Key findings
- Aggregate illicit activity on-chain has dropped by almost 20% year-to-date, demonstrating that legitimate activity is growing more quickly than illicit activity.
- Despite the decline in illicit transactions compared to this time last year, two categories of illicit activity — stolen funds and ransomware — are on the rise. Specifically, stolen funds inflows nearly doubled from $857 million to $1.58 billion, while ransomware inflows rose by approximately 2%, from $449.1 million to $459.8 million.
- The average amount of cryptocurrency stolen per heist increased by almost 80%.
- Part of this is attributable to the rise in the price of bitcoin (BTC), which accounted for 40% of the total transaction volume associated with these heists. Crypto thieves also appear to be returning to their roots by targeting centralized exchanges with greater frequency rather than prioritizing DeFi protocols, which are less popular vehicles for trading BTC.
- Advanced cybercriminals, including IT workers linked to North Korea, are increasingly leveraging off-chain methods, such as social engineering, to steal funds by infiltrating crypto-related services.
- 2024 is set to be the highest-grossing year yet for ransomware payments, due in no small part to strains carrying out fewer high-profile attacks, but collecting large payments (known in the industry as “big game hunting”). 2024 has seen the largest ransomware payment ever recorded at approximately $75 million to the Dark Angels ransomware group.
- The median ransom payment to the most severe ransomware strains has spiked from just under $200,000 in early 2023 to $1.5 million in mid-June 2024, suggesting that these strains are prioritizing targeting larger businesses and critical infrastructure providers that may be more likely to pay high ransoms due to their deep pockets and systemic importance.
- The ransomware ecosystem has undergone some fragmentation due to recent law enforcement disruptions of the largest players, such as ALPHV/BlackCat and LockBit. Following these disruptions, some affiliates have migrated to less effective strains or launched their own strains.
2024 has seen a number of positive developments for the cryptocurrency ecosystem. In many ways, crypto has continued to gain mainstream acceptance, following the approval of spot Bitcoin and Ethereum exchange-traded funds (ETFs) in the United States and revisions to the Financial Accounting Standards Board (FASB)’s fair accounting rules. But as with any new technology, adoption will grow among both good and bad actors. And while illicit activity is down year-to-date (YTD) compared to previous years, crypto inflows to specific cybercrime-related entities show some worrying trends.
As depicted in the chart below, so far this year, inflows to legitimate services are the highest they’ve been since 2021, the previous bull market peak. This encouraging sign points to the continued adoption of crypto globally. Inflows to risky services (made up primarily of mixers and exchanges that do not collect KYC information) are trending higher than they were at this point last year. Meanwhile, aggregate illicit activity fell YTD by 19.6%, dropping from $20.9B to $16.7B, demonstrating that legitimate activity is growing faster than illicit activity on-chain. As always, we have to caveat by saying that these illicit figures are lower bound estimates based on inflows to illicit addresses we’ve identified today. Over time, these totals will almost certainly be higher, as we attribute more illicit addresses and incorporate their historic activity into our data.
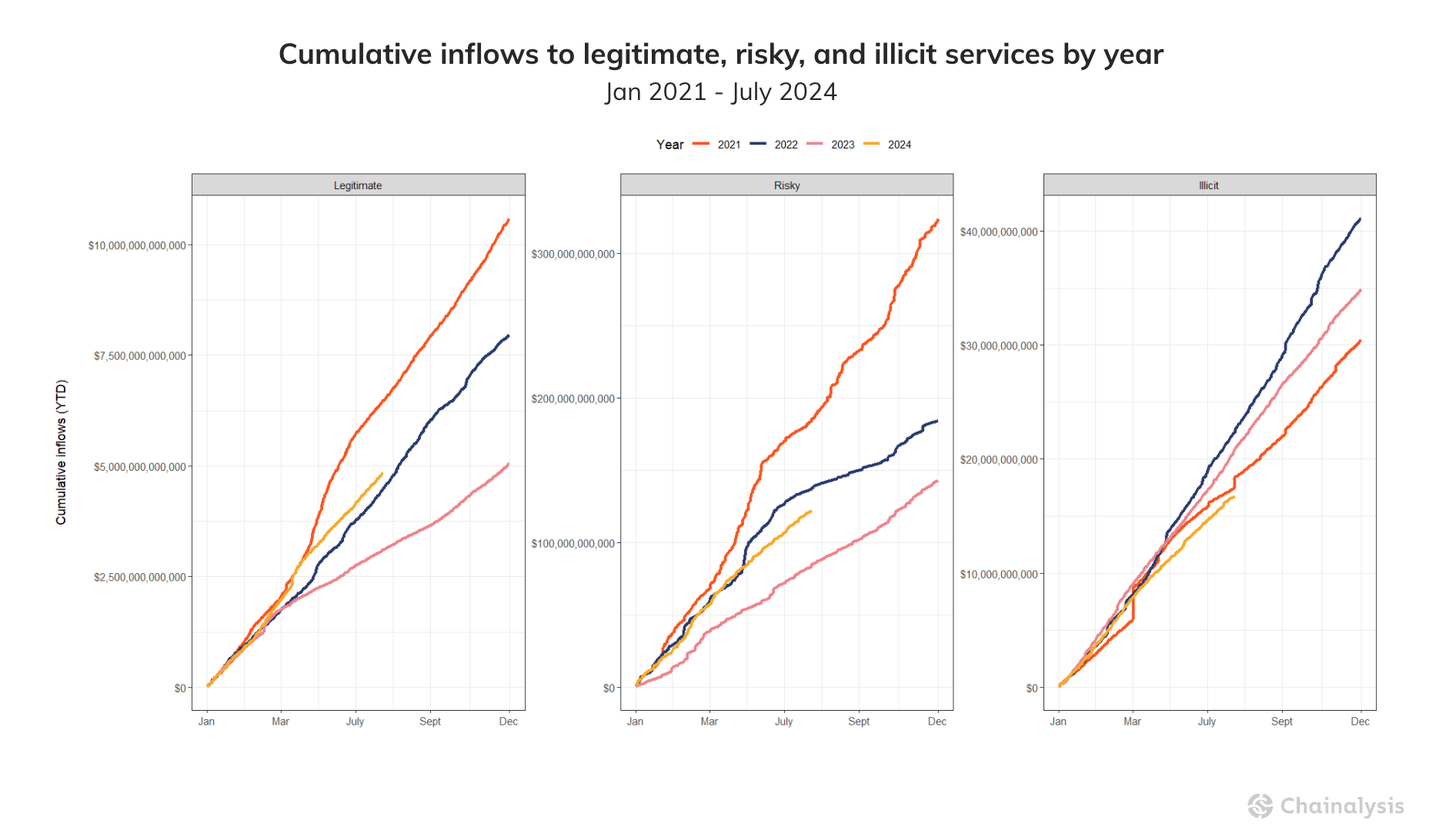
Another important update this year is that we have begun to include suspected illicit activity into our total estimates for certain crime types, based on Chainalysis Signals data. Previously, our estimates only included totals tied to addresses for which Chainalysis had supporting documentation demonstrating that they belong to a certain illicit entity. Signals leverages on-chain data and heuristics to identify the suspected category for a particular unknown address or cluster of addresses, with confidence levels ranging from likely to almost certain. The introduction of Signals not only grows our estimates of certain categories of illicit activity over time, but also enables us to refine previous years’ estimates, given more time has passed to collect inputs and understand on-chain patterns of suspicious activity. As bad actors continue to evolve their tactics, so too will our methods of detecting and disrupting them.
Despite the overall decline in illicit transactions compared to this time last year, two notable types of illicit activity — stolen funds and ransomware — have been on the rise. Funds stolen in crypto heists increased Year-over-Year (YoY), nearly doubling from $857M to $1.58B through the end of July. In last year’s mid-year update, ransomware inflows through June of 2023 totaled $449.1M. This year, ransomware inflows over the same period have topped $459.8M, suggesting we’re potentially looking at another record year for ransomware.
Stolen funds surge as attackers go back to the future and target centralized exchanges
After a 50% drawdown in crypto value stolen in 2023 compared to 2022, this year has seen a resurgence of hacking activity. Comparing both amounts stolen and the number of hacking incidents YoY is telling. As the chart below demonstrates, cumulative value stolen this year through the end of July has already crested $1.58B and is around 84.4% greater than the value stolen over the same period last year. Interestingly, the number of hacking incidents in 2024 has only marginally outpaced that of 2023, rising at just 2.76% YoY. The average amount of value compromised per event has increased by 79.46%, rising from $5.9M per event from January to July of 2023 to $10.6M per event thus far in 2024, based on the value of the assets at the time of theft.

Much of the change in the value compromised is attributable to rising asset prices. For example, the price of bitcoin has increased from an average price of $26,141 in the first seven months of 2023 to an average price of $60,091 this year through July, an increase of 130%.
The price of bitcoin is particularly important here. One hacking measure Chainalysis tracks is the transaction volume associated with the movement of stolen funds after the hack takes place. This can be a proxy for assets stolen because many times hacked services don’t publicly report the breakdown of what was taken. Last year, 30% of this transaction volume was associated with Bitcoin. This year, BTC transaction volume associated with stolen fund activity accounts for 40% of these flows. This pattern seems to be driven by a change in the type of entity being compromised, with centralized services being hacked for high values in 2024. This is particularly the case with centralized exchanges such as DMM, which lost $305M. In the DMM hack, which accounts for roughly 19% of hacked value in 2024, some 4500 BTC was reportedly stolen.
Crypto thieves seem to be returning to their roots and targeting centralized exchanges again after four years focused on their decentralized counterparts, which typically do not trade bitcoin.
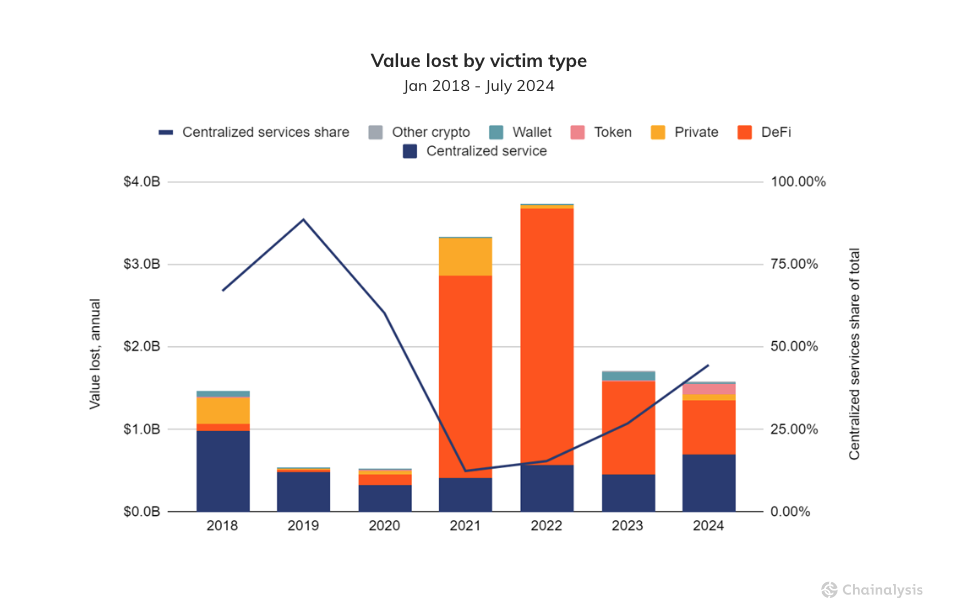
While attacks on DeFi services — and cross-chain bridges in particular — were at their peak in 2022, we speculated that attackers had turned their attention to newer, more vulnerable organizations after centralized exchanges had increased their investments in security. Now attackers, including those linked to North Korea, are leveraging increasingly sophisticated social engineering tactics — including applying for IT jobs — to steal crypto by infiltrating one of their top historical targets in centralized exchanges. The UN recently reported that Western tech industry firms have hired more than 4,000 North Koreans.
2024 on track to be the highest-grossing ransomware year yet
Ransomware set a record in 2023 with over $1B in ransoms paid. These huge volumes came from high-profile, damaging attacks such as the Cl0p exploit of the MoveIT zero-day and the ALPHV/BlackCat ransomware group’s exploit of Caesars’ hotel properties, resulting in the company paying $15 million in ransom. [1] These payments also occurred despite major law enforcement actions targeting ransomware deployer malware and organizational infrastructure. At this point last year, we reported cumulative ransomware payments of around $449.1M through the end of June 2023. This year through the same period, we’ve recorded a total of $459.8M in ransoms paid, setting 2024 firmly on track for the worst year on record.
Andrew Davis, general counsel at Kiva Consulting, says that ransomware activity has held relatively steady despite the disruptions of LockBit and ALPHV/BlackCat. “Whether it be former affiliates of these well-known threat actor operations, or new upstarts, a large number of new ransomware groups have joined the fray, displaying new methods and techniques to carry out their attacks such as expansion in their means for initial access and lateral movement approaches.”
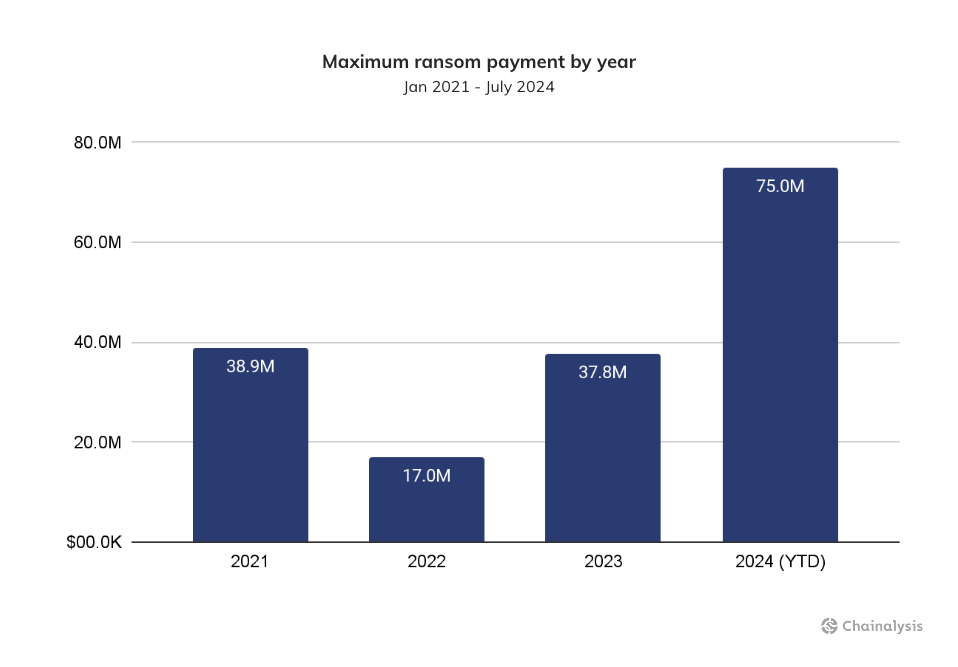
As shown in the chart below, ransomware attacks are also getting demonstrably worse. One remarkable change is the ballooning of the maximum ransom payment that we have observed in a given year. Thus far, 2024 saw the largest single payment ever recorded at approximately $75M to a ransomware group known as Dark Angels. This jump in maximum payment size also represents a 96% YoY growth in the maximum payment from 2023 and a 335% increase from the maximum payment made in 2022.
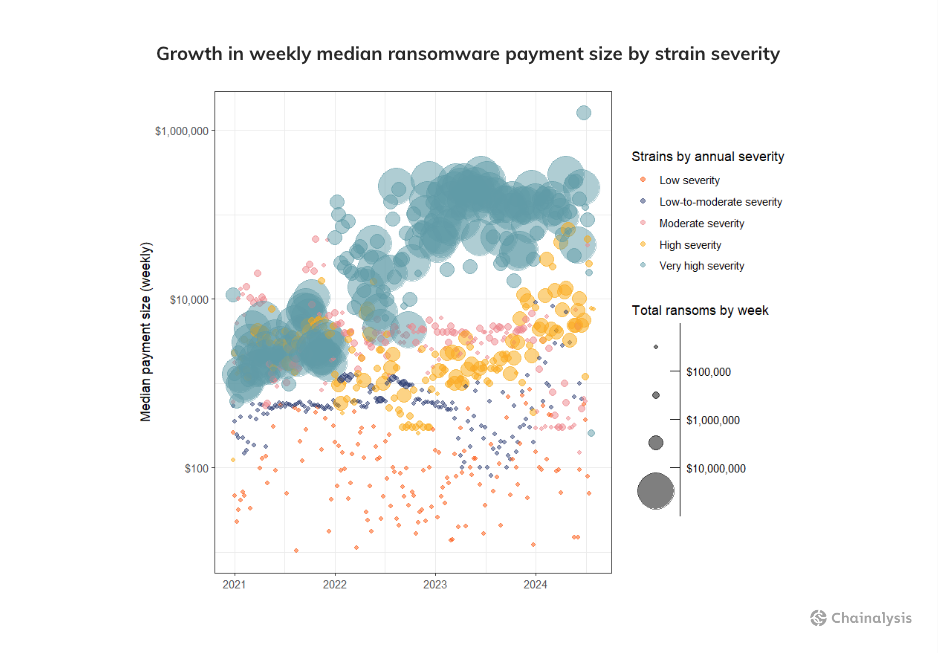
If the rapidly increasing maximum payment amount were not bad enough, it is doubly discouraging that this trend in the outlier value for each year is actually mirrored by a growing trend in the median payment. This trend is especially common among the most-damaging ransomware events. To get at this point, we categorize all strains in the following buckets, based on their on-chain activity levels:
- Very high severity strains: received a maximum payment exceeding $1M in a given year
- High severity strains: received a maximum payment between $100K – $1M in a given year
- Moderate severity strains: received a maximum payment between $10K – $100K in a given year
- Low-to-medium severity strains: received a maximum payment between $1K – $10K in a given year
- Low severity strains: received a maximum payment less than $1K in a given year
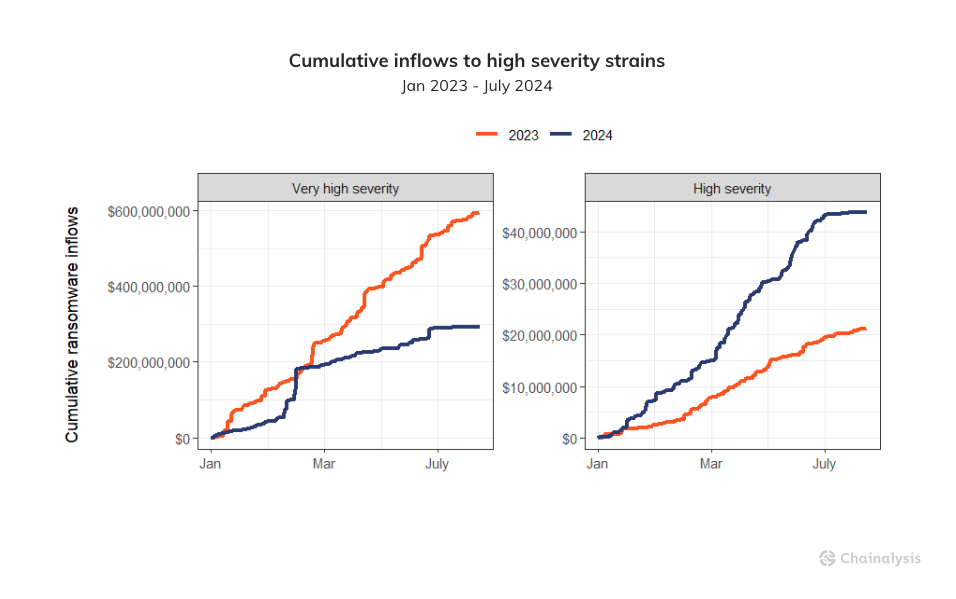
Leveraging this classification system, we can track the extraordinary growth in median payment size by severity over time. The upward trend is particularly evident for “very high severity” strains, which have increased from a median payment size of $198,939 in the first week of 2023 to a median payment of $1.5M in mid June of 2024. This represents an 7.9x increase in the typical size of ransom paid for the most severe strain types during this period, and a nearly 1200x rise since the start of 2021. This pattern could suggest that these strains are starting to target larger businesses and critical infrastructure providers that may be more likely to pay ransoms of inordinate size due to these targets’ deep pockets and systemic importance.
However, the highest severity strains have still underperformed their 2023 YTD totals by 50.8% as seen in the chart below. This could be attributable to law enforcement disruptions of the largest players, ALPHV/BlackCat and LockBit, which halted ransomware operations for a time. In the wake of those disruptions, the ecosystem became more fragmented and affiliates migrated to less effective strains or launched their own. As such, high severity strains increased their YTD activity by 104.8%
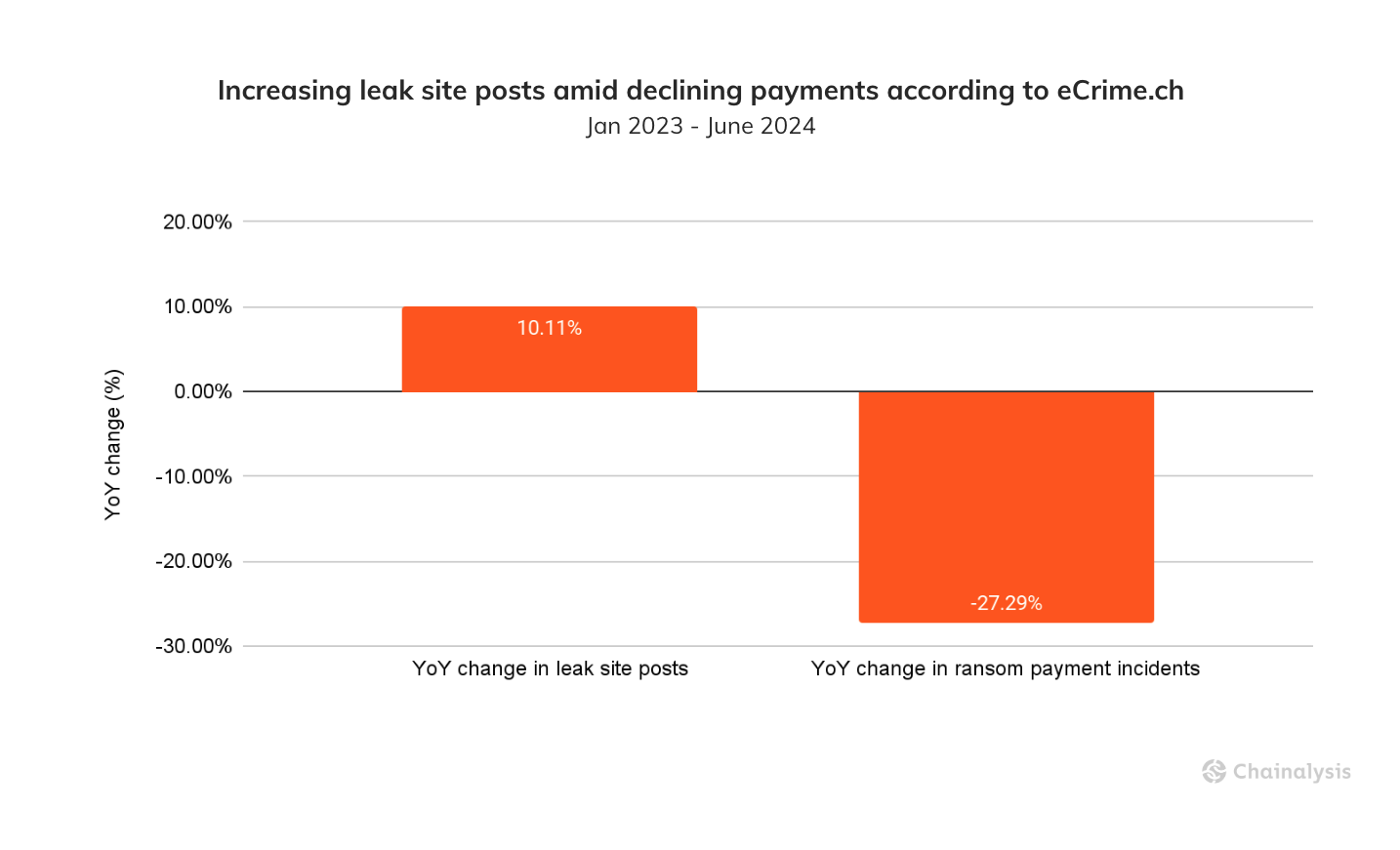
Another trend for ransomware is that attacks are also becoming more frequent with at least 10% more attacks so far this year, according to data leak site statistics from eCrime.ch. Remarkably, despite being on track for a record year in terms of total ransom volumes and already seeing a record-setting maximum ransom size and a worsening attack landscape, there may be a glimmer of good news. Amidst all these headwinds, victims are still paying ransoms less often. Posts to ransomware leak sites as a measure of ransomware incidents have increased YoY by 10%, something we would expect to see if more victims were being compromised. However, total ransomware payment events as measured on-chain have declined YoY by 27.29%. Reading these two trends in tandem suggests that while attacks might be up so far this year, payment rates are down YoY. This is a positive sign for the ecosystem signaling that perhaps victims are better prepared, negating the need to pay.
Davis says, “Approximately 65% of the matters in which Kivu has been engaged in to assist victim organizations have resolved without a resulting payment of the ransom, continuing the positive trend of resiliency on the part of impacted organizations and a lack of necessity to pay the attackers.”
While illicit activity in the crypto ecosystem is continuing to trend downward, two categories of crypto crime appear to be bucking the trend: stolen funds and ransomware. Notably, these two crime types are often perpetrated by actors that share certain characteristics. They’re typically organized groups that leverage sophisticated cyber infrastructure. In the case of stolen funds, North Korean-linked hacking groups are notoriously behind some of the largest heists. These actors are known to employ calculated social engineering tactics to break into crypto businesses, steal crypto assets, and leverage expert money laundering techniques in attempts to cash out before the funds can be seized.
The key to disrupting cybercrime is disrupting its supply chains, including attackers, affiliates, partners, infrastructure services providers, launderers, and cashout points. Because the operations for crypto heists and ransomware operate almost entirely on the blockchain, law enforcement armed with the right solutions can follow the money to better understand and disrupt these actors’ operations. Corsin Camichel, researcher with eCrime.ch, says, “I believe takedowns and law enforcement actions like Operation Cronos, Operation Duck Hunt, and Operation Endgame are essential in curbing these activities and signaling that criminal actions will have consequences.”
End notes
[1] Zero-day attacks are those that exploit unknown security vulnerabilities in computer software, hardware, or firmware. Learn more about Cl0p’s most notorious attack of 2023.

