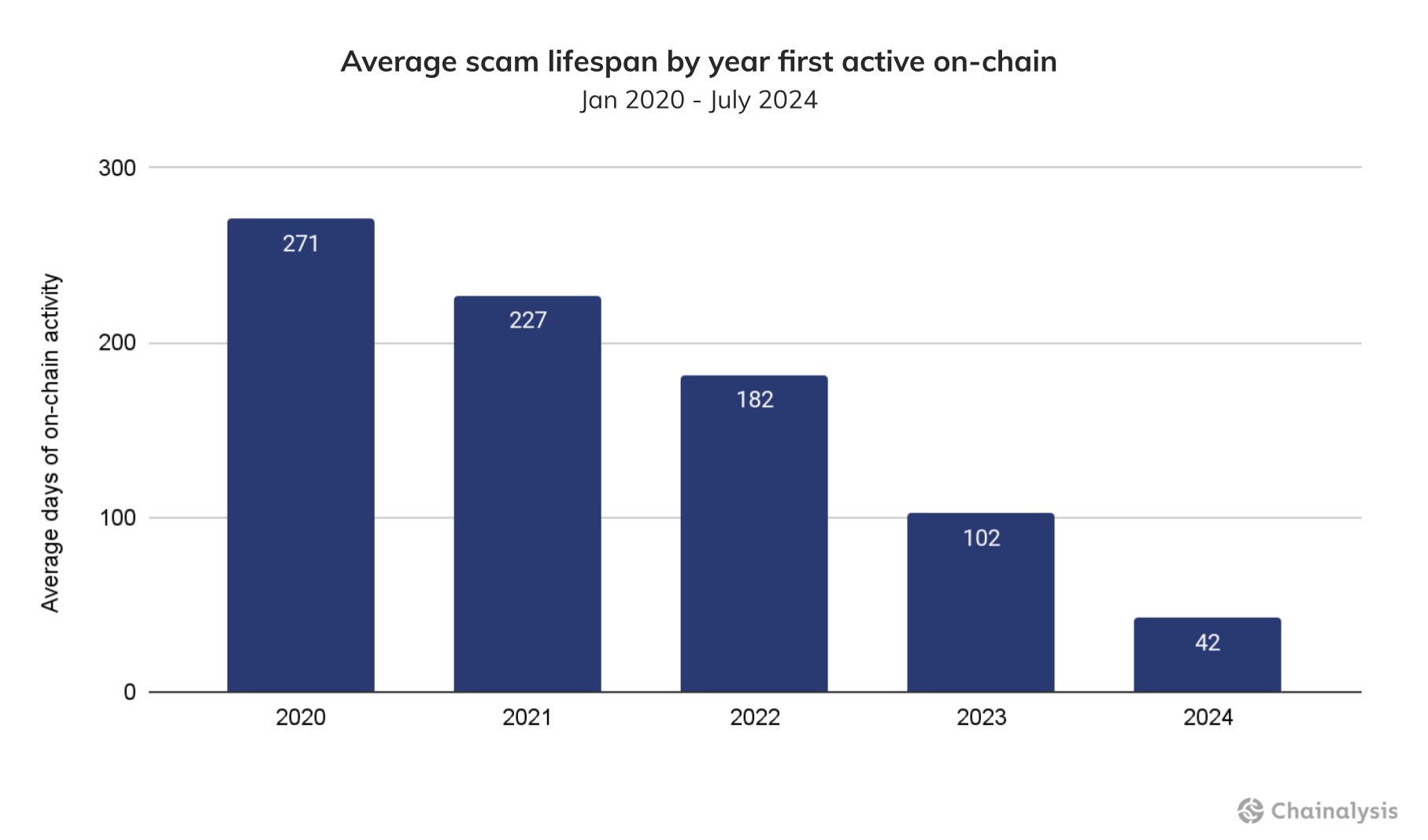
This trend is well represented by a marked decline in the average lifespan of scams, shown in the chart below. We’ve plotted this trend by counting the days between when scam activity was first and last observed on-chain. Between 2020 and 2024 YTD, the average number of days scams were active has significantly decreased, starting at 271 days for scams that began in 2020, and ending at 42 days so far for scams beginning in 2024. This macro trend is consistent with the continued pivot of scammers from elaborate ponzi schemes that cast a wide net to more targeted campaigns like pig butchering or address poisoning, driven in part by increasing enforcement efforts and stablecoin issuers blacklisting scam addresses.
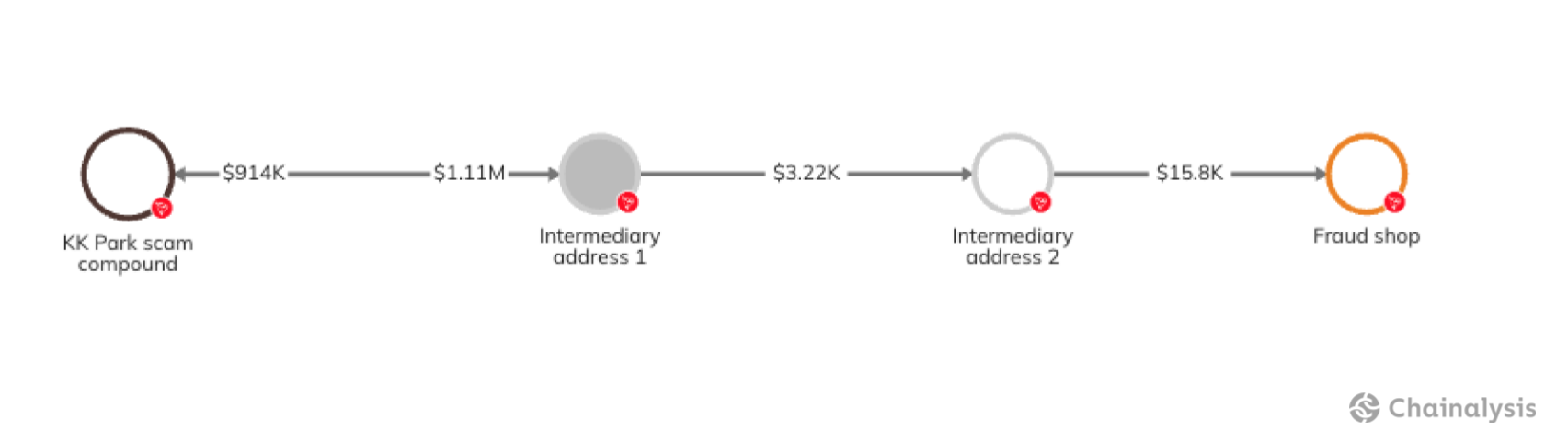
Despite the trend towards the use of fresh on-chain addresses by scammers, some 57% of 2024 YTD scam inflows are still going to wallets that became active before 2024. One of the largest single wallets associated with scamming active this year consolidates funds from many scams operating out of Myanmar’s most notorious pig butchering compound, KK Park. This wallet was first observed on-chain in 2022, and scamming operations using this address continue to generate significant revenue, netting over $100 million so far this year. Those funds could have come both from scam victims and from ransom payments submitted by families attempting to save their trafficked family members.
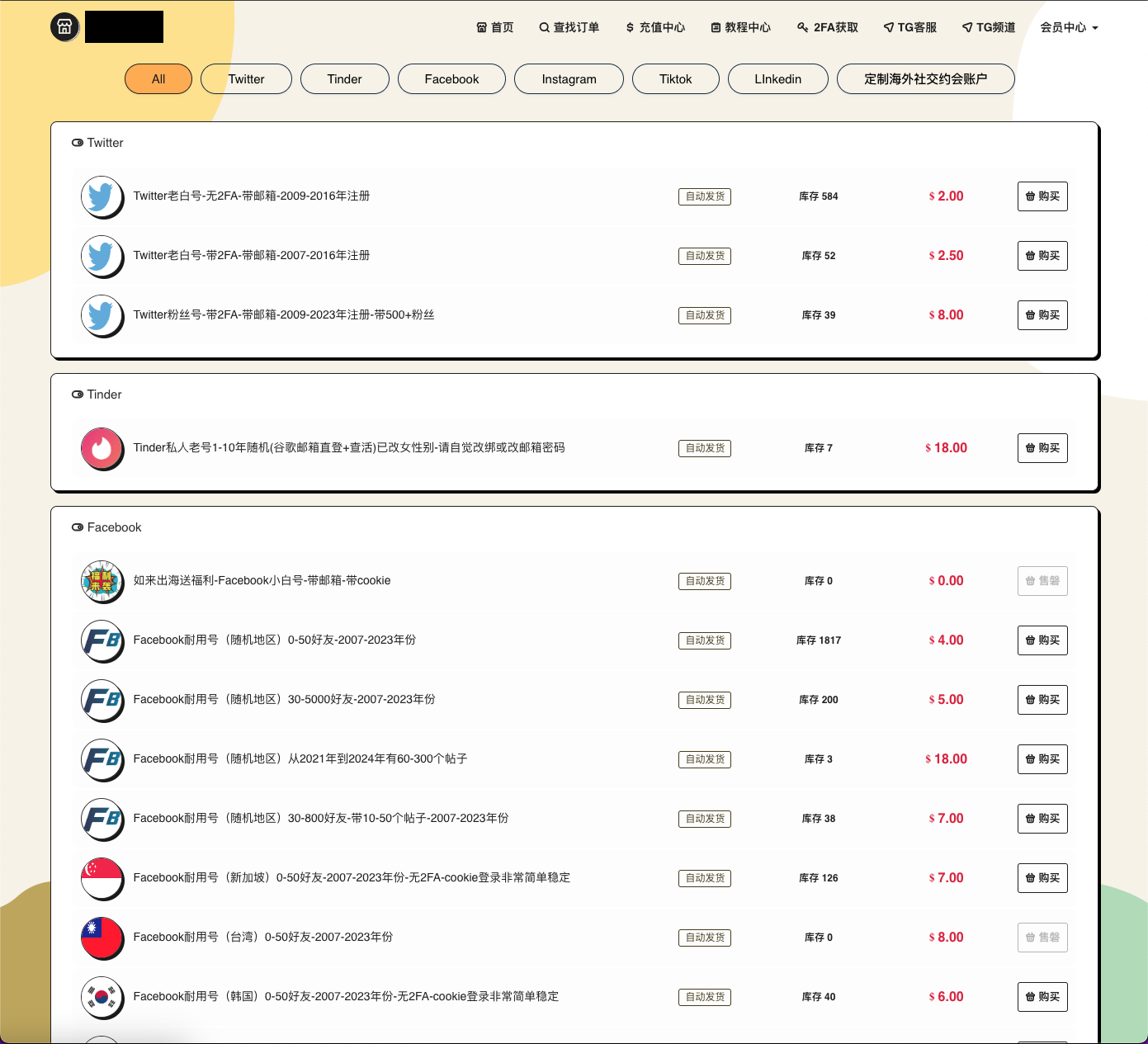
Additionally, it is important to note that scam operations coming out of KK Park and similar compounds are prolific when it comes to adapting their off-chain scam presence, frequently purchasing seasoned Facebook, Tinder, and Match.com profiles from China-based services for use in their campaigns. Below is a graph showing the flow of value from the KK Park scam wallet to a fraud shop that sells illicit products that scammers leverage to devastating effect.
A screenshot from the fraud shop’s website also shows pricing for the social media accounts it sells.
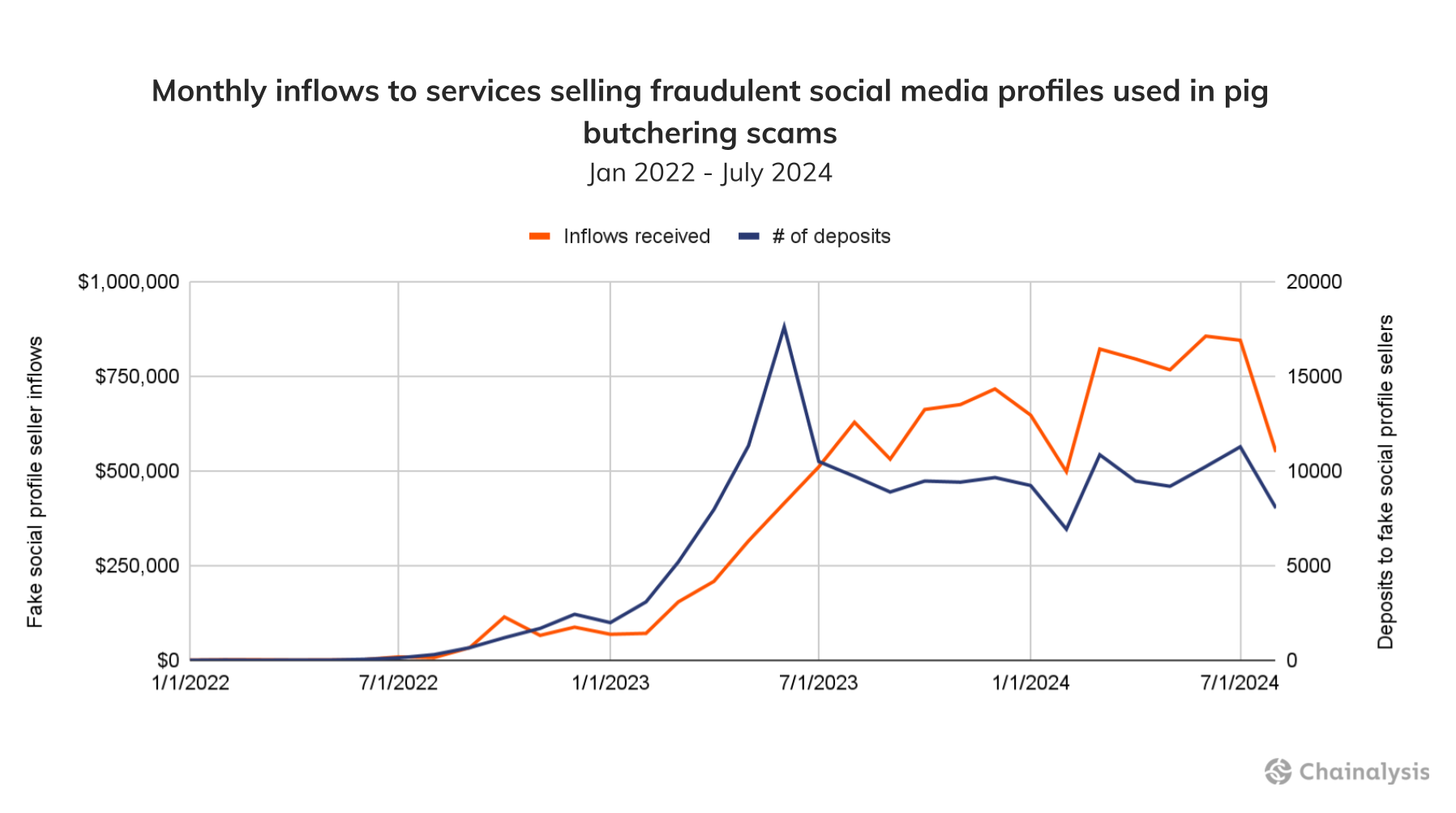
We see more evidence to support this trend by looking at aggregate inflows to services that sell social media accounts like this fraud shop. The chart below shows a steady increase in crypto sent to these services in the last two years, totaling some $10.5M from 2022 to 2024, across 178K deposits. Pricing for social media profiles on these sites can range from anywhere between $5 and $20 per account, implying that scammers may have purchased between 525K and 2.1M social media profiles they could use to target victims.
In addition to sending funds to services that provide scamming tools, scammers eventually need to send their ill-gotten gains to services for laundering and off-ramping into fiat, primarily through centralized exchanges. This year, we’re also seeing a rise in the use of Chinese language marketplaces and laundering networks, including Huione Guarantee.
Huione Guarantee: The $49 Billion Online Marketplace
Huione Guarantee, an online marketplace tied to the Cambodian conglomerate, Huione Group, has recently been exposed as a significant player in facilitating cybercrimes. Our coverage of the service is much larger than previously reported — we identified that the platform has processed more than $49 billion in cryptocurrency transactions since 2021.
Historically, Huione Group has offered legitimate services, operating as a remittance system for overseas transfers, and providing insurance services. At one point, the company also dabbled in the luxury tourism business. However, its platform, Huione Guarantee, appears heavily used for illicit crypto-based activities, including pig butchering, investment fraud, and money laundering. Huione Guarantee has grown into a large and diverse ecosystem that supports the lucrative pig butchering operations that continue to operate in Southeast Asia.
Huione Guarantee operates as a peer-to-peer (P2P) marketplace that connects buyers and sellers, typically by providing Telegram handles of the contact points, thus facilitating these transactions. In total, there are thousands of Telegram groups advertising or posting communications on Huione Guarantee, each run by different independent merchants or affiliates, many of whom likely have ties to criminal enterprises operating within the region.
Huione Guarantee claims to be a neutral party in these transactions; it reportedly operates like an exchange platform that takes a fee for every transaction executed, but does not verify the legitimacy of listed goods and services.
Note: This image has been machine-translated from its original Chinese version.
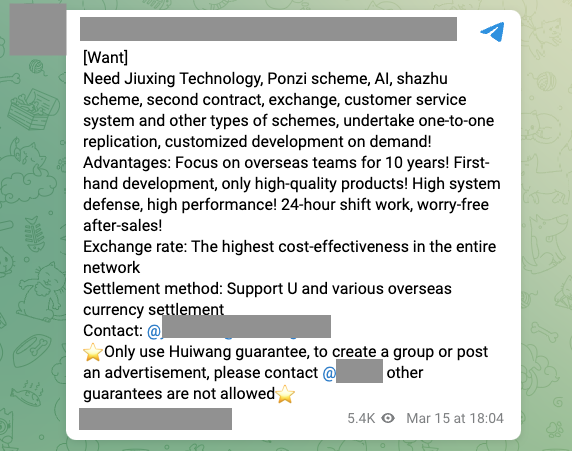
Many merchants on Huione Guarantee put little effort into masking their activities, advertising the types of services they look for using thinly-veiled code words. For example, some advertisements show users who sought “motorcades,” meaning they were looking for money mules to move money through several points and layers, thus obfuscating the source and destination of their funds.
Other postings have advertised the following:
- Offering technology for facial recognition or facial alteration within the “development” section of the platform.
- Orchestrating pig butchering schemes and Ponzi schemes.
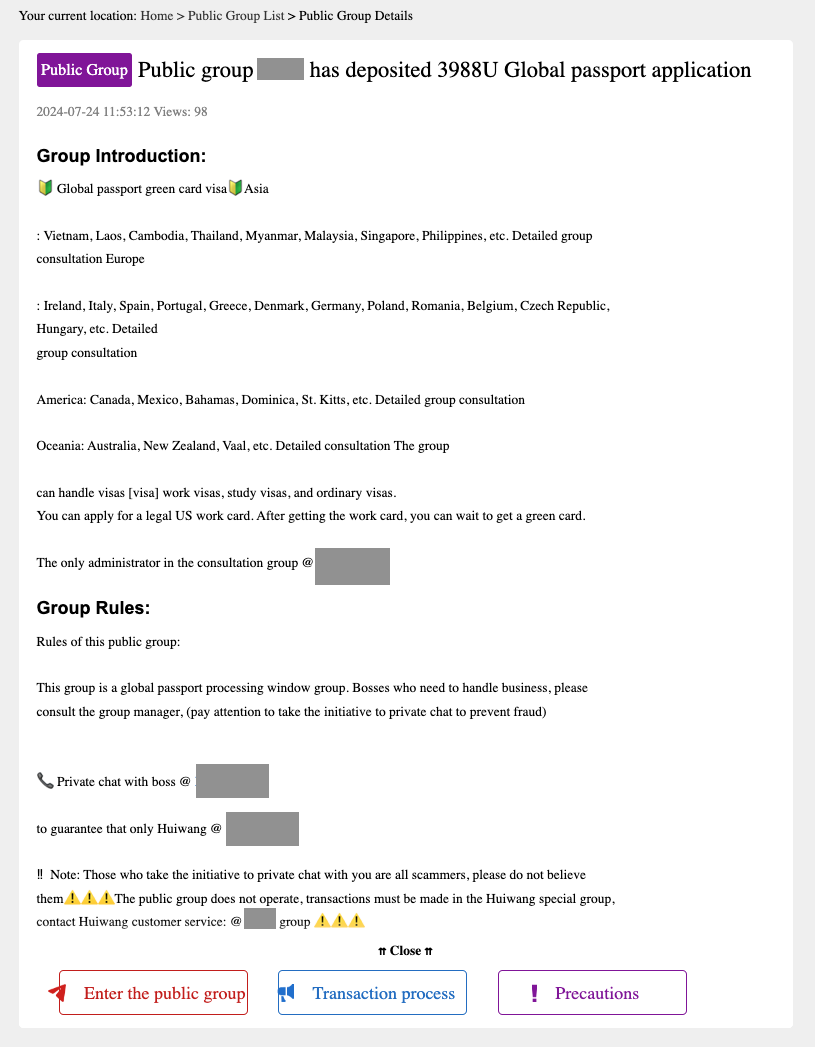
- Providing global passports, visas, and purportedly assisting with applications.
Note: This image has been machine-translated from its original Chinese version. “Shazhu” translates to “pig butchering”.
Note: This image has been machine-translated from its original Chinese version.
Huione Guarantee’s on-chain activities
On-chain analysis reveals that Huione Pay was active on Ethereum, with more than $1.9 billion in total inflows, and on TRON, with more than $47 billion in inflows. In the below graph, we see examples of this activity, with transfers between Huione Pay and a wide array of illicit and risky counterparties, highlighting the expansive Huione facilitation network. The P2P network that Huione appears to support off-chain also maps on-chain; Huione has received and sent funds to all types of counterparties, including scams, addresses reported as stolen funds, the OFAC-sanctioned Russian exchange Garantex, fraud shops, CSAM, Chinese language gambling sites and casinos, and more.
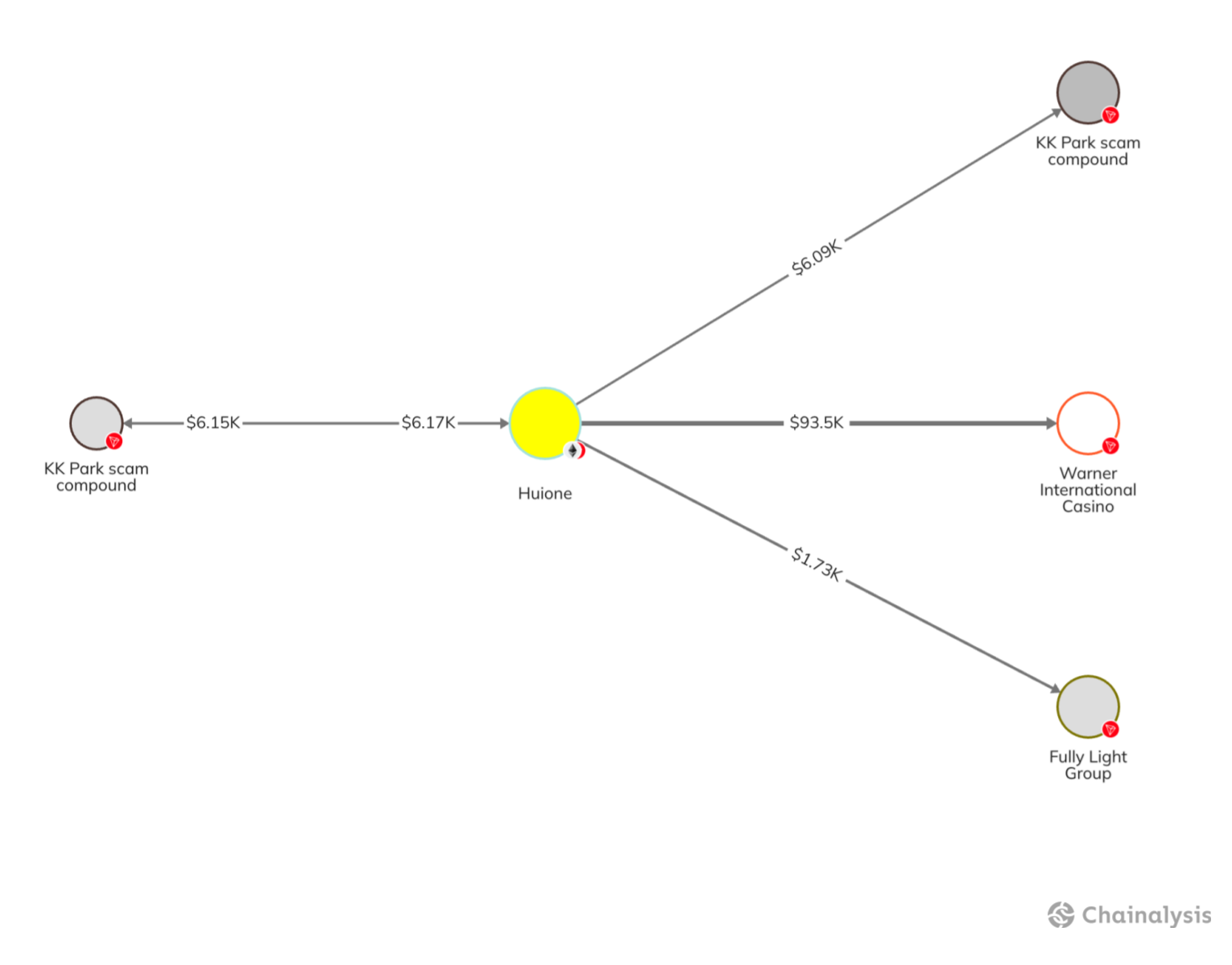
Huione Guarantee has also processed transactions involving wallets reportedly associated with larger crime syndicates, including KK Park. Additionally, Chainalysis has identified wallets related to Fully Light Group and Warner International, entities operated by the Kokang families in Myanmar, who have been reportedly connected to illicit activities including gambling establishments, covert financial networks, and laundering schemes.
These networks’ use of Huione Guarantee showcases that the service has facilitated activity not just with the scammers and fraudsters themselves, but the criminally-affiliated networks behind them.
Huione Guarantee is notable as it serves as a nexus for different kinds of cybercriminal actors, including pig butchering scammers and CSAM networks. While it may be the largest, it is not the only service of its kind. Other networks similarly harness Telegram to facilitate P2P transactions, often for the exchange of illicit goods and services. Chainalysis is closely monitoring this ecosystem in collaboration with our partners to shine a light on this activity.