Darknet markets were one of two categories of crypto crime that saw revenues rise in 2023. In total, darknet markets and fraud shops received $1.7 billion last year, a rebound from 2022 — the year that saw the sizable Hydra Marketplace close. The ensuing war for darknet market dominance that began in 2022 continued into 2023, but no other market has since matched Hydra’s financial success. We’ll discuss theories as to why, and other darknet market trends here.
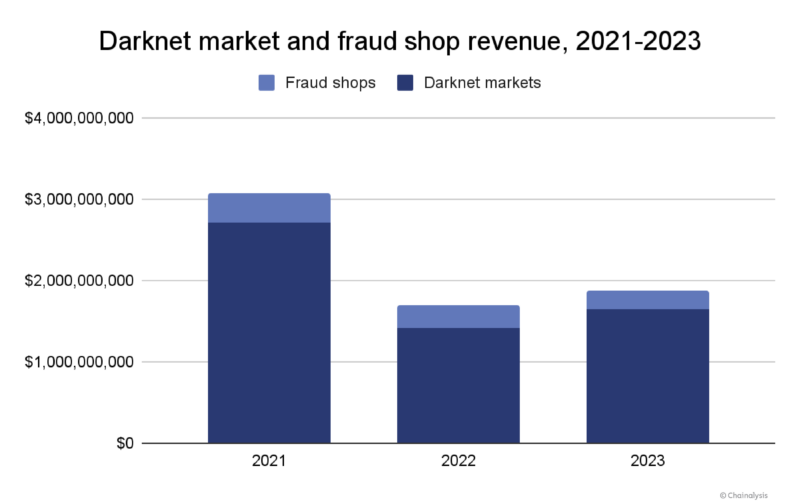
The chart above shows that, while values haven’t risen back to 2021 levels, darknet market revenue has slightly rebounded since Hydra’s closure in 2022.
The continuing battle for darknet market dominance
In terms of individual market success, Mega Darknet Market led the pack with over half a billion in crypto inflows, and Kraken Market (not to be confused with the popular cryptocurrency exchange Kraken) in particular gained prominence among Russian darknet markets, as shown below. Blacksprut and OMG!OMG!, markets that jockeyed for position in the wake of Hydra’s closure, are still top players in the darknet market ecosystem.
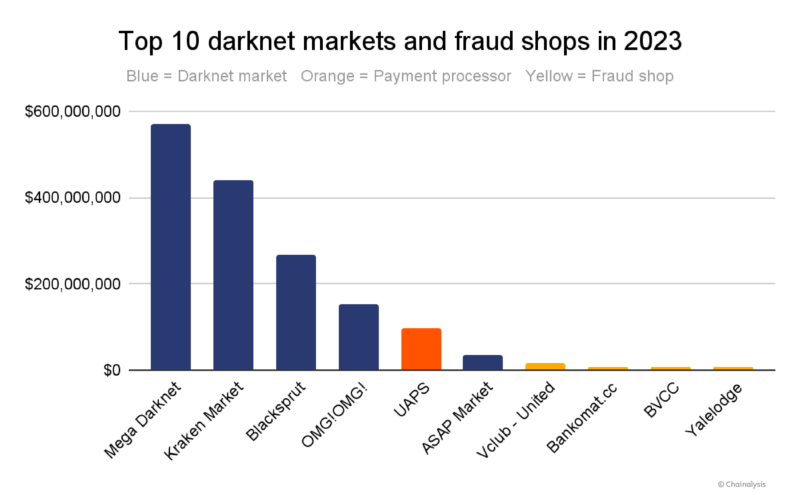
In recent years, some darknet markets and fraud shops have been integrating crypto payment processors on their websites via APIs, possibly as a way to improve operational efficiency and increase security. Essentially, these payment processors provide a white label service for darknet markets and fraud shops, and a seamless checkout experience for those services’ customers. UAPS, shown in the chart above, is one such example of a payment processor that many fraud shops, including the OFAC-designated Genesis Market, used in 2023. The value received by UAPS in this chart includes payments sent to multiple fraud shops using the service as a payment processor.
Another newer trend: Darknet markets that employed brazen marketing tactics in 2022 appeared to gain a competitive edge in 2023. Take Kraken Market for instance, which opened in 2022 and bills itself as Hydra’s successor. As a way to tease its impending launch, in the fall of 2022, Kraken Market employed an immersive 3D billboard in Moscow containing an animated kraken.
 Kraken Market’s immersive 3D billboard in Moscow. Source: Lenta.ru
Kraken Market’s immersive 3D billboard in Moscow. Source: Lenta.ru
And, perhaps the most aggressive marketing stunt the darknet market ecosystem has seen yet, in December of that year, Kraken Market wrapped a bus in an advertisement that included a QR code for the market’s website. The bus blocked two traffic lanes on a road near Russia’s Ministry of Foreign Affairs before security forces removed it an hour later.
On a smaller scale, Mega Darknet Market placed a few ads with QR codes in public places like Moscow subway trains. While tactics like these may have helped boost revenue for both markets, again, they have yet to match Hydra’s sizable financial success.
Darknet market services show fragmentation in 2023
Throughout the history of the darknet market ecosystem, at different turns one marketplace has typically played the dominant role. The last several years’ examples include Silk Road, AlphaBay, Wall Street Market, and Hydra, most recently. Historically, as law enforcement closed each dominant marketplace, a new leader emerged. We can see this pattern on the chart below, which shows the level of market share controlled by the dominant market of each epoch. The recovery pattern is fairly consistent until the Hydra Marketplace closure, after which no dominant darknet market emerged.

Darknet market role specialization provides one possible explanation as to why the ecosystem has yet to see a dominant player.
Darknet markets differentiate themselves by unique service offering
Historically, darknet markets have been heavily associated with illicit drug trade, a reputation that Silk Road played a significant role in creating. However, over the years some markets have evolved beyond this capacity to develop a robust catalog of illicit services like money laundering, fiat offramping, and products that enable cybercriminal activities like ransomware and malware attacks. One such sophisticated darknet market, Hydra, offered all that and more.
By contrast, it appears today’s darknet markets largely serve specific niches and have individually organized themselves into unique criminal functions, which we determined when examining the origin points for darknet market inflows last year. As such, the chart below illustrates darknet market share by crime type based on the following categories:
- Cybercriminal enablement. Darknet market services related to ransomware, malware, stolen funds, and other types of cybercrime. Enablement could include root kits, access to personally identifiable information (PII), and potentially, offramping for stolen funds.
- Drug sourcing and supply. Online pharmacies or darknet markets that sell drugs to vendors on other darknet markets.
- Other illicit laundering/buying. Transfers made to darknet markets for the purpose of obfuscating on-chain activity or purchasing illegal products.
- Rest of world drug exchange. Drug purchases made on darknet markets serving a global customer base, as opposed to primarily a Western or Russian customer base.
- Russian-serving drug exchange. Drug purchases made on darknet markets by customers based in Russia.
- Western-facing drug exchange. Drug purchases made on darknet markets by customers generally based in the United States and Western Europe.
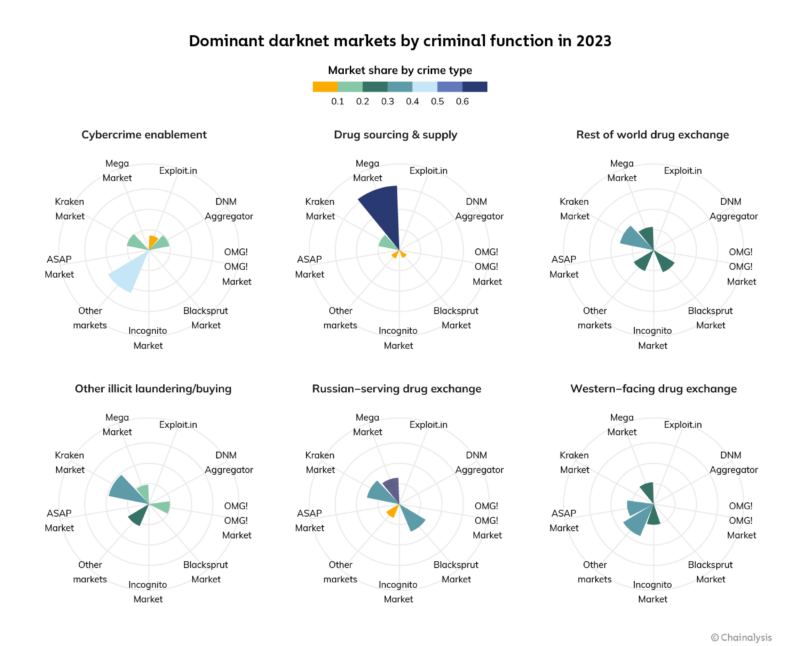
The categorization in the chart above is based on origin points. Cybercrime enablement represents flows from ransomware, stolen funds, malware, or fraud shops to darknet markets.
Drug-related revenue comes from sources like exchanges. Western drug flows in particular come from US-domiciled exchanges and trace flows from those to darknet markets. The entity “DNM Aggregator” that appears within each category refers to a service we’ve identified as being in control of multiple, disparate darknet markets.
When it comes to cybercriminal enablement, markets like Kraken Market, the DNM Aggregator, and Exploit.in are go-to services, providing bad actors with tools to carry out ransomware attacks, hacks, and more. Kraken Market also captured the largest share of transfers potentially sent for the purpose of obfuscating funds, as well as buying illegal products. In addition to that activity, markets like these host vendors that advertise their own cashout or swapping services, resulting in tens of millions of dollars in laundered funds.
Mega Darknet Market is the dominant drug supply source for drug vendors on other darknet sites, holding a 63.4% share of that market. When looking at darknet drug markets serving Russia-based customers, Kraken Market captured 30.9% of market share, with Blacksprut and Mega Darknet markets closely following. As for drug markets serving Western customers, ASAP Market held a 25.0% share, followed by Mega and Incognito.
Darknet market revenue based on drug-purchasing behaviors
When looking at 2023 drug-purchasing habits for customers from exchanges primarily serving users in North America and Western Europe, the data indicate that just two markets played dominant roles across drug purchase types, while most captured smaller, fragmented shares of total revenue received.
Here are category definitions for the chart below. Keep in mind that these categories are based solely on purchase sizes, which we use to make assumptions about their likely purpose.
- Small retail. Purchases of less than $100, likely made for personal consumption.
- Large retail. Purchases between $100 and $500, likely made for personal consumption.
- Social supply. Purchases between $500 and $1,000, which indicate customers may be sharing drugs with other third parties in social settings.
- Potential wholesale. Purchases over $1,000, more likely to be made by drug sellers and distributors.
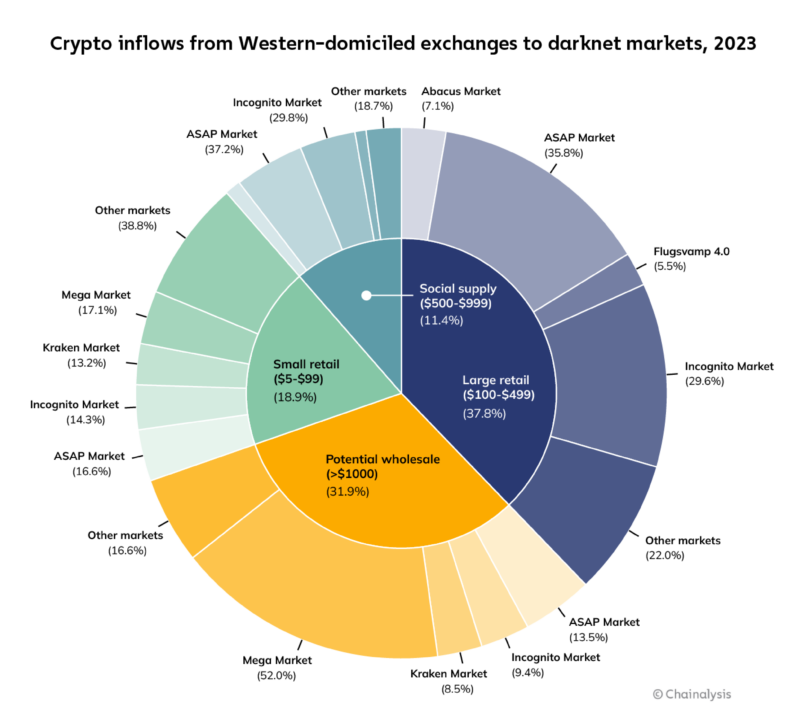
The chart above shows that ASAP and Mega Darknet markets led the large retail and wholesale segments respectively. Looking closer at ASAP Market inflows, it won some share of revenue across all drug purchase types, receiving 37.1% of social supply, 35.7% of large retail, 16.5% of small retail, and 13.5% of wholesale purchases.
Though Mega Darknet Market typically serves a Russian customer base, the drug revenue shown in the chart above likely came from customers based in Europe. Mega clearly dominated the realm of wholesale drug purchases, capturing 51.9% of that segment.
Fentanyl sales in darknet markets
Despite most darknet markets banning the sale of fentanyl in their terms of service, nearly all mainstream Western-facing markets have vendors that sell fentanyl-laced products. While it received a relatively small share of large retail purchases as shown in the previous chart, Abacus Market is one such example. Though many customers are concentrated in Australia, Abacus has vendors and customers around the world, including the United States.
Customer reviews found on the Abacus site indicate that some of its American vendors sell drug products laced with fentanyl. Additionally, vendors found on Abacus and many top Western-facing markets sell an analog of fentanyl called a-Methylfentanyl — colloquially known as “China White.” According to the Universal Journal of Clinical Medicine, drug researchers believe that this analog is the product of contamination during important parts of the fentanyl synthesis process, and is sold for its powerful effects, which can be up to 300 times more potent than morphine. It has appeared in overdose deaths in recent years.
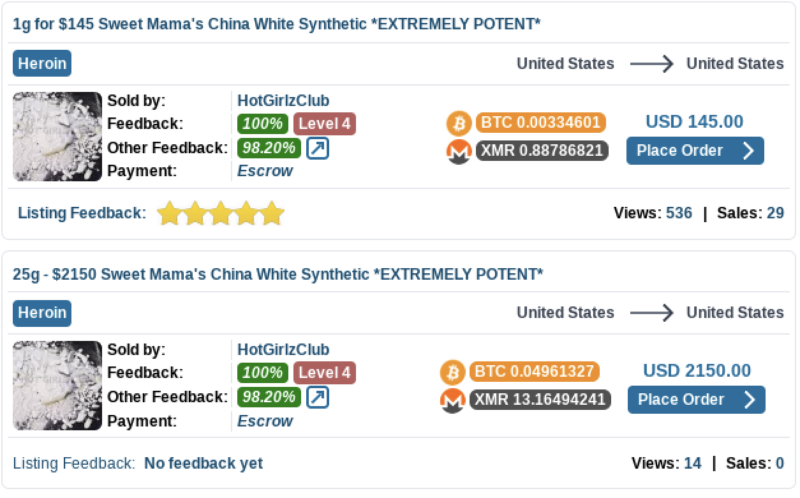
U.S.-based drug vendors on Abacus Market advertising a synthetic opioid called China White, which its customers can purchase using Bitcoin or Monero.
Another darknet market known for facilitating fentanyl sales to the United States was Canada-based AlphaBay. A once-sizable illicit enterprise that began in 2014, AlphaBay was closed by authorities in 2017 and then reopened in 2021. The last version of the market operated until February of 2023, and a month after that closure, a former AlphaBay vendor pled guilty to distributing fentanyl that caused fatal overdoses in Oregon.
Fentanyl and fentanyl-laced drugs also arrive in the United States through Latin America based cartels. U.S. customers predominantly purchase drugs from these groups that are known to have used crypto to source fentanyl precursor chemicals from labs based in China. The cartels then use those chemicals to manufacture fentanyl that is later sold in the U.S.
Crime forums and markets specializing in cybercrime enablement
Much like with drug sales, a similar pattern of task differentiation emerged among darknet markets providing cybercriminal services. In the chart below, we see that the DNM Aggregator emerged as the clear leader among fraud shops enabling cybercrime, and Exploit.in and Kraken Market almost equally sold tools used to facilitate ransomware attacks. Kraken Market also received the largest share of stolen funds. As for cybercriminal administration, the category includes inflows from ransomware affiliate wallets. This includes purchases such as malicious software and supporting services which cybercriminals sometimes make using escrow services on crime forums.
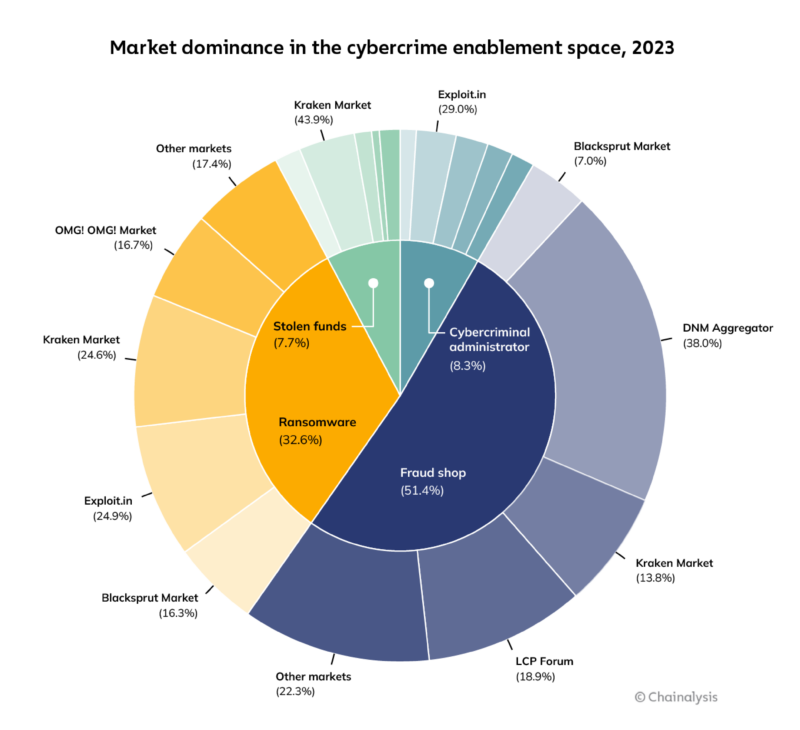
Dutch National Police share depth and sophistication of Genesis Market identity theft operation
Fraud shops are vendors that typically operate on the dark web and facilitate the sale of stolen data and personally identifiable information (PII), which cybercriminals abuse in illicit activities like scamming, identity theft, and ransomware. One fraud shop that provided services like these, Genesis Market, saw its end last April after a coordinated, international law enforcement effort called Operation Cookie Monster closed it down, and OFAC sanctioned it.
Though it’s common for fraud shops to operate on the dark web, Genesis Market was accessible on the clearnet via Google search, and simply required an invitation code to create an account. This ease of access attracted a new breed of criminals not typically associated with cybercrime. To them and others, Genesis sold forms of stolen PII like credentials for email and social media accounts, as well bank accounts and crypto service accounts, and in its lifetime received tens of millions of dollars in crypto, mostly Bitcoin.
For a fraud shop, Genesis Market demonstrated an unusual level of sophistication by offering Impersonation-as-a-Service (IMPaaS), meaning robust “online fingerprints” of victims rather than just their credentials for individual services; Genesis’ IMPaaS packages included access to victims’ browser cookies, which allowed cybercriminals to circumvent two-factor authentication (2FA) and wreak havoc with victims’ accounts.
We spoke with Ruben van Well, Chief Inspector of Team Cybercrime Rotterdam from the Dutch National Police, to learn about their involvement in the Genesis Market case, and how the Genesis operation worked.
How Genesis Market stole the identity of over 2 million victims worldwide
In 2019, the FBI started its investigation into Genesis Market and enlisted other government agencies and law enforcement organizations across the world, working towards the market’s closure on April 4, 2023. As part of the investigation, the Dutch National Police took the lead on cybercrime prevention, and Van Well shared his insight on the sophistication of the fraud shop’s operation.
In order to gain control of victims’ computers, the malware Genesis Market employed used a legacy Bitcoin address to determine the command-and-control (C2) server, from which cybercriminals initiated remote access to infected devices.
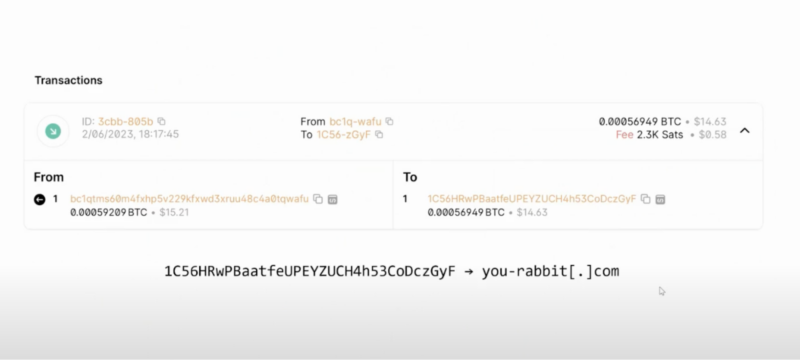
The legacy Bitcoin address pivotal to the malware side of the Genesis operation
The information-stealing malware package that Genesis Market used to exploit victims included a hidden Chromium-based browser plugin, made to look like a Google Drive plugin, which captured credentials stored in victims’ browsers.
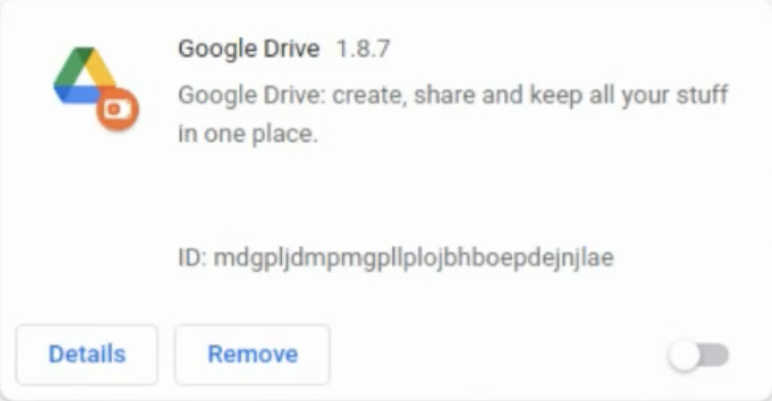
Hidden browser plugin which captured credentials stored in victims’ browsers
As it retrieved data from malware-infected computers, Genesis sold victims’ online footprints — which it called “bots” — on its market. Each bot represented a compromised computer or device and the credentials associated with its owner. While it operated, Genesis Market sold 1.6 million bots. On the fraud shop’s website, cybercriminals could comb through hundreds of thousands of bots on its robust user interface (UI), filtering results by criteria like country or searching for credentials tied to a particular domain name. The UI showed how many logins and what accounts each bot contained; the more logins provided, the more expensive the bot, especially when it included bank or crypto account credentials. The UI also showed when the victim’s device was infected by the malware and when it was last updated, and Genesis provided customers with a wiki on how to abuse victims’ credentials.
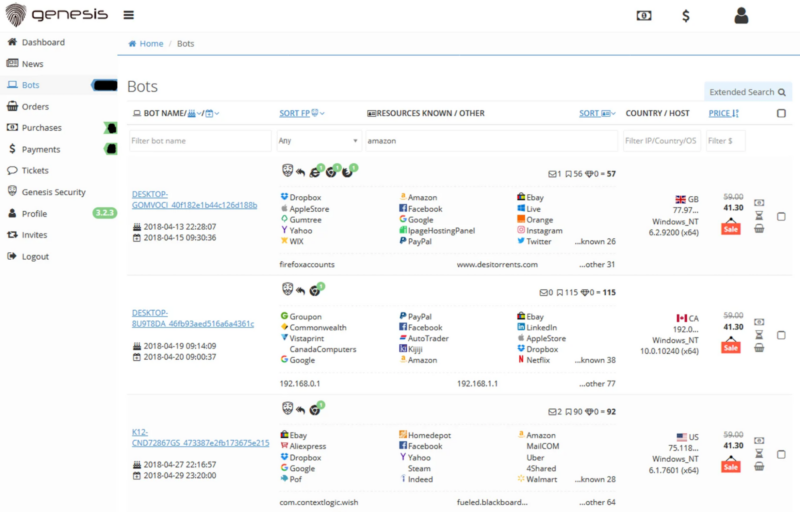
A page on the former Genesis Market showing bots (i.e., victims’ profiles) for sale. Source: ZDNet
One of its most insidious innovations — the Genesium browser — was a browser plugin that Genesis built for its customers to use. Any time the information-stealing malware detected changes to a victim’s passwords or a new account, it would update the Genesium browser with the latest credentials. In addition to stealing logins, the malware scraped browser cookies, granting cybercriminals control over session cookies which helped them mimic victims’ computers. Since many website cookies persist for 30 days, criminals were often able to evade 2FA processes.
“This made Genesis Market extremely dangerous because they had their hands on a lot of credentials but they could also impersonate the victim online,” says Van Well. “We saw bank accounts and crypto wallets being cleared, as well as identity being misused to open new accounts. We saw goods being bought from online shops, and a variety of cybercrime, which was all related to Genesis Market.”
In one particularly devastating case, a man lost his entire $80,000 pension. Using his credentials, cybercriminals committed a variety of online fraud activity over the course of six months. Given the tooling’s ability to capture new password updates, the perpetrators could easily maintain control over his accounts, and they opened bank accounts in his name and had his physical mail sent to an address where they could receive it.
How the Dutch National Police helped Genesis Market victims
In addition to investigating individual incidents of crime against Dutch citizens, the Dutch National Police worked with public and private sector partners to investigate the infection chain — the path of distribution and installation — for the information-stealing malware that enabled Genesis Market to steal victims’ identities. The results of that investigation were published in a report called Technical analysis of the Genesis Market. Van Well explained that his organization doesn’t typically share so much detailed technical information around investigations, but it felt imperative to provide these details to law enforcement and tech companies around the world to help them fight future cybercrimes. Though Genesis Market domains and servers were seized and antivirus programs have been updated, cybercriminals have already rebuilt illicit services like these.
To help Genesis Market victims and prevent future crimes, the Dutch Police created a Check your hack tool that lets victims see if their credentials were sold or for sale on Genesis Market. The tool is still available today, and interested parties simply need to enter their email address to place an inquiry. If the address is in one of the cybercrime datasets, the person will receive an email that includes personalized instructions on how to clean up their computer and make it safe again. In the first 24 hours of launching Check your hack, two million people took advantage of the service. So far, five million people have used the tool, and over 13,000 victims have been notified that their computer was infected, and received instructions to help them make their device safe again.
As far as financial recourse for victims, some banks and insurance companies have provided payouts and will include those funds as damages in lawsuits against Genesis Market cybercriminals. As for Genesis Market cybercriminals located in the Netherlands, three have already been convicted and received prison sentences considered severe for that jurisdiction. The first received 24 months and the second, four years. The third convicted cybercriminal — the biggest Dutch user and the number 10 user worldwide — received a four-year sentence.
Fraud shops use payment processor to boost efficiency
In 2023, Chainalysis discovered that some popular fraud shops rely on payment processors as a way to reduce their own costs, add efficiency to their operations, and perhaps add a layer of security to transactions. Genesis Market extensively used a payment processor called UAPS, so much that the processor’s average inflows fell by 25.7% after Genesis closed last April. Regardless, UAPS remains a key provider of payment infrastructure to top fraud shops.
Darknet market revenues rose slightly, but have yet to regain Hydra Marketplace highs
While the darknet market ecosystem showed signs of recovery in 2023, it has yet to return to the revenues it experienced before the Hydra Marketplace closure in 2022, given the financial success of that operation. It’s noteworthy that, despite some unusual marketing efforts, no other darknet market has since assumed Hydra’s mantle of being the one-stop-shop for illicit products and services. Though the sanctioning and closure of fraud shop Genesis Market occurred last year, there were no other sanction events for the darknet market ecosystem, or major market takedowns. We’ll continue monitoring darknet market trends in 2024, and are curious to see what new tactics markets and fraud shops may employ to find more customers.

