This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
In our last Crypto Crime Report, we deemed 2020 the “Year of Ransomware” due to the huge growth in cryptocurrency extorted in ransomware attacks. When we first released that report last year, we announced that we had tracked roughly $350 million worth of payments from victims to ransomware operators. However, we explained at the time that this figure was likely an underestimate we would raise in the future due to both underreporting by ransomware victims and our continuing identification of ransomware addresses that have received previous victim payments.
Sure enough, we updated our ransomware numbers a few times throughout 2021, reflecting new payments we hadn’t identified previously. As of January 2022, we’ve now identified just over $692 million in 2020 ransomware payments — nearly double the amount we initially identified at the time of writing last year’s report.
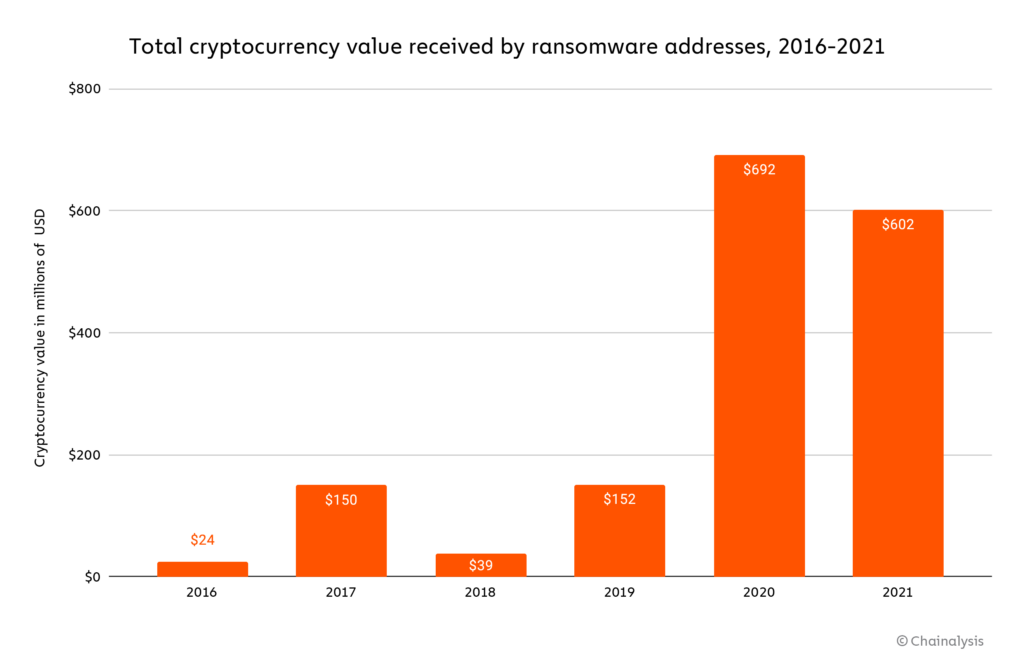
You’ll also see above that as of now, we’ve identified just over $602 million worth of ransomware payments in 2021. However, just like last year, we know that this too is an underestimate, and that the true total for 2021 is likely to be much higher. In fact, despite these numbers, anecdotal evidence, plus the fact that ransomware revenue in the first half of 2021 exceeded that of the first half of 2020, suggests to us that 2021 will eventually be revealed to have been an even bigger year for ransomware. Below, we’ll look more at which ransomware strains were most prolific in 2021, how ransomware operators laundered their funds, and examples of how law enforcement and security agencies are fighting back against ransomware.
2021 ransomware activity summarized
Conti was the biggest ransomware strain by revenue in 2021, extorting at least $180 million from victims.
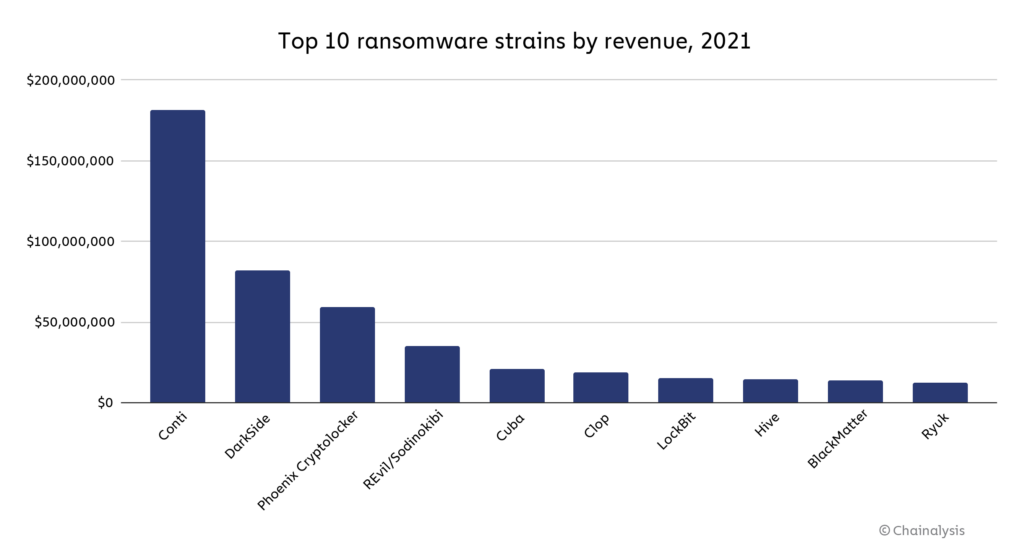
Believed to be based in Russia, Conti operates using the ransomware-as-a-service (RaaS) model, meaning Conti’s operators allow affiliates to launch attacks using its ransomware program in exchange for a fee.
DarkSide is also notable, both for ranking second in 2021 in funds extorted from victims that we’ve been able to identify, and also for its role in the attack on oil pipeline Colonial Pipeline, one of the year’s most notable ransomware attacks. The attack caused fuel shortages in some areas, which were exacerbated by subsequent panic buying as word of the attack’s impact spread. The Colonial story serves as an important reminder of one reason ransomware attacks are so dangerous: They frequently target critical infrastructure we need to keep the country running — not just energy providers, but food providers, schools, hospitals and financial services companies as well.
However, the Colonial Pipeline attack also turned into a success story, as the U.S. Department of Justice was able to track and seize $2.3 million of the ransom that Colonial paid to DarkSide. Law enforcement’s growing ability to seize payments after they’re made represents a huge step forward in the fight against ransomware. It also serves as one more reason why more victims should report attacks — even if you pay, law enforcement may be able to help you get those funds back. You can learn more about how investigators seized cryptocurrency from DarkSide with the aid of Chainalysis tools by reading our case study here.
Overall, 2021 also saw more active individual ransomware strains than any other year.
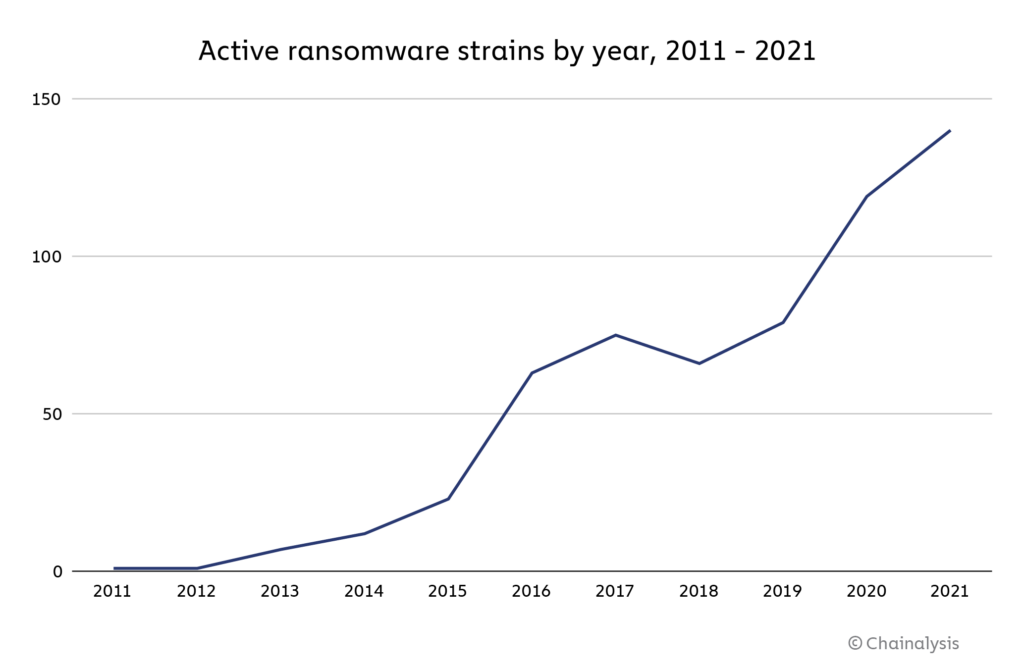
At least 140 ransomware strains received payments from victims at any point in 2021, compared to 119 in 2020, and 79 in 2019. Those numbers are emblematic of the intense growth of ransomware we’ve seen over the last two years. Most ransomware strains come and go in waves, staying active for a short amount of time before becoming dormant. We show this on the graph below, which shows how the top ten ransomware strains ebbed and flowed in activity throughout the year.
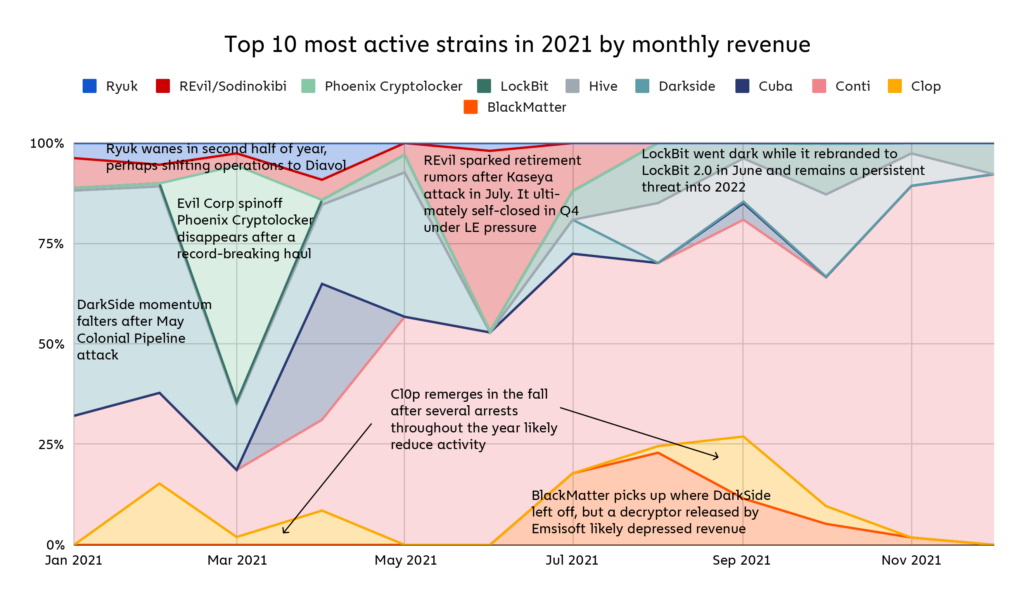
Conti was the one strain that remained consistently active for all of 2021, and in fact saw its share of all ransomware revenue grow throughout the year. Overall though, Conti’s staying power is increasingly outside the norm.
As we’ll explore more later on, the growing number of active strains and generally short lifespan of most strains is also a result of rebranding efforts. More and more in 2021, we’ve seen the operators of strains publicly “shut down” before re-launching under a new name, presenting themselves as a separate cybercriminal group. Often, the rebranded strain’s financial footprint on the blockchain aligns with that of the original, which can tip investigators off as to who’s really behind the new strain.
Ransomware payment sizes also continued to grow in 2021, a trend we’ve observed every year since 2018.
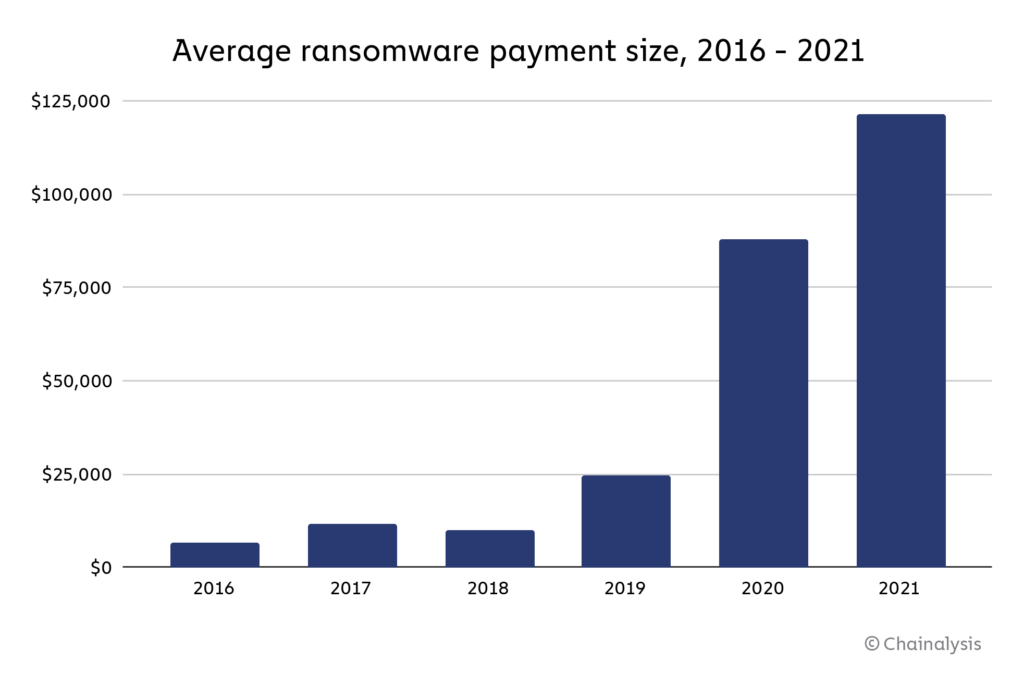
The average ransomware payment size was over $118,000 in 2021, up from $88,000 in 2020 and $25,000 in 2019. Large payments such as the record $40 million received by Phoenix Cryptolocker spurred this all-time high in average payment size. One reason for the increase in ransom sizes is ransomware attackers’ focus on carrying out highly-targeted attacks against large organizations. This “big game hunting” strategy is enabled in part by ransomware attackers’ usage of tools provided by third-party providers to make their attacks more effective. These tools range from illicit hacking aids to legitimate products, and include:
- Rented infrastructure such as bulletproof web hosting, domain registration services, botnets, proxy services, and email services to carry out attacks.
- Hacking tools like network access to already-infiltrated networks, exploit kits that scan victims’ networks for vulnerabilities, and malware programs that help attackers distribute ransomware more effectively.
- Stolen data such as passwords, individuals’ personally identifiable information, and compromised remote desktop protocol (RDP) credentials, which help attackers break into victims’ computer networks.
Usage of these services by ransomware operators spiked to its highest ever levels in 2021.
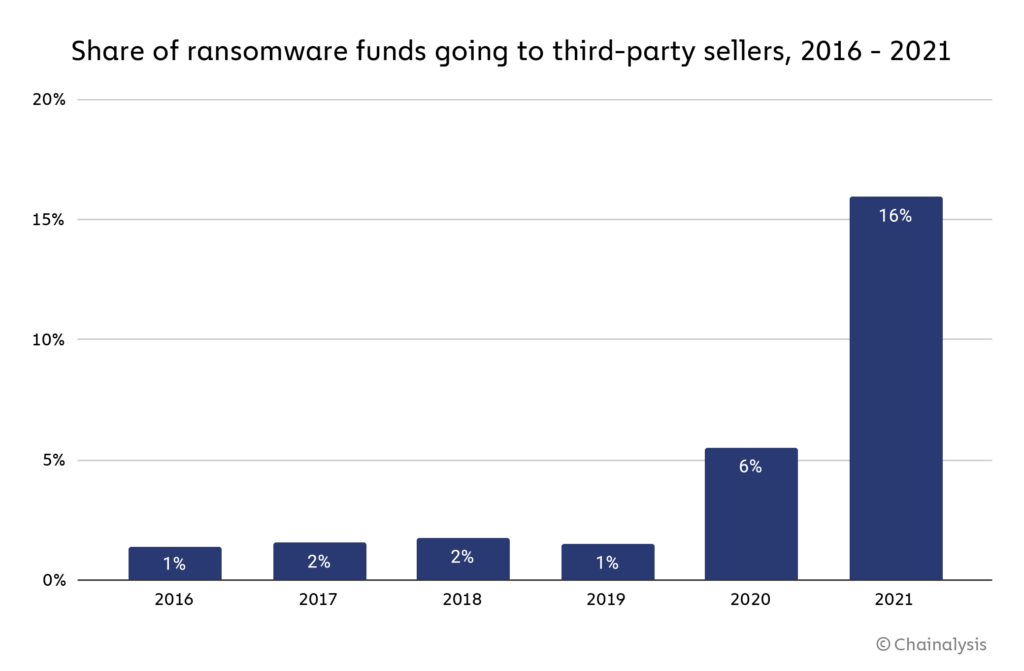
16% of all funds sent by ransomware operators were spent on tools and services used to enable more effective attacks, compared to 6% in 2020. While it’s possible some of that activity constitutes money laundering rather than the purchase of illicit services, we believe that increasing use of those services is one reason ransomware attackers became more effective in 2021, as evidenced by rising average victim payment sizes.
Another important trend to monitor in ransomware is money laundering. The graph below shows where attackers move the cryptocurrency they extort from victims.
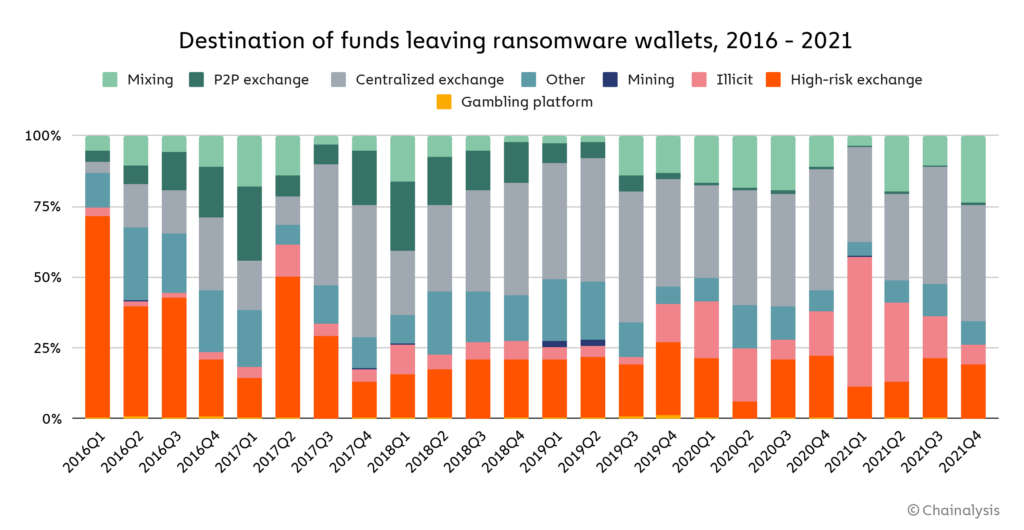
Over the last few years, most ransomware strains have laundered their stolen funds by sending them to centralized exchanges. Some are in the high-risk category, meaning that they tend to have relaxed compliance procedures, but mostly to mainstream exchanges with more established compliance programs. We also see substantial funds sent to both mixers and addresses associated with other forms of illicit activity.
The money laundering trends get even more interesting if we drill down to the individual services receiving funds from ransomware.
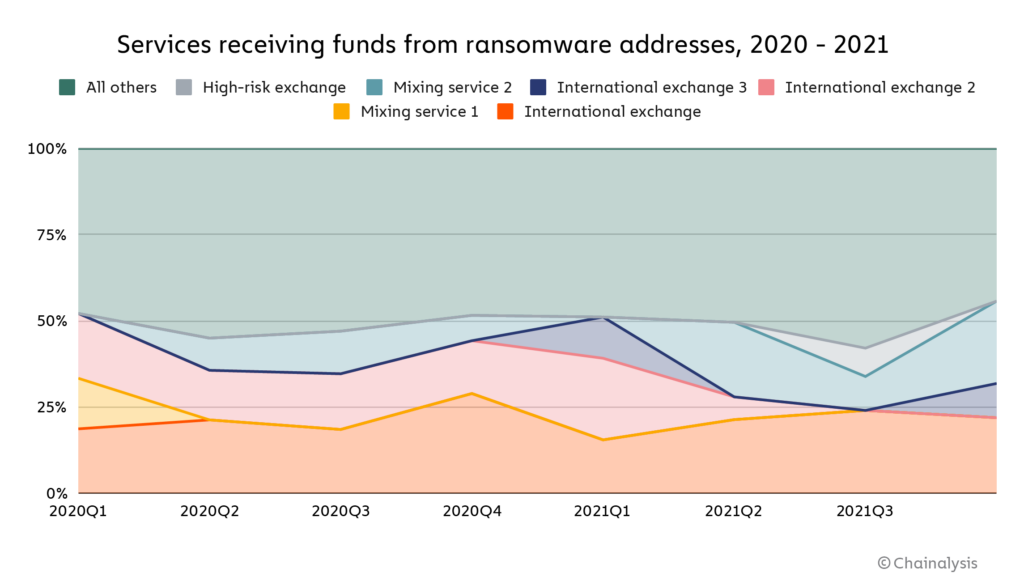
Amazingly, 56% of funds sent from ransomware addresses since 2020 have wound up at one of six cryptocurrency businesses:
- Three large, international exchanges
- One high-risk exchange based in Russia
- Two mixing services
Similar to the rebranding activity we described above, these money laundering trends show how small the ransomware ecosystem really is. That’s good news, as it means the strategy for fighting ransomware is likely simpler than it appears at first glance. By cracking down on the small number of services that facilitate this money laundering activity, law enforcement can significantly reduce attackers’ options for cashing out, reducing the financial incentive to carry out ransomware attacks and hampering ransomware organizations’ ability to operate.
2021’s rebranding craze shows the ransomware ecosystem is smaller than we think
As we discussed above, most ransomware strains aren’t active for very long. While this has always been the case to some degree, the trend has become even more pronounced in 2021.
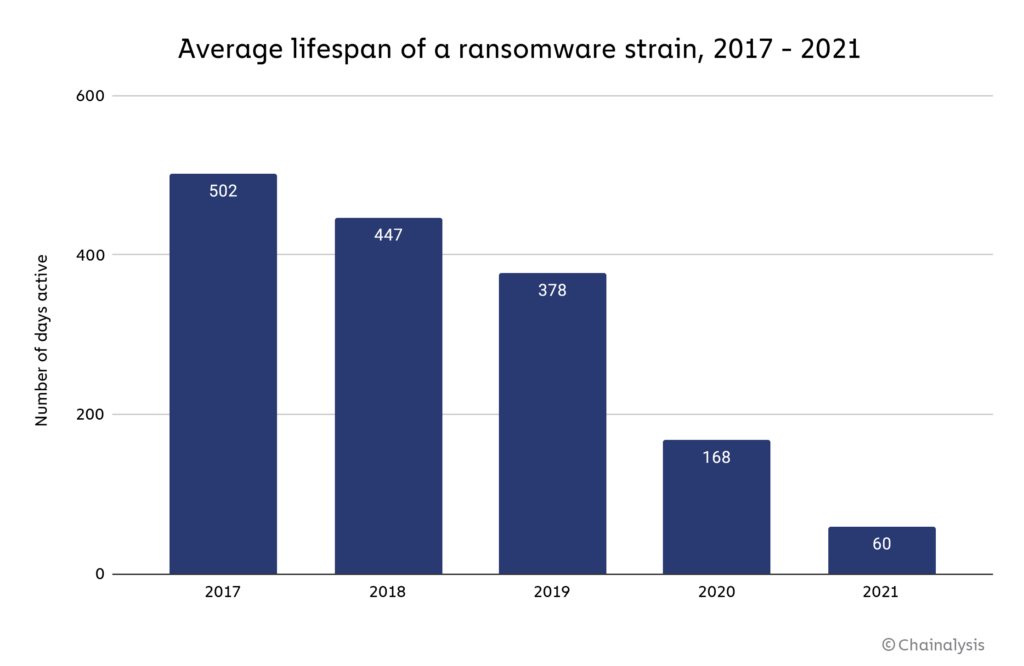
Two years ago, the average ransomware strain remained active for exactly one year. In 2021, the average strain is active for no more than two months. Why is the average ransomware lifespan dropping so quickly?
One big reason is rebranding. More than ever in 2021, cybersecurity researchers have noted instances of ransomware attackers publicly claiming to cease operations, only to relaunch later under a new name — the giveaway is usually similarities in the ransomware’s code, as well as intelligence gathered from cybercriminal forums and blockchain analysis. So, while at least 140 ransomware strains were active at 2021, many of those strains were in fact run by the same cybercriminal groups.
These strains attempt to create the illusion that they belong to different cybercriminal organizations by setting up separate victim payment sites and other infrastructure, but share similarities in their code. Evil Corp, a Russia-based cybercriminal gang behind several ransomware attacks in recent years, has launched several rebranded strains throughout its history, including:
- Doppelpaymer
- Bitpaymer
- WastedLocker
- Hades
- Phoenix Cryptolocker. This strain is notable for “shutting down” after one attack that extorted $40 million — the largest known ransom ever paid.
- Grief. Grief exhibits code similarities to Doppelpaymer ransomware, including the telltale use of Dridex malware. As of 2021, Grief is notable for demanding ransomware payments in Monero.
- Macaw. Interestingly, Macaw uses a completely different negotiation method than previous Evil Corp strains. In this way, Macaw could be described less as a “rebrand” of an old strain and more as a unique strain launched by an existing ransomware organization.
- PayloadBIN. Many cybersecurity analysts have reported that Evil Corp’s launch of the PayloadBIN strain is intended to look like a rebrand of an old strain used by another ransomware group, making PayloadBIN a double rebrand of sorts.
We can also see evidence of some of these strains’ common ownership in their cryptocurrency transaction histories. Check out the Chainalysis Reactor graph below.
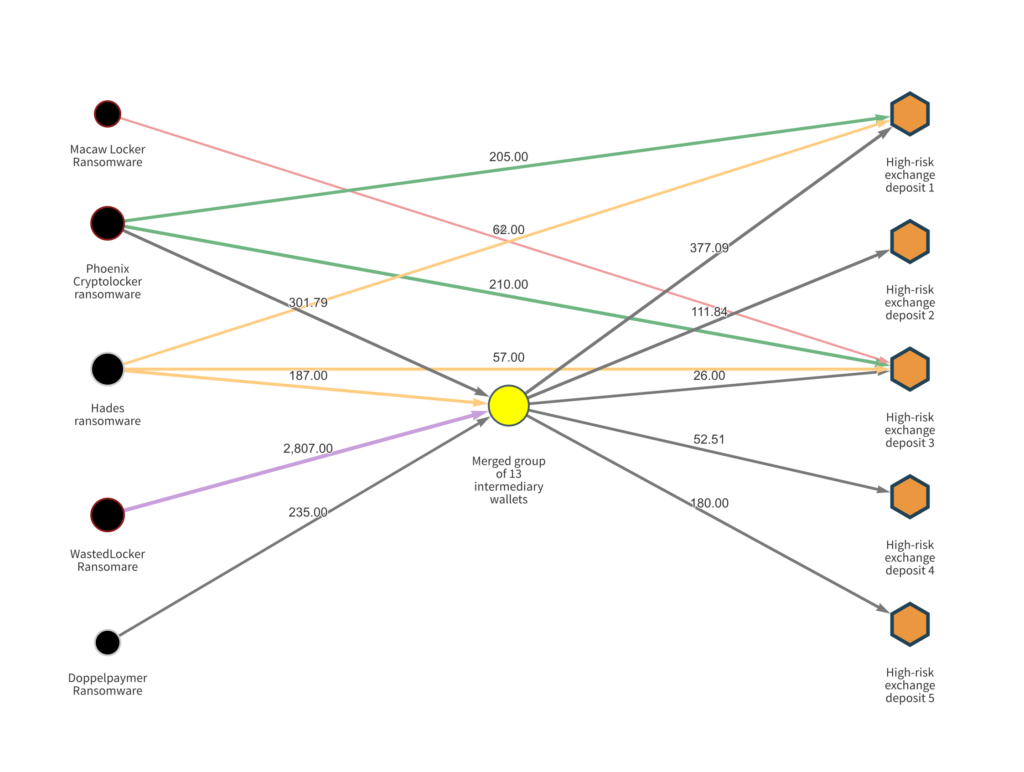
This graph shows the money laundering process for five of the Evil Corp ransomware strains we mentioned above. While all of them appear to be run by separate organizations, most send funds derived from attacks to the same group of intermediary wallets, and from there move funds to many of the same deposit addresses at high-risk exchanges.
But why does Evil Corp rebrand its ransomware strains so often? Most analysts believe it’s an effort to evade sanctions. Evil Corp, whose leaders are suspected to have ties to the Russian government, has been sanctioned by the United States since December 2019. In October 2020, the U.S. Treasury’s Office of Foreign Asset Control (OFAC) reiterated guidance that ransomware victims who pay ransoms to sanctioned groups could face penalties. This put Evil Corp in a bad position, as it meant that many victims and their representatives would likely be reluctant to pay them following due diligence on the sanctions risk. By rebranding, Evil Corp likely believes it can fool victims into paying before researchers can discover the potential sanctions risk.
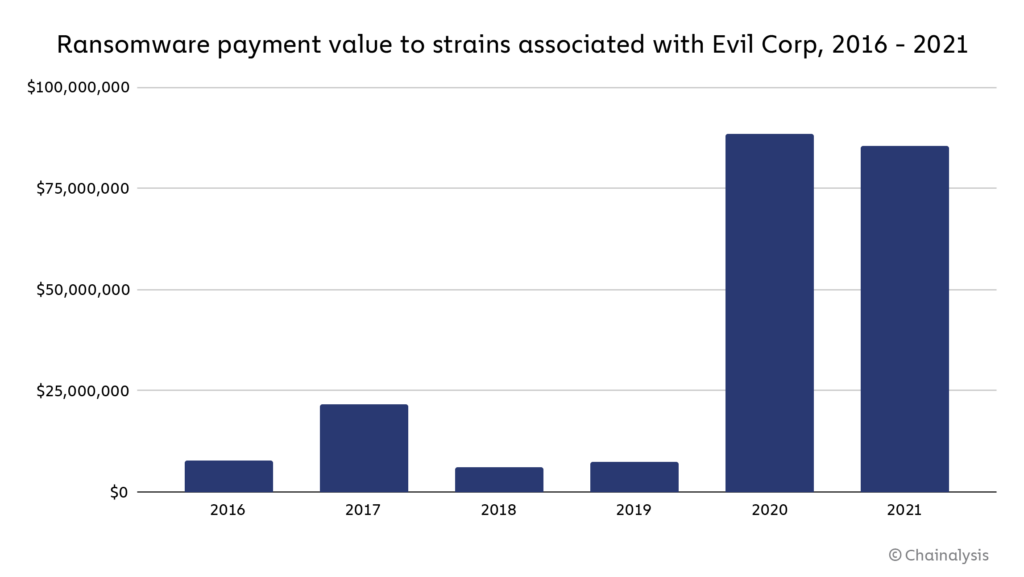
Unfortunately, rebranding appears to have worked for Evil Corp in many cases, as victims paid at least $85 million in ransoms to strains associated with the organization.
 Of course, Evil Corp isn’t the only organization rebranding its ransomware strains. In July 2021, the group behind the DarkSide ransomware strain began launching attacks with a very similar strain called BlackMatter. This came following DarkSide’s attack on Colonial Pipeline and the FBI’s subsequent seizing of most of that ransom, and it’s our belief that the rebrand came in response to pressure from law enforcement. One piece of evidence supporting this is BlackMatter’s stated unwillingness to attack oil and gas companies, which would make sense for a rebranded DarkSide considering the law enforcement action brought on by their attack on Colonial. We should also note that the DarkSide group appears to have since abandoned their commitment to avoid oil and gas companies. In late January 2022, a ransomware strain known as Black Cat (also known as “Alphv”), which many believe is DarkSide’s latest rebrand, attacked two German oil and gas companies, Mabanaft GmbH and Oiltanking GmbH Group.
Of course, Evil Corp isn’t the only organization rebranding its ransomware strains. In July 2021, the group behind the DarkSide ransomware strain began launching attacks with a very similar strain called BlackMatter. This came following DarkSide’s attack on Colonial Pipeline and the FBI’s subsequent seizing of most of that ransom, and it’s our belief that the rebrand came in response to pressure from law enforcement. One piece of evidence supporting this is BlackMatter’s stated unwillingness to attack oil and gas companies, which would make sense for a rebranded DarkSide considering the law enforcement action brought on by their attack on Colonial. We should also note that the DarkSide group appears to have since abandoned their commitment to avoid oil and gas companies. In late January 2022, a ransomware strain known as Black Cat (also known as “Alphv”), which many believe is DarkSide’s latest rebrand, attacked two German oil and gas companies, Mabanaft GmbH and Oiltanking GmbH Group.
The uptick in ransomware rebranding is an important reminder that the ransomware ecosystem is smaller than it appears at first glance. While new strains pop up all the time, many of them are ultimately run or deployed by the same groups and individuals, all of whom are likely feeling the pressure from law enforcement’s increasing efforts to prevent attacks, seize extorted funds, and arrest the individuals responsible. Rebranding is one way of evading those efforts, and suggests that investigators and cybersecurity professionals may be best served by studying ransomware attackers at the organizational level, and focusing less on the unique strains.
Ransomware as a geopolitical weapon
Most ransomware attacks appear to be financially motivated. However, others appear to be motivated by geopolitical goals, and seem more geared toward deception, espionage, reputational damage and disruption of the enemy government’s operations.
In cases where a ransomware strain contains no mechanism to collect payment or allow victims to recover their files, we can be more certain that money isn’t the attackers’ primary motivation. And that’s exactly what we saw in a recent ransomware attack on Ukrainian government agencies by hackers believed to be associated with the Russian government.
As the Computer Emergency Response Team of Ukraine (CERT-UA) describes here, the attack occurred on the night of January 13, 2022, and disrupted several government agencies’ ability to operate. The attack came against a backdrop of increasing tensions between the two countries, with Russian troop build-ups along the Ukrainian border causing concern that an invasion could be imminent. We saw a similar situation unfold in 2017, when tensions between the two nations were also running high. At that time, the Russia-based NotPetya ransomware strain, which contained no viable payment mechanism, targeted several Ukrainian organizations and was also widely judged to be a geopolitically motivated disruption attempt by the Russian military rather than a money-making effort.
Microsoft Security published its own analysis of the recent attack, noting that the ransomware strain in question — dubbed DEV-0586 or more commonly known as WhisperGate— has no way of returning victims’ access to their files. Microsoft Security’s blog also includes the message the ransomware group displayed to its Ukrainian victims.
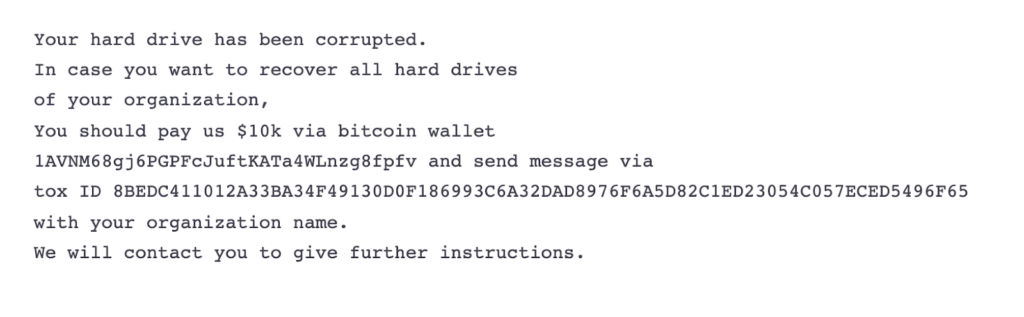
Credit: Microsoft Security Blog
DEV-0586’s address doesn’t have an extensive transaction history for us to draw from. But further analysis of the ransomware’s technical characteristics indicates even more geopolitical gamesmanship. On January 26, CERT-UA released a report showing that DEV-0586 contains code repurposed from WhiteBlackCrypt, a ransomware strain active in 2021 that, like DEV-0586, is designed to wipe victims’ systems rather than extort them for money. But there’s a twist: WhiteBlackCrypt targeted Russian organizations rather than Ukrainian ones. Cybersecurity analysts believe DEV-0586’s reuse of code previously used by WhiteBlackCrypt, as well as the presence of other similarities linking the two strains, is a gambit by Russian hackers to make DEV-0586 appear to be of Ukrainian rather than Russian origin — in other words, a false flag attack. The gambit shows how far state actors using ransomware to attack foes will go to conceal their attacks’ origins and maintain plausible deniability. We’ll continue to monitor DEV-0586’s address for more activity and provide updates when possible.
Russia-affiliated attackers aren’t the only ones using ransomware for geopolitical ends. Cybersecurity analysts at Crowdstrike and Microsoft have concluded that many attacks by ransomware strains affiliated with Iran, mostly targeting organizations in the U.S., the E.U., and Israel, are geared more toward causing disruption or serving as a ruse to conceal espionage activity. Generally speaking, Chainalysis has seen significant growth over the last year in the number of ransomware strains attributed to Iranian cybercriminals in the past year — in fact, Iran accounts for more individual identified strains than any other country.
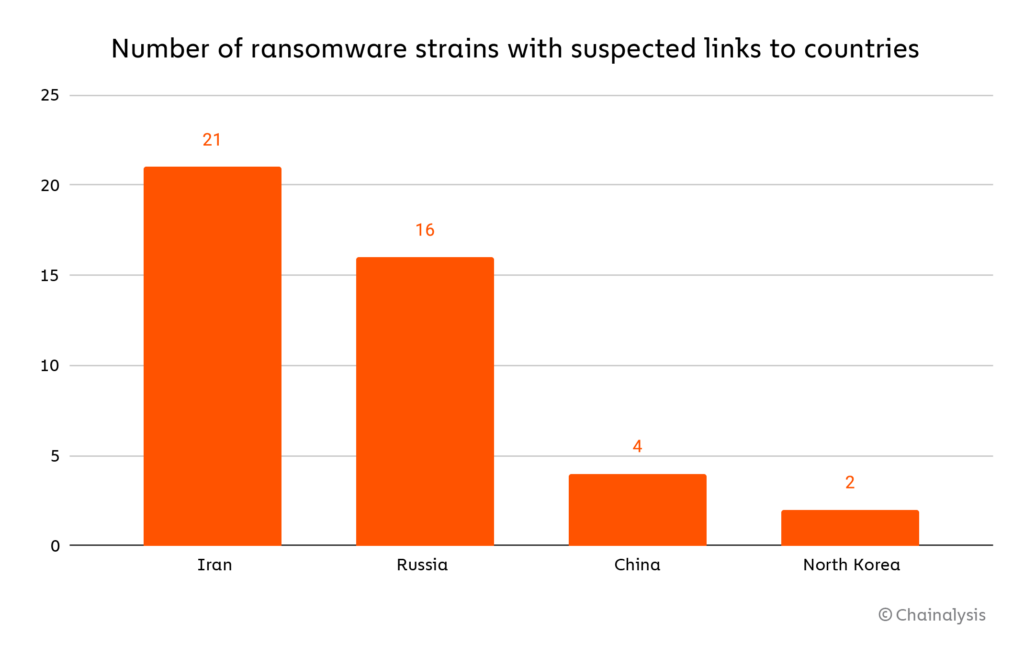
To be clear, many of those Iranian ransomware strains are used for conventional, financially motivated attacks by cybercriminals operating in the country. Iran has a highly educated population but limited occupational opportunities, which likely contributes to the allure of ransomware. However, other strains behave more like tools of espionage, extorting negligible amounts of cryptocurrency from victims. Other analysts have previously identified instances of strains affiliated with China, such as ColdLock, carrying out similar geopolitical attacks on Taiwanese organizations.
Ransomware is a useful cover for strategic denial and deception against enemy states because attacks can be carried out cheaply, and it gives the attacking nation some measure of plausible deniability, as they can always claim the attack was carried out by mere cybercriminals or another nation state. But even ransomware attacks carried out for non-financial reasons leave a trail on the blockchain. For that reason, it’s crucial that agencies focused on national security understand how to trace funds using blockchain analysis, as this is the key to identifying the individuals involved in the attacks themselves, the tools they use, and how they launder any funds obtained from victims.
What’s next for ransomware?
Ransomware isn’t just dangerous. It’s also one of the most dynamic, constantly changing forms of cryptocurrency-based crime. Between constant rebrands, shifting money laundering strategies, and the influence of geopolitics, it’s hard to know what’s coming next. One trend to look out for though is Monero ransoms. Analysts have noted that more and more attackers are demanding victims pay in Monero, likely due to the heightened anonymity it offers. While the vast majority of attackers continue to demand Bitcoin, law enforcement and cybersecurity professionals should keep an eye out for ransom notes requesting Monero or assets associated with other protocols with privacy-enhancing features, as this will change the investigative tactics they must employ.
There’s only one thing that’s certain in ransomware: Law enforcement will continue to investigate the cybercriminals responsible, and Chainalysis software and services will be there to help them every step of the way. Events like the seizure of funds from DarkSide show that we’re making progress, and we look forward to keeping up the fight in 2022.
This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making investment decisions.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
