On April 17, 2024, London’s Metropolitan Police announced the disruption of LabHost, a notorious phishing-as-a-service (PhaaS) provider that enabled cybercriminals to breach the bank accounts of victims around the world, following an operation conducted in tandem with international law enforcement and industry partners. Active since 2021, LabHost is believed to have enabled thousands of phishing attacks, which means that this successful law enforcement operation has made the internet a safer place.
LabHost charged cybercriminals a monthly fee for access to their phishing tools, and accepted cryptocurrency for payment. As such, we can analyze LabHost’s on-chain activity. Keep reading for that analysis, as well as a primer on LabHost’s operations and role in cybercrime.
What is LabHost?
LabHost is a PhaaS provider that sells “phishing kits,” which cybercriminals use to build fake web pages imitating those of banks. These fake sites are designed to trick the banks’ customers into entering their login information for the cybercriminals to steal. According to Bleeping Computer, LabHost has also provided web hosting infrastructure to keep phishing pages online, email campaign tools for targeting victims with spam driving them to the phishing pages, and even tools for circumventing two-factor authentication.
LabHost charged a monthly fee for these tools, with varied offerings at different pricing tiers.
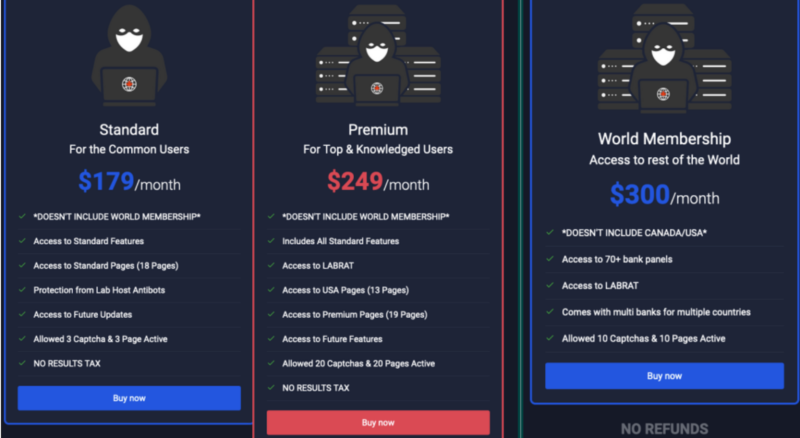
LabHost’s pricing plans via Bleeping Computer.
LabHost’s popularity grew in 2023 when it rolled out high-powered phishing kits for Canadian banks specifically. However, its tools enabled cybercriminals to target bank customers all over the world, as well as users of shipping services and apps like Spotify. According to the Metropolitan Police’s press release on this operation, cybercriminals used LabHost to spin up more than 40,000 phishing sites, and the service boasted more than 2,000 registered users. The agency also says that cybercriminals using LabHost have stolen over 480,000 credit card numbers, 64,000 PIN numbers, and over 1 million passwords for various online services.
LabHost’s on-chain activity and use of cryptocurrency
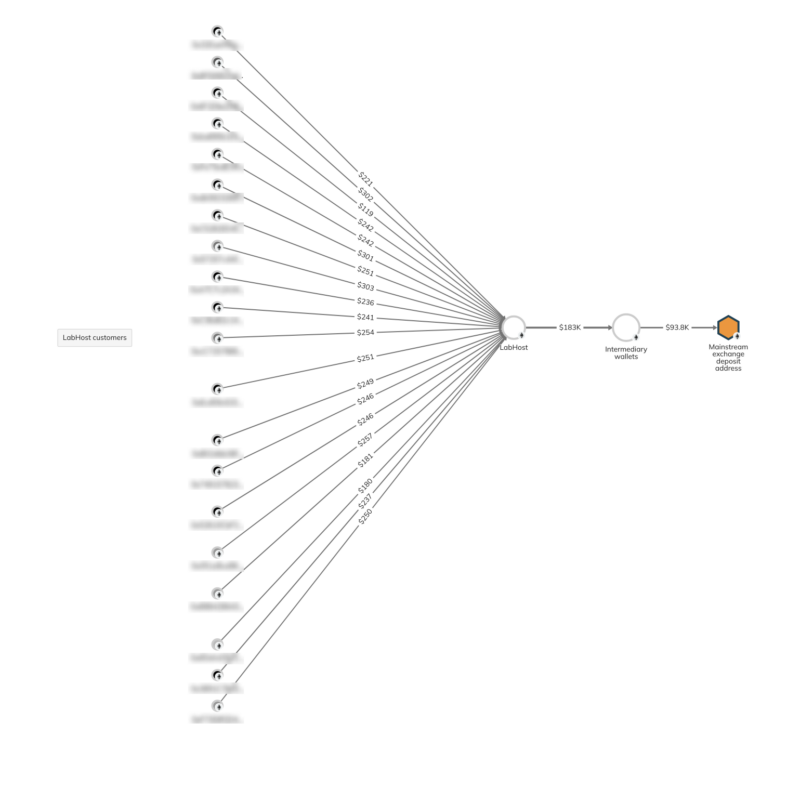
Since becoming active in August 2021, LabHost’s identified cryptocurrency wallets have received over $1.1 million worth of cryptocurrency across thousands of transfers, with payments coming in Bitcoin, Etherum, Litecoin, and Monero. LabHost’s incoming payments in Bitcoin specifically are visible on the Chainalysis Investigations graph below. We can assume that most of that represents cybercriminals paying their monthly fee for the use of LabHost’s phishing tools.
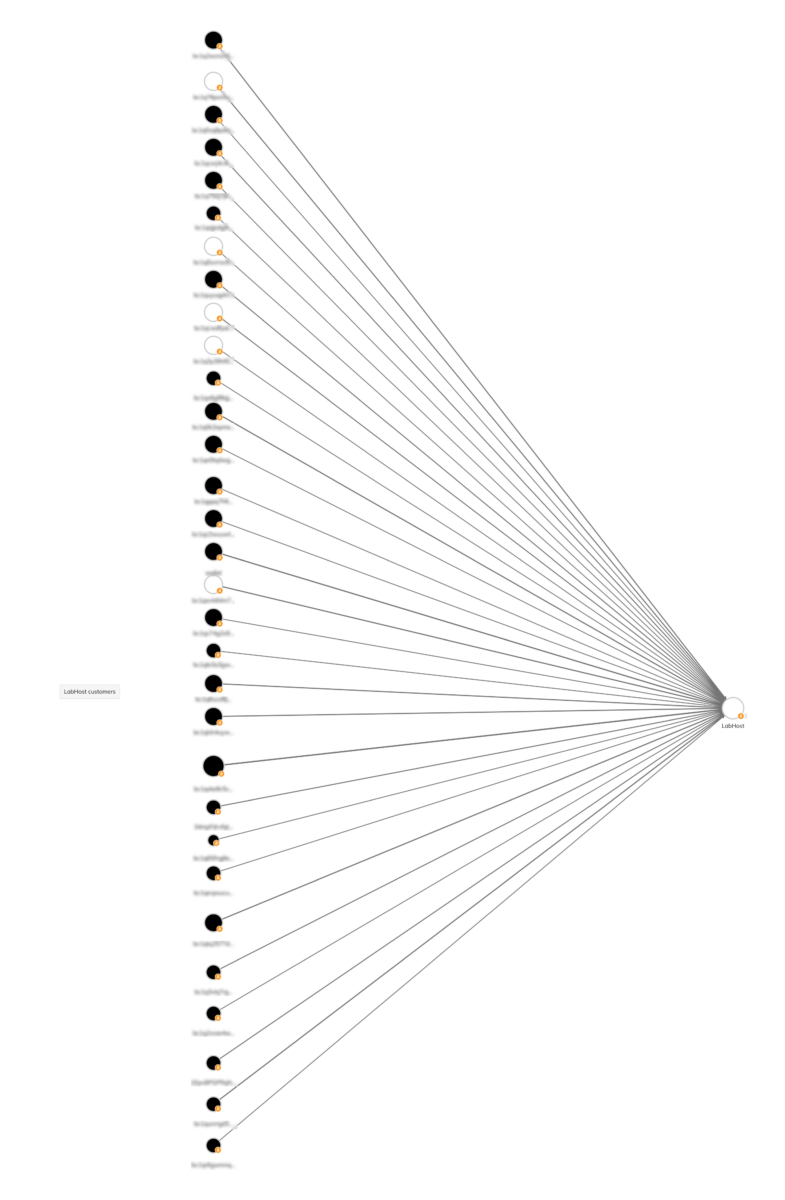
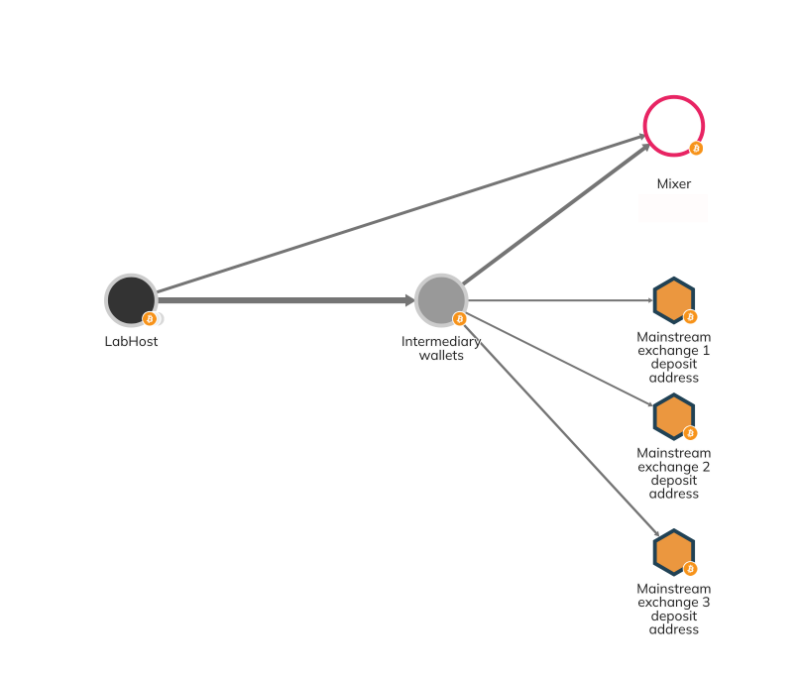
LabHost then sent most of those funds to a few mainstream exchanges, presumably to be cashed out, as well as to a popular mixer, likely to launder the funds and obfuscate their origins. We can see some of this activity on the Chainalysis Investigations graph below.
We can see similar patterns in LabHost’s Ethereum activity as well, though without the usage of mixers.
Like many cybercriminal organizations, LabHost utilized a range of third-party services and infrastructure providers. We can see on-chain evidence of this on the Chainalysis Investigations graph below.
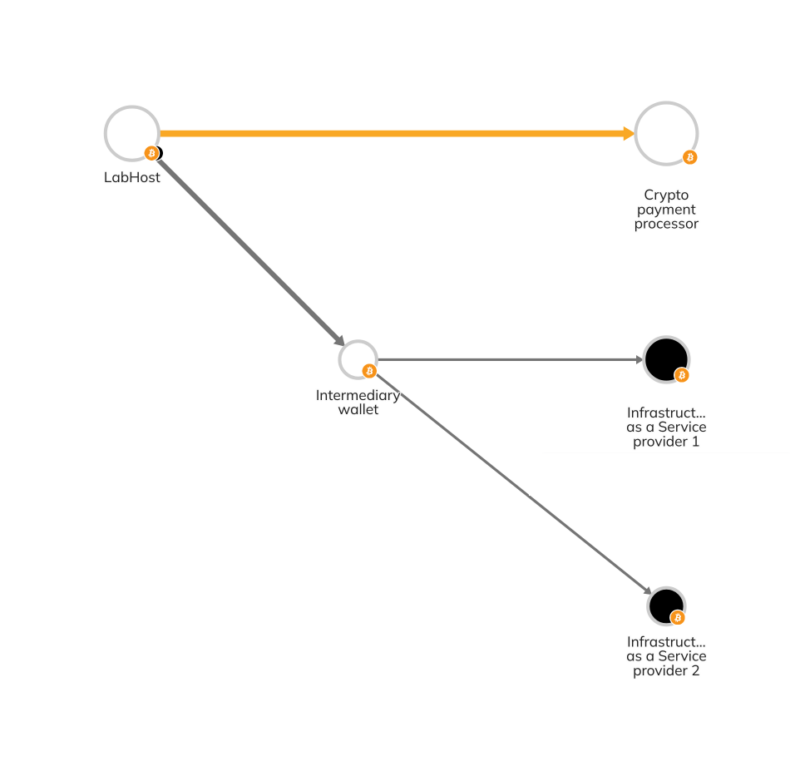
Here, we see LabHost sending funds to two types of service providers: A payment processor that facilitates the crypto payments for businesses (also known as a merchant services provider), and two infrastructure-as-a-service providers. While we can’t share the exact nature of all of the infrastructure providers LabHost transacted with, other criminal organizations have utilized these services for web hosting, email tools, proxy services, and more. It’s possible that LabHost did the same.
Finally, blockchain analysis also reveals that many of the cybercriminals who used LabHost also appear to have been customers of iSpoof, another illicit provider of tools used for fraud that was shut down by the Metropolitan Police and other law enforcement agencies in 2022. The Chainalysis Investigations graph below shows several wallets that transacted with both iSpoof and LabHost.
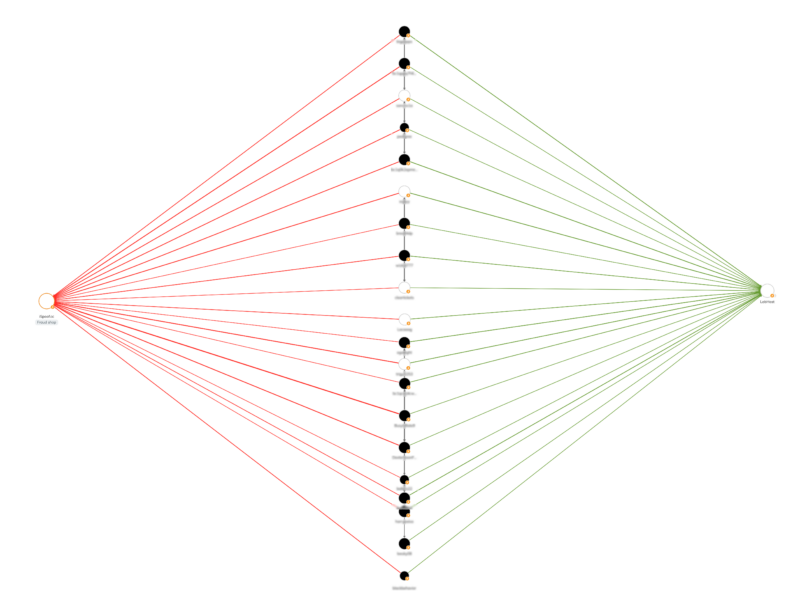
The 20 wallets shown above transacting with iSpoof and LabHost, who we can assume are almost certainly involved in online fraud, have collectively sent and received over $5.3 million worth of Bitcoin, suggesting that their criminal activity is extensive and lucrative.
Fighting online fraud
As we’ve covered previously, scams are perhaps the biggest threat to consumers in the entire crypto crime ecosystem. This case shows that cryptocurrency’s role in scams extends beyond threat actors promoting crypto Ponzi schemes, or seeking to take funds from users’ crypto wallets. Victims whose bank accounts were compromised in LabHost-supported phishing attacks likely had no idea the crime against them had a cryptocurrency nexus, but in many cases, the cybercriminals involved likely wouldn’t have been able to access LabHost’s tools without paying in crypto. Crypto can play a crucial role in virtually all forms of crime, even in non-obvious cases.
Thanks to the efforts of the Metropolitan Police and the other agencies involved in this disruption, LabHost is one crypto-adjacent criminal organization that has been severely hampered.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

